[Day 44] Cisco ISE Mastery Training: WPA2-Enterprise Configuration
Table of Contents
Introduction
WPA2-Enterprise is the gold standard for securing enterprise Wi-Fi networks. Unlike WPA2-PSK (which uses a single shared key), WPA2-Enterprise leverages 802.1X authentication with a RADIUS server to provide per-user authentication, dynamic encryption keys, and granular network access control.
In Cisco ISE, WPA2-Enterprise forms the backbone of secure wireless NAC — integrating user identity, device posture, and context-aware policies. This ensures only authenticated, authorized, and compliant endpoints gain access, while applying the right VLANs, ACLs, and QoS dynamically.
When combined with certificates (EAP-TLS) or credentials (PEAP-MSCHAPv2), WPA2-Enterprise not only enhances security but also enables full visibility and policy enforcement for corporate and BYOD devices.
Problem Statement
In many organizations:
- Wi-Fi networks use shared passphrases (PSK), making them vulnerable to leaks.
- IT cannot track which user or device is connecting.
- There’s no integration between Wi-Fi authentication and corporate identity systems (AD, LDAP).
- Network policies can’t be enforced per user or per device.
The result?
- Credential sharing undermines accountability.
- No per-session keys means a compromise affects everyone.
- Lack of visibility makes threat detection harder.
A scalable, standards-based wireless authentication method that ties user identity to network access is critical. That’s where WPA2-Enterprise with Cisco ISE comes in.
Solution Overview
With Cisco ISE as the RADIUS server, WPA2-Enterprise works like this:
- User connects to the secure WLAN (SSID).
- 802.1X authentication begins — the WLC sends EAP requests to the client.
- EAP method negotiation occurs (e.g., PEAP-MSCHAPv2, EAP-TLS).
- The WLC forwards EAP messages to ISE over RADIUS.
- ISE validates the user/device credentials against Active Directory or internal identity stores.
- Upon success, ISE returns an Access-Accept with authorization attributes (VLAN, ACL, dACL).
- The WLC applies the attributes, encrypts traffic using a unique session key per user.
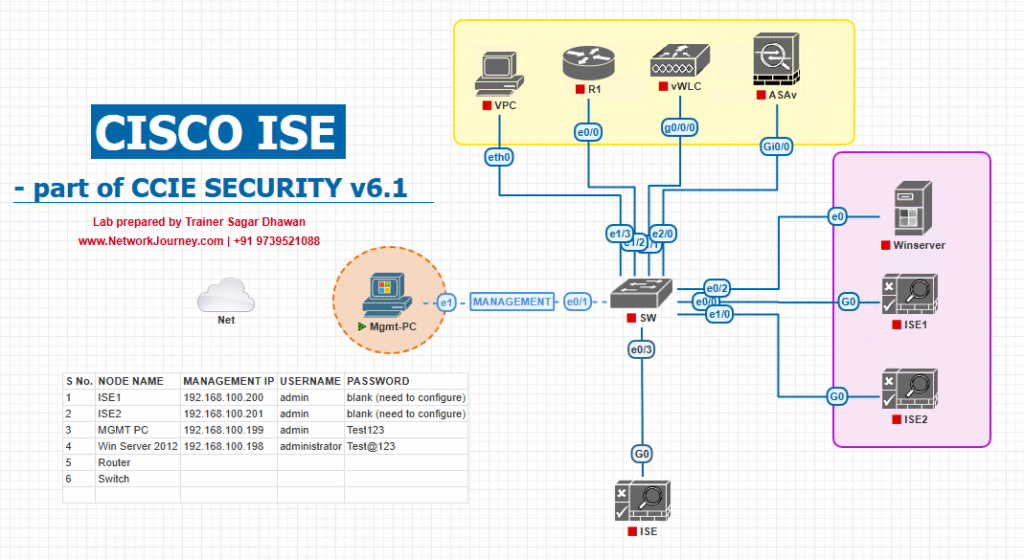
Sample Lab Topology
Lab Components:
- Virtualization: VMware Workstation or EVE-NG.
- Cisco ISE: v3.x.
- Cisco WLC: 9800-CL or AireOS 8.10+.
- Switch: Catalyst 9300 (physical or virtual).
- AD Server: Windows Server 2019 (with DNS + AD).
- Endpoints:
- Windows 10 laptop (domain joined).
- BYOD laptop (non-domain).
- Smartphone.
Topology Diagram:
Step-by-Step GUI Configuration Guide
Part A – WLC Configuration
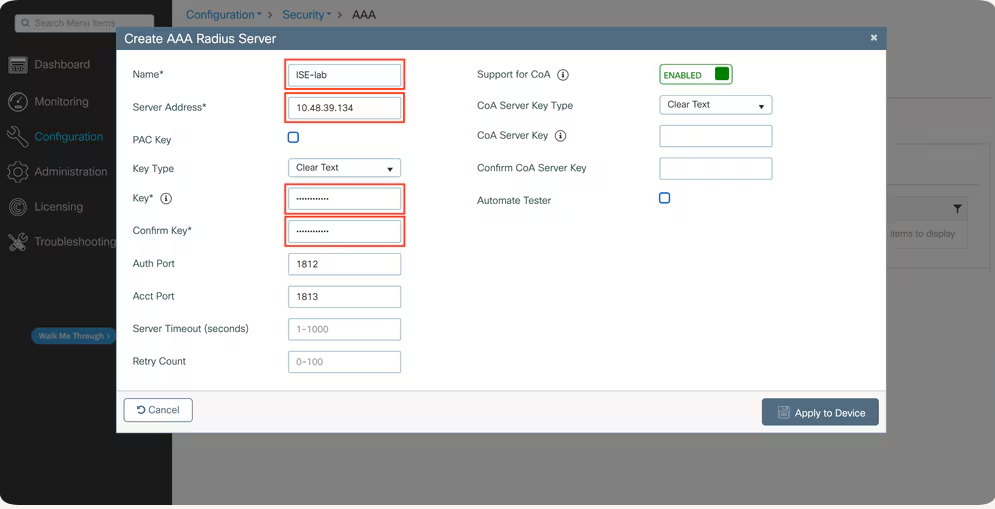
- Add ISE as RADIUS Server
- WLC GUI: Security > AAA > RADIUS > Authentication
- Add:
- Server IP:
ISE-IP - Shared Secret:
ISE-Secret(match with ISE)
- Server IP:
- [Screenshot: WLC RADIUS Server Config]
- Create Secure WLAN (SSID)
- WLANs > Create New > SSID:
WPA2ENT - WLAN ID:
2 - [Screenshot: WLAN Creation]
- WLANs > Create New > SSID:
- Configure 802.1X Security
- WLAN > Security > Layer 2
- Layer 2 Security: WPA2-Enterprise
- Authentication Key Management (AKM): 802.1X
- [Screenshot: WPA2-Enterprise Enable]
- Bind WLAN to ISE
- WLAN > Security > AAA Servers
- Authentication Server:
ISE - [Screenshot: Bind AAA Server]
Part B – Cisco ISE Configuration
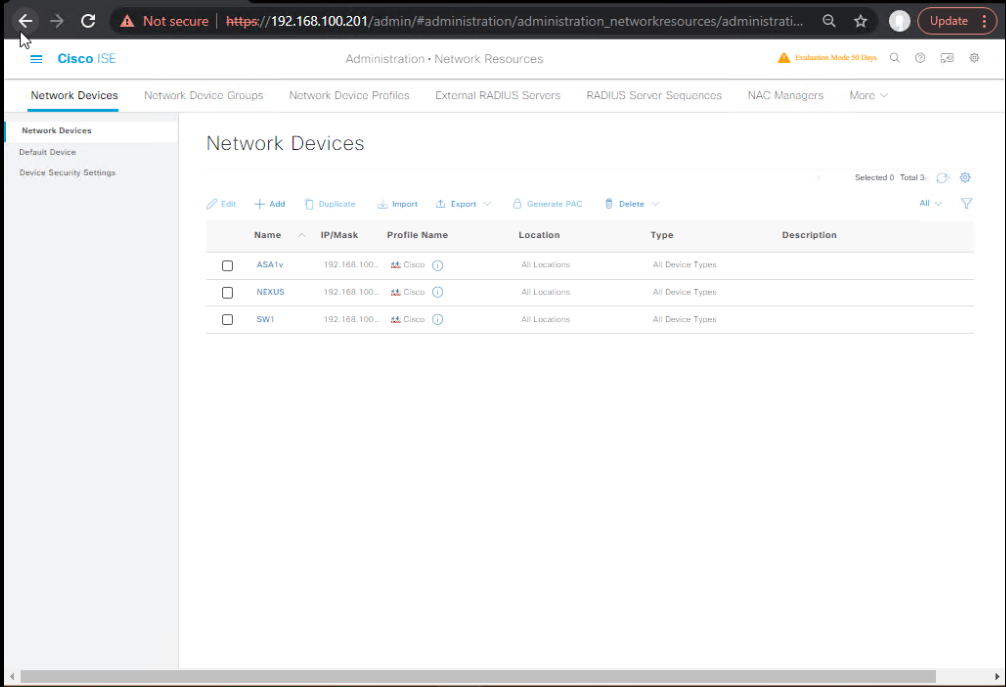
- Add WLC as Network Device
- Administration > Network Resources > Network Devices
- Name:
WLC-9800CL - IP:
WLC-IP - Shared Secret: Same as WLC config
- [Screenshot: Add Network Device]
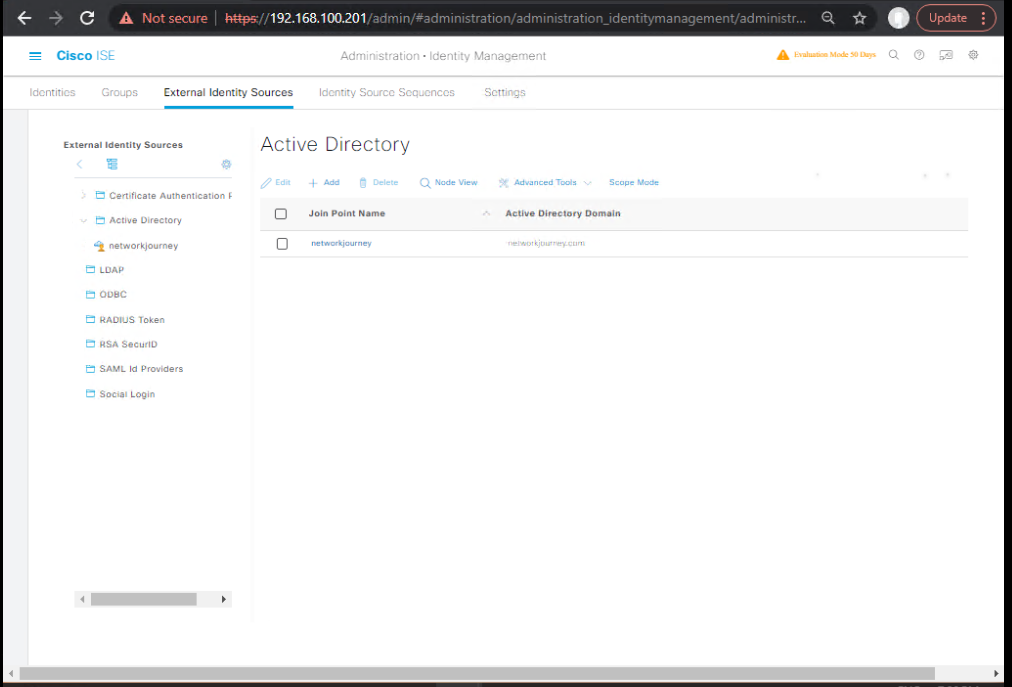
- Integrate with Active Directory
- Administration > Identity Management > External Identity Sources > Active Directory
- Join ISE to the domain
- [Screenshot: AD Join Screen]
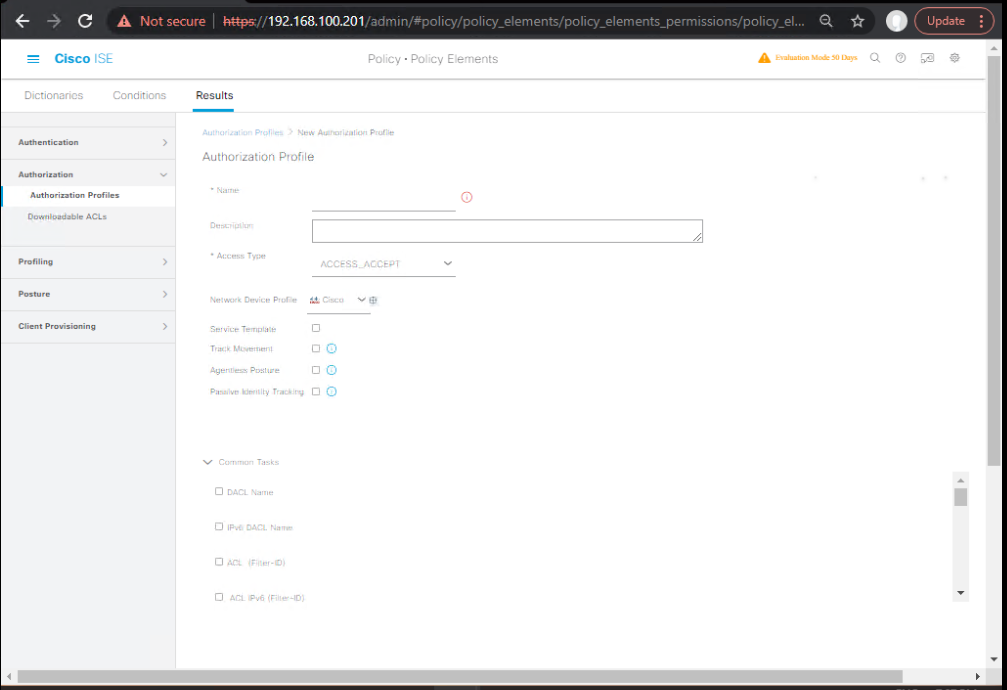
- Create Authorization Profile
- Policy > Policy Elements > Results > Authorization > Authorization Profiles
- Name:
Corp-Access - VLAN ID: 20
- dACL: Permit_Corp_Resources
- [Screenshot: Authorization Profile Config]
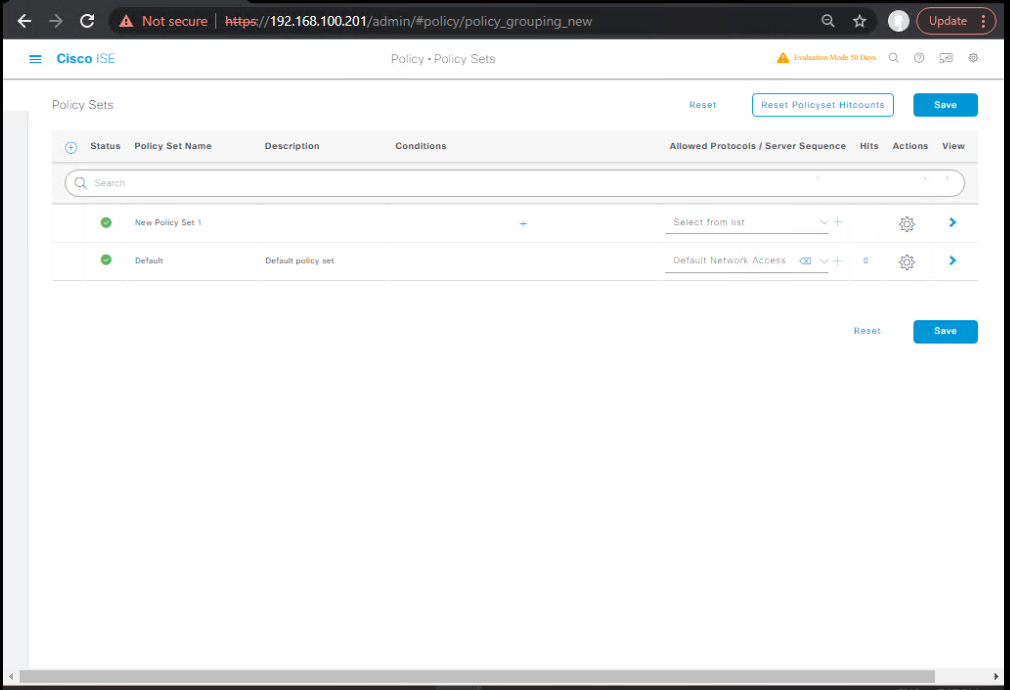
- Configure Policy Set for WPA2-Enterprise
- Policy > Policy Sets
- Create:
WPA2-Enterprise Policy - Condition:
Wired/Wireless = WirelessANDAuthenticationMethod = EAP - Authentication Policy: External > Active Directory
- Authorization Policy: AD Group →
Corp-Access - [Screenshot: Policy Set Config]
Part C – Client Configuration
- On Windows:
- Network Settings > Connect to SSID
WPA2ENT - Enter domain username/password or certificate authentication.
- [Screenshot: Windows WLAN Auth Prompt]
- Network Settings > Connect to SSID
- On Smartphones:
- Choose SSID, enter enterprise credentials.
- Accept server certificate (if prompted).
Part D – Validation
- WLC CLI:
show client detail <MAC> show wlan summary show radius auth statistics debug client <MAC> - ISE GUI:
- Operations > RADIUS > Live Logs → Filter by username/MAC.
- Check method: PEAP-MSCHAPv2 or EAP-TLS.
- Verify authorization profile applied.
FAQs for WPA2-Enterprise in Cisco ISE
1. Which EAP method should I use — PEAP or EAP-TLS?
- PEAP-MSCHAPv2 is easier to deploy (username/password), works well for corporate AD environments, but is less secure because passwords can be brute-forced offline if intercepted.
- EAP-TLS is the most secure (certificate-based), but requires a PKI and certificate management process.
2. Do I need a CA (Certificate Authority) for WPA2-Enterprise?
- For PEAP-MSCHAPv2, you still need a server certificate on ISE to prevent credential theft via rogue APs.
- For EAP-TLS, both the server and client certificates are required, so a CA is mandatory.
3. Can I use WPA2-Enterprise for BYOD and corporate devices on the same SSID?
Yes. ISE can detect the device posture or identity group and apply different authorization profiles dynamically — corporate devices get full access, BYOD gets restricted access.
4. How can I avoid certificate warnings on client devices?
Install your internal CA root certificate (or the public CA root, if using a public cert) on all client devices so they trust the ISE server certificate during authentication.
5. Can WPA2-Enterprise assign VLANs dynamically per user or device?
Yes — the ISE Authorization Profile can return a VLAN ID or name as a RADIUS attribute, letting the WLC place the user/device in the correct network segment.
6. What happens if ISE is unreachable during authentication?
- Clients will fail to connect unless the WLC is configured for critical VLAN or fallback SSID.
- You can also configure a secondary RADIUS server as backup.
7. How do I troubleshoot WPA2-Enterprise authentication failures?
- On WLC CLI:
debug client <MAC> show client detail <MAC> show radius auth statistics - On ISE: Check Operations > RADIUS > Live Logs to see authentication method, failure reason, and policy result.
8. Can WPA2-Enterprise be combined with posture checks?
Yes — after the 802.1X authentication, ISE can perform posture assessment (e.g., antivirus status, OS patch level) before granting full access.
9. Is WPA2-Enterprise compatible with WPA3?
Yes — WPA3-Enterprise builds on the same 802.1X/EAP framework but uses stronger encryption (GCMP-256). Most modern WLCs can run both WPA2-Enterprise and WPA3-Enterprise on the same SSID for compatibility.
10. What’s the maximum number of WPA2-Enterprise sessions ISE can handle?
It depends on licensing and hardware resources. With a properly scaled distributed deployment, ISE can handle hundreds of thousands of concurrent 802.1X authentications.
YouTube Link
For more in-depth Cisco ISE Mastery Training, subscribe to my YouTube channel Network Journey and join my instructor-led classes for hands-on, real-world ISE experience
Closing Notes
WPA2-Enterprise with Cisco ISE delivers identity-based, encrypted, and policy-driven Wi-Fi access. It not only strengthens wireless security but also integrates with NAC for compliance checks, guest management, and segmentation. In modern enterprise NAC design, it’s a must-have — and with proper lab practice, you can master it quickly.
Upgrade Your Skills – Start Today
If you’re serious about becoming a job-ready Cisco Security Engineer, don’t just read about configurations — build them in real labs with expert guidance.
I run a focused an intensive 4-Month CCIE Security Instructor-Led Training program that takes you from fundamentals to advanced multi-vendor NAC, firewall, VPN, and threat control.
Includes:
- Live interactive classes
- Full EVE-NG topologies
- Step-by-step real-world labs
- Lifetime recording access
- Career mentorship & interview prep
Secure your spot here → https://course.networkjourney.com/ccie-security/ and join the hundreds of engineers who’ve leveled up their careers.
Enroll Now & Future‑Proof Your Career
Email: info@networkjourney.com
WhatsApp / Call: +91 97395 21088
![[Day 44] Cisco ISE Mastery Training: WPA2-Enterprise Configuration](https://networkjourney.com/wp-content/uploads/2025/08/Day-44-Cisco-ISE-Mastery-Training-WPA2-Enterprise-Configuration.png)
![Static vs Dynamic Routing – Which One Should You Trust in Real Networks? [CCNP ENTERPRISE]](https://networkjourney.com/wp-content/uploads/2025/06/Static-vs-Dynamic-Routing–Which-One-Should-You-Trust-in-Real-Networks_networkjourney-1.png)

