[Day 45] Cisco ISE Mastery Training: Wireless Guest Access Flow
Table of Contents
Introduction
In modern enterprises, guest Wi-Fi access is no longer just a convenience — it’s an expectation. Whether it’s vendors, customers, contractors, or interview candidates, visitors expect to connect instantly and securely.
But here’s the challenge:
- You want guests online quickly, without IT intervention.
- You must isolate guests from corporate resources.
- You still need visibility, logging, and control.
Cisco ISE’s Wireless Guest Access Flow solves this with centralized guest authentication portals, policy-based network segmentation, and sponsor-based approvals — all integrated into your wireless infrastructure.
The result? Guests get seamless, secure internet access, and you maintain NAC-level security control.
Problem Statement
Without a structured guest Wi-Fi solution, networks often:
- Use open SSIDs with no tracking — anyone can connect.
- Share WPA2-PSK keys — leading to key leaks and uncontrolled access.
- Lack onboarding workflows — requiring IT to manually configure devices.
- Provide no accountability — you don’t know who connected or what they did.
From a security perspective, unmanaged guest Wi-Fi creates:
- Attack vectors into corporate VLANs.
- Compliance violations (no audit logs).
- Inability to meet security policies for visitors.
Solution Overview
Cisco ISE addresses this by implementing a Guest Access Flow with:
- Dedicated Guest SSID on the WLC.
- Web Authentication (Central WebAuth) via redirect to ISE’s Guest Portal.
- Portal Options: Self-registration, sponsor approval, or bulk account creation.
- Dynamic VLAN/dACL assignment to isolate guest traffic.
- Timed credentials — accounts expire automatically.
- Audit logging — all guest logins are tracked in ISE.
The WLC acts as the redirector, while ISE handles authentication, authorization, and portal presentation.
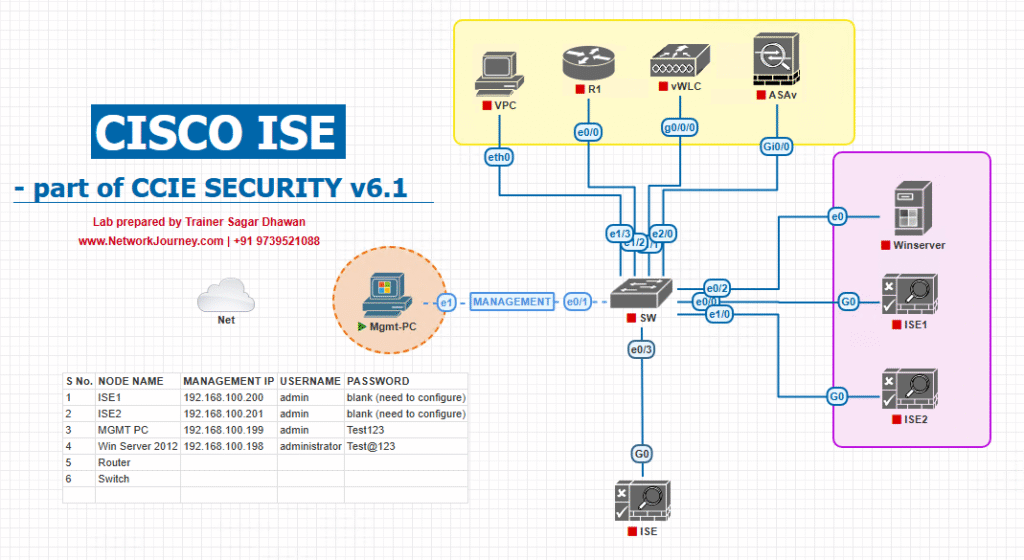
Sample Lab Topology
Lab Environment:
- Virtualization: VMware Workstation / EVE-NG.
- Cisco ISE: v3.x.
- Cisco WLC: 9800-CL (virtual).
- Switch: Catalyst 9300 or virtual switch in EVE-NG.
- Endpoints:
- Guest laptop (Windows).
- Sponsor/admin laptop.
- AD/DNS server (for sponsor authentication).
Topology Layout:
Step-by-Step GUI Configuration Guide
Part A – WLC Configuration
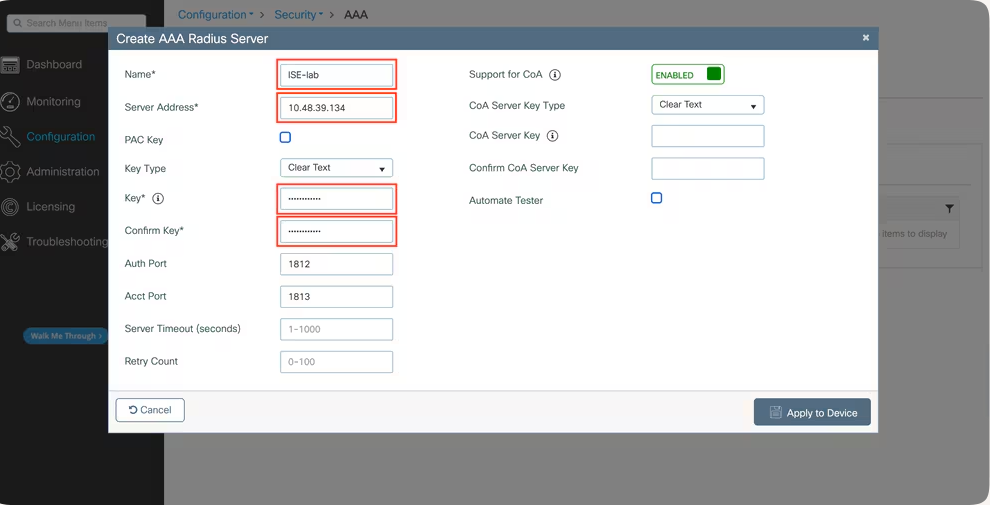
- Add ISE as RADIUS Server
- Security > AAA > RADIUS > Authentication
- Add ISE IP, shared secret (match in ISE).
- [Screenshot: WLC RADIUS Config]
- Create Guest WLAN
- WLANs > Create New > SSID:
Guest-WiFi - WLAN ID: 3
- [Screenshot: WLAN Creation]
- WLANs > Create New > SSID:
- Enable MAC Filtering for WebAuth
- WLAN > Security > Layer 2: None
- MAC Filtering: Enabled.
- Configure AAA Override
- WLAN > Advanced > Enable AAA Override (so ISE can push VLANs/dACLs).
- Configure Redirect ACL
- Security > Access Control Lists > Create ACL:
ACL-REDIRECT - Permit DNS, DHCP
- Deny all other traffic except redirect to ISE portal.
- [Screenshot: ACL Creation]
- Security > Access Control Lists > Create ACL:
- Bind WLAN to AAA Server and ACL
- WLAN > Security > AAA Servers: Set ISE as Authentication Server.
- WLAN > Security > Layer 3: Web Policy = Authentication + Redirection to ACL-REDIRECT.
Part B – Cisco ISE Configuration
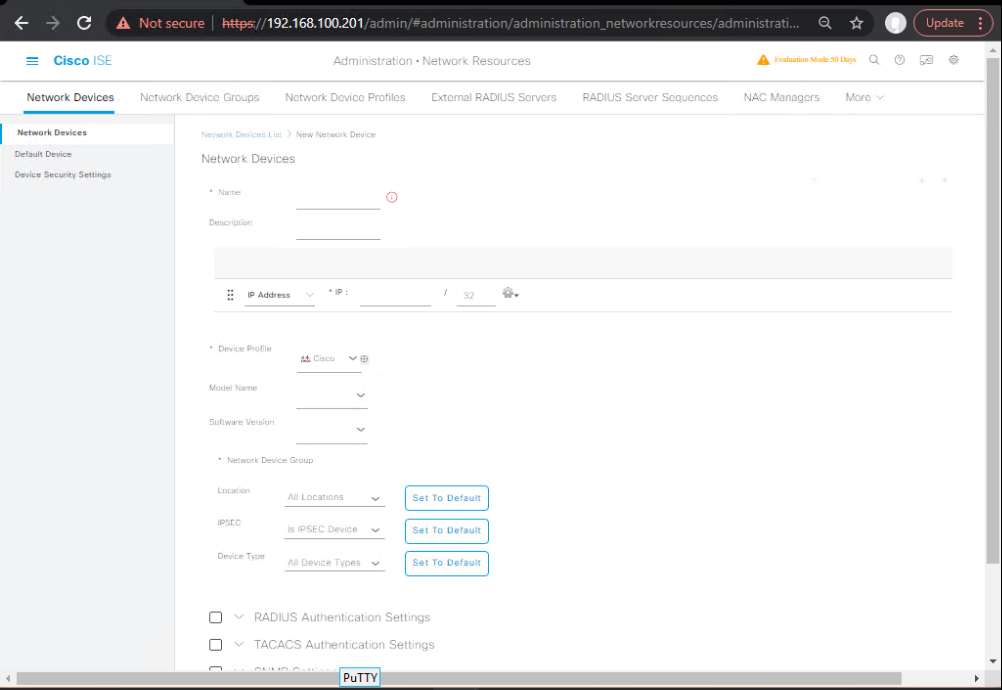
- Add WLC as Network Device
- Administration > Network Resources > Network Devices
- Add: WLC name, IP, shared secret.
- [Screenshot: Add Network Device]
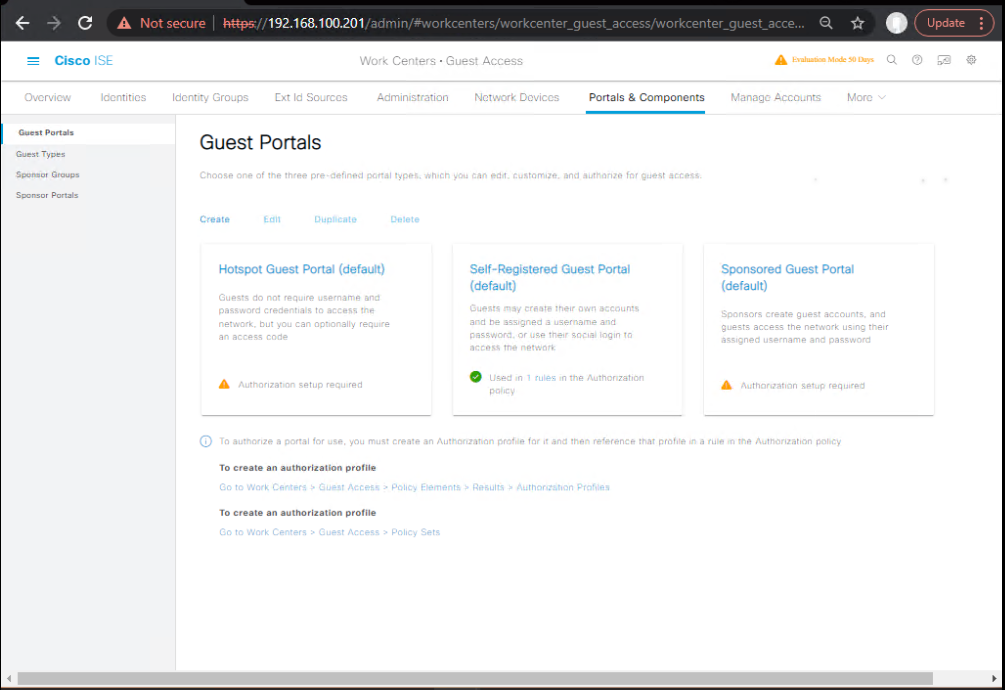
- Create Guest Portal
- Work Centers > Guest Access > Portals & Components > Guest Portals
- Select “Self-Registered Guest Portal” or “Sponsored Guest Portal”.
- Configure look & feel, expiry time, and credential delivery (email/SMS).
- [Screenshot: Portal Config]
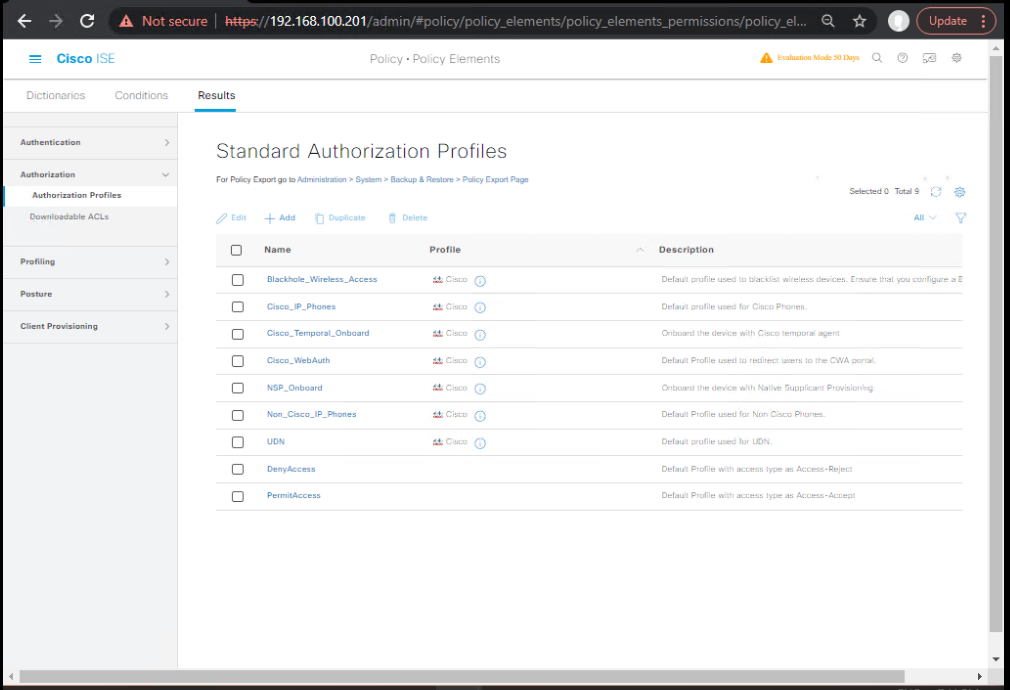
- Configure Authorization Profiles
- Policy > Policy Elements > Authorization Profiles
- Profile 1:
Guest-Redirect→ ACL = ACL-REDIRECT - Profile 2:
Guest-Access→ VLAN = Guest-VLAN (internet only).
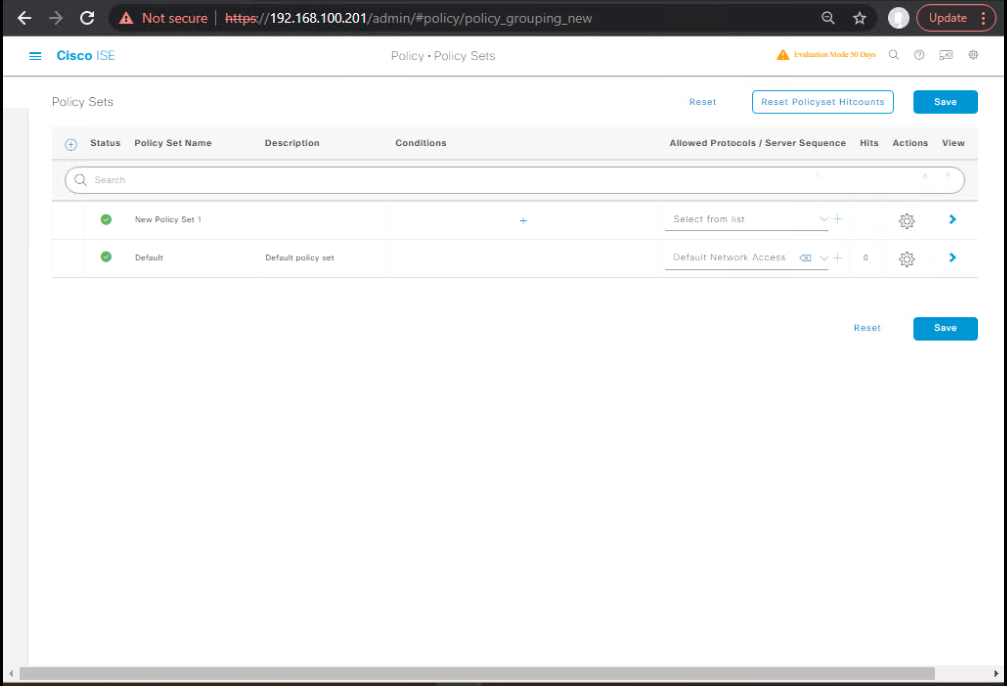
- Create Policy Set for Guest Flow
- Policy > Policy Sets
- New Set:
Wireless Guest Access - Authentication Policy: MAC Authentication against Internal Endpoints (guests start unknown).
- Authorization Policy:
- If Endpoint = Unknown → Apply
Guest-Redirect. - If Guest Authenticated → Apply
Guest-Access.
- If Endpoint = Unknown → Apply
- [Screenshot: Policy Set Screen]
Part C – Guest Flow Validation
- Guest Laptop Connection:
- Connect to SSID
Guest-WiFi. - Browser opens redirect page to ISE Guest Portal.
- Complete self-registration or sponsor approval.
- Connect to SSID
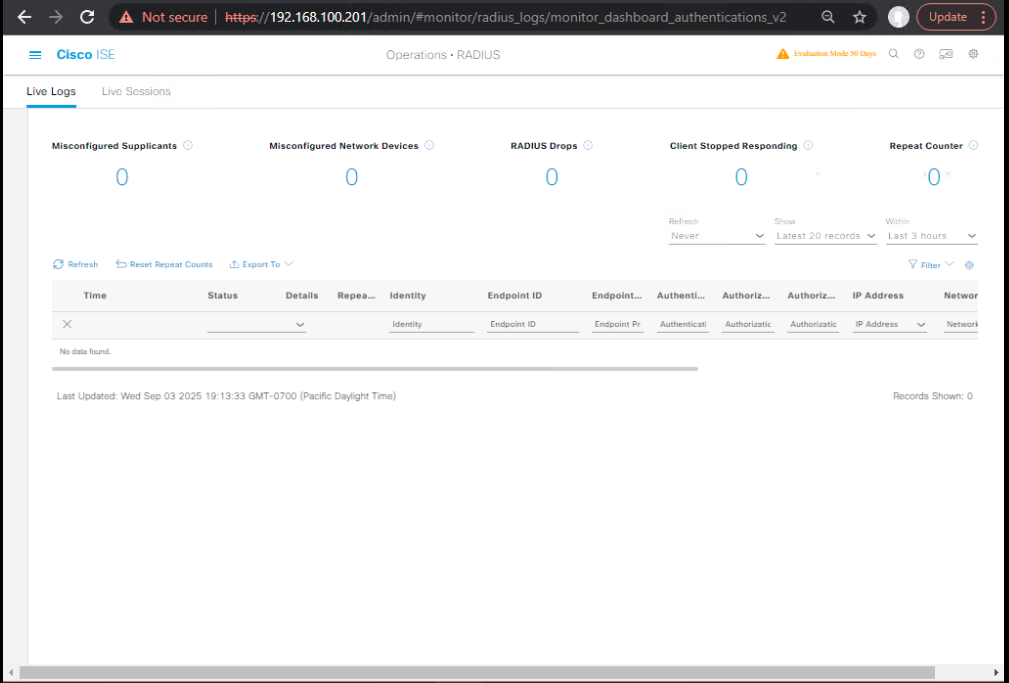
- ISE GUI Check:
- Operations > RADIUS > Live Logs — verify MAC auth → redirect → successful guest login.
- [Screenshot: ISE Live Logs]
- WLC CLI Check:
show client detail <MAC> show wlan summary show acl summary debug client <MAC> - Ping Test:
- After authentication, ensure internet access works.
- Verify no corporate subnet access.
FAQs for Wireless Guest Access Flow
1. Can I let guests self-register without sponsor approval?
Yes. In ISE’s Guest Portal settings, you can configure a Self-Registered Guest Portal that automatically approves accounts after registration, skipping sponsor intervention.
2. How do I ensure guests are completely isolated from corporate resources?
Place all guest devices in a dedicated Guest VLAN or apply a downloadable ACL (dACL) that only allows internet-bound traffic. Verify no routes exist between the guest network and corporate subnets.
3. Can I customize the guest portal with my company’s branding?
Yes. ISE supports full portal customization — you can upload logos, change colors, apply custom CSS, and even modify HTML to match your corporate branding.
4. What encryption should I use for the Guest SSID?
Many deployments use an open SSID with HTTPS redirect for ease of use, but WPA2/WPA3 encryption is more secure and prevents data sniffing before portal login.
5. Can I limit how many devices a guest can connect?
Yes. Under the portal configuration, set a Device Registration Limit per account. Once reached, new devices cannot log in with that account unless old ones are removed.
6. How do I handle expired guest accounts?
ISE automatically disables expired accounts. Guests attempting to reconnect are redirected back to the portal to re-register or request new credentials.
7. Can I pre-create guest accounts for a conference or large event?
Yes. ISE allows bulk account creation in the Guest Management section. You can export credentials to a CSV, print them, or email them to attendees.
8. What if a guest tries to bypass the portal by setting a static IP?
They will still be blocked because the redirect ACL on the WLC prevents any traffic except DHCP/DNS and HTTP/HTTPS to the ISE portal until authentication is complete.
9. Can I integrate social media logins for guests?
Yes. ISE supports OAuth integration with platforms like Facebook, Google, and LinkedIn, allowing guests to authenticate using their social accounts.
10. Does ISE log guest activity?
ISE logs authentication and session details (who connected, when, from where). For detailed browsing history, integrate your guest VLAN with a firewall or proxy server for deeper logging.
YouTube Link
For more in-depth Cisco ISE Mastery Training, subscribe to my YouTube channel Network Journey and join my instructor-led classes for hands-on, real-world ISE experience
Closing Notes
Wireless Guest Access in Cisco ISE is more than a splash page — it’s a controlled, secure, and accountable onboarding flow for non-corporate devices. By integrating WLC, ISE, and optional sponsor workflows, you deliver fast, user-friendly access while keeping your internal network safe.
Upgrade Your Skills – Start Today
Stop just reading about Cisco ISE and start building enterprise-grade NAC solutions in real labs.
I run a focused 4-Month CCIE Security Instructor-Led Training that takes you from zero to deploying advanced Cisco Security solutions — including ISE NAC, Firewalls, VPNs, and Threat Control — just like in Fortune 500 environments.
You’ll Get:
- Live interactive classes
- Full lab access in EVE-NG
- Real-world case studies & configs
- Lifetime recordings & reference material
- Career mentorship from an industry expert
Secure your spot now → https://course.networkjourney.com/ccie-security/ and join engineers who’ve transformed their careers with hands-on training.
Enroll Now & Future‑Proof Your Career
Email: info@networkjourney.com
WhatsApp / Call: +91 97395 21088


![AAA Authentication with TACACS+ and RADIUS – Step-by-Step Cisco Guide [CCNP ENTERPRISE]](https://networkjourney.com/wp-content/uploads/2025/07/nj-blog-post-AAA-TACACS-RADIUS.jpg)
![[Day 7] Cisco ISE Mastery Training: Configuring Certificates (Self-Signed & CA-Signed)](https://networkjourney.com/wp-content/uploads/2025/08/Day-7-Cisco-ISE-Mastery-Training-Configuring-Certificates-Self-Signed-CA-Signed.png)