[Day 48] Cisco ISE Mastery Training: BYOD Wireless Onboarding Overview
Table of Contents
Introduction
BYOD wireless onboarding in Cisco ISE delivers a secure, automated way to move unmanaged personal devices onto enterprise Wi-Fi using identity + certificates. Instead of static PSKs or manual Mac-whitelists, ISE provisions per-device EAP-TLS certificates, installs OS-native Wi-Fi profiles, enforces device limits & expiries, and gates access with central web auth (CWA) and authorization policy. You’ll implement a production-style BYOD flow that works across iOS/Android/Windows/macOS and validates cleanly in GUI + CLI.
Problem Statement
Real networks struggle with:
- Leaky PSKs / shared credentials across personal devices.
- No visibility into who is on Wi-Fi or what device they use.
- Weak segmentation (flat access) for unmanaged BYOD.
- Manual onboarding that doesn’t scale, no expiries, no device limits.
- Compliance gaps (no per-device identity or audit trail).
You need a zero-helpdesk workflow where users self-onboard, install a certificate, and land in the right role/VLAN/dACL—with logging, expiry, and revocation.
Solution Overview (What you will implement)
- Dual-SSID BYOD (recommended for labs):
- SSID #1 (Open):
BYOD-ONBOARD→ CWA redirect to BYOD Portal → profile + cert issuance. - SSID #2 (Secure):
CORP-SECURE→ EAP-TLS using the issued device certificate.
- SSID #1 (Open):
- Single-SSID BYOD (alt design): one SSID does CWA first; after CoA, the same SSID reauthenticates with EAP-TLS.
- ISE roles: BYOD Portal + Client Provisioning + SCEP proxy to a CA (e.g., MS NDES).
- Policy: Pre-auth redirect; post-provision allow; EAP-TLS = employee/BYOD authorization with VLAN/dACL.
- Controls: Device limit, account expiry, endpoint group tagging, revocation.
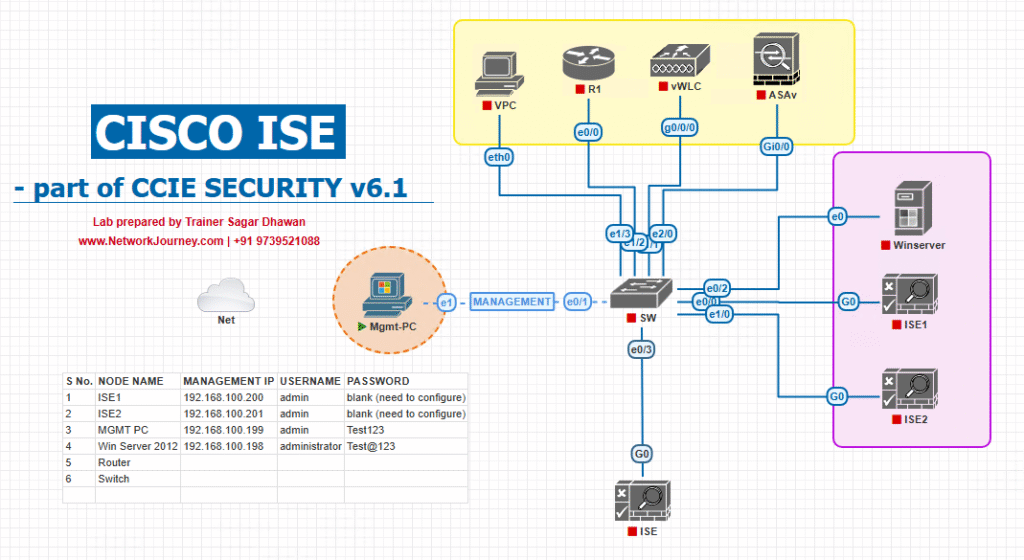
Sample Lab Topology
Software/VMs
- VMware/EVE-NG
- Cisco ISE 3.x (PAN/PSN in one VM for lab)
- WLC 9800-CL (or AireOS 8.10+)
- Windows Server 2019/2022 (AD DS + DNS + Enterprise CA + NDES/SCEP)
- Catalyst 9300 (or virtual L2)
- DHCP (on switch/Windows)
Endpoints
- iPhone/iPad (iOS/iPadOS), Android 10+, Windows 11, macOS.
Topology Layout:
Step-by-Step GUI Configuration Guide
PREREQS (do once)
- NTP/DNS consistent across ISE/WLC/AD/clients.
- ISE HTTPS cert trusted (public CA easiest for guests/BYOD).
- Enterprise CA + NDES (SCEP) installed & reachable from ISE.
- WLC registered as a Network Device in ISE with matching RADIUS secret.
- Decide Dual-SSID vs Single-SSID approach (we’ll build Dual-SSID, then note Single-SSID deltas).
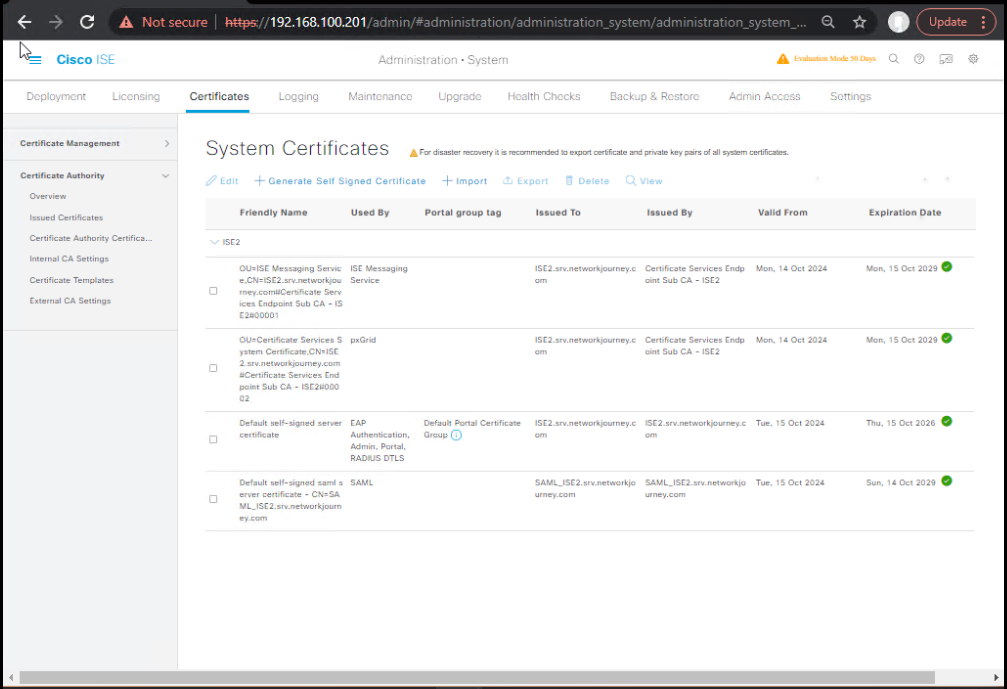
A) ISE – Integrate SCEP/CA for BYOD Certificates
- Add SCEP/NDES
- Administration > System > Certificates > Certificate Authority → Add
- Type: SCEP
- URL:
http(s)://<NDES-FQDN>/certsrv/mscep/ - RA/Challenge: Configure per your NDES setup.
- Templates: Select/enter the user/device cert template to issue for BYOD.
- [Screenshot: ISE SCEP Profile]
- Define Certificate Template Mapping
- Still under Certificate Authority, map Subject/SAN (e.g.,
SAN=RFC822Name = user email,OtherName/MAC, or device-ID). - [Screenshot: BYOD Cert Mapping]
- Still under Certificate Authority, map Subject/SAN (e.g.,
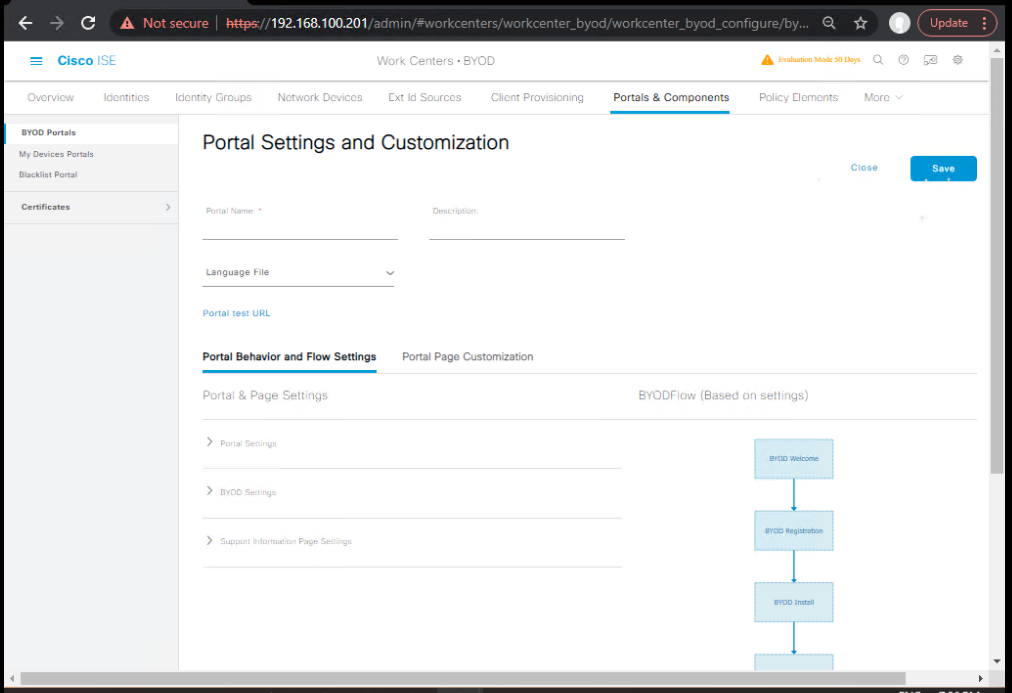
B) ISE – BYOD Portal & My Devices
- Create BYOD Portal
- Work Centers > BYOD > Portals & Components > BYOD Portals > Add
- Name:
BYOD-Portal - Auth Sources: AD/Internal Users as needed
- Enable “Device Registration”, “Device Limit”, “Expiry (e.g., 365 days)”
- Bind SCEP Profile created in (A).
- Branding: Logo/colors; add ToS + consent.
- [Screenshot: BYOD Portal Summary]
- My Devices Portal (optional but recommended)
- Work Centers > BYOD > Portals & Components > My Devices Portal → Enable
- Allow users to view/remove their registered devices.
- [Screenshot: My Devices Portal]
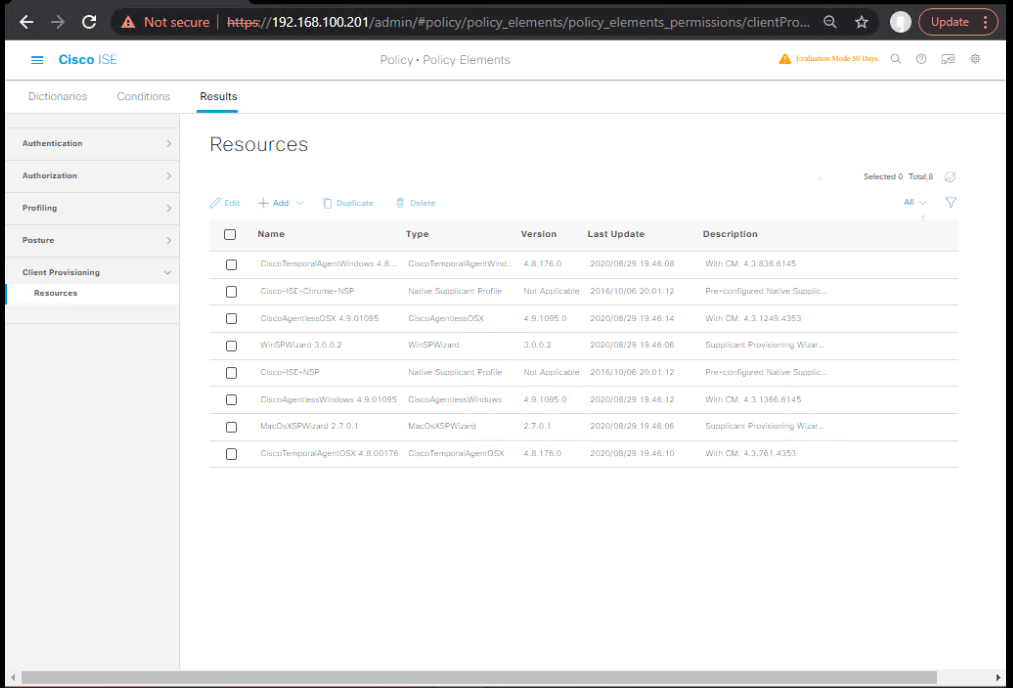
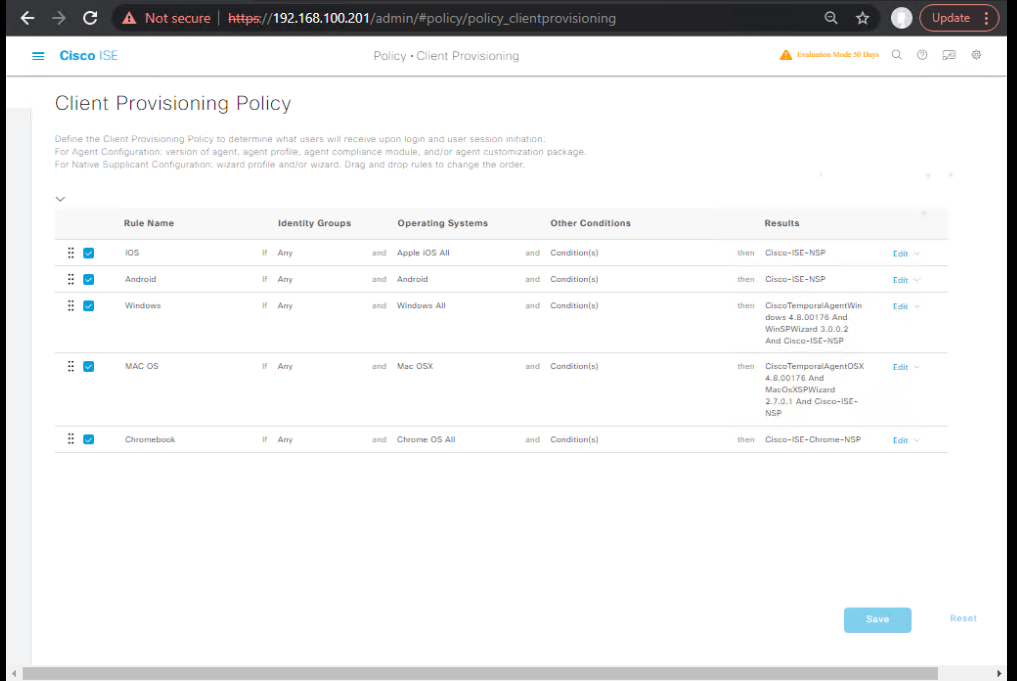
C) ISE – Client Provisioning (Native Supplicant Profiles)
- Create EAP-TLS Wi-Fi Profiles
- Policy > Policy Elements > Results > Client Provisioning > Resources → Add
- Type: Native Supplicant Profile (one per OS)
- iOS/macOS: SSID
CORP-SECURE/ EAP-TLS / install CA + client cert. - Android: SSID
CORP-SECURE/ EAP-TLS (note: user must allow cert install). - Windows 10/11: SSID
CORP-SECURE/ EAP-TLS, validate server cert.
- iOS/macOS: SSID
- [Screenshot: NSP per OS]
- Provisioning Policies
- Policy > Client Provisioning → Add rules per OS:
- Condition:
Device:OS = iOS→ Deliver iOS NSP + SCEP - Condition:
Device:OS = Android→ Deliver Android NSP + SCEP - …repeat for Windows/macOS.
- Condition:
- [Screenshot: Provisioning Policy]
D) ISE – Authorization Profiles & Policy Set (Dual-SSID)
- Pre-Auth Redirect (Onboarding SSID)
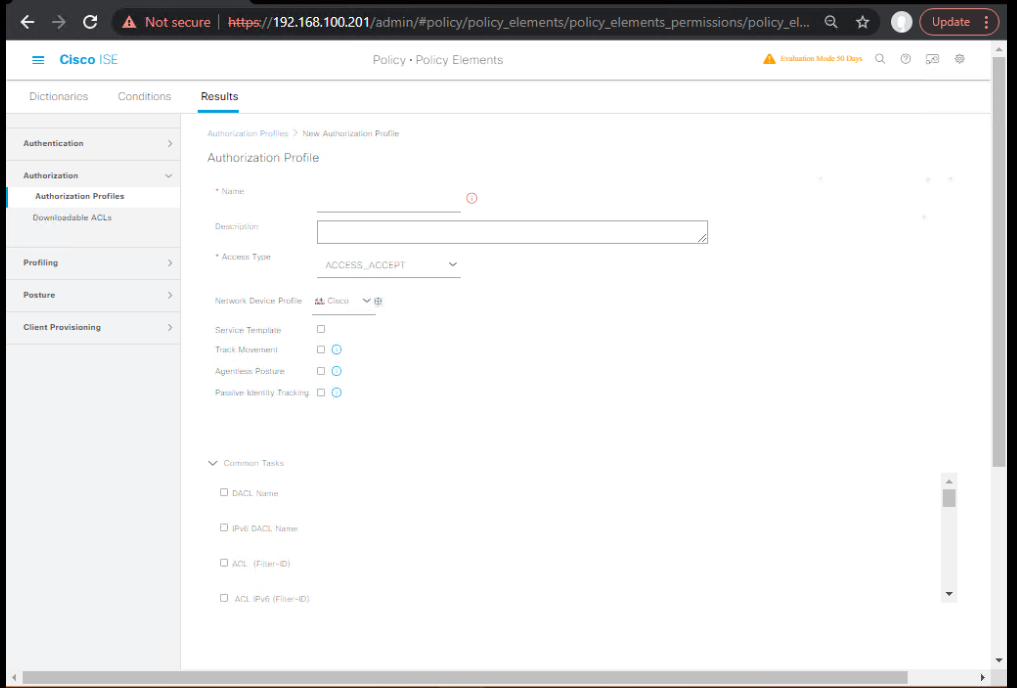
- Policy > Policy Elements > Results > Authorization > Authorization Profiles > Add
- Name:
BYOD-Redirect - Web Redirection: Centralized Web Auth → ACL:
ACL-BYOD-REDIRECT→ BYOD Portal - (Optional) dACL:
BYOD_PREAUTH_BASE(DNS/DHCP/Portal only)
- Name:
- [Screenshot: AuthZ Profile Redirect]
- Policy > Policy Elements > Results > Authorization > Authorization Profiles > Add
- Post-Provision (Onboarding SSID)
- Name:
BYOD-Registered-Quarantine(optional brief allow) - Minimal internet if you keep user on onboarding SSID; our recommended design forces switch to CORP-SECURE after provisioning.
- Name:
- Secure Access (CORP-SECURE SSID)
- Name:
BYOD-EAPTLS-Access - Match:
NetworkAccess:EapAuthentication EQUALS EAP-TLSANDCertificate:Issuer CONTAINS <Your CA>AND/OREndpoint Identity Group = BYOD-Registered - Result: VLAN =
EMP/BYOD, or dACLBYOD_CORP_ACCESS(L3 micro-seg). - [Screenshot: AuthZ Profile EAP-TLS]
- Name:
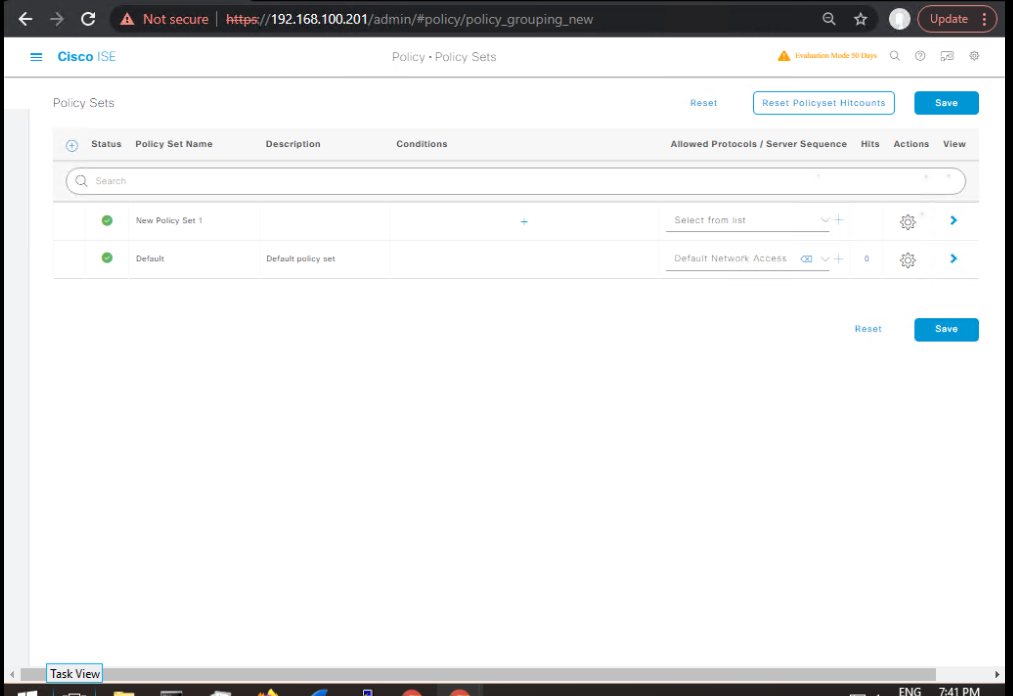
- Policy Set – “Wireless BYOD”
- Policy > Policy Sets > Add → Conditions:
Device Type = Wireless - Authentication Policy:
- MAB → Internal Endpoints (for CWA)
- 802.1X → AD/Cert as appropriate
- Authorization Policy (top-down):
- IF
SSID=BYOD-ONBOARDAND (UnknownORNotRegistered) → BYOD-Redirect - IF
RegisteredDeviceANDSSID=BYOD-ONBOARD→ (optional short allow or prompt to move) - IF
SSID=CORP-SECUREANDEAP-TLSANDIssuedBy=<CA>→ BYOD-EAPTLS-Access - ELSE → Deny/Quarantine
- IF
- [Screenshot: ISE Policy Set]
- Policy > Policy Sets > Add → Conditions:
E) WLC 9800-CL – SSIDs, ACLs, AAA
- Add ISE as RADIUS
- Configuration > Security > AAA > Servers > RADIUS → Add (auth+acct)
- [Screenshot: WLC RADIUS]
- Create Pre-Auth Redirect ACL (matches ISE profile name)
- Configuration > Security > ACL > Add (IPv4) → Name:
ACL-BYOD-REDIRECT - Permit: DHCP (67/68), DNS (53), ISE PSN (tcp/80,443)
- Deny: all else (implicit)
- [Screenshot: WLC ACL]
- Configuration > Security > ACL > Add (IPv4) → Name:
- Onboarding SSID (Open)
- Configuration > Tags & Profiles > WLANs > Add
- SSID:
BYOD-ONBOARD - Layer2: None, MAC Filtering: Enable (for MAB/CWA)
- AAA: Use ISE for AuthN/AuthZ/Acct
- Layer3: Web Auth ON → Pre-Auth ACL:
ACL-BYOD-REDIRECT→ Redirect URL: BYOD Portal URL (or let ISE push) - Policy Profile: Enable AAA Override
- SSID:
- [Screenshot: WLAN Onboard]
- Configuration > Tags & Profiles > WLANs > Add
- Secure SSID (EAP-TLS)
- WLAN SSID:
CORP-SECURE - Security > Layer2: WPA2-Enterprise (or WPA3-Ent) | AKM: 802.1X
- AAA: ISE as Auth/Acct; AAA Override enabled
- [Screenshot: WLAN Secure]
- WLAN SSID:
- Accounting
- Enable RADIUS accounting on both WLANs (profiling, session logs).
(AireOS: create WLANs, RADIUS, ACL, WebAuth redirect under Security > AAA/WebAuth; names must match.)
F) End-to-End Validation (GUI + CLI)
Expected Flow (Dual-SSID)
- Device joins
BYOD-ONBOARD→ WLC sends MAB → ISE returns BYOD-Redirect → browser gets BYOD Portal. - User authenticates (AD/guest), accepts ToS → Client Provisioning installs CA + client cert + Wi-Fi profile for
CORP-SECURE. - ISE issues CoA (or instructs user to join
CORP-SECURE). - Device joins
CORP-SECUREwith EAP-TLS → ISE returns BYOD-EAPTLS-Access (VLAN/dACL).
ISE GUI Checks
- Operations > RADIUS > Live Logs
- Entry 1: MAB → BYOD-Redirect (CWA) [Screenshot: Live Logs CWA]
- Entry 2: Client Provisioning success (OS matched policy) [Screenshot: CP Results]
- Entry 3: EAP-TLS success → BYOD-EAPTLS-Access [Screenshot: Live Logs EAP-TLS]
- Context Visibility > Endpoints → device shows Registered, Endpoint Group, Cert details [Screenshot: Endpoint Cert]
WLC CLI (9800)
show wlan summary show wireless client mac <client-mac> show access-lists summary show logging | inc Webauth|AAA|802.1X|EAP debug wireless mac <client-mac> events debug aaa all undebug all
AireOS CLI
show client detail <mac> show acl summary debug client <mac> debug aaa events enable debug web-auth redirect enable
AD/CA Validation
- CA MMC > Issued Certificates → confirm a cert for the user/device template.
- NDES logs (if troubleshooting SCEP).
Endpoint Validation
- Wi-Fi Profiles:
CORP-SECUREpresent, EAP-TLS configured. - Certificates: user/device cert + CA root installed.
- Connectivity: corp resources per dACL/VLAN policy; internet OK.
G) Single-SSID BYOD (What changes)
- Only one SSID (e.g.,
CORP-SECURE). - Initial CWA on that SSID → device gets cert + profile for the same SSID → CoA → client automatically reauths via EAP-TLS on the same SSID.
- WLC config: same SSID has WebAuth (pre-auth) and 802.1X; ISE policy must carefully distinguish pre-CWA vs post-EAP-TLS conditions.
- Validate that URL-Redirect ACL permits portal and SCEP flows.
FAQs for BYOD Wireless Onboarding
1. What’s the difference between BYOD onboarding and normal wireless authentication?
In normal wireless authentication, devices use pre-shared keys or certificates without an automated provisioning process. In BYOD onboarding, ISE automatically provisions device certificates, configures supplicants, and registers the device for ongoing secure access.
2. Does BYOD onboarding require an MDM?
Not necessarily. Cisco ISE can handle onboarding without an MDM, but for posture/compliance checks, an MDM integration (e.g., Intune, MobileIron, AirWatch) is often recommended.
3. Can onboarding work for both corporate and personal devices?
Yes. Policies can differentiate between devices by ownership. Corporate devices can skip onboarding if pre-configured, while personal devices can be routed through onboarding.
4. How is the device identified during onboarding?
ISE primarily uses the device MAC address and profiling attributes (OS type, browser agent) to identify and track the device in the Endpoint database.
5. Is a separate SSID required for BYOD onboarding?
Best practice is to have a dedicated Open SSID for onboarding, which redirects users to the onboarding portal. After provisioning, the device connects to the secure WPA2/WPA3-Enterprise SSID.
6. Can BYOD onboarding support non-802.1X devices?
Not directly. BYOD onboarding is built for 802.1X-capable devices (Windows, macOS, iOS, Android). Non-802.1X devices should use MAC Authentication Bypass (MAB) or a guest-like registration process.
7. What happens if a user deletes the onboarded SSID from their device?
The user will need to repeat onboarding so the configuration profile (including certificate and 802.1X settings) is reinstalled.
8. Can the onboarding portal be customized with company branding?
Yes. The portal pages are fully customizable with logos, colors, and text under Work Centers > BYOD in ISE.
9. How can I verify onboarding was successful?
Check:
- Operations > Live Logs in ISE for a successful EAP-TLS or EAP-PEAP session post-onboarding.
- WLC CLI
show client detail <MAC>for correct VLAN/SSID assignment. - Certificates > Endpoint Certificates in ISE for the provisioned certificate.
10. What’s the fallback if onboarding fails mid-process?
ISE can be configured to fall back to limited access (guest VLAN or remediation VLAN) and display troubleshooting instructions to the user.
YouTube Link
For more in-depth Cisco ISE Mastery Training, subscribe to my YouTube channel Network Journey and join my instructor-led classes for hands-on, real-world ISE experience
Closing Notes
You built a repeatable BYOD pipeline: CWA ➜ profile + cert ➜ EAP-TLS ➜ segmented access—backed by device limits, expiry, and revocation. This is the secure baseline for personal devices at scale. Keep your CA/NDES healthy, ACLs tight, policies explicit, and always validate EAP-TLS hits in ISE Live Logs.
Upgrade Your Skills – Start Today
Build this in production with expert oversight—land interviews with a deployable BYOD portfolio.
Join a 4-Month Instructor-Led CCIE Security & ISE Mastery:
- Live, hands-on NAC/BYOD/SGT/pxGrid deep dives
- EVE-NG lab topologies, workbooks, graded checklists
- Certificate/SCEP integrations, WLC 9800 enterprise designs
- Lifetime recordings, career mentorship, mock interviews
Lead Magnet: Grab the BYOD Runbook Pack (dACL templates, WLC/ISE snippets, RCA checklist).
Claim your seat & syllabus: https://course.networkjourney.com/ccie-security/
(Enroll today to receive the runbook pack + orientation lab files)
Enroll Now & Future‑Proof Your Career
Email: info@networkjourney.com
WhatsApp / Call: +91 97395 21088
![[Day 48] Cisco ISE Mastery Training: BYOD Wireless Onboarding Overview](https://networkjourney.com/wp-content/uploads/2025/08/Day-48-Cisco-ISE-Mastery-Training-BYOD-Wireless-Onboarding-Overview.png)


