[Day 49] Cisco ISE Mastery Training: Configuring BYOD Portal in ISE
Table of Contents
Introduction
The BYOD Portal in Cisco ISE converts unmanaged personal devices into identity-bound, certificate-based endpoints that can safely use enterprise Wi-Fi. The portal handles user authentication, device registration, supplicant/profile install, and certificate issuance (via SCEP/NDES), then flips the session to EAP-TLS with correct VLAN/dACL—hands-off for IT, predictable for security.
Problem Statement
Real networks hit these walls:
- Shared PSKs and leaked credentials across personal devices
- No per-device identity, no expirable access, weak segmentation
- Manual onboarding that doesn’t scale (and breaks audits/compliance)
- Inconsistent device experiences across iOS/Android/Windows/macOS
You need a self-service, certificate-driven onboarding flow that is repeatable, auditable, and OS-aware.
Solution Overview (What you will build)
- Dual-SSID BYOD:
BYOD-ONBOARD(Open + Redirect) → BYOD Portal → install CA + client cert +CORP-SECUREprofileCORP-SECURE(802.1X EAP-TLS) → policy-driven access (VLAN/dACL)
- ISE roles: BYOD Portal, Client Provisioning, SCEP proxy to Enterprise CA (NDES)
- MAC/device registration, device limits, auto-expiry, revocation
- Live Logs + WLC/ISE CLI to validate each hop
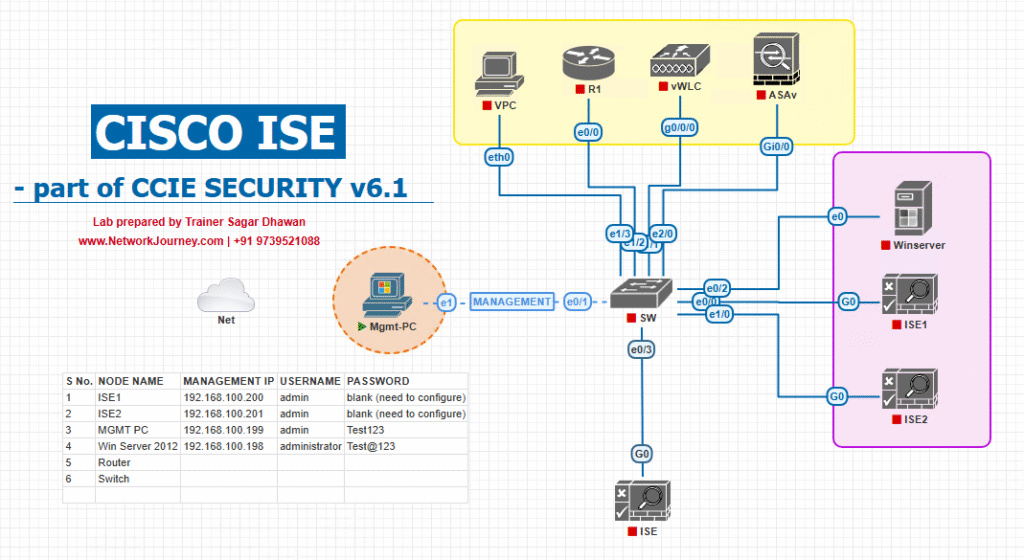
Sample Lab Topology (Text + Diagram)
Platform
- VMware/EVE-NG
- Cisco ISE 3.x (single node for lab)
- Cisco WLC 9800-CL (or AireOS 8.10+)
- Windows Server 2019/2022: AD DS + DNS + Enterprise CA + NDES (SCEP)
- Catalyst 9300 (or virtual L2)
- DHCP on switch/Windows
- Endpoints: iOS/Android/Windows/macOS
Diagram:
Step-by-Step GUI Configuration Guide (with validation)
PREREQS (once)
- NTP/DNS consistent across ISE/WLC/AD/clients
- ISE HTTPS cert trusted by endpoints (public CA easiest)
- NDES/SCEP installed and reachable from ISE
- WLC added in ISE (Administration > Network Resources > Network Devices)
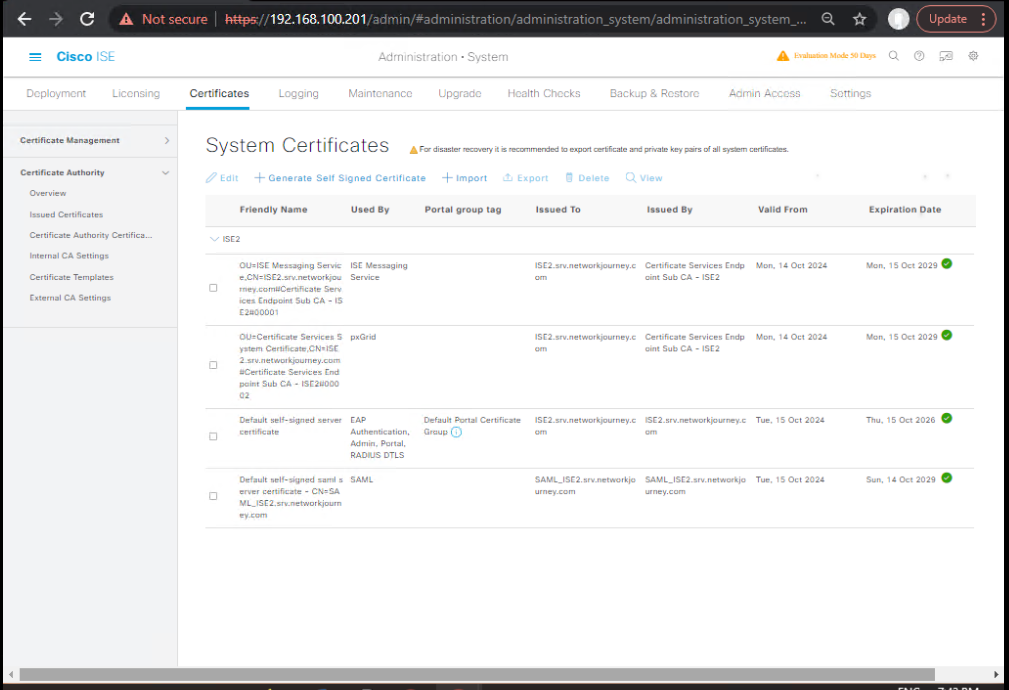
A) ISE — Add SCEP/NDES (CA Integration)
- Administration > System > Certificates > Certificate Authority > Add
- Type: SCEP
- URL:
http(s)://<NDES-FQDN>/certsrv/mscep/ - Challenge/RA: per NDES setup
- Template: your BYOD template (user/device)
- [Screenshot: ISE SCEP Profile]
- Map Cert Fields (Subject/SAN)
- Common:
SAN = RFC822Name (user email)and/or device identifiers - [Screenshot: SCEP Template Mapping]
- Common:
Validation
- On CA: MMC → Issued Certificates (should later show BYOD certs)
- Network reachability:
ping <NDES>from ISE CLI (if allowed)
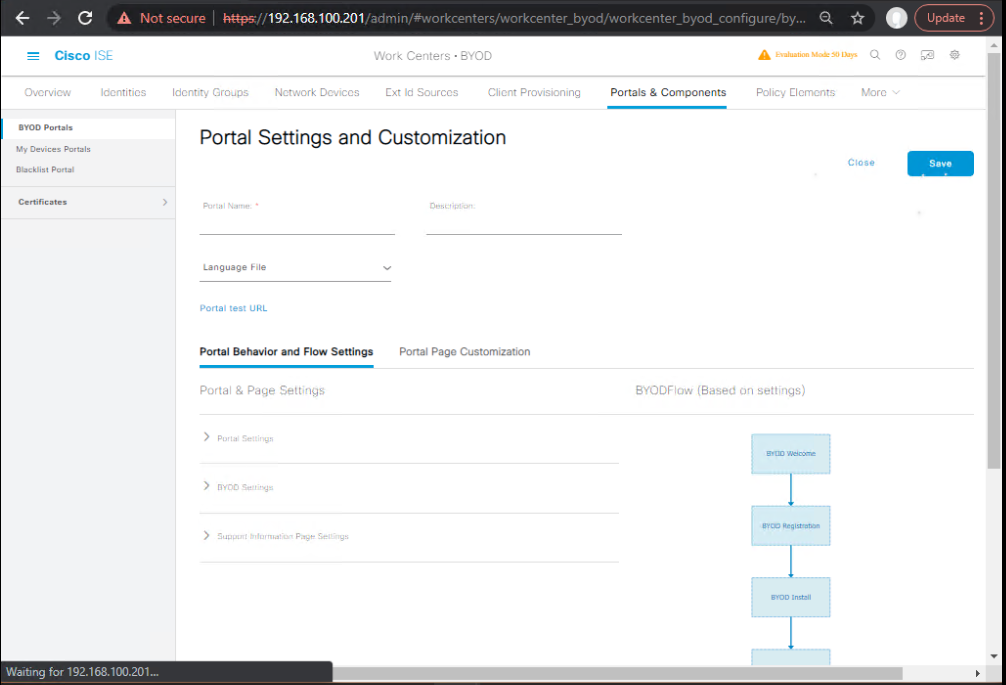
B) ISE — Create BYOD Portal
- Work Centers > BYOD > Portals & Components > BYOD Portals > Add
- Name:
BYOD-Portal - Identity Sources: AD / Internal Users
- Bind SCEP Profile from (A)
- Enable Device Registration, Device Limit (e.g., 2), Expiry (e.g., 365 days)
- Branding: logo, colors, ToS (must accept)
- [Screenshot: BYOD Portal Summary]
- Name:
- My Devices Portal (optional)
- Work Centers > BYOD > Portals & Components > My Devices Portal → Enable
- Lets users view/remove their own devices
- [Screenshot: My Devices Portal]
Validation
- Portal URL note for redirect
- Preview from Portal editor should render fine (no cert warnings)
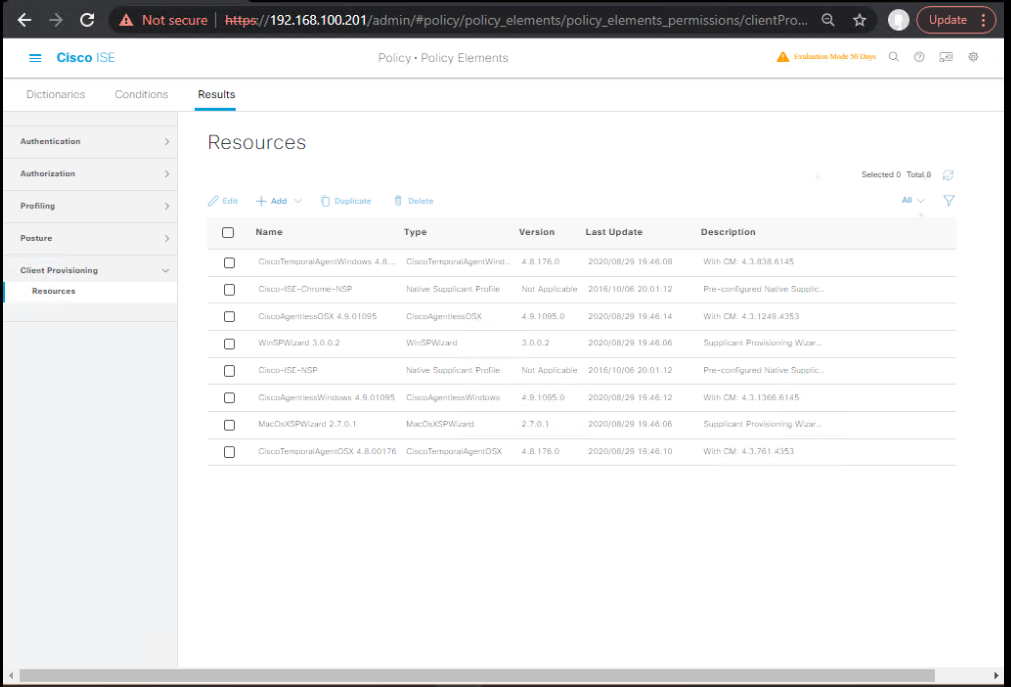
C) ISE — Client Provisioning (Native Supplicant Profiles)
- Policy > Policy Elements > Results > Client Provisioning > Resources > Add
- Type: Native Supplicant Profile (NSP)
- Create per OS:
- iOS/macOS: SSID
CORP-SECURE, EAP-TLS, trust ISE CA - Android: SSID
CORP-SECURE, EAP-TLS, user approval for cert - Windows 10/11: SSID
CORP-SECURE, EAP-TLS, server cert validate
- iOS/macOS: SSID
- [Screenshot: NSP per OS]
- Policy > Client Provisioning
- Add rules:
- If
OS = iOS→ iOS NSP + SCEP - If
OS = Android→ Android NSP + SCEP - If
OS = Windows→ Windows NSP + SCEP - If
OS = macOS→ macOS NSP + SCEP
- If
- [Screenshot: Client Provisioning Policy]
- Add rules:
Validation
- In a test run, the portal must present the correct OS package
D) ISE — Authorization Profiles & Policy Set
- Policy > Policy Elements > Results > Authorization > Authorization Profiles > Add
- Name:
BYOD-Redirect - Web Redirection (Centralized Web Auth): ACL =
ACL-BYOD-REDIRECT(must match WLC) - Portal: select
BYOD-Portal - (Optional) dACL
BYOD_PREAUTH_BASE(DNS/DHCP/HTTPS to ISE) - [Screenshot: AuthZ Profile Redirect]
- Name:
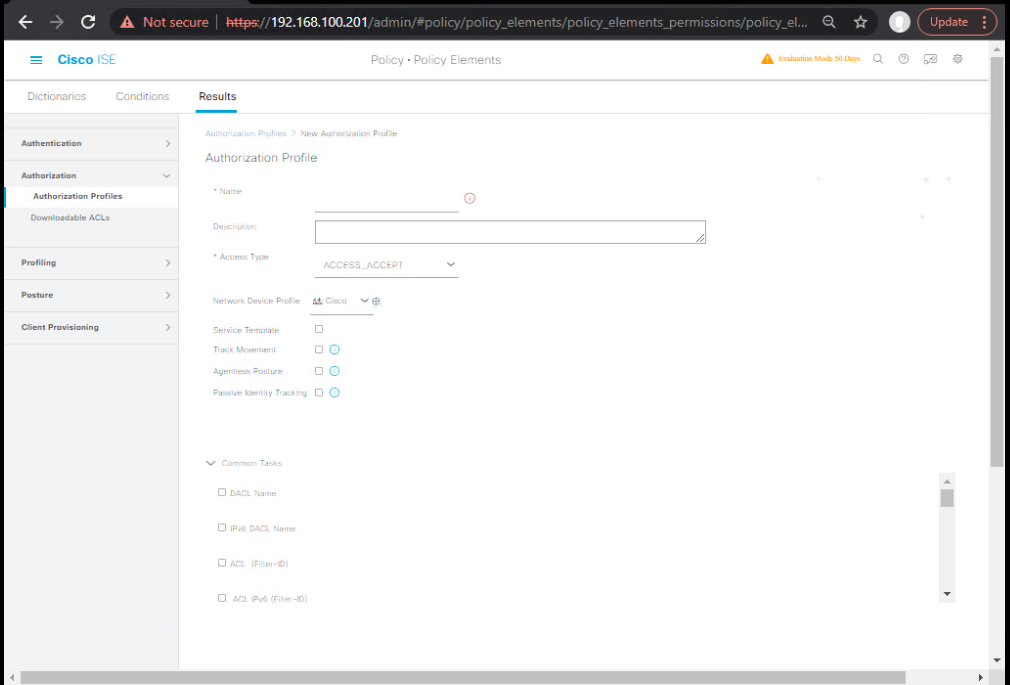
- Post-Provision / Secure Access
- Name:
BYOD-EAPTLS-Access - Condition later: EAP-TLS + Issuer=Your CA (or Endpoint Group=BYOD Registered)
- Result: VLAN
EMP-BYODor dACLBYOD_CORP_ACCESS - [Screenshot: AuthZ Profile EAP-TLS]
- Name:
- Policy > Policy Sets > Add → Name:
Wireless-BYOD- Conditions:
Device Type = Wireless(or NDG:WLC) - Authentication Policy:
- If MAB → Internal Endpoints
- If 802.1X → AD/certs as applicable
- Authorization Policy (top-down):
- IF
SSID = BYOD-ONBOARDANDUnknown(orUseCase = Guest/BYOD) → BYOD-Redirect - IF
SSID = CORP-SECUREANDEAP-TLSANDIssuer contains <Your CA>→ BYOD-EAPTLS-Access - ELSE → Deny/Quarantine
- IF
- [Screenshot: ISE Policy Set Screen]
- Conditions:
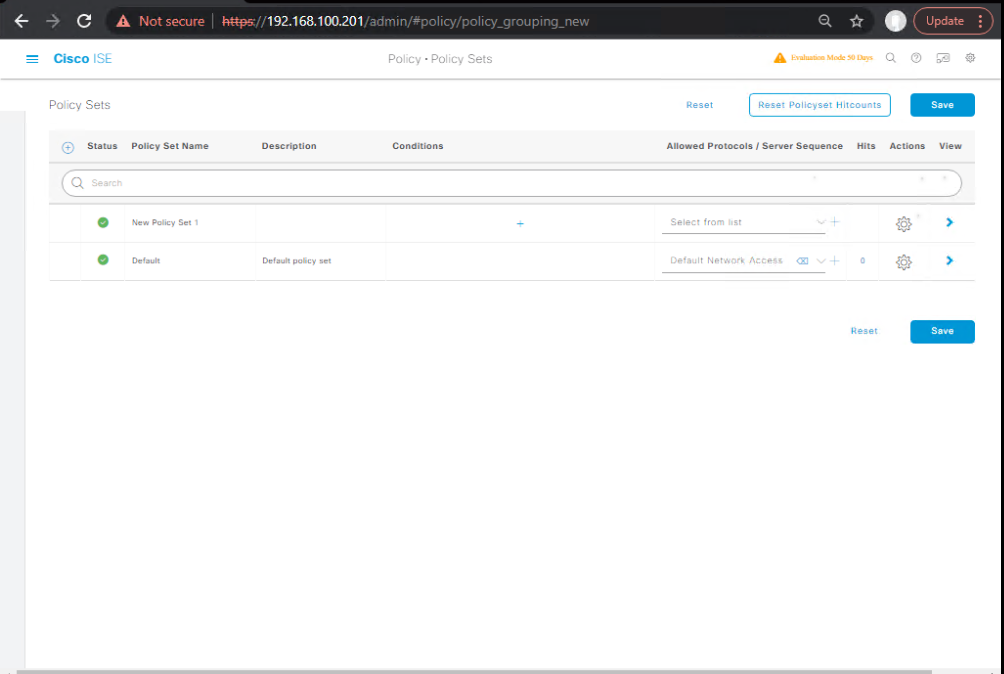
Validation
- Operations > RADIUS > Live Logs shows pre-auth redirect hit, then post EAP-TLS allow
E) WLC 9800-CL — AAA, ACL, WLANs
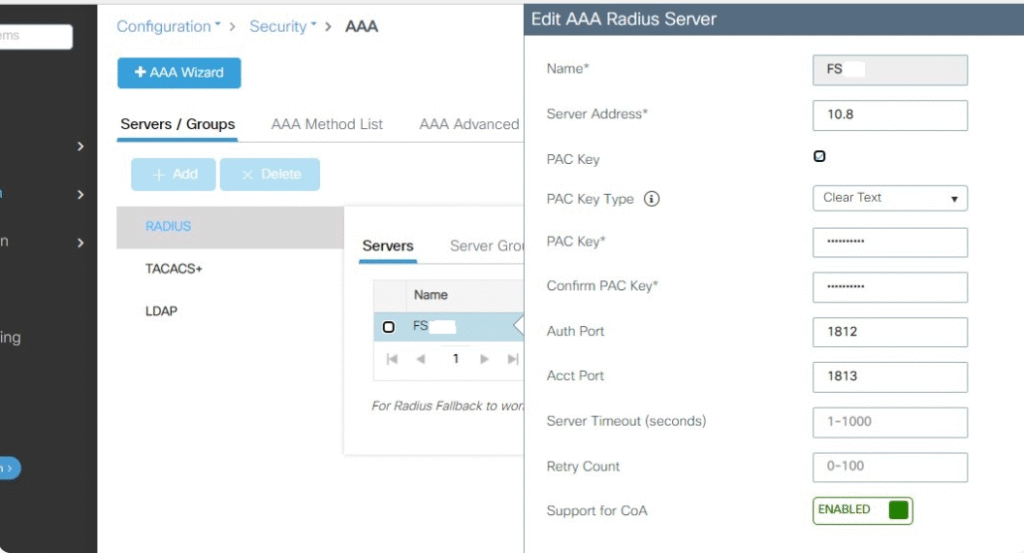
- Add RADIUS (ISE)
- Configuration > Security > AAA > Servers > RADIUS > Add
- AuthN + Accounting enabled
- [Screenshot: WLC RADIUS]
- Pre-Auth Redirect ACL
- Configuration > Security > ACL > Add (IPv4)
- Name:
ACL-BYOD-REDIRECT - Permit: DHCP (67/68), DNS (53), ISE PSN (tcp/80,443)
- Deny: all else (implicit)
- [Screenshot: WLC ACL]
- Onboarding SSID
- Configuration > Tags & Profiles > WLANs > Add
- SSID:
BYOD-ONBOARD - Layer 2: None (Open)
- MAC Filtering: Enable (for MAB/CWA)
- AAA: ISE for Auth/Acct; AAA Override enabled
- Layer 3: Web Auth ON → Pre-Auth ACL
ACL-BYOD-REDIRECT→ (or let ISE push URL) - [Screenshot: WLAN Onboard]
- Secure SSID
- SSID:
CORP-SECURE - Security > Layer2: WPA2/WPA3-Enterprise (802.1X)
- AAA: ISE Auth/Acct; AAA Override enabled
- [Screenshot: WLAN Secure]
- SSID:
AireOS equivalents: create RADIUS servers, WLANs, Pre-Auth ACL, WebAuth redirect under Security > AAA/WebAuth; ensure ACL/profile names match ISE.
F) End-to-End Validation (GUI + CLI)
Expected Path (Dual-SSID)
- Client joins
BYOD-ONBOARD→ WLC sends MAB → ISE returns BYOD-Redirect - Browser redirects to BYOD Portal → user auth → Client Provisioning installs CA + client cert +
CORP-SECUREprofile - ISE issues CoA or user switches SSID
- Client joins
CORP-SECUREwith EAP-TLS → ISE returns BYOD-EAPTLS-Access
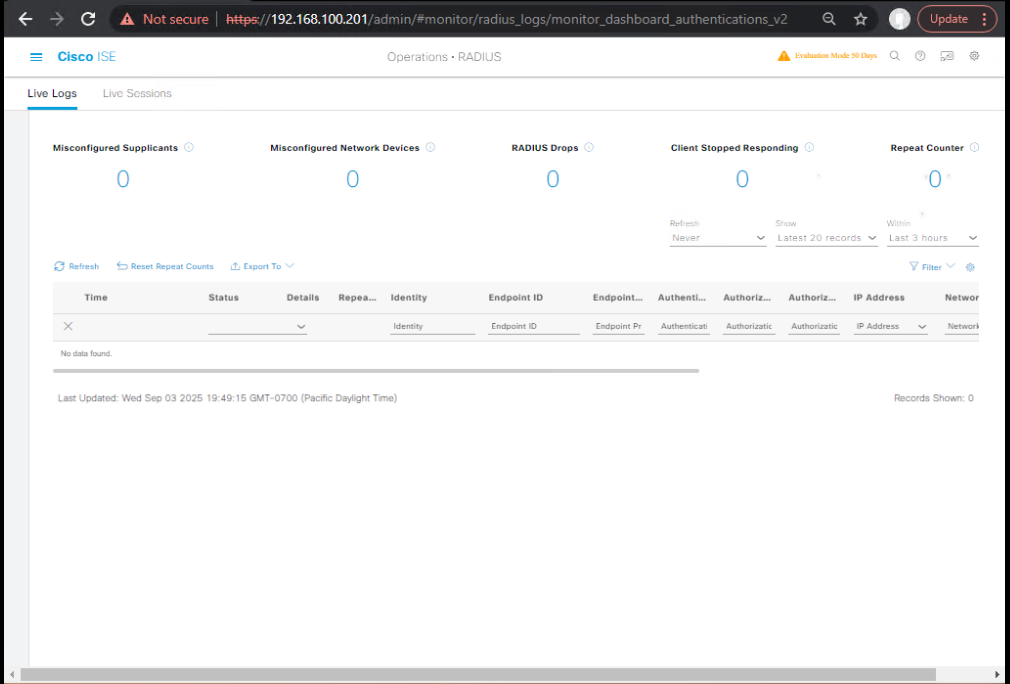
ISE GUI
- Operations > RADIUS > Live Logs
- 1st hit: MAB →
BYOD-Redirect(CWA) - 2nd: Client Provisioning success
- 3rd: 802.1X EAP-TLS →
BYOD-EAPTLS-Access - [Screenshot: ISE Live Logs Timeline]
- 1st hit: MAB →
- Context Visibility > Endpoints
- See device Registered, Endpoint Group, Cert details, last auth result
- [Screenshot: Endpoint Details]
WLC 9800 CLI
show wlan summary show wireless client mac <client-mac> show access-lists summary show logging | inc Webauth|AAA|802.1X|EAP|CoA debug wireless mac <client-mac> events debug aaa all undebug all
AireOS CLI
show client detail <mac> show acl summary debug client <mac> debug aaa events enable debug web-auth redirect enable
CA/NDES
- Issued Certificates: one appears for the user/device template
- If not, check NDES permissions and template issuance
Endpoint (device)
- Cert store: client cert + CA installed
- Wi-Fi profile:
CORP-SECUREpresent - Connectivity: Correct VLAN/dACL behavior
FAQs – Cisco ISE BYOD Portal
1) How does Cisco ISE differentiate between BYOD devices and corporate-managed devices?
ISE uses policy conditions such as Endpoint Group = BYOD-Registered or Certificate.Issuer = BYOD CA to classify devices. Corporate-managed devices might be pre-provisioned with a different certificate or enrolled via MDM, while BYOD devices go through the BYOD portal registration flow.
2) Do I have to integrate Microsoft NDES/SCEP for BYOD to work?
Not strictly—but without SCEP, you lose automated certificate provisioning, which means you’d have to manually install certs on each device. SCEP/NDES lets ISE provision unique client certs during onboarding, making EAP-TLS seamless.
3) Can I use a single SSID for BYOD onboarding and secure access?
Yes—this is the Single-SSID BYOD method, but it requires:
- Pre-auth redirect during onboarding (CWA)
- Post-onboarding CoA to trigger EAP-TLS on the same SSID
Dual-SSID is simpler for labs; single SSID offers a smoother user experience in production.
4) What happens if a BYOD device’s certificate expires?
The device will fail EAP-TLS authentication. The user must re-onboard via the BYOD portal, which will reissue a certificate. You can configure certificate expiry reminders and shorter device registration lifetimes to encourage clean re-enrollment.
5) How can I limit the number of devices a user can register?
Inside the BYOD Portal settings, set Maximum Devices per User (e.g., 2–3). ISE enforces this at onboarding—if a user tries to add a fourth device, they must delete an old one via the My Devices Portal.
6) What if my WLC redirect doesn’t work and users never see the BYOD portal?
Check:
- Pre-Auth ACL (must allow DNS, DHCP, ISE HTTPS)
- AAA Override enabled on the WLAN
- ACL name matches the one referenced in the ISE authorization profile
- ISE certificate trusted by the client’s browser
7) Can BYOD onboarding enforce MDM enrollment?
Yes—ISE can redirect devices to an MDM enrollment page before granting secure access. The MDM compliance check can be built into the BYOD flow, especially for corporate policy enforcement.
8) Is AnyConnect required for BYOD onboarding?
Not for Native Supplicant Provisioning (NSP). AnyConnect is optional for posture assessment or VPN. BYOD onboarding works with built-in supplicants on iOS, Android, Windows, and macOS.
9) How do I revoke a BYOD device’s access immediately?
You can:
- Revoke the certificate on the CA
- Delete the endpoint from ISE’s Context Visibility
- Remove it from My Devices Portal (self-service)
These actions block the device from passing EAP-TLS authentication.
10) How do I validate a successful BYOD onboarding in ISE?
Check:
- Live Logs: First CWA hit → Client Provisioning → EAP-TLS success
- Endpoint identity: Context Visibility → Endpoint → “BYOD-Registered” group
- Certificate presence: Device cert store contains valid client cert issued by your CA
- WLC CLI:
show wireless client mac <mac>confirms VLAN/dACL applied
YouTube Link
For more in-depth Cisco ISE Mastery Training, subscribe to my YouTube channel Network Journey and join my instructor-led classes for hands-on, real-world ISE experience
Closing Notes
You now have a repeatable BYOD portal workflow: CWA → Provision cert/profile → EAP-TLS → policy-driven access. Keep SCEP/NDES healthy, ISE cert trusted, redirect ACL minimal, and Live Logs as your first stop for RCA.
Upgrade Your Skills – Start Today
Turn this BYOD lab into a production-ready blueprint with expert guidance.
Join a 4-Month, Instructor-Led CCIE Security & ISE Mastery:
- Live NAC/BYOD/SGT/pxGrid deep dives
- EVE-NG topologies + graded lab workbooks & solution keys
- Real-world WLC 9800 + SCEP/NDES integrations
- Lifetime recordings, career mentorship, mock interviews
Lead Magnet for enrollees: “BYOD Runbook Pack” (dACL templates, WLC/ISE snippets, RCA checklists).
See the full syllabus & claim your seat: https://course.networkjourney.com/ccie-security/
Enroll Now & Future‑Proof Your Career
Email: info@networkjourney.com
WhatsApp / Call: +91 97395 21088



![[Day 6] Cisco ISE Mastery Training: Initial Setup Wizard & GUI Tour](https://networkjourney.com/wp-content/uploads/2025/08/Day-6-Cisco-ISE-Mastery-Training-Initial-Setup-Wizard-GUI-Tour.png)