[Day 54] Cisco ISE Mastery Training: Redirection for Non-Compliant Wireless Devices
Table of Contents
Introduction
In today’s enterprise networks, wireless access is no longer just a convenience—it’s mission-critical. But with convenience comes risk: not every device connecting to your Wi-Fi is secure, patched, or compliant with your corporate security policies.
A single non-compliant laptop with outdated antivirus or a BYOD smartphone lacking encryption can become the weakest link in your network security chain. This is exactly where Cisco Identity Services Engine (ISE) steps in with redirection for non-compliant devices—a powerful feature that doesn’t just block risky endpoints, but guides them toward compliance.
Think of it like airport security: if your bag triggers the scanner, you’re not thrown out of the airport—you’re redirected for further screening. Similarly, in ISE, non-compliant devices are transparently redirected to a remediation portal, where users are guided step-by-step to fix issues before gaining full network access.
In this Day 54 Cisco ISE Mastery Training, we’ll go beyond the theory.
You’ll learn exactly how to configure wireless redirection policies, integrate with posture assessment results, and validate the workflow both via ISE GUI and CLI commands on your WLC and endpoints.
By the end of this lesson, you’ll be able to:
- Detect and isolate non-compliant wireless clients in real-time.
- Redirect them to a custom compliance/remediation portal.
- Validate the posture check, authorization rules, and redirection ACLs step-by-step.
- Prove compliance before granting secure access.
This skill is non-negotiable for network security engineers, NAC specialists, and anyone preparing for CCNP Security, CCIE Security, or real-world ISE deployments.
Problem Statement
In a perfect world, every device connecting to your corporate Wi-Fi would be fully patched, encrypted, and equipped with the latest security controls.
In reality, network engineers face a very different picture:
- A visiting contractor’s laptop with no antivirus installed.
- An employee’s BYOD tablet running outdated OS software.
- A corporate laptop that failed the last posture update.
Each of these non-compliant wireless devices represents a potential entry point for malware, ransomware, or unauthorized data access. The stakes are even higher in industries where compliance frameworks (ISO 27001, HIPAA, PCI-DSS) mandate strict endpoint posture validation.
The real-world challenge?
- You can’t just block these users entirely—it breaks productivity and frustrates business units.
- You can’t give them unrestricted access either—that’s a security disaster waiting to happen.
- You need a controlled, automated way to detect, isolate, and guide them back into compliance without manual IT intervention.
Without an effective redirection and remediation process in place, IT teams face:
- Endless helpdesk tickets for connectivity issues.
- Shadow IT workarounds from frustrated users.
- A weakened security posture that can be exploited by attackers.
This is why wireless redirection for non-compliant devices in Cisco ISE is not just a nice-to-have—it’s a business-critical function for every modern enterprise network.
Solution Overview
Cisco Identity Services Engine (ISE) solves the non-compliant device problem by combining real-time endpoint posture assessment with dynamic access control to automatically quarantine risky devices and guide them toward remediation.
Here’s how it works step-by-step in a live wireless environment:
- Device Attempts to Connect to Wi-Fi
- The wireless client associates with the SSID and initiates 802.1X/EAP authentication or MAB (MAC Authentication Bypass).
- Posture Assessment via AnyConnect/Agent
- Cisco ISE triggers a posture scan using Cisco Secure Client (formerly AnyConnect).
- Checks include antivirus status, OS version, disk encryption, firewall status, or custom compliance rules.
- Non-Compliance Detection
- If the device fails any compliance check, ISE classifies it as non-compliant in real time.
- Dynamic Policy Application (DACL/VLAN Change)
- Instead of granting full network access, ISE pushes a Downloadable ACL (DACL) or moves the device to a remediation VLAN via the WLC.
- This VLAN has restricted internet access but allows connection to update servers, AV repositories, and patch management tools.
- Redirection to Remediation Portal
- ISE instructs the WLC to perform web redirection for HTTP/HTTPS traffic.
- The user is sent to a custom ISE web portal with clear instructions to update antivirus, apply OS patches, or enable required security settings.
- Automated Re-Assessment
- Once the user remediates their device, ISE automatically triggers a new posture check.
- If the device passes, ISE dynamically reassigns full access policies without IT manual intervention.
- End-to-End Logging & Reporting
- ISE maintains audit logs showing posture failures, remediation steps, and final compliance status — critical for security audits and compliance reporting.
Why this solution works:
- No manual IT ticketing — remediation is self-service.
- Prevents infected or outdated devices from accessing sensitive resources.
- Ensures continuous compliance, not just one-time checks.
- Fully integrates with Cisco WLC, switches, and security platforms for end-to-end NAC enforcement.
Sample Lab Topology
Lab Goal
To simulate Cisco ISE wireless posture assessment and HTTP/HTTPS redirection for non-compliant wireless devices, using a virtual lab setup that can be fully run on VMware Workstation, EVE-NG, or a hybrid physical-virtual environment.
Lab Components
- Cisco ISE Server
- Version: ISE 3.x (VM on VMware/EVE-NG)
- Roles: Policy Service Node (PSN), Administration Node (PAN)
- Functions: Posture policy, Web redirection portal, DACL assignment, reporting.
- Cisco Wireless LAN Controller (WLC)
- Version: 9800-CL (Cloud) in EVE-NG or 5508 physical.
- Functions: SSID broadcast, RADIUS redirection, VLAN change, ACL application.
- Access Point (AP)
- Mode: FlexConnect or Local Mode.
- Associated with WLC for SSID broadcast.
- Wireless Clients (Endpoints)
- Windows 10/11 VM (non-compliant posture for testing).
- Cisco Secure Client (AnyConnect) with Posture Module installed.
- Switch
- Optional — used for trunking AP traffic to WLC and ISE VM.
- DNS/DHCP Server
- Provides IP addresses to clients in remediation VLAN.
- DNS for portal redirection hostname resolution.
Logical Flow
- Client connects to Wi-Fi → Auth request sent to WLC.
- WLC → RADIUS Auth → Sent to Cisco ISE.
- ISE Posture Check → Result = Non-Compliant.
- ISE sends CoA (Change of Authorization) → WLC applies DACL or VLAN for remediation.
- Client HTTP/HTTPS traffic → Redirected to ISE Web Portal.
- Client remediates system → Posture recheck → Access restored.
Text Diagram Description
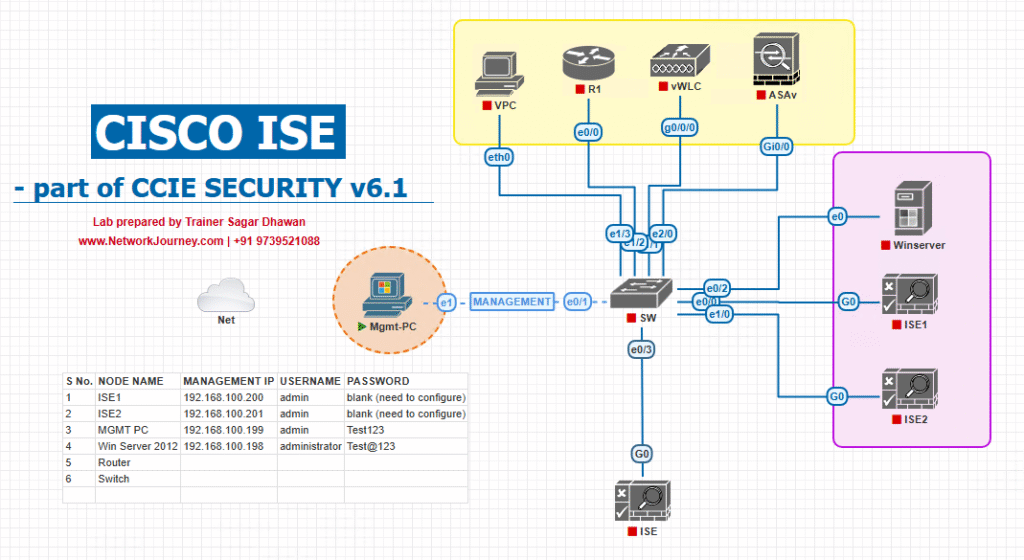
Key Lab VLANs:
- VLAN 10 – Corporate Access VLAN (Full Access)
- VLAN 20 – Remediation VLAN (Internet + AV/Update Servers only)
Key IPs:
- ISE: 192.168.10.10
- WLC: 192.168.10.20
- Client VLAN 10: DHCP scope 192.168.10.x
- Client VLAN 20: DHCP scope 192.168.20.x
Step-by-Step GUI & CLI Configuration Guide
Part 1 – Cisco ISE Configuration
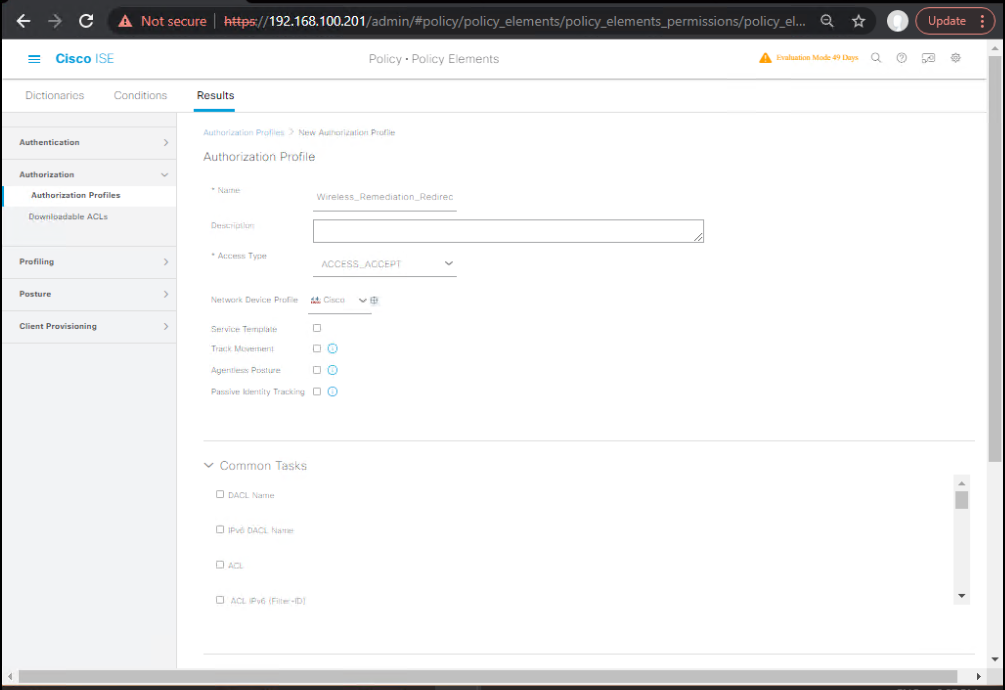
1. Create Authorization Profile for Redirection
- Navigate to Policy → Policy Elements → Results → Authorization → Authorization Profiles
- Click Add
- Name:
Wireless_Remediation_Redirect - Access Type:
ACCESS_ACCEPT - Common Tasks → Web Redirection (CWA, MAB, Posture) → Select
Posture - ACL Name: Enter the preconfigured ACL name on WLC (example:
ACL-REDIRECT) - Redirection URL: Automatically populated for posture portal.
- Save. [Screenshot: ISE Authorization Profile Creation Screen]
2. Create Posture Policy
- Navigate to Policy → Policy Elements → Conditions → Posture → Posture Policy
- Create new posture condition:
- Name:
AV_Not_Installed - Criteria:
AntiVirus Installed = False
- Name:
- Save. [Screenshot: ISE Posture Policy Condition Screen]
3. Define Authorization Policy Rules
- Go to Policy → Policy Sets → Wireless Policy Set
- Add a new rule before full access:
- Condition:
Wired_MAB/Wireless_MABANDPostureStatus = NonCompliant - Result:
Wireless_Remediation_Redirect(from Step 1)
- Condition:
- Save and deploy. [Screenshot: ISE Policy Set with Non-Compliant Rule]
4. Enable Client Provisioning Portal
- Navigate to Work Centers → Posture → Client Provisioning
- Ensure AnyConnect Compliance Module is uploaded and assigned to Windows/Mac.
- Save. [Screenshot: ISE Client Provisioning Portal Config]
5. Enable Policy Service Node (PSN) for Posture
- Navigate to Administration → System → Deployment
- Select your PSN → Enable Posture role.
- Save & Restart services.
Part 2 – Wireless LAN Controller (WLC) Configuration
6. Create Redirect ACL
CLI:
(WLC) > config acl create ACL-REDIRECT (WLC) > config acl rule add ACL-REDIRECT 1 permit tcp any host <ISE_IP> eq 8443 (WLC) > config acl rule add ACL-REDIRECT 2 permit tcp any host <ISE_IP> eq 8905 (WLC) > config acl rule add ACL-REDIRECT 3 deny ip any any
GUI:
- Security → Access Control Lists → Create ACL-REDIRECT
- Add permit rules for ISE portal ports (8443, 8905), deny all else. [Screenshot: WLC ACL Config]
7. Configure WLAN for Posture
- WLANs → Select SSID → Security → AAA Servers
- Assign ISE as RADIUS Auth & Accounting server.
- Security → Advanced → Enable RADIUS NAC.
- Save & Apply. [Screenshot: WLAN Security NAC Config]
Part 3 – Client & Validation
8. Client Connect Test
- Connect the wireless client to the SSID.
- ISE should mark it as Non-Compliant → Redirected to posture portal.
- AnyConnect Posture Module downloads/remediates. [Screenshot: Client Redirect Page]
9. Posture Re-Check
- Once the AV/firewall is installed → AnyConnect triggers posture recheck → ISE sends CoA → Client moved to full-access VLAN or DACL. CLI Validation:
ISE-PSN/admin# show logging application radius all ISE-PSN/admin# show posture-session all WLC# show client detail <MAC>
10. Final Access Test
- Ping internet sites.
- Access corporate resources.
- Verify ISE Live Logs: Status = Compliant, Authorization Profile = Full Access. [Screenshot: ISE Live Logs Posture Compliant]
FAQs
1. What is the main purpose of redirection in posture assessment?
Redirection temporarily limits a client’s access and forces them to a posture portal where they can install missing security software (e.g., AV, firewall, patches) before being granted full network access.
2. How does ISE decide which devices to redirect?
ISE evaluates the Posture Status returned by the AnyConnect Posture Module. If the device is marked as Non-Compliant, ISE applies an authorization profile containing a Redirect ACL and Posture Portal URL.
3. Is the Redirect ACL configured on ISE or WLC?
The Redirect ACL is created on the WLC (or switch for wired), but the name of this ACL must match exactly in the ISE authorization profile so it can be referenced dynamically.
4. Which ports must be allowed in the Redirect ACL for posture redirection to work?
At minimum:
- TCP 8443 → ISE portal
- TCP 8905 → NAC agent communication
- TCP/UDP 53 → DNS resolution
- Optionally TCP 80/443 for remediation servers (AV updates, OS patches)
5. Do I need CoA (Change of Authorization) for posture redirection?
Yes. CoA is critical because once the client becomes compliant, ISE sends a CoA to the WLC to reauthorize the session and move the client from remediation to full access.
6. What’s the difference between CWA and Posture redirection?
- CWA (Central Web Authentication) is for guest onboarding, device registration, etc.
- Posture redirection is specifically for NAC posture compliance workflows.
7. Can I run posture redirection without AnyConnect?
For full posture checks (like AV presence, patch level), AnyConnect Posture Module is required. Without it, ISE can only use profiling and basic MAB/802.1X checks, not deep posture.
8. How do I troubleshoot if redirection isn’t happening?
- Check ISE Live Logs for matching policy set and authorization rule.
- Ensure Redirect ACL name matches exactly in ISE and WLC.
- Confirm PSN Posture role is enabled.
- Test with
show client detail <MAC>on WLC to see applied ACL.
9. What happens if the posture agent never reports compliance?
The device remains in the remediation VLAN/DACL indefinitely, only able to reach the posture portal and remediation resources until fixed or admin intervention.
10. Can posture redirection be combined with VLAN assignment or downloadable ACLs?
Yes. In fact, many enterprises combine VLAN assignment for remediation and DACLs for granular control until compliance is met.
YouTube Link
For more in-depth Cisco ISE Mastery Training, subscribe to my YouTube channel Network Journey and join my instructor-led classes for hands-on, real-world ISE experience
Closing Notes
You now have a closed-loop, user-friendly containment: non-compliant devices get just enough network to fix themselves and are forced to a helpful page. Once healthy, ISE CoA slides them into full access—measurable, repeatable, auditable.
Upgrade Your Skills – Start Today
Turn this lab into a production-grade, audit-ready posture & redirection rollout—guided by an expert.
Join 4-Month, Instructor-Led CCIE Security & Cisco ISE Mastery:
- Live builds: Wireless posture & redirection, BYOD, Guest/Sponsor, Profiling, dACL/SGT, pxGrid
- EVE-NG topologies, graded lab workbooks, solution keys
- Ready-to-use templates: Redirect ACLs, AuthZ rulebooks, CoA runbooks, Remediation playbooks
- Career mentorship, lifetime recordings, mock interviews
Wireless Redirection Pack
- Prebuilt WLC ACLs (
ACL-PREPOSTURE,ACL-REMEDIATE) - ISE Authorization Profiles (Unknown/Non-Compliant/Compliant)
- Validation checklists & common debug snippets
View the full syllabus & reserve your seat: https://course.networkjourney.com/ccie-security/
Enroll Now & Future‑Proof Your Career
Email: info@networkjourney.com
WhatsApp / Call: +91 97395 21088



