[Day 56] Cisco ISE Mastery Training: PEAP Wireless Authentication Configuration
Table of Contents
Introduction
In the enterprise wireless world, security is a game of trust — and trust starts with knowing exactly who is connecting to your network and proving they are who they claim to be. PEAP (Protected Extensible Authentication Protocol) with Cisco ISE is one of the most widely deployed 802.1X authentication methods because it strikes the perfect balance between security, scalability, and ease of deployment.
Unlike open SSIDs or pre-shared keys, PEAP uses a secure TLS tunnel between the endpoint and Cisco ISE, protecting user credentials (typically username/password) from prying eyes. Inside this tunnel, EAP-MSCHAPv2 verifies the identity of the user against your enterprise directory services — usually Microsoft Active Directory.
This method becomes invaluable in environments where:
- Deploying certificates to every device (EAP-TLS) is not yet feasible
- Corporate security policies demand encrypted authentication
- BYOD and mixed-OS environments need quick onboarding without compromising security
- Network access policies must dynamically adapt to who and what is connecting
In Cisco ISE, PEAP is not just about allowing access — it’s about controlled access. ISE can dynamically assign VLANs, apply ACLs, redirect users for posture checks, or block them entirely based on identity and device posture.
By the end of this lab, you’ll not only know how to configure PEAP on ISE and your Wireless LAN Controller (WLC), but you’ll also understand why each setting exists, how it impacts authentication flow, and how to validate success both in the GUI and via CLI debug commands. This is not theory — this is the exact same process used in live enterprise networks with thousands of wireless clients.
Problem Statement
Without a secure authentication framework, wireless credentials (especially plain MSCHAPv2 or PAP) are vulnerable to:
- Man-in-the-Middle Attacks
- Credential Harvesting (Evil Twin)
- Replay Attacks
Also, without central policy control, managing access for thousands of wireless users becomes unscalable — especially if you need group-based access, device-type restrictions, or dynamic access control lists.
Solution Overview
Cisco ISE solves this by:
- Acting as a RADIUS server to process PEAP authentications from the WLC
- Creating a secure TLS tunnel for username/password exchange (commonly EAP-MSCHAPv2 inside PEAP)
- Integrating with Active Directory or LDAP to verify user credentials
- Applying authorization policies dynamically — VLAN assignment, ACLs, session profiles — based on AD group membership or endpoint attributes
- Logging & reporting every authentication attempt for auditing
Sample Lab Topology
Lab Components:
- VMware Workstation / EVE-NG running:
- Cisco ISE (3.x)
- Cisco WLC (9800-CL or 3504 in VM)
- Cisco Catalyst Switch (L2 trunk to WLC & ISE)
- Windows Server (AD + DNS + DHCP)
- Wireless Clients (Windows 10 laptop, iOS/Android device)
Logical Diagram:
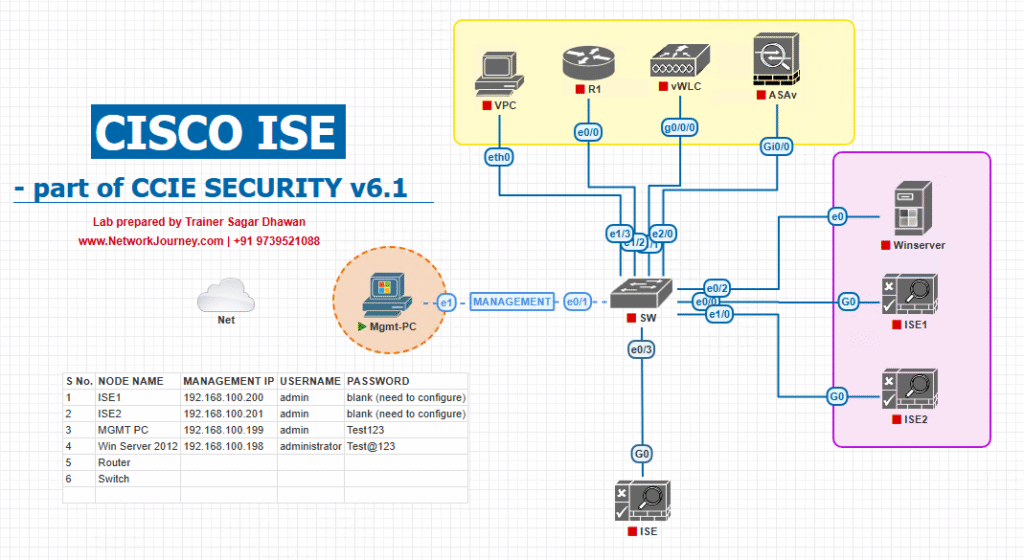
The WLC acts as the authenticator, passing RADIUS requests to ISE, which authenticates against AD and applies policy.
Step-by-Step GUI Configuration Guide
Step 1 – Configure Certificates in ISE
- Go to Administration > System > Certificates > System Certificates
- Import or generate a server certificate signed by your internal CA (CN = ISE FQDN)
- Ensure EAP Authentication is enabled for the certificate
- [Screenshot: ISE System Certificate with EAP checkmark]
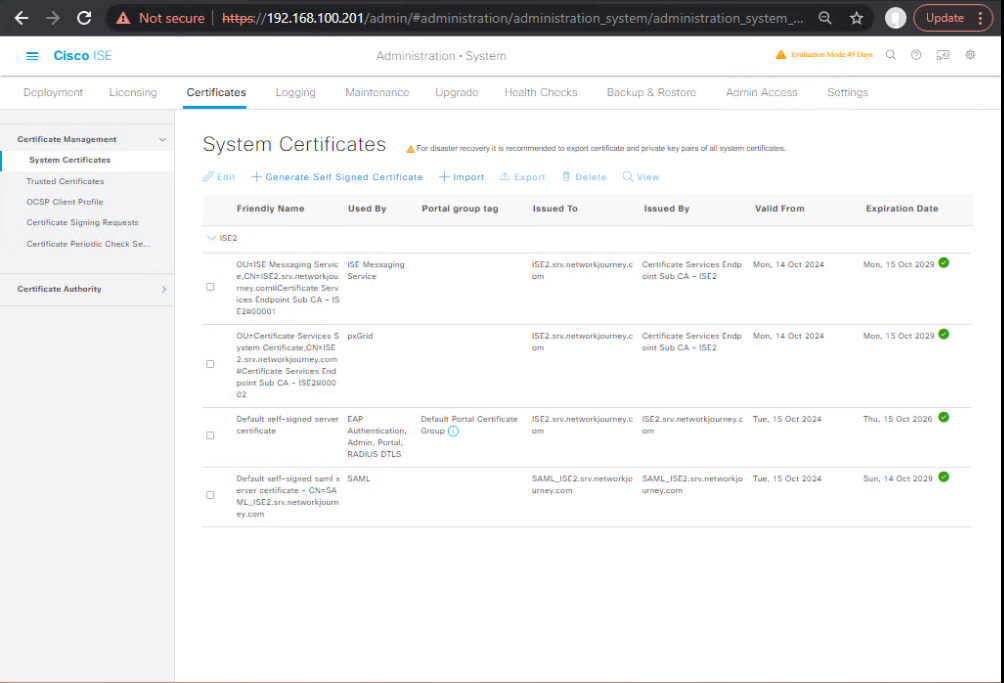
Step 2 – Integrate ISE with Active Directory
- Administration > Identity Management > External Identity Sources > Active Directory
- Join ISE to the domain using AD Admin credentials
- Select the AD Groups to be used for authorization policies
- [Screenshot: ISE AD Integration Screen]
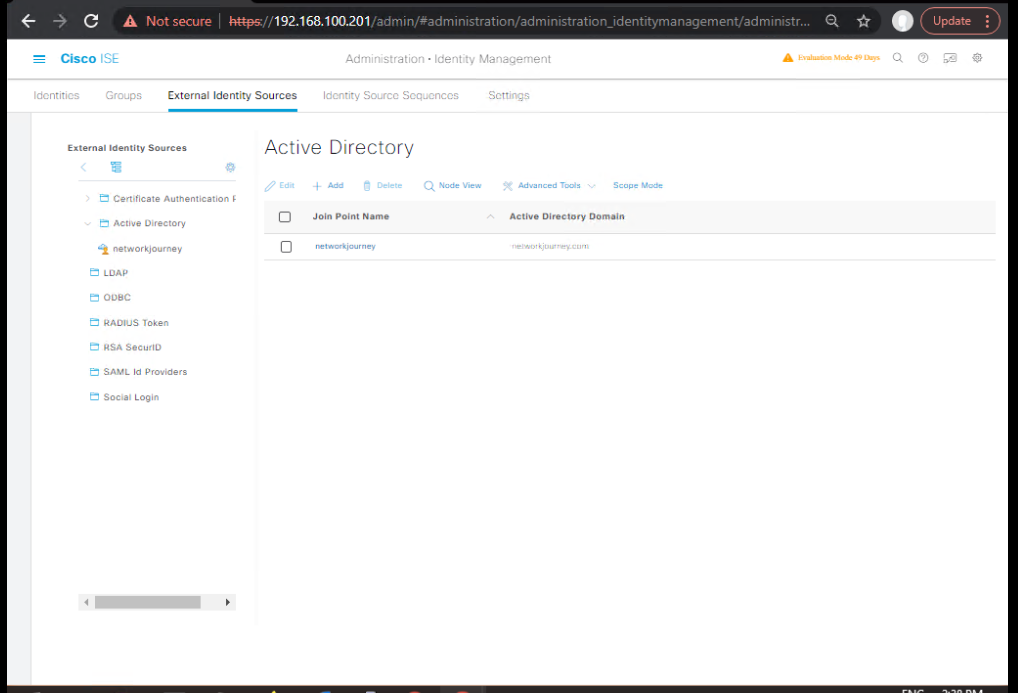
Step 3 – Enable PEAP in ISE
- Administration > System > Settings > Protocols > EAP
- Enable PEAP and select EAP-MSCHAPv2 as the inner method
- Bind it to the previously imported EAP certificate
- [Screenshot: ISE EAP Protocol Settings]
Step 4 – Create ISE Authentication Policy
- Policy > Policy Sets
- Create new Policy Set: Name = Wireless-PEAP, Condition =
DEVICE:WLC - Authentication Policy:
- If
Wireless_MAB→ use MAB identity source - If
Wireless_802.1X→ use AD for PEAP - [Screenshot: ISE Authentication Policy Set]
- If
Step 5 – Create ISE Authorization Policy
- Add rule: If AD group = Domain Users → PermitAccess (VLAN=Corporate)
- Add rule: If AD group = Guests → Redirect to Guest Portal
- [Screenshot: ISE Authorization Rules]
Step 6 – Configure WLC for PEAP
GUI Method (9800-CL):
- Configuration > Tags & Profiles > WLANs → Create new WLAN
- SSID: Corp-PEAP, WLAN ID: 1
- Security > Layer 2: WPA2-Enterprise, 802.1X enabled
- Authentication Server: ISE’s IP + Shared Secret
- [Screenshot: WLC WLAN Security Settings]
CLI Method:
wlan Corp-PEAP 1 Corp-PEAP security wpa wpa2 enable security 802.1X authentication-list ISE-RADIUS no shutdown
Step 7 – Test and Validate
GUI Validation (ISE):
- Operations > RADIUS > Live Logs → Check authentication result (should show “Access-Accept”)
- Expand details to verify PEAP-MSCHAPv2 inner method
CLI Validation (WLC):
show client summary show client detail <MAC> debug client <MAC>
Look for:
- TLS handshake success
- RADIUS Access-Accept
- Correct VLAN/ACL assignment
FAQs – PEAP Wireless Authentication in Cisco ISE
1. What is PEAP, and how is it different from EAP-TLS?
PEAP (Protected Extensible Authentication Protocol) uses a server-side certificate to create a secure TLS tunnel, but client devices authenticate with username/password (EAP-MSCHAPv2 inside the tunnel). EAP-TLS requires certificates on both the server and client, offering stronger security but with more administrative overhead.
2. Does PEAP require certificates on the client?
No — only the Cisco ISE server (and optionally the WLC if using mutual authentication) needs a certificate. The client must trust the server’s certificate authority (CA), which can be achieved by pre-installing the CA in the client’s trusted root store.
3. Which identity store can be used with PEAP in ISE?
PEAP can authenticate users against:
- Active Directory (most common)
- LDAP directories
- Internal ISE user database (lab/testing)
- External RADIUS servers
4. What ports and protocols must be allowed for PEAP?
You must allow:
- UDP 1812 (RADIUS authentication) and 1813 (RADIUS accounting) between WLC and ISE
- TCP/UDP 443 (GUI access to ISE for admin/portal)
- EAPOL (EtherType 0x888E) on the access layer
- Ensure there’s no firewall blocking RADIUS responses during the handshake
5. How can I verify PEAP authentication success in Cisco ISE?
In ISE GUI:
- Operations > RADIUS > Live Logs → Filter for the test client MAC or username
- Check for a “Authentication Succeeded” message
In CLI (on WLC):
debug client <MAC-address>
Look for the RADIUS Access-Accept and VLAN assignment or ACL application lines.
6. What is the most common reason for PEAP authentication failure?
The #1 cause is certificate trust issues — if the client does not trust the ISE server’s certificate CA, it will drop the connection before sending credentials. Another common cause is incorrect user credentials or domain mismatch when using AD.
7. Can I use PEAP for both corporate and guest wireless users?
Yes, but not in the same SSID unless you design conditional ISE policy sets to handle different identity groups. Typically, corporate users use PEAP with AD, while guests are redirected to a web portal instead.
8. How does PEAP protect user credentials?
The TLS tunnel encrypts the entire EAP conversation, so credentials are never sent in cleartext. Inside the tunnel, EAP-MSCHAPv2 securely challenges and validates the user password against the backend identity store.
9. How can I force clients to validate the ISE certificate?
On Windows: Enable “Validate server certificate” and specify the trusted root CA in the wireless profile.
On macOS/iOS: This is automatic if the CA is installed.
On Android: Requires importing the CA certificate or using an MDM to push wireless configs.
10. How can I test PEAP without a WLC in my lab?
You can simulate PEAP authentication using:
- EVE-NG or GNS3 with a virtual WLC (vWLC) and ISE
- A wired 802.1X lab with a switch in place of WLC (PEAP works the same at RADIUS level)
- The
eapol_testutility from the wpa_supplicant package to directly send EAP-PEAP requests to ISE
YouTube Link
For more in-depth Cisco ISE Mastery Training, subscribe to my YouTube channel Network Journey and join my instructor-led classes for hands-on, real-world ISE experience
Closing Notes
PEAP remains one of the fastest ways to roll out secure wireless authentication in environments where full PKI for EAP-TLS is not yet feasible. Cisco ISE’s tight integration with WLC and AD means you can easily scale PEAP authentication across thousands of users, with centralized policy enforcement, detailed reporting, and dynamic access control.
Fast-Track to Cisco ISE Mastery Pro
Ready to master Cisco ISE in real-world enterprise deployments?
Join 4-Month Instructor-Led CCIE Security Mastery Program — a hands-on, lab-intensive training covering Cisco ISE, ASA/FTD, VPN, SD-WAN, and more.
- Learn directly from a CCIE Security expert
- Lab every concept — from basic NAC to advanced EAP-TLS & posture
- Get career-ready skills with enterprise-grade configs
Limited seats → Reserve your seat now
Enroll Now & Future‑Proof Your Career
Email: info@networkjourney.com
WhatsApp / Call: +91 97395 21088



