[Day 57] Cisco ISE Mastery Training: Multi-SSID Wireless Integration
Table of Contents
Introduction
In today’s enterprise networks, a single SSID is rarely enough. Organizations often need multiple wireless networks (SSIDs) to segregate traffic and apply different security policies — for example, separating corporate devices, guests, IoT devices, and contractors.
However, without a central policy engine, managing authentication, VLAN assignments, and access rules for multiple SSIDs quickly becomes an administrative nightmare — leading to inconsistent security and poor user experience.
Cisco Identity Services Engine (ISE) changes the game by integrating with the Wireless LAN Controller (WLC) to manage multiple SSIDs from a single point of control, enabling you to:
- Assign different authentication methods per SSID
- Dynamically enforce VLANs, ACLs, or SGTs
- Apply posture checks and profiling
- Simplify operational management for wireless security
In this session, we will configure Cisco ISE for Multi-SSID Wireless Integration, lab-test the setup, and validate it with both GUI and CLI.
Problem Statement
The challenge:
When an organization deploys multiple SSIDs for different user groups:
- Security policies are hard to maintain across WLANs
- Manual VLAN mapping leads to misconfiguration risks
- Different authentication types (PEAP, EAP-TLS, MAB) require separate setups
- Guest onboarding becomes time-consuming and inconsistent
- Managing policies on both WLC and ISE independently causes duplication
We need a centralized NAC solution that ties all SSIDs together under a unified policy framework.
Solution Overview
Cisco ISE integrates with the WLC via RADIUS. Each SSID maps to a WLAN profile on the WLC, and ISE uses Policy Sets to identify the SSID and apply the right authentication & authorization rules.
In this lab:
- SSID CORP-WIFI → EAP-TLS with VLAN 20
- SSID GUEST-WIFI → WebAuth Redirect to Guest Portal VLAN 30
- SSID IOT-WIFI → MAC Authentication Bypass (MAB) VLAN 40
ISE dynamically instructs WLC which VLAN, ACL, or SGT to apply after authentication.
Sample Lab Topology
Environment:
- VMware / EVE-NG
- Cisco ISE 3.x (VM)
- Cisco vWLC (8.x or 9800-CL)
- Two 802.1X-capable APs (Lightweight mode in WLC)
- Test clients: Windows 10 (EAP-PEAP), Android (Guest), IoT device (MAB)
- L3 switch for VLAN routing (VLANs 20, 30, 40)
Diagram description:
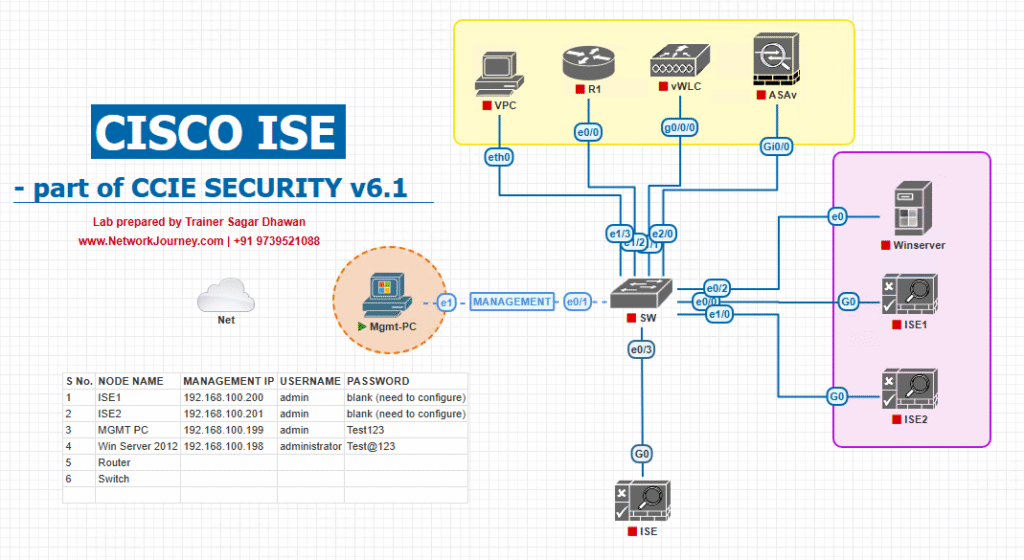
- RADIUS traffic between WLC and ISE
- VLAN assignment handled dynamically via RADIUS attributes
Step-by-Step GUI + CLI Configuration Guide
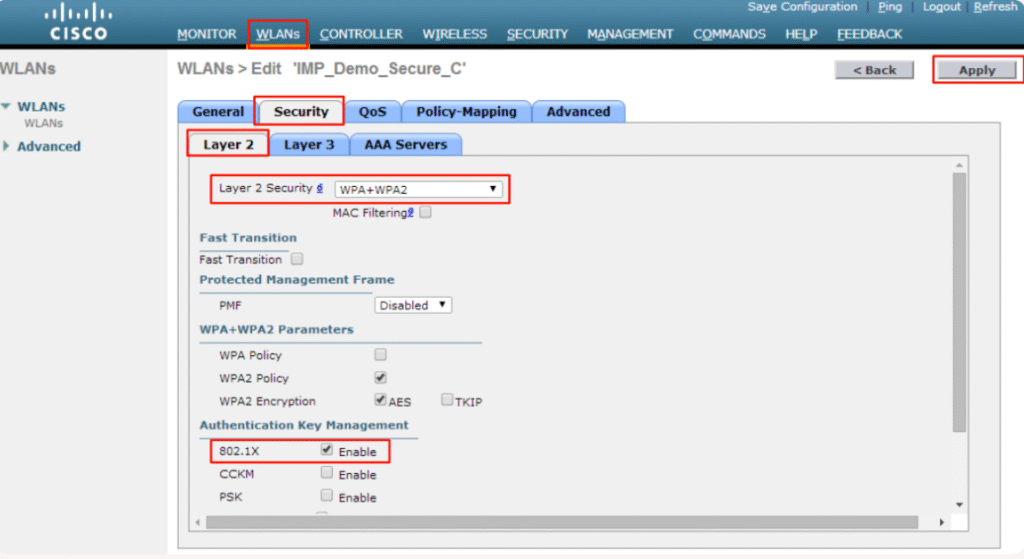
Step 1 – Configure WLANs on WLC
- Create CORP-WIFI SSID
- Security → Layer 2 → WPA2-Enterprise (802.1X)
- AAA Servers → Add ISE as RADIUS Auth Server
- VLAN ID: Leave to be assigned by ISE (Dynamic VLAN)
- [Screenshot: WLC WLAN Security Settings]
- Create GUEST-WIFI SSID
- Security → Layer 3 → Web Policy: Enabled
- Redirect URL: Guest Portal URL from ISE
- VLAN ID: Leave for dynamic assignment
- [Screenshot: WLC WLAN WebAuth Settings]
- Create IOT-WIFI SSID
- Security → Layer 2 → None
- MAC Filtering Enabled
- AAA Servers → ISE as RADIUS Auth Server
- [Screenshot: WLC MAC Filtering Config]
Step 2 – Add WLC as Network Device in ISE
- ISE GUI → Administration > Network Resources > Network Devices
- Add WLC hostname/IP
- Enable RADIUS Authentication Settings → Add shared secret
- [Screenshot: ISE Network Device Config]
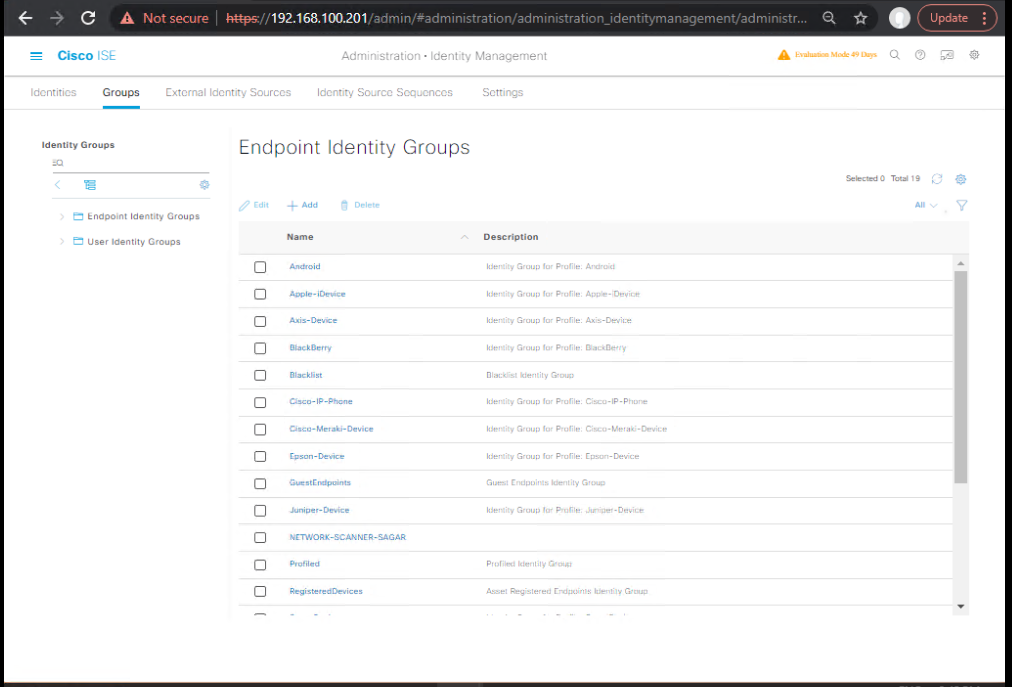
Step 3 – Create Identity Groups
- ISE → Administration > Identity Management > Groups
- Create groups: Employees, Guests, IoT
- Assign test accounts or MAC addresses to the respective groups
- [Screenshot: ISE Identity Group Config]
Step 4 – Create Policy Sets
- CORP-WIFI Policy Set
- Condition:
RADIUS Called-Station-ID CONTAINS "CORP-WIFI" - Auth Policy: EAP-TLS → AD / Internal Users
- AuthZ Policy: Permit + VLAN 20 + ACL_Corp
- [Screenshot: ISE Policy Set – CORP]
- Condition:
- GUEST-WIFI Policy Set
- Condition:
RADIUS Called-Station-ID CONTAINS "GUEST-WIFI" - Auth Policy: MAB → Internal Endpoints (Guest MACs)
- AuthZ Policy: Redirect to Guest Portal VLAN 30
- [Screenshot: ISE Policy Set – Guest]
- Condition:
- IOT-WIFI Policy Set
- Condition:
RADIUS Called-Station-ID CONTAINS "IOT-WIFI" - Auth Policy: MAB → IoT MAC Database
- AuthZ Policy: Permit VLAN 40
- [Screenshot: ISE Policy Set – IoT]
- Condition:
Step 5 – CLI Validation on WLC
show wlan summary show client detail <MAC> debug client <MAC>
Look for:
- RADIUS Access-Accept
- VLAN assignment from ISE
- ACL/SGT application
Step 6 – Validation in ISE GUI
- Operations > RADIUS > Live Logs
- Filter by SSID or MAC
- Check for:
- Authentication Success/Failure
- Authorization Profile applied
- [Screenshot: ISE Live Log Result]
FAQs – Multi-SSID Wireless Integration
Q1: How does Cisco ISE distinguish between different SSIDs coming from the same WLC?
A: The WLC sends the SSID name inside the RADIUS attribute Called-Station-ID. In ISE, you can create policy conditions to match CONTAINS "SSID-NAME" so each SSID gets its own authentication and authorization flow.
Q2: Do I need separate RADIUS servers configured on WLC for each SSID?
A: No. You can point all SSIDs to the same ISE RADIUS server(s). The differentiation happens inside ISE policy sets based on SSID attributes.
Q3: Can a single device connect to multiple SSIDs if needed?
A: Yes, if the user/device meets the authentication requirements for each SSID. For example, an employee laptop might connect to CORP-WIFI via EAP-TLS and also use GUEST-WIFI for testing.
Q4: Will multiple SSIDs reduce wireless performance?
A: Yes, every SSID increases beacon overhead and can reduce airtime efficiency. Cisco generally recommends keeping SSIDs to 4–6 per AP and leveraging dynamic VLAN assignment for segmentation where possible.
Q5: Can ISE dynamically assign different VLANs for the same SSID instead of creating many SSIDs?
A: Yes. Instead of multiple SSIDs, you can have one SSID and use ISE authorization profiles to push VLANs dynamically. Multi-SSID is still used when you need different security/auth methods.
Q6: How can I handle authentication fallback if ISE is down?
A: On WLC, configure “Local EAP” or “Fallback MAC Authentication” for critical SSIDs. This allows basic connectivity even if ISE is unreachable.
Q7: Is it possible to apply posture assessment to only one SSID in a multi-SSID setup?
A: Yes. Create a dedicated policy set for that SSID with posture conditions enabled. Other SSIDs can skip posture assessment to avoid unnecessary checks.
Q8: Can guest SSIDs be integrated with sponsor-based or self-registration portals?
A: Absolutely. ISE’s Guest Portal can be integrated per SSID so that GUEST-WIFI automatically redirects users to self-register or require sponsor approval.
Q9: How do I troubleshoot when a client fails to connect on a specific SSID?
A:
- Check WLC CLI:
debug client <MAC> show client detail <MAC> - Check ISE Live Logs for authentication result and authorization profile.
- Verify SSID-specific policy set matches in ISE.
Q10: Can Multi-SSID integration work with FlexConnect mode APs at branch sites?
A: Yes. FlexConnect supports multiple SSIDs and still receives dynamic VLAN assignments from ISE. However, ensure VLAN mappings are configured locally on the AP for fallback.
YouTube Link
For more in-depth Cisco ISE Mastery Training, subscribe to my YouTube channel Network Journey and join my instructor-led classes for hands-on, real-world ISE experience
Closing Notes
With Multi-SSID integration, Cisco ISE and WLC deliver a centralized, secure, and scalable wireless access architecture — allowing precise control over different user/device categories. This reduces manual VLAN mapping, strengthens security, and simplifies ongoing operations.
Fast-Track to Cisco ISE Mastery Pro
If you’re serious about mastering enterprise-grade NAC, Cisco ISE integrations, and advanced wireless security — stop guessing, and start building production-ready skills.
Join my 4-Month Instructor-Led CCIE Security Training Program — where we go far beyond theory and configure every lab step-by-step in real time.
We cover:
- Cisco ISE end-to-end
- Wired + Wireless NAC
- Advanced 9800/IOS-XE Integration
- Posture, BYOD, SGT, pxGrid, TrustSec
- Troubleshooting with GUI & CLI like a pro
Seats are limited → Get the complete course outline here: https://course.networkjourney.com/ccie-security/
Book your seat now and transform your NAC skills into a career advantage.
Enroll Now & Future‑Proof Your Career
Email: info@networkjourney.com
WhatsApp / Call: +91 97395 21088



![Ticket 21: Wireless Clients Disconnect Randomly: FlexConnect Central Switching Misconfigured[CCNP Enterprise]](https://networkjourney.com/wp-content/uploads/2025/07/Ticket21_-Wireless-Clients-Disconnect-Randomly-FlexConnect-Central-Switching-Misconfigured_networkjourney.png)