[Day 58] Cisco ISE Mastery Training: iOS Device Onboarding
Table of Contents
Introduction
iOS Device Onboarding in Cisco ISE is more than just “getting an iPhone onto the Wi-Fi.” In enterprise NAC (Network Access Control) deployments, onboarding refers to the process where unmanaged, personally owned, or BYOD (Bring Your Own Device) iOS devices are securely registered, provisioned, and granted network access based on corporate security policy.
For iOS, Cisco ISE provides a streamlined BYOD workflow using a captive portal redirection that guides users through certificate enrollment via SCEP, installing an MDM profile, and automatically reconfiguring their Wi-Fi settings to use secure EAP methods (like EAP-TLS).
This eliminates weak password-based authentication for personal devices and gives network admins visibility and control — without making employees jump through IT tickets.
Problem Statement
Modern enterprises often allow employees to connect personal iPhones or iPads to corporate resources. Without a proper onboarding process:
- Devices may connect using insecure credentials (e.g., simple WPA2-PSK).
- IT loses visibility into device ownership, compliance, and security posture.
- Password changes break connectivity for unmanaged devices.
- Offboarding is manual and error-prone.
The challenge: How can we allow BYOD iOS devices while ensuring certificate-based, policy-driven, and revocable access without burdening the helpdesk?
Solution Overview
Cisco ISE’s BYOD Onboarding workflow for iOS devices solves this by:
- Redirecting new/unregistered devices to an ISE BYOD portal.
- Authenticating the user with their corporate credentials.
- Enrolling the device for a client certificate via SCEP (through ISE or integrated CA).
- Delivering a mobileconfig profile that configures the secure SSID and EAP-TLS authentication.
- Applying device registration records in ISE for ongoing policy enforcement.
- Allowing revocation or quarantine of non-compliant devices.
Sample Lab Topology
Lab Components:
- ISE Server: 3.2 or later, running on VMware ESXi/EVE-NG.
- Wireless LAN Controller (WLC): AireOS or Catalyst 9800.
- Access Points: Lightweight APs connected to WLC.
- Switches: Layer 2/Layer 3 access switch for AP connectivity.
- Endpoints: iPhone/iPad (latest iOS), test Windows/macOS device for admin portal.
- CA Server: Internal Microsoft CA integrated with ISE for SCEP.
Topology Diagram:
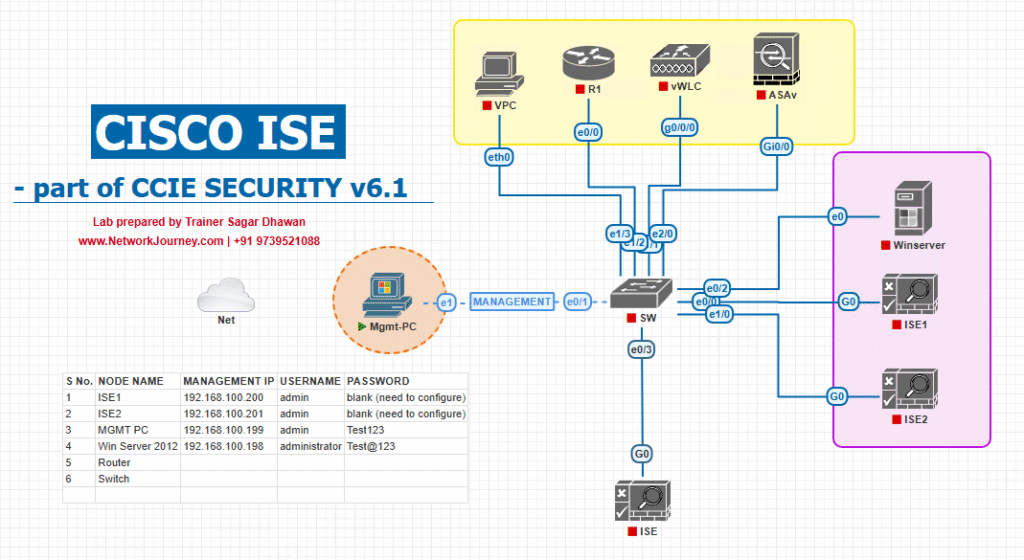
- SSID: BYOD-WIFI (open or WPA2-Enterprise with MAC-based redirection)
- ISE handles RADIUS authentication and redirection.
- WLC applies ACL for pre-onboarding redirection.
Step-by-Step GUI Configuration Guide
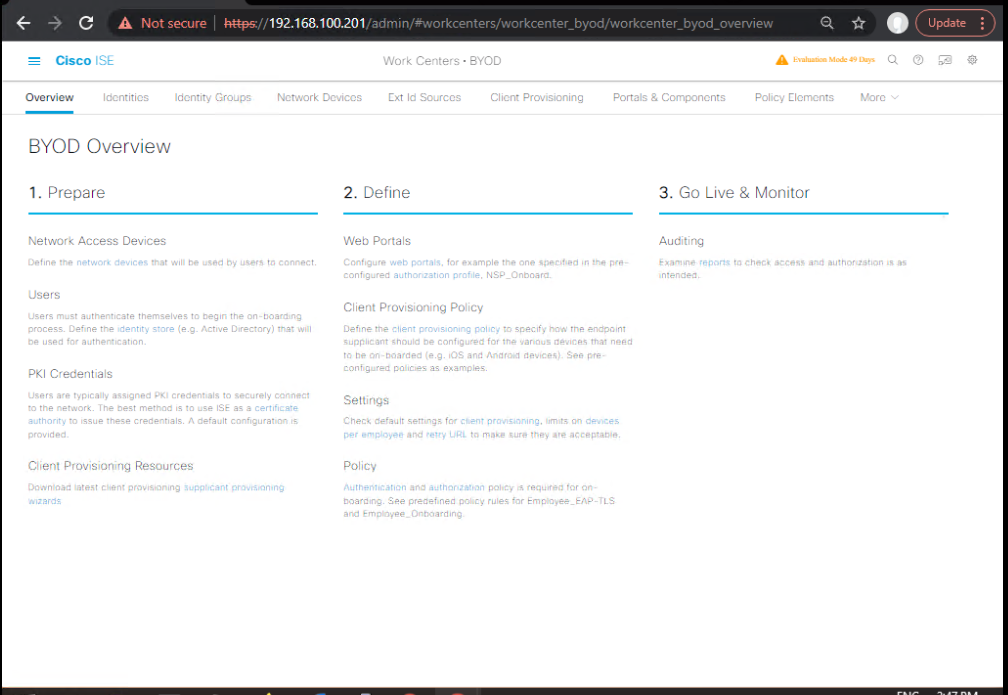
Step 1: Enable BYOD in ISE
- Navigate to Work Centers > BYOD.
- Click Enable BYOD and select Self-Service Portal as the onboarding method.
[Screenshot: ISE BYOD Portal Configuration]
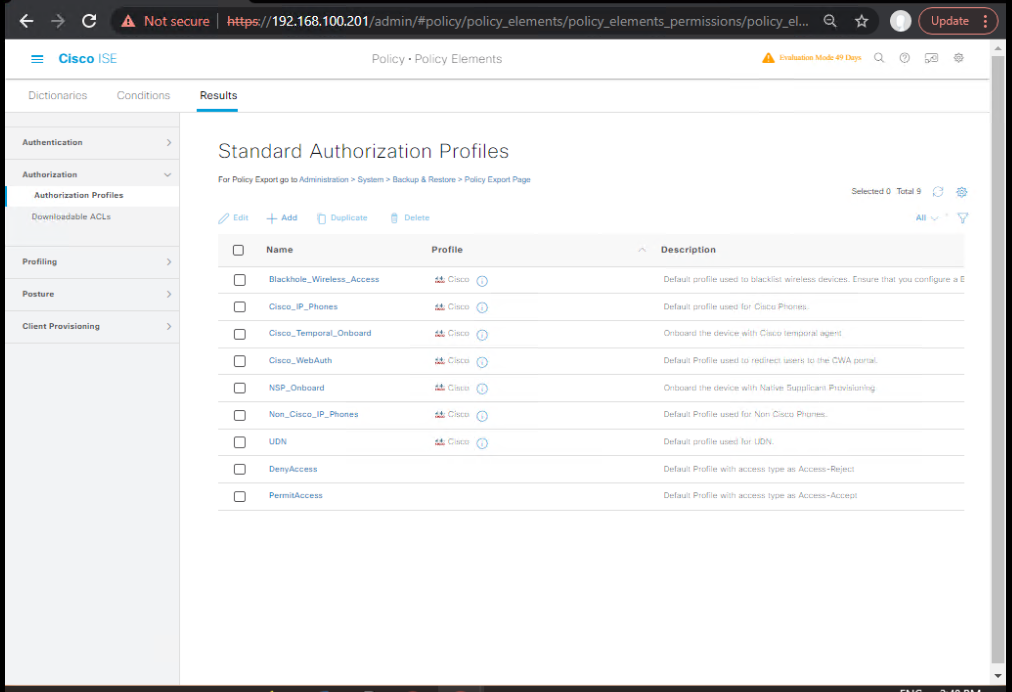
Step 2: Configure Policy Elements
- Authorization Profile – BYOD Redirect
- Go to Policy > Policy Elements > Results > Authorization > Authorization Profiles.
- Create
BYOD-REDIRECT:- Access Type: Access-Accept.
- ACL: Pre-auth ACL (configured on WLC).
- Redirect URL: ISE BYOD Portal URL.
[Screenshot: BYOD Redirect Authorization Profile]
- Authorization Profile – BYOD Completed
- Create
BYOD-ACCESS:- Access Type: Access-Accept.
- VLAN: BYOD-SECURE.
- Downloadable ACL (optional).
- Create
Step 3: Configure WLC for BYOD Redirect
On WLC GUI:
- Create ACL
BYOD-REDIRECT-ACL:- Permit ISE IP, DNS, CA server.
- Deny all other traffic (except DHCP).
- Create WLAN
BYOD-WIFI:- Security: WPA2-Enterprise or open + MAC Filtering.
- AAA Override: Enabled.
- RADIUS Servers: ISE nodes.
- Apply pre-auth ACL for redirection.
CLI Example:
config acl create BYOD-REDIRECT-ACL config acl rule add BYOD-REDIRECT-ACL permit 0.0.0.0 0.0.0.0 host <ISE_IP> config wlan create 5 BYOD-WIFI BYOD-WIFI config wlan security wpa2 enable 5 config wlan security 802.1X enable 5 config wlan radius_server auth add 5 <ISE_IP> 1812
Step 4: Create ISE Policy Set
- Condition – iOS Detection
- Use
Device:Device Type EQUALS Apple-iOS.
- Use
- Authentication Policy
- Allow MAB for redirect phase.
- Allow EAP-TLS/EAP-PEAP for post-onboarding.
- Authorization Policy
- IF (Device Not Registered AND iOS) →
BYOD-REDIRECT. - IF (Device Registered AND iOS) →
BYOD-ACCESS.
- IF (Device Not Registered AND iOS) →
[Screenshot: ISE Policy Set for iOS Onboarding]
Step 5: Test iOS Onboarding
- Connect iPhone to
BYOD-WIFI. - Safari opens BYOD Portal automatically (via redirection).
- Authenticate with AD credentials.
- Download & install mobileconfig profile.
- Device reconnects to SSID using EAP-TLS with installed certificate.
Step 6: Validation
On ISE GUI:
- Operations > RADIUS > Live Logs
Look for two authentications:- Initial MAB/PEAP-Redirect (Access-Accept with Redirect URL).
- Final EAP-TLS (Access-Accept with full access VLAN).
On WLC CLI:
show client detail <MAC> show acl summary
On iOS Device:
- Settings → General → VPN & Device Management → Verify installed profile.
- Wi-Fi → Verify SSID is using “EAP-TLS” under details.
FAQs – iOS Device Onboarding in Cisco ISE
Q1: Why do iOS devices require a different onboarding approach compared to Windows or Android?
A: iOS has a sandboxed OS design and a special provisioning method using .mobileconfig profiles. This means EAP settings, certificates, and Wi-Fi configs must be pushed via an MDM profile or ISE’s BYOD portal — you can’t just manually import them like on Windows.
Q2: Does onboarding require the iOS device to first connect to an open SSID?
A: Usually yes, for the redirect stage. Many deployments use an open or PSK SSID with a pre-auth ACL to redirect unregistered devices to ISE. Some enterprises also use MAC-based bypass on the secure SSID for onboarding.
Q3: Can we onboard an iOS device if it’s already connected to the corporate SSID with username/password?
A: Yes. The device will be detected as not registered and redirected to the BYOD portal for certificate provisioning, then it will reconnect with EAP-TLS.
Q4: How does ISE detect that an iOS device is unregistered?
A: Through endpoint profiling and endpoint identity groups. The device MAC address is checked against ISE’s endpoint database; if not registered, it matches the BYOD redirection policy.
Q5: What happens if the user closes Safari during onboarding?
A: The process halts. The device remains in pre-onboarding state, and the next time it tries to access the network it will be redirected again until completion.
Q6: What’s the difference between BYOD onboarding and Guest access for iOS devices?
A: BYOD onboarding results in device registration and certificate-based secure access for corporate resources. Guest access is typically temporary, not registered in ISE for long-term policy enforcement, and uses different portal/auth rules.
Q7: Can we integrate MDM with iOS onboarding in ISE?
A: Yes. When integrated, ISE can enforce posture/compliance checks (e.g., device encryption, jailbreak detection) before granting access, in addition to certificate provisioning.
Q8: How are the installed certificates renewed when they expire?
A: ISE can prompt the device to re-enroll before expiry. In BYOD mode, the user revisits the portal; with MDM, the process can be automated.
Q9: What if an iOS device is lost or stolen after onboarding?
A: The admin can revoke the certificate in the CA and delete the endpoint record in ISE. The device will then fail EAP-TLS authentication.
Q10: Can one user onboard multiple iOS devices under the same account?
A: Yes, unless the ISE policy explicitly limits devices per user. Many deployments set a max device count per user to prevent abuse.
YouTube Link
For more in-depth Cisco ISE Mastery Training, subscribe to my YouTube channel Network Journey and join my instructor-led classes for hands-on, real-world ISE experience
Closing Notes
iOS Device Onboarding with Cisco ISE transforms BYOD from a security headache into a controlled, automated process. You get:
- Certificate-based secure Wi-Fi for personal devices.
- Self-service user experience.
- Centralized visibility & revocation in ISE.
Done right, it’s a one-time setup that pays off in reduced IT tickets and stronger NAC security.
Fast-Track to Cisco ISE Mastery Pro
Take your Cisco ISE skills from lab to enterprise-ready.
I run a focused 4-month Instructor-Led CCIE Security Mastery Program covering Cisco ISE, ASA/FTD, VPN, SD-WAN, Advanced Network Security, and real-world design labs.
This isn’t just training — it’s hands-on, job-ready skill building with live Q&A, recorded sessions, and 24×7 support.
Course Outline & Registration: https://course.networkjourney.com/ccie-security
Limited seats — Secure your spot now and start mastering ISE like a pro.
Enroll Now & Future‑Proof Your Career
Email: info@networkjourney.com
WhatsApp / Call: +91 97395 21088

![Ticket#4 - BGP Route Not Installing in RIB – Path Attributes and Fix [CCNP Enterprise]](https://networkjourney.com/wp-content/uploads/2025/07/nj-blog-post-Ticket-4.jpg)

