[Day 59] Cisco ISE Mastery Training: Android Device Onboarding
Table of Contents
Introduction
In modern BYOD environments, Android devices represent a significant share of the wireless client base — from personal smartphones to ruggedized enterprise tablets. Unlike iOS, Android devices vary widely by manufacturer and OS version, which means onboarding is not “one-size-fits-all.”
Cisco ISE’s BYOD onboarding for Android automates the secure enrollment process by provisioning an EAP-TLS certificate, configuring Wi-Fi profiles, and registering the device in ISE’s endpoint database for long-term policy enforcement. This process ensures:
- Zero manual Wi-Fi configuration errors from end users.
- Strong mutual authentication using certificates instead of just usernames/passwords.
- Visibility & control over Android endpoints, even in a diverse device landscape.
Problem Statement
Without proper onboarding:
- Users manually configure Wi-Fi and may skip important security settings.
- Credentials can be phished or stored insecurely.
- Unregistered Android devices can connect without corporate compliance checks.
- IT teams struggle to enforce device limits, certificate revocation, and per-device policy control.
Android’s fragmentation problem (Samsung, Pixel, Xiaomi, etc., each with different OS behaviors) means that manual configuration becomes support-heavy, time-consuming, and prone to errors.
Solution Overview
Cisco ISE solves this via:
- Pre-Authentication Redirection – Unregistered Android devices connecting to the onboarding SSID are redirected to the ISE BYOD portal.
- Agent or Agentless Profile Provisioning – ISE uses the Android browser to download a
network_setup.apkor.mobileconfig-style installer for Wi-Fi + certificate. - Certificate Enrollment – A SCEP request is sent to the internal CA or external CA integrated with ISE.
- Automatic Switch to Secure SSID – Post-onboarding, the device reconnects using EAP-TLS to the corporate SSID.
- Device Registration in Endpoint DB – Allows ongoing compliance monitoring, posture checks, and access enforcement.
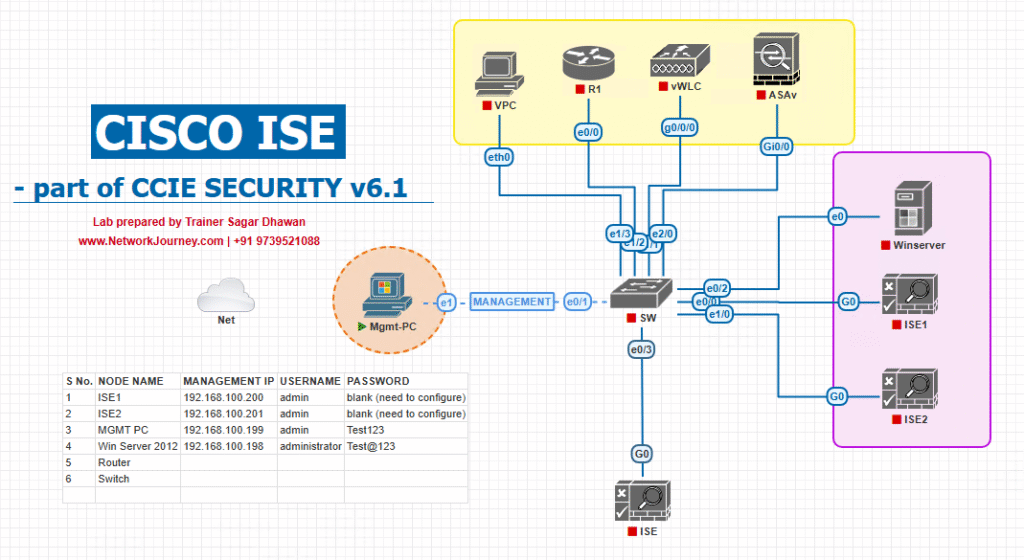
Sample Lab Topology
Lab Setup Components:
- Cisco ISE 3.x on VMware ESXi (or EVE-NG)
- Cisco WLC 9800-CL (VM on EVE-NG) managing lightweight APs
- Catalyst Switch for trunking & VLAN assignment
- Android Device (physical or emulator)
- AD Domain Controller for user authentication
- Internal CA or ISE SCEP service
Topology Flow:
- Android connects to BYOD SSID → WLC applies ACL → Redirect to ISE portal.
- User logs in with AD credentials → Downloads provisioning wizard.
- ISE pushes certificate + SSID profile.
- Device reconnects to secure SSID with EAP-TLS.
Topology Layout:
Step-by-Step GUI Configuration Guide
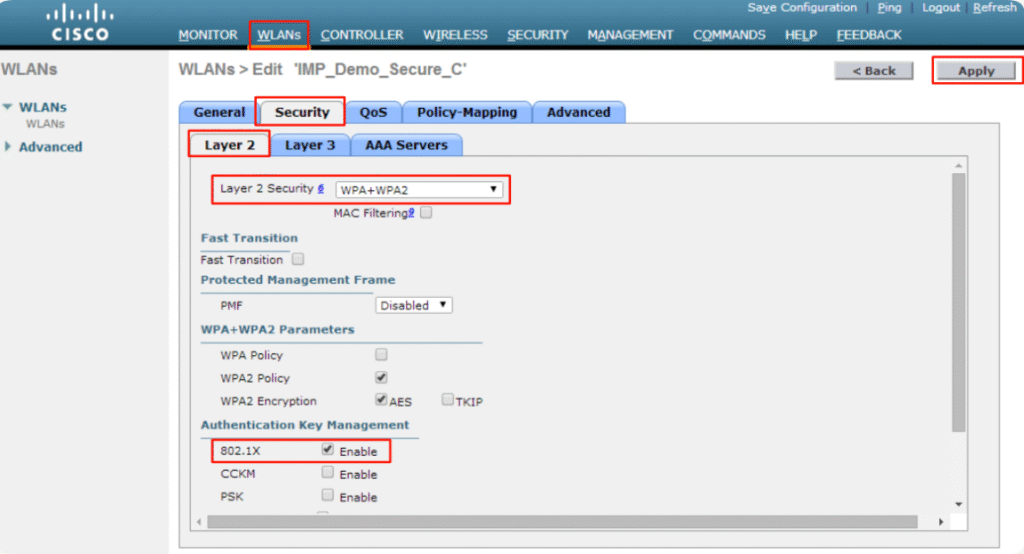
Step 1 – Configure SSID on WLC for Onboarding
- Login to WLC GUI → WLANs → Create New → Name:
BYOD-Android→ ID:10→ SSID:BYOD-Android. - Security → Layer 2 → Open Authentication.
- Layer 3 → MAC Filtering enabled (for redirect ACL).
- Advanced → Enable AAA Override.
[Screenshot: WLC WLAN Creation Screen]
Step 2 – Create Pre-Auth ACL on WLC
(config)# ip access-list extended PRE_AUTH_ACL (config-ext-nacl)# permit udp any any eq 53 (config-ext-nacl)# permit tcp any host <ISE_IP> eq 8443 (config-ext-nacl)# deny ip any any
Apply this ACL in WLAN → Security → ACL.
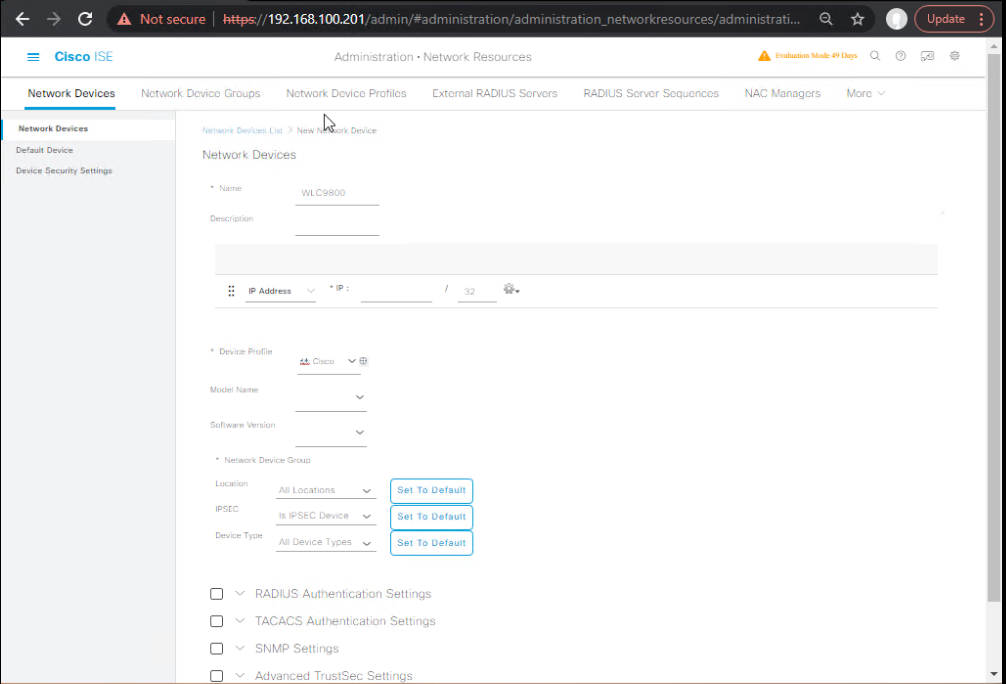
Step 3 – Add WLC as Network Device in ISE
- ISE GUI → Administration > Network Resources > Network Devices → Add.
- Name:
WLC9800→ IP:<WLC_Mgmt_IP>→ Shared Secret:ISEkey. - Enable RADIUS Authentication and RADIUS Accounting.
[Screenshot: ISE Add Network Device Screen]
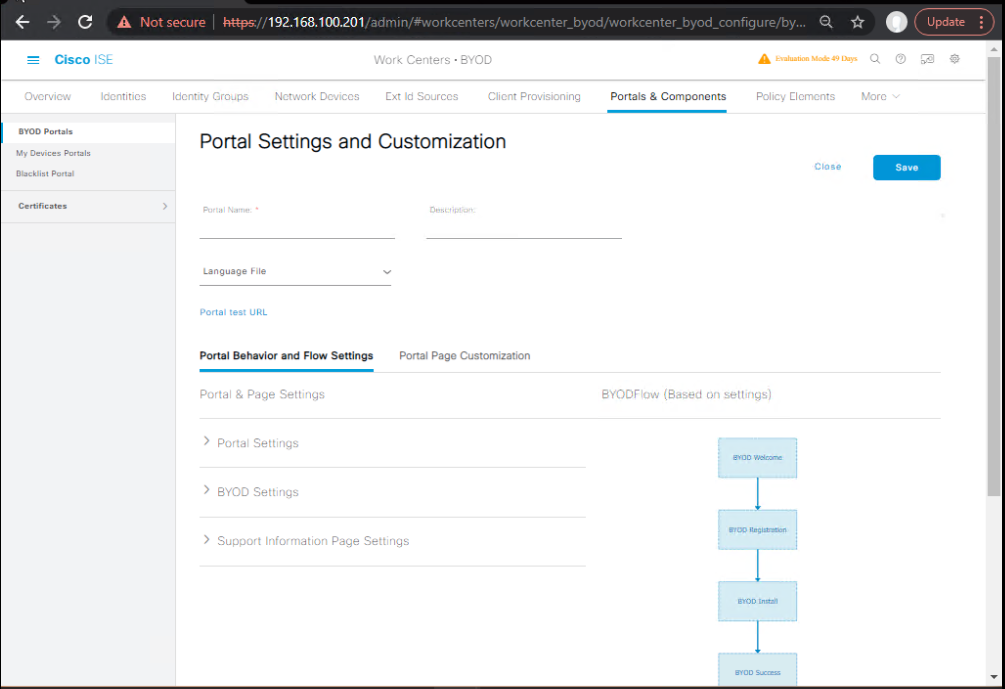
Step 4 – Configure BYOD Portal in ISE
- ISE → Work Centers > BYOD > Portals & Components.
- Create BYOD Portal → Assign name
Android BYOD Onboarding. - Enable Certificate Provisioning and choose SCEP CA.
- Configure redirection URL:
https://<ISE_FQDN>:8443/portal/PortalSetup.action?portal=BYOD.
Step 5 – Create Policy Set in ISE
- ISE → Policy > Policy Sets → Add
Android BYOD. - Condition:
Wireless_MABANDDevice:Profile = Android. - Authorization Rules:
- Unregistered Android → Redirect to BYOD Portal (using Web Redirection ACL name).
- Registered Android → PermitAccess with EAP-TLS.
[Screenshot: ISE Policy Set Screen]
Step 6 – Test & Validate
- On Android → Connect to
BYOD-AndroidSSID. - Browser auto-redirects to ISE BYOD portal.
- Login with AD credentials.
- Download
network_setup.apkfrom ISE. - Install & allow certificate installation.
- Device automatically switches to Secure SSID.
- Check in ISE → Context Visibility > Endpoints → Verify device shows as registered with certificate.
CLI Validation:
# On WLC: show client summary show wlan id 10 client detail <client-mac> debug client <client-mac> # On ISE: show logging application ise-psc.log show logging application ise-acs.log
FAQs – Android Device Onboarding in Cisco ISE
Q1: Why does Cisco ISE treat Android onboarding differently from iOS onboarding?
A: Android has no universal API for Wi-Fi and certificate provisioning across all manufacturers. Unlike iOS, which supports profile delivery via a .mobileconfig file, Android often requires an APK (downloaded from the BYOD portal) to automate EAP-TLS configuration.
Q2: Can we bypass the APK install and still onboard Android devices?
A: In theory, yes — if the user manually installs the certificate and configures the secure SSID with EAP-TLS. However, this increases human error and defeats the automation benefits of ISE onboarding.
Q3: How does ISE detect that a connecting device is Android?
A: ISE uses profiling — gathering attributes such as DHCP option 55 values, HTTP User-Agent strings, and MAC OUI lookups. A matching profiling policy tags the device as Android in Context Visibility.
Q4: What causes APK installation failures during onboarding?
A: Common reasons include:
- User not enabling “Install from Unknown Sources”
- Browser blocking APK downloads
- Antivirus/Play Protect interference
- Outdated Android version not supporting WPA2-Enterprise with EAP-TLS
Q5: Can a single Android device be onboarded to multiple corporate SSIDs?
A: Yes. If the provisioning profile contains multiple SSIDs or if the process is repeated with different SSID parameters. However, this should be managed carefully to avoid policy conflicts.
Q6: How does ISE handle certificate expiration for onboarded Android devices?
A: Without an MDM, ISE cannot silently renew the cert. When the certificate nears expiry, the device will fail EAP-TLS authentication, and ISE can redirect the user back to the BYOD portal for renewal.
Q7: Is Android onboarding compatible with WPA3-Enterprise?
A: Yes, if the device supports WPA3-Enterprise with EAP-TLS and the SSID/WLC configuration matches. Older Android versions may need WPA2-Enterprise fallback.
Q8: Can posture assessment be done at the same time as onboarding?
A: Yes, if the AnyConnect Network Access Manager (NAM) and posture module are deployed during onboarding. This adds checks for OS patch level, antivirus status, etc., alongside certificate provisioning.
Q9: What are the most common troubleshooting commands for Android onboarding?
A:
- WLC:
show client detail <MAC> debug client <MAC>
- ISE CLI:
show logging application ise-psc.log show logging application ise-acs.log
- ISE GUI: Check Operations > Live Logs for RADIUS authentication and web redirection events.
Q10: Can we restrict onboarding to only corporate-issued Android devices?
A: Yes. Combine profiling with endpoint identity groups and MDM compliance status. For example, only allow onboarding if the device MAC is pre-registered in ISE or if the device passes an MDM compliance check.
YouTube Link
For more in-depth Cisco ISE Mastery Training, subscribe to my YouTube channel Network Journey and join my instructor-led classes for hands-on, real-world ISE experience
Closing Notes
Android onboarding in Cisco ISE transforms an unmanaged, potentially insecure device into a fully registered, certificate-authenticated endpoint. It closes the gap between flexibility (BYOD) and corporate security, without burdening the IT team with endless Wi-Fi support tickets.
Fast-Track to Cisco ISE Mastery Pro
If you want to master Cisco ISE end-to-end — from basic NAC to advanced wireless onboarding, posture, and pxGrid integrations — join 4-month Instructor-Led CCIE Security Program.
In this training, you’ll get:
- Real-world enterprise labs (VMware & EVE-NG)
- Step-by-step configs for every ISE feature
- Troubleshooting drills so you can fix issues under pressure
Enroll now → https://course.networkjourney.com/ccie-security/
Seats are limited, and early registrants get bonus ISE Deployment Templates.
Enroll Now & Future‑Proof Your Career
Email: info@networkjourney.com
WhatsApp / Call: +91 97395 21088

![AAA Authentication with TACACS+ and RADIUS – Step-by-Step Cisco Guide [CCNP ENTERPRISE]](https://networkjourney.com/wp-content/uploads/2025/07/nj-blog-post-AAA-TACACS-RADIUS.jpg)

