[Day 61] Cisco ISE Mastery Training: Guest Wireless Reporting & Analytics
Table of Contents
Introduction
Guest wireless access is one of the most widely used features in enterprise networks — and also one of the most mismanaged when it comes to security visibility. While Cisco ISE’s Guest Portal handles onboarding, the real power lies in reporting & analytics. Proper reporting tells you who connected, when, for how long, what device, and from where, enabling compliance audits, forensic analysis, and capacity planning.
This is not just about tracking visitors — it’s about turning guest usage data into actionable security insights. With ISE’s Operations Reports, Context Visibility, and Custom Report Scheduler, network teams can monitor activity in near real-time, detect abnormal usage patterns, and prove regulatory compliance during audits.
In this session, we’ll build a hands-on lab to generate, filter, and schedule guest wireless reports, validate them using both GUI and CLI, and learn the exact workflows TAC engineers use for troubleshooting guest sessions.
Problem Statement
Without centralized reporting:
- Security teams can’t quickly identify malicious guest activity.
- Compliance officers have no proof of user access logs for audits.
- Network engineers have no visibility into device types or locations.
- Guest accounts expire without tracking — causing frustrated visitors and helpdesk overload.
The challenge is building a scalable, accurate, real-time guest reporting system that integrates seamlessly with the existing wireless infrastructure.
Solution Overview
Cisco ISE solves this by:
- Centralizing guest authentication logs across all controllers.
- Context Visibility to enrich logs with device profiling data.
- Pre-built guest access reports under Operations → Reports → Guest Access.
- Custom filters & scheduling to automatically email daily/weekly usage reports.
- Integration with Syslog/SIEM for real-time security monitoring.
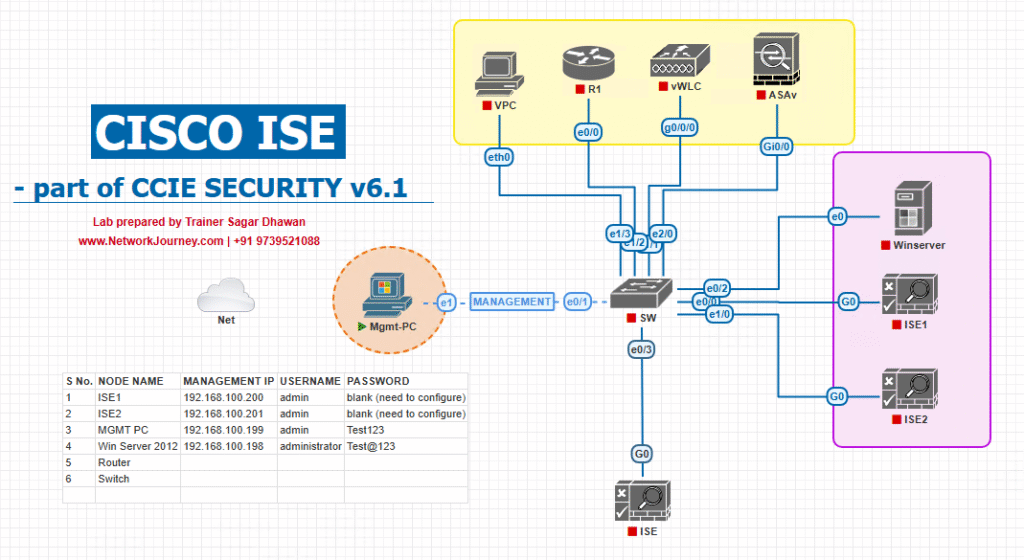
Sample Lab Topology
Text Description:
- Platform: VMware Workstation or EVE-NG
- ISE Node: v3.2 (Admin + PSN roles)
- Wireless LAN Controller: 9800-CL running in VMware/EVE-NG
- Switch: Catalyst 9300 virtual or CSR1000v
- AP: CAPWAP AP (EVE-NG simulated or physical)
- Endpoints: Laptop & smartphone acting as guests
- External Identity Source: ISE internal guest database
- Syslog Server: Optional (for SIEM integration)
Topology Layout:
Step-by-Step GUI Configuration Guide
A. Enabling Guest Access Logs
- Login to ISE GUI → Go to Administration → System → Logging → Target Settings.
- Ensure Internal Log Target is enabled for Authentication and Authorization logs.
- (Optional) Add a Syslog Target for external logging.
[Screenshot: ISE Logging Targets Screen]
B. Viewing Real-Time Guest Sessions
- Navigate to Context Visibility → Endpoints.
- Filter by Endpoint Group = GuestEndpoints.
- Click any entry to see MAC, IP, Device Profile, SSID, and Location.
[Screenshot: Context Visibility Guest Filter]
C. Generating Guest Wireless Reports
- Go to Operations → Reports → Guest Access → Active Guest Sessions.
- Use the Time Range filter (Last 24 Hours, Custom Date).
- Export report in CSV/PDF for archival.
[Screenshot: Guest Access Report Output]
D. Creating a Scheduled Guest Report
- Go to Operations → Reports → Report Scheduler.
- Select Guest Access Summary report.
- Set frequency (Daily @ 6 AM), output format (PDF), and email recipients.
[Screenshot: Report Scheduler Config]
E. CLI Validation (ISE Node)
- SSH to ISE node:
application configure ise show logging application ise-psc.log | include Guest - Verify guest authentication entries with timestamps.
F. CLI Validation (WLC)
- On WLC:
show client summary show client detail <MAC> - Confirm the SSID matches guest SSID and the RADIUS server is ISE.
FAQs — Guest Wireless Reporting & Analytics
Q1: How do I verify if ISE is logging guest authentications correctly?
A: Check Operations → Live Logs in the ISE GUI and filter by the Guest SSID or endpoint MAC. From CLI, use:
show logging application ise-psc.log | include Guest
Q2: Can I create a report showing guest usage by SSID?
A: Yes, in Guest Access Reports, select filters for SSID and Date Range. This helps isolate analytics per wireless network.
Q3: What’s the difference between “Active Guest Sessions” and “Guest Access Summary” reports?
A:
- Active Guest Sessions shows real-time connected guests.
- Guest Access Summary provides historical records, including past logins and logouts.
Q4: How can I automatically send guest reports to compliance teams?
A: Use Operations → Report Scheduler to set a daily or weekly email job, exporting in PDF or CSV.
Q5: What if my guest report shows no data?
A: Possible causes:
- Guest authentication isn’t hitting ISE.
- Log targets for Authentication are disabled.
- Wrong time range or filters applied in the report.
Q6: How do I identify which sponsor created a guest account?
A: Run the Guest Users Report and check the Created By column to see the sponsor username.
Q7: Can I view the device type (OS) in guest reports?
A: Yes — enable Device Profiling in ISE. Context Visibility will tag guests by OS (e.g., Apple iOS, Android, Windows).
Q8: How do I track expired guest accounts?
A: Use the Expired Guest Accounts report under Guest Access Reports. This is useful for cleaning up the database.
Q9: Can I integrate ISE guest reporting with Splunk or another SIEM?
A: Yes — configure a Syslog Target in Administration → System → Logging to forward guest session logs to your SIEM.
Q10: How can I confirm guest users are assigned to the correct VLAN?
A: Check the Authorization Profile applied in ISE and verify on the WLC using:
show client detail <MAC>
Look for the VLAN ID field in the output.
YouTube Link
For more in-depth Cisco ISE Mastery Training, subscribe to my YouTube channel Network Journey and join my instructor-led classes for hands-on, real-world ISE experience
Closing Notes
Guest wireless reporting in Cisco ISE isn’t just a compliance checkbox — it’s your window into visitor behavior, device types, and potential threats. By mastering ISE’s reporting and analytics, you move from reactive troubleshooting to proactive network security monitoring.
Fast-Track to Cisco ISE Mastery Pro
If you want to go beyond just configuration and learn how to design, deploy, and troubleshoot ISE like a CCIE Security expert, join 4-Month Instructor-Led Cisco ISE Mastery Program.
- Hands-on labs with VMware/EVE-NG
- Step-by-step enterprise scenarios
- Advanced troubleshooting with GUI & CLI
- Complete NAC design workflows
Secure your seat & download the course outline here:
https://course.networkjourney.com/ccie-security/
Enroll Now & Future‑Proof Your Career
Email: info@networkjourney.com
WhatsApp / Call: +91 97395 21088


