[Day 65] Cisco ISE Mastery Training: Integrating SMS Gateway for Guest Credentials
Table of Contents
Introduction
Guest onboarding is only as strong as your identity proofing. Email is slow, shared codes are risky, and front-desk bottlenecks kill user experience. SMS-based credential delivery / OTP verification in Cisco ISE gives you instant, user-bound verification at the edge of your network: guests type a phone number, receive an SMS (OTP or username/password), prove possession, and only then receive network access. Done right, you’ll reduce helpdesk tickets, stop bogus registrations, and pass audits with clean trails.
Problem Statement
Typical guest flows suffer from:
- Fake identities (throwaway emails), no proof of possession.
- Shared passwords and uncontrolled re-use.
- Manual account handling by reception (slow + error-prone).
- Compliance gaps (no verifiable link between phone and account).
- Operational noise (lost credentials, repeated portal retries).
We need a self-service workflow that proves real-user possession (phone), binds identity to a device, and enforces time/attempt limits — all centrally logged.
Solution Overview
Cisco ISE enables SMS in guest workflows by:
- Adding an SMS Gateway (HTTP/HTTPS API, SMPP, or SMTP-to-SMS).
- Enabling SMS OTP verification and/or SMS credential delivery in the Self-Registration or Sponsored Guest portals.
- Using Guest Types to constrain lifetime, concurrent sessions, and OTP validity / retry limits.
- Authorization Policies that isolate unverified devices until OTP succeeds; then elevate access.
- Full audit & reporting (who registered, which MSISDN, when verified, who approved).
Sample Lab Topology
Platform: VMware Workstation or EVE-NG
Nodes:
- Cisco ISE 3.x (Admin + PSN on same VM for lab)
- WLC 9800-CL (Guest SSID with L3 WebAuth redirect to ISE)
- L2/L3 switch (Catalyst 9300v or IOU)
- AD/DNS (optional for sponsors)
- SMS Gateway: Public provider (e.g., generic HTTP API) or on-prem SMPP
- Endpoints: Guest phone (iOS/Android), Guest laptop (Windows/macOS)
Flow (diagram description):
- Guest joins Guest-WiFi → redirected to ISE portal → enters phone → receives SMS → enters OTP / gets credentials → ISE authorizes → WLC updates session (AAA override / VLAN / DACL).
Step-by-Step GUI Configuration Guide
(Screenshots placeholders included; CLI where useful)
A. Pre-Reqs & Hygiene
- DNS/NTP/PKI set on ISE (valid HTTPS cert for portals).
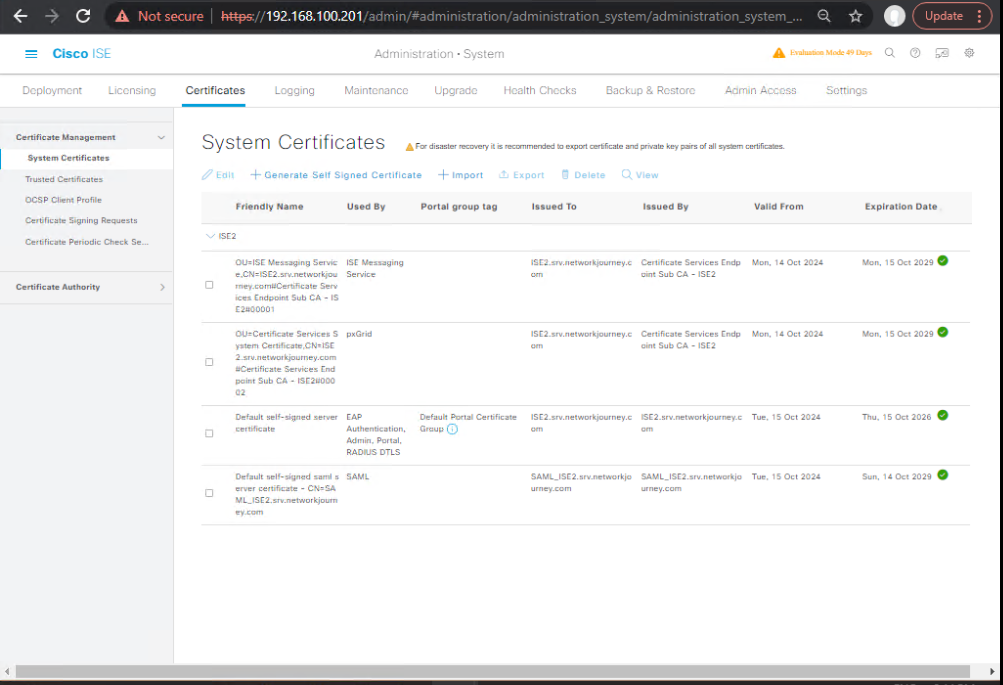
- Admin GUI → Administration → System → Certificates (portal cert)
- [Screenshot: ISE Certificates – Portals]
- Outbound HTTPS permitted from ISE to SMS provider (firewall).
- Guest SSID ready on WLC with L3 WebAuth redirect (we’ll refine below).
B. Configure SMS Gateway (Generic HTTP/HTTPS)
We’ll build a Generic HTTP Provider (POST/GET). Exact fields differ by provider, but ISE exposes variable pickers for recipient (MSISDN) and message.
- ISE GUI → Work Centers → Guest Access → Settings → SMS Gateways → Add.
- Type: Generic HTTP(S) / REST.
- HTTP Method: POST (recommended).
- URL: Provider’s API endpoint (e.g.,
https://api.provider.tld/send). - Auth: As required (Basic / Header token).
- Headers: e.g.,
Content-Type: application/x-www-form-urlencodedorapplication/json. - Body/Parameters: Map Phone = (select ISE variable for phone from UI list), Message = (ISE message variable).
- Save → Test by sending to your own number.
- [Screenshot: ISE SMS Gateway – Generic HTTP Config]
Tip: Use the “Test SMS” button in ISE to validate connectivity and payload mapping before wiring it to a portal.
C. (Alternative) Configure SMPP Gateway
- SMS Gateways → Add → SMPP.
- Enter Host/Port, System ID, Password, SMSC TON/NPI per provider.
- Set Source TON/NPI and Source Address (From) if required.
- Bind Mode: Transceiver.
- Save & Test.
- [Screenshot: ISE SMS Gateway – SMPP Config]
D. Message Templates (OTP / Credential Text)
- Guest Access → Settings → Notification Templates → SMS.
- Create SMS_OTP: “Your verification code is: $OTP$ (expires in 5 minutes).”
- Create SMS_CREDS: “User: $USERNAME$ Pass: $PASSWORD$ Valid: $VALIDITY$.”
- [Screenshot: ISE SMS Templates]
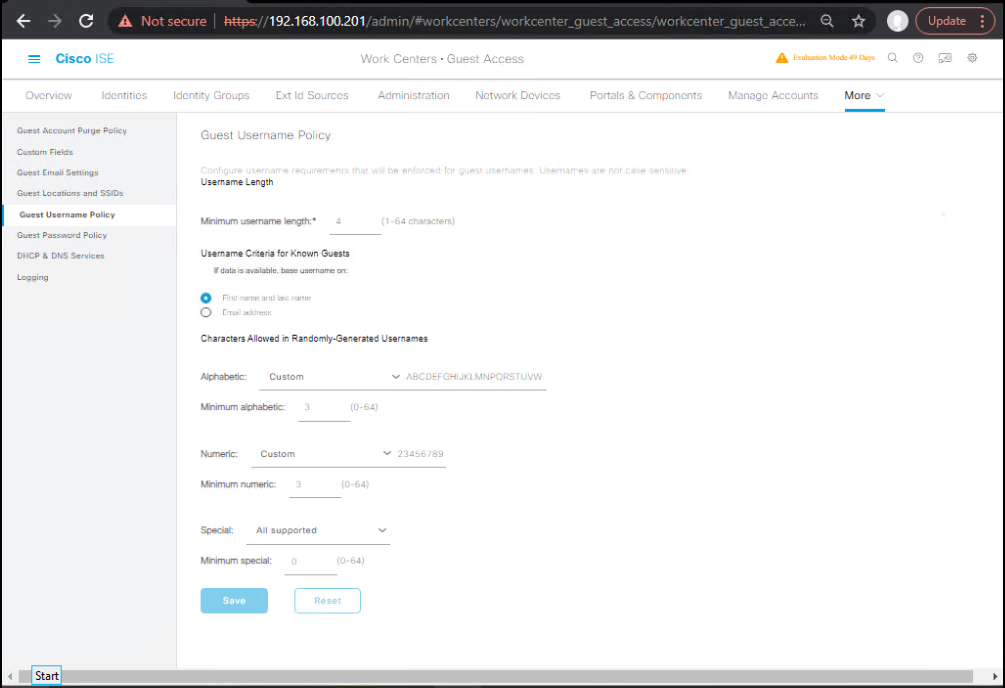
E. Self-Registration Portal (SMS OTP Verification)
- Portals & Components → Guest Portals → Add → Self-Registration Portal.
- Registration Form → Fields:
- Ensure Phone Number is enabled & mandatory.
- Add regex/mask (e.g.,
^\+?[1-9]\d{7,14}$) to enforce E.164. - [Screenshot: Portal Registration Fields]
- Workflow / Verification: Enable “SMS Verification (OTP)”.
- Select SMS Gateway = your provider.
- Set OTP length (e.g., 6), Validity (e.g., 5 minutes), Max Attempts (e.g., 3).
- Template = SMS_OTP.
- [Screenshot: Portal Verification Settings]
- Account Delivery (optional alternative to OTP): Send credentials via SMS using SMS_CREDS.
- Guest Type: choose
SelfReg-24h(lifetime, concurrent sessions, session timeout). - Portal FQDN correct (DNS resolves from guests).
- Save & Preview Portal.
- [Screenshot: Portal Preview]
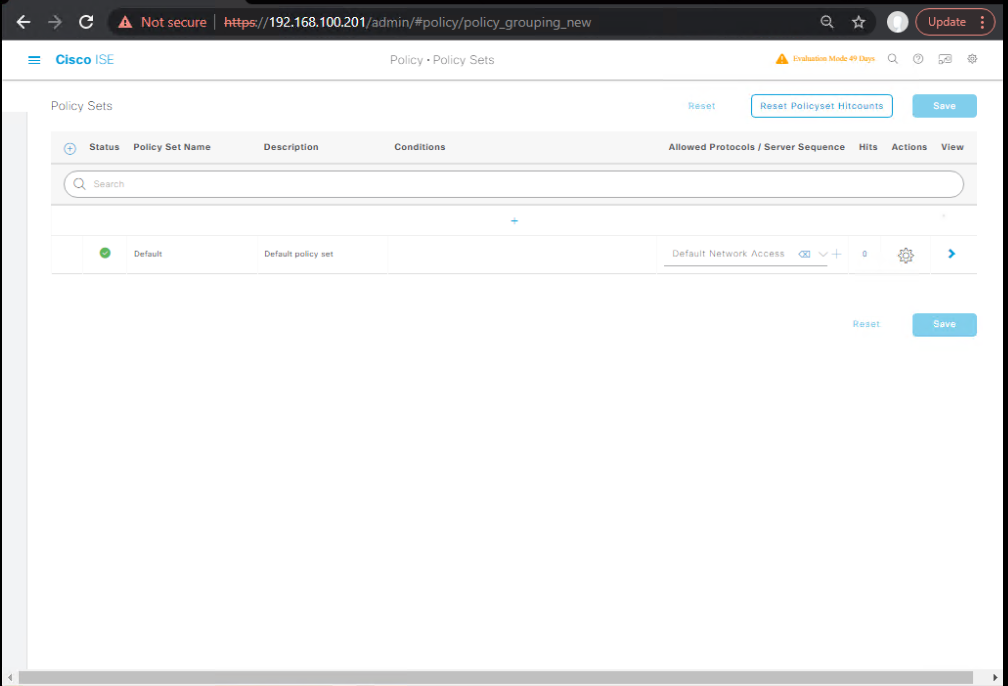
F. Authorization & Redirect (ISE Policy Sets)
- Policy → Policy Sets → (Guest-WiFi)
- Authentication Policy:
- If Wireless_MAB (pre-auth) → Allow and Redirect to Portal (URL-Redirect) using your Guest Redirect authorization profile (points to Self-Reg portal).
- Authorization Policy (examples):
- If
Endpoint:GuestRegistrationStatus = PendingVerification→ Keep Redirect (limited access). - If
GuestUser:Verified = TrueANDIdentityGroup = GuestEndpoints→ Permit Access (Internet-Only) (apply VLAN/DACL). - [Screenshot: Policy Set Screen]
- If
Validation (GUI):
- Operations → RADIUS → Live Logs: See Access-Requests and Authorization transitions from pending → verified.
- [Screenshot: Live Logs – OTP Success]
G. WLC (9800-CL) – WebAuth Redirect & AAA Override
Redirect ACL (allow portal + DNS + DHCP; deny to other until verified):
conf t ip access-list extended GUEST_REDIRECT permit udp any any eq 67 permit udp any any eq 68 permit udp any any eq 53 permit tcp any host <ISE_PSNUIP> eq 8443 permit tcp any host <ISE_PSNUIP> eq 443 deny ip any any ! parameter-map type web-auth guest-redirect type webauth redirect exclude acl GUEST_REDIRECT ! wlan GUEST 30 GUEST client vlan <guest-vlan> security web-auth security web-auth parameter-map guest-redirect no shutdown end wr mem
CLI Validation (WLC):
show wlan summary show client summary show client detail <MAC>
Confirm URL-Redirect pre-auth → AAA Override post-verification (VLAN/DACL change).
H. End-to-End Functional Test (Engineer Playbook)
- Join Guest-WiFi on phone → Captive portal shows registration.
- Enter phone number (E.164 format) → Receive OTP SMS.
- Enter OTP → Success page → Reauth occurs.
- Reconnect or auto-continue → Now Internet-Only access.
- ISE Live Logs: verify pre-auth redirect → OTP validate → Access-Accept.
- Reports → Guest: confirm account creation, MSISDN, timestamps.
- [Screenshot: Guest User Report]
I. CLI / System Validation (ISE)
# Verify overall app health show application status ise # Tail relevant logs for guest/portal/sms actions show logging application ise-psc.log | include SMS|OTP|guest show logging application ise-guestmanager.log | include phone|sms|otp|verify # Confirm RADIUS flows for the client MAC show logging application ise-radius.log | include <client-mac-or-ip>
J. Hardening & Guardrails
- Rate-limit OTP (attempts + resend cooldown).
- Block premium/international ranges if not needed (regex or drop lists).
- Geofence (country code allowlist).
- Short OTP lifetime (3–5 mins), short link TTL if using URL.
- Rotate API keys / use HTTPS only; pin outbound via firewall.
- Use E.164 everywhere (+) to avoid delivery failures.
FAQs
1. What types of SMS gateways can be integrated with Cisco ISE?
ISE supports SMTP-to-SMS, HTTP/S API-based gateways (like Twilio, Clickatell, Nexmo, etc.), and local SMS gateways using SMPP protocol. The most common method is HTTP/S REST API integration.
2. Where do I configure the SMS gateway settings in Cisco ISE?
Navigate to:
Administration → Identity Management → External Identity Sources → SMS Gateway.
Here, you can configure:
- Gateway type (SMTP/HTTP/SMPP)
- API endpoint or SMTP server details
- Authentication (API key, username/password)
- Message format
3. How does ISE send guest credentials to the SMS gateway?
When a guest account is created:
- The sponsor or self-registration portal generates username/password.
- ISE forwards the credentials in a predefined message format to the SMS gateway.
- The SMS gateway delivers the message to the guest’s mobile number.
Validation: Use ISE Live Logs to verify delivery status.
4. Can I use multiple SMS gateways for redundancy?
Yes. Cisco ISE allows you to configure primary and backup SMS gateways. If the primary gateway fails, ISE automatically retries with the backup.
5. How do I test SMS gateway integration in ISE?
- Go to the SMS Gateway configuration page.
- Use the Test SMS button to send a dummy message.
- Check Message Delivery Reports in ISE Logs.
- Validate at the mobile phone end.
CLI validation:
ise/admin# application sms test <phone_number> "Test message from ISE"
6. What are common reasons SMS delivery fails?
- Incorrect API endpoint or SMTP server details.
- Invalid mobile number format (missing country code).
- Wrong authentication (API key mismatch).
- Firewall blocking outbound ISE → SMS gateway traffic.
- SMS provider-specific restrictions (daily limits, blocked regions).
7. How do I customize the SMS template for guest credentials?
Go to:
Administration → Guest Management → Settings → SMS Message Templates
You can insert variables like:
%username%%password%%validity%
Example template:
“Welcome to Guest WiFi. Username: %username%, Password: %password%, valid for %validity%.”
8. Can I send OTP (One-Time Password) instead of static credentials?
Yes. With ISE + SMS Gateway, you can integrate OTP workflow by configuring Guest Portal with Dynamic Passwords. Each login attempt generates a fresh OTP delivered via SMS.
9. How do I verify if ISE is actually communicating with the SMS gateway?
- Check ISE Live Logs → System → Guest Access Logs.
- Review SMS Gateway debug logs (API response codes or SMTP logs).
- Use ISE CLI:
ise/admin# show logging application ise-psc.log | include SMS
10. Is SMS delivery secure in Cisco ISE guest workflows?
Yes, but with limitations:
- HTTPS-based gateways provide TLS encryption.
- SMTP with STARTTLS is recommended instead of plain SMTP.
- Remember: SMS itself is not end-to-end encrypted, so use for temporary guest credentials only.
YouTube Link
For more in-depth Cisco ISE Mastery Training, subscribe to my YouTube channel Network Journey and join my instructor-led classes for hands-on, real-world ISE experience
Closing Notes
Integrating an SMS gateway with Cisco ISE transforms guest onboarding into a verified, low-friction journey. With OTP before authorization, clear redirect policies, and tight audit logs, you’ll stop fake sign-ups, speed lobby throughput, and keep compliance teams happy. Always validate the end-to-end flow: Portal → SMS → OTP → Policy elevation.
Fast-Track to Cisco ISE Mastery Pro
Want this running flawlessly in your lab and production? Join 4-Month, instructor-led CCIE Security program — a hands-on, scenario-driven bootcamp where you’ll:
- Build 20+ ISE labs (BYOD, Guest, TACACS+, Posture, pxGrid).
- Implement SMS/Email OTP, sponsor approval, and advanced policy sets.
- Master WLC/9800 & Catalyst integrations (VLAN/DACL/URL-Redirect).
- Learn TAC-style troubleshooting (GUI + CLI + logs) and exam strategy.
Grab the full outline & join the waitlist: https://course.networkjourney.com/ccie-security/
Subscribe to the Network Journey YouTube channel for weekly deep-dives & lab walk-throughs.
Enroll Now & Future‑Proof Your Career
Email: info@networkjourney.com
WhatsApp / Call: +91 97395 21088
![[Day 65] Cisco ISE Mastery Training: Integrating SMS Gateway for Guest Credentials](https://networkjourney.com/wp-content/uploads/2025/08/Day-65-Cisco-ISE-Mastery-Training-Integrating-SMS-Gateway-for-Guest-Credentials.png)
![[Day 42] Cisco ISE Mastery Training: Integrating Cisco WLC for Wireless Access Control](https://networkjourney.com/wp-content/uploads/2025/08/Day-42-Cisco-ISE-Mastery-Training-Integrating-Cisco-WLC-for-Wireless-Access-Control.png)

