[Day 68] Cisco ISE Mastery Training: Wireless Threat Mitigation
Table of Contents
Introduction
Wireless is your largest, noisiest edge—BYOD, guests, contractors, IoT, and traveling staff all converge here. One compromised phone, a malicious hotspot, or a phished laptop can become lateral-movement fuel within minutes. Cisco ISE turns your WLAN into a response fabric: it identifies risky devices (profiling/posture), ingests threat verdicts (pxGrid), and changes the client’s authorization in real time (CoA → VLAN/DACL/SGT quarantine). Today you’ll build a threat-centric NAC for wireless that detects, contains, and proves mitigation with auditable logs.
Problem Statement
Without automated mitigation on Wi-Fi you get:
- Slow incident response (manual ticket → helpdesk → WLC admin → hours of exposure).
- Inconsistent outcomes (some clients blocked, others not).
- No audit trail (who quarantined what, when, and why?).
- Easy evasion (MAC spoofing, re-association to regain access).
We need repeatable, fully logged, policy-driven actions that instantly reduce blast radius on wireless when a device is infected, suspicious, or violating posture.
Solution Overview
You’ll implement the following ISE-centric controls:
- Profiling + Feed Service → classify clients (Windows, iOS, Android, printers, IoT).
- Posture (optional) → ensure agent/OS compliance; non-compliant → remediation VLAN/DACL.
- pxGrid Threat Ingest (e.g., from Cisco Secure Endpoint/AMP, Firepower, Secure Network Analytics, MDM/UEM) → IOCs & verdicts flow into ISE sessions.
- Adaptive Network Control (ANC) → on trigger, ISE applies Quarantine to a MAC/session.
- Authorization Policies map ANC state / Threat attributes → DACL, SGT, VLAN.
- CoA (Change of Authorization) → immediate enforcement on the WLC client.
- Reports + Live Logs → irrefutable evidence of mitigation.
Sample Lab Topology
Platform: VMware or EVE-NG
Nodes
- Cisco ISE 3.x (Admin + PSN)
- WLC 9800-CL + lightweight AP
- Catalyst L3 Switch (SVIs for user/guest/quarantine VLANs)
- (Optional) pxGrid Producers: Cisco Secure Endpoint / FMC / SNA
- DNS/NTP
- Endpoints: Windows 11 laptop, iPhone/Android (victim/test)
Flow (diagram description)
- Pre-auth: WebAuth/802.1X to ISE; WLC supports AAA override/DACL/SGT.
- Post-auth: Threat arrives via pxGrid or posture fails → ISE ANC=Quarantine → CoA → client lands in Quarantine DACL/VLAN.
Step-by-Step GUI Configuration Guide
A) ISE Hygiene & NAD Onboarding
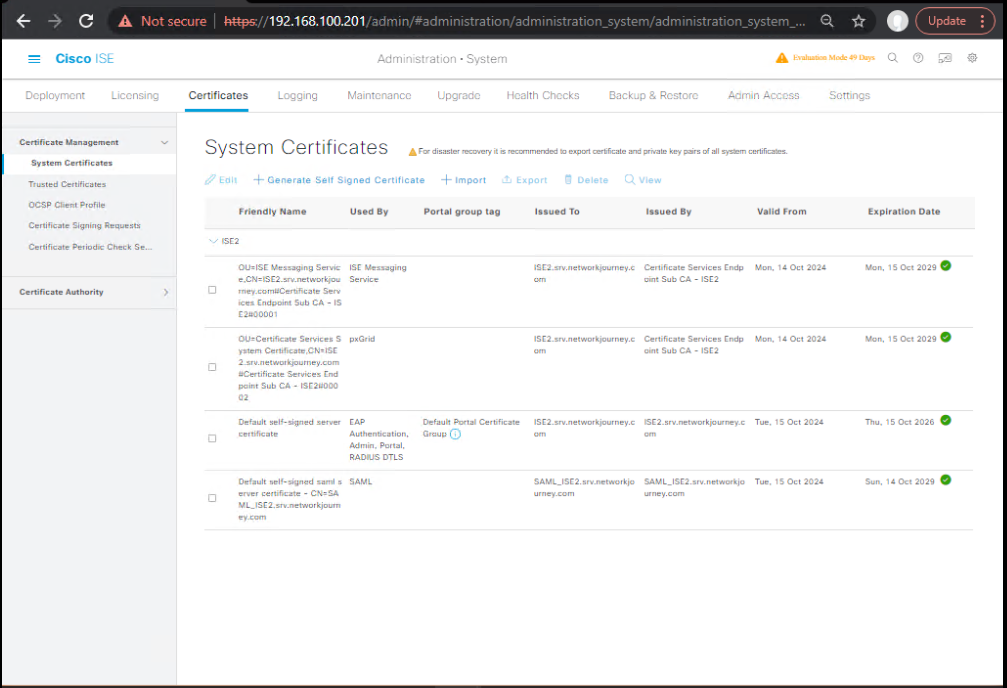
- Portal/AAA Certificate (Public CA)
- Administration → System → Certificates → bind to EAP (if 802.1X) and Portal usages.
[Screenshot: ISE Certificate—EAP & Portal usages]
- Administration → System → Certificates → bind to EAP (if 802.1X) and Portal usages.
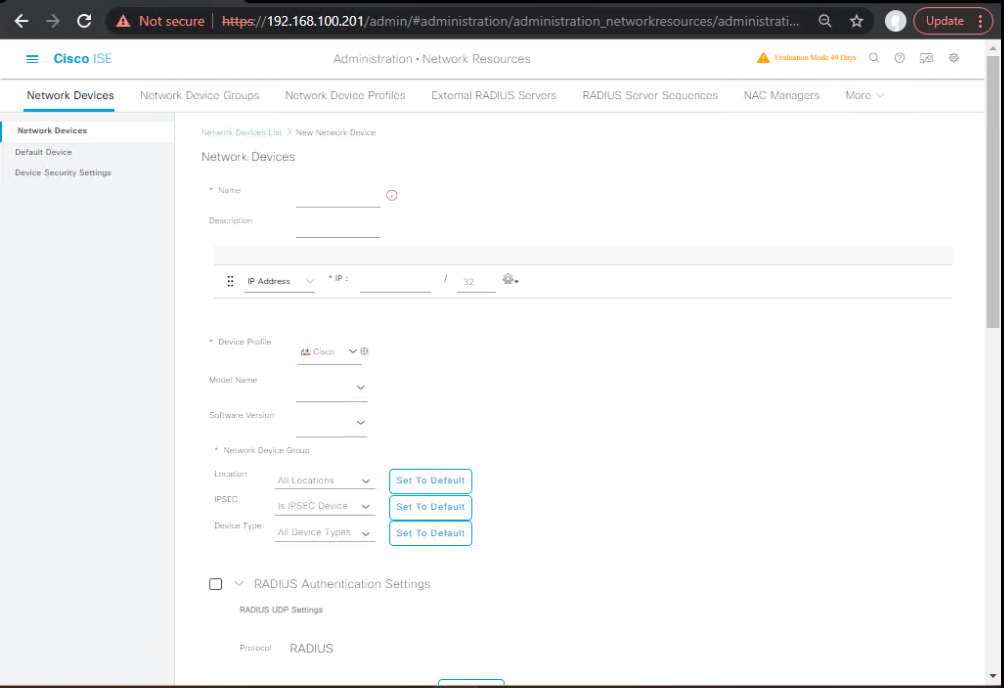
- Add WLC as NAD
- Administration → Network Devices → Add
- Name/FQDN, RADIUS shared secret, Device Type=Wireless.
- Enable CoA.
[Screenshot: ISE Network Device Add—WLC]
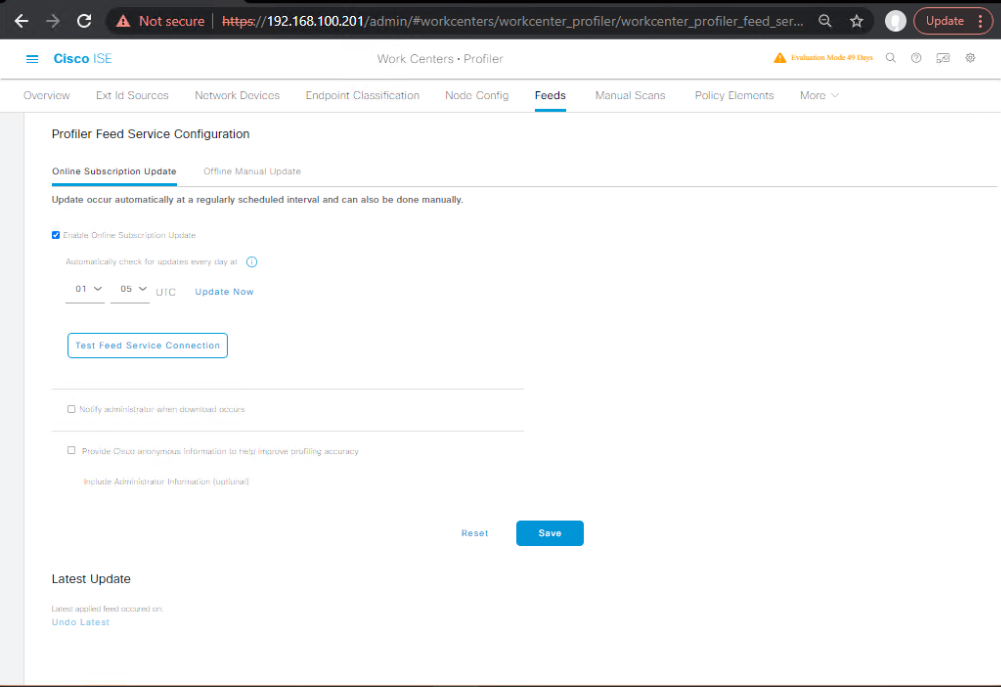
- Enable Profiling & Feed Service
- Administration → System → Settings → Profiling → On.
- Work Centers → Profiler → Feed Service → Enable & Sync.
[Screenshot: ISE Profiler/Feed Service]
B) Build Enforcement Objects
- DACL – QUARANTINE-WIRELESS
- Policy → Policy Elements → Results → Authorization → Downloadable ACLs → Add
- Example DACL:
permit udp any any eq 67 permit udp any any eq 68 permit udp any any eq 53 permit tcp any host <ISE_PSNUIP> eq 443 deny ip any any
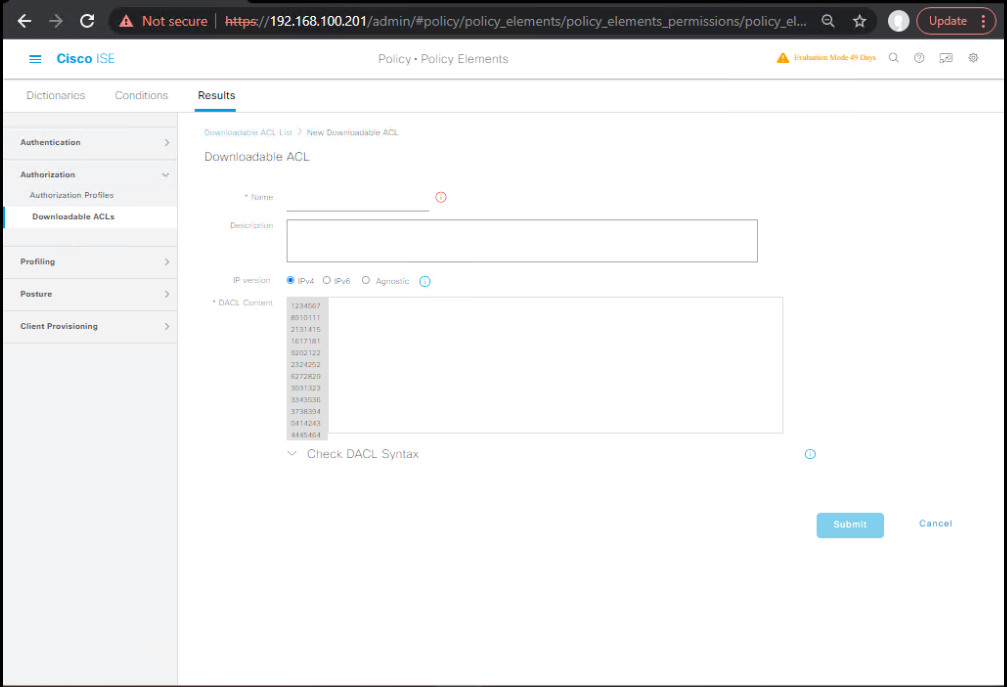
- Authorization Profiles
- WIRELESS-INTERNET →
Airespace-ACL: ALLOW-INTERNET(or DACL with allowed destinations) / or VLAN X. - WIRELESS-QUARANTINE →
DACL: QUARANTINE-WIRELESS(or VLAN Q).
[Screenshot: ISE Authorization Profile—QUARANTINE]
- WIRELESS-INTERNET →
- ANC Policy
- Operations → Adaptive Network Control → Policies → Add
- Name: Quarantine; Action: Quarantine.
- (Optional) Add Port Bounce action for stubborn clients.
[Screenshot: ISE ANC Policy—Quarantine]
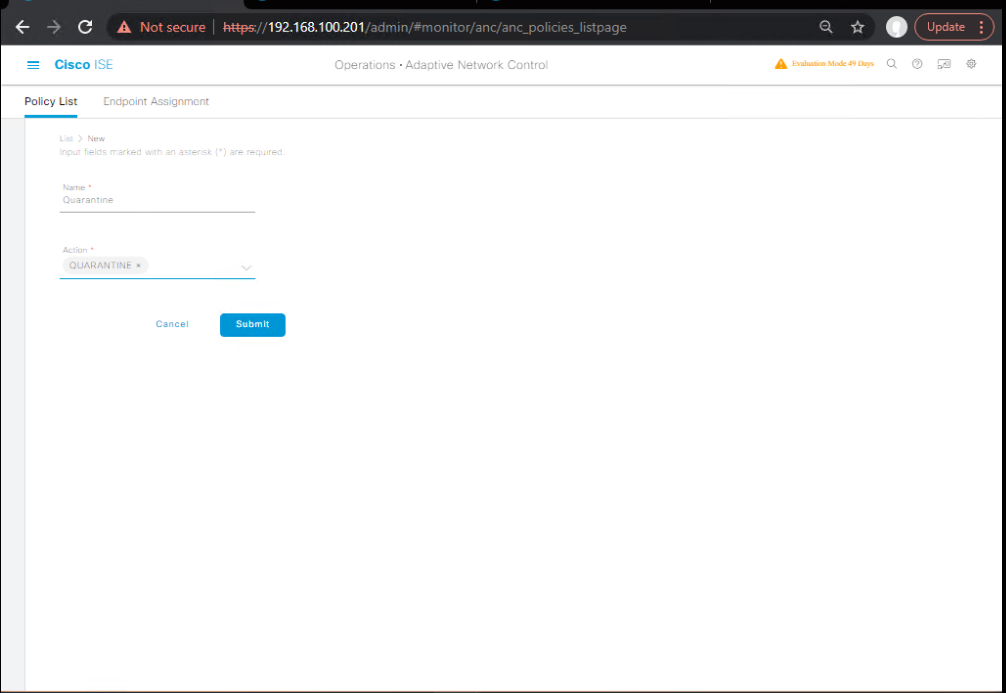
C) pxGrid Threat Ingest (Optional but Recommended)
- Enable pxGrid
- Administration → pxGrid Services → Enable; approve certificates.
[Screenshot: ISE pxGrid Services]
- Administration → pxGrid Services → Enable; approve certificates.
- Register Producers (e.g., Secure Endpoint/FMC/SNA) on pxGrid and Auto-subscribe to threat events (malicious, CnC, high risk).
- Approve clients in ISE pxGrid GUI.
[Screenshot: pxGrid Client Approval]
- Approve clients in ISE pxGrid GUI.
- Context Visibility Mapping
- Verify Session attributes (e.g.,
ThreatLevel,AMPVerdict) appear in Context Visibility → Endpoints.
[Screenshot: ISE Context Visibility—Threat Attributes]
- Verify Session attributes (e.g.,
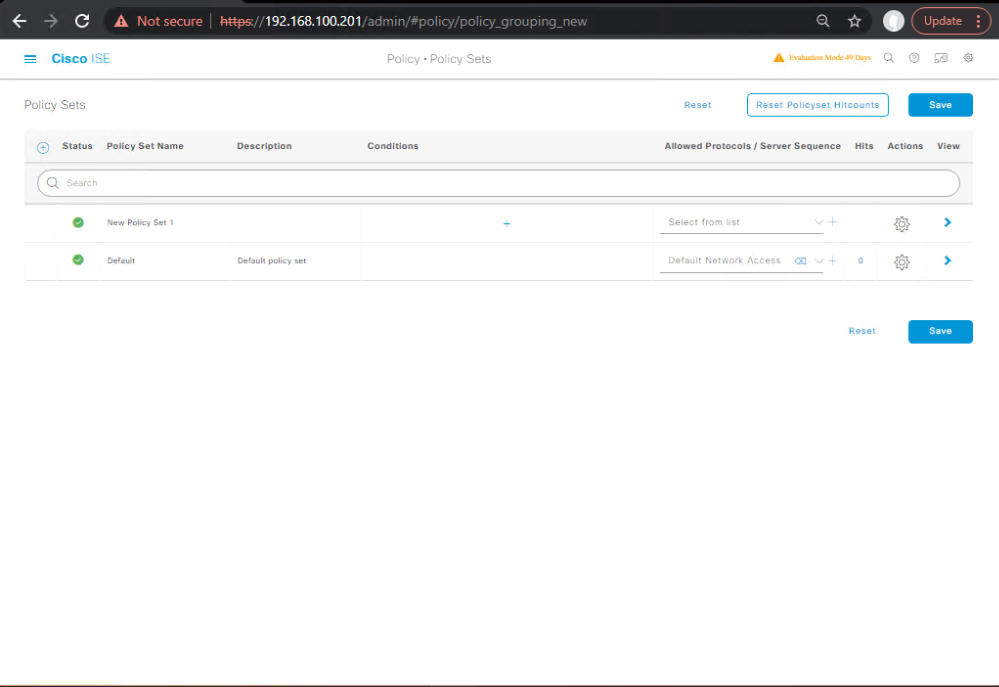
D) Policy Set (Wireless)
- Policy → Policy Sets → Add “WLC-Wireless Threat Mitigation”
- Conditions:
NDG:DeviceType EQUALS Wirelessand/orRADIUS:Called-Station-ID contains <SSID>
[Screenshot: Policy Set Match]
- Conditions:
- Authentication Policy
- 802.1X: PEAP/EAP-TLS as applicable.
- MAB: for non-dot1x devices/IoT.
[Screenshot: Authentication Policy]
- Authorization Policy (top-down examples)
- IF
ANCPolicy EQUALS Quarantine→ WIRELESS-QUARANTINE - ELSE IF
PostureStatus EQUALS NonCompliant→ WIRELESS-QUARANTINE - ELSE IF
ThreatLevel >= High(pxGrid attribute) → WIRELESS-QUARANTINE - ELSE known/compliant → WIRELESS-INTERNET
[Screenshot: Authorization Policy—Threat & ANC Conditions]
- IF
E) WLC 9800-CL Configuration (CLI)
RADIUS + CoA
conf t aaa new-model radius server ISE1 address ipv4 <ISE_PSN_IP> auth-port 1812 acct-port 1813 key <SECRET> ! aaa group server radius ISE-GRP server name ISE1 ! aaa authentication dot1x default group ISE-GRP aaa authorization network default group ISE-GRP aaa accounting network default start-stop group ISE-GRP ! ip http client source-interface GigabitEthernet1 end wr mem
WLAN with AAA Override & DACL support
conf t wlan CORP 20 CORP security wpa psk set-key ascii 0 <if using PSK test> ! or dot1x under policy profile no security wpa psk no shutdown ! wireless profile policy CORP-POL aaa-override radius-profiling central switching vlan <default-user-vlan> ! wireless tag policy CORP-TAG wlan CORP policy CORP-POL ! device-tracking policy DT device-tracking ! end wr mem
Quarantine Pre-Auth/Redirect ACLs (if using WebAuth/Hotspot flows)
conf t ip access-list extended GUEST_PREAUTH permit udp any any eq 67 permit udp any any eq 68 permit udp any any eq 53 permit tcp any host <ISE_PSN_IP> eq 443 deny ip any any end
Validation (WLC)
show wlan summary show wireless client mac <CLIENT_MAC> detail ! Look for AAA Override, DACL name, VLAN show aaa servers show platform software trace wireless core r0 ! if deep debugging needed
F) Operator Playbook: Apply/Auto-Apply Quarantine
Manual (for drill/validation)
- ISE → Context Visibility → Endpoints → select endpoint → Apply ANC Policy → Quarantine.
- ISE sends CoA → client reauths → Authorization hits WIRELESS-QUARANTINE (DACL/VLAN Q).
Automatic (from threat)
- pxGrid event arrives (e.g., Malicious).
- ISE rule or pxGrid ANC mapping sets ANC=Quarantine.
- CoA fires → client contained.
G) Validation – What to Prove (GUI & CLI)
On ISE (GUI)
- Operations → RADIUS → Live Logs
- Entry 1: Access-Accept with normal profile (before incident).
- Entry 2: CoA-Reauth triggered.
- Entry 3: Access-Accept with WIRELESS-QUARANTINE (DACL/VLAN).
[Screenshot: Live Logs – CoA & New AuthZ]
- Operations → Adaptive Network Control → Events
- Shows who applied Quarantine, when, and reason.
[Screenshot: ANC Events]
- Shows who applied Quarantine, when, and reason.
- Context Visibility → Endpoints
- Endpoint shows ANC=Quarantine, Threat attributes, and current AuthZ profile.
[Screenshot: Endpoint Details—Quarantine]
- Endpoint shows ANC=Quarantine, Threat attributes, and current AuthZ profile.
ISE CLI
show logging application ise-radius.log | include <CLIENT_MAC>|<session_id> show logging application ise-psc.log | include ANC|CoA|Quarantine show logging application ise-pxgrid.log | include Threat|Malicious|pxgrid
WLC CLI
show wireless client mac <CLIENT_MAC> detail ! Verify: Policy Profile, VLAN, Airespace-ACL or DACL name present show access-lists show run | sec wlan|policy profile
Endpoint Test
- Internet should be blocked except DNS/ISE (per DACL).
- After Clear ANC and reauth → full access returns.
FAQs
1. How does Cisco ISE detect rogue access points (APs) in a wireless network?
Cisco ISE integrates with the Wireless LAN Controller (WLC) and Cisco DNA Center to receive telemetry data. Using profiling and threat feeds, it identifies unauthorized APs broadcasting SSIDs that mimic the corporate WLAN. These rogue APs can then be flagged in ISE dashboards and mitigated by applying policies.
2. What types of wireless threats can ISE mitigate?
ISE can mitigate:
- Rogue APs (unauthorized devices)
- Rogue clients (endpoints connected to unauthorized SSIDs)
- Honeypot SSIDs (fake SSIDs mimicking corporate WLAN)
- Misconfigured APs
- Man-in-the-middle (MITM) attempts
- Unauthorized peer-to-peer wireless bridges
3. What role does Cisco WLC play in wireless threat detection with ISE?
The WLC is responsible for RF scanning and threat reporting. It sends client association logs, rogue detection data, and security events to Cisco ISE. ISE then uses this information to trigger dynamic network access control (NAC) policies.
4. How can we configure Cisco ISE to quarantine a device connecting to a rogue AP?
You can configure an authorization profile in ISE with a Quarantine VLAN or DACL. The policy set can match the condition “Endpoint Profile: Rogue Client” and apply the quarantine profile, effectively cutting off network access.
5. Does Cisco ISE require pxGrid for wireless threat mitigation?
Yes, pxGrid is strongly recommended. Cisco ISE shares threat intelligence with Cisco DNA Center, Stealthwatch, Firepower, and WLC via pxGrid. This enables automated policy enforcement when a rogue or malicious device is detected.
6. Can Cisco ISE automatically shut down a switch port if a rogue AP is connected?
Yes. Using Adaptive Network Control (ANC) policies, ISE can send a CoA (Change of Authorization) to the access switch, which either shuts down the port or places the rogue AP into a restricted VLAN.
7. How do we validate that wireless threat mitigation is working in ISE?
Validation can be done by:
- Checking ISE > Operations > Reports > Threat Reports
- Reviewing Live Logs for CoA/Quarantine actions
- Running CLI on the switch/WLC:
show authentication sessions show wireless rogue-ap summary
8. Can ISE integrate with third-party Wireless IDS/IPS systems for threat detection?
Yes. ISE can consume threat intelligence from third-party platforms via pxGrid or syslog feeds. For example, if an Aruba or AirMagnet WIPS system detects a rogue AP, ISE can enforce mitigation via policy.
9. What’s the difference between rogue AP detection and containment in ISE?
- Detection = Identifying unauthorized SSIDs/APs broadcasting in the air.
- Containment = Taking action (shutting down switch ports, redirecting clients, quarantining endpoints) to neutralize the rogue AP.
10. What are the best practices for wireless threat mitigation in Cisco ISE?
- Always integrate ISE with WLC for visibility.
- Enable profiling for endpoint identification.
- Use pxGrid with DNA Center/Firepower for automated responses.
- Create custom reports to monitor rogue activity.
- Apply Authorization Policies with Quarantine VLANs or ACLs for fast isolation.
- Test containment policies in a lab before deploying in production.
YouTube Link
For more in-depth Cisco ISE Mastery Training, subscribe to my YouTube channel Network Journey and join my instructor-led classes for hands-on, real-world ISE experience
Closing Notes
Wireless threat mitigation in ISE is about speed + certainty: detect (profiling/posture/pxGrid), decide (policy/ANC), and change the network in seconds (CoA → DACL/SGT/VLAN). Build small, test often, and always verify with Live Logs + WLC client detail so every action is defensible.
Fast-Track to Cisco ISE Mastery Pro
Want production-grade threat mitigation with policy packs, quarantine runbooks, and pxGrid integrations you can deploy this week?
Join 4-Month, instructor-led CCIE Security program to:
- Implement 25+ labs: Threat-centric NAC, BYOD, Guest, Posture, pxGrid.
- Master DACL/SGT/VLAN containment patterns on 9800/Catalyst.
- Build automation hooks (ANC APIs, ticketing) + iron-clad audit exports.
- Leave with templates for fast rollouts across sites.
Course outline & waitlist: https://course.networkjourney.com/ccie-security/
Subscribe to Network Journey on YouTube for weekly ISE deep-dives & live builds.
Enroll Now & Future‑Proof Your Career
Email: info@networkjourney.com
WhatsApp / Call: +91 97395 21088

![[Day 67] Cisco ISE Mastery Training: Guest Portal Branding Customization](https://networkjourney.com/wp-content/uploads/2025/08/Day-67-–-Cisco-ISE-Mastery-Training-Guest-Portal-Branding-Customization.png)

![[Day 65] Cisco ISE Mastery Training: Integrating SMS Gateway for Guest Credentials](https://networkjourney.com/wp-content/uploads/2025/08/Day-65-Cisco-ISE-Mastery-Training-Integrating-SMS-Gateway-for-Guest-Credentials.png)