[Day 69] Cisco ISE Mastery Training: Detecting Rogue Access Points
Table of Contents
Introduction
Rogue APs are the wireless backdoor attackers don’t have to pick. A consumer router on a free LAN jack, a misconfigured travel AP, or a malicious evil-twin near your office can bypass NAC, leak data, or phish users. In a modern Cisco stack, WLC does the RF hunting and classification, while ISE enforces containment on users and wired uplinks (DACL/SGT/VLAN/ANC). Today you’ll build a detect-classify-contain loop that’s provable in logs and repeatable in audits.
Problem Statement
Without a coordinated ISE+WLC approach:
- Blind spots: APs appear/disappear quickly; ad-hoc scans miss them.
- Slow response: finding a rogue ≠ stopping clients from using it.
- Lateral risk: a rogue AP on a switch port can NAT dozens of devices into your LAN.
- No evidence: security can’t show who acted, when, and what was blocked.
We need continuous RF detection, deterministic classification, and automatic enforcement (wireless & wired) with auditable logs.
Solution Overview (How ISE fits)
- WLC Rogue Detection & Classification: APs/clients seen over-the-air are inventoried; “on-wire” rogues are detected via wired neighbor correlation.
- Auto/Manual Containment (WLC): deauth/contain malicious rogues (respect local laws/policy).
- ISE Profiling (Wired side): if a rogue AP is physically plugged into your LAN, ISE profiler (LLDP/CDP/DHCP/OUI) classifies it (e.g., Home-AP/Consumer-Router).
- ISE Authorization & ANC: match Endpoint: category/type = AP/Consumer Router or ANC=Quarantine → DACL/VLAN/SGT to isolate its uplink.
- pxGrid (Optional): consume “rogue” events from DNA Center/Secure Network Analytics → trigger ANC automatically.
- Evidence: ISE Live Logs + ANC events, WLC rogue tables, switch auth sessions.
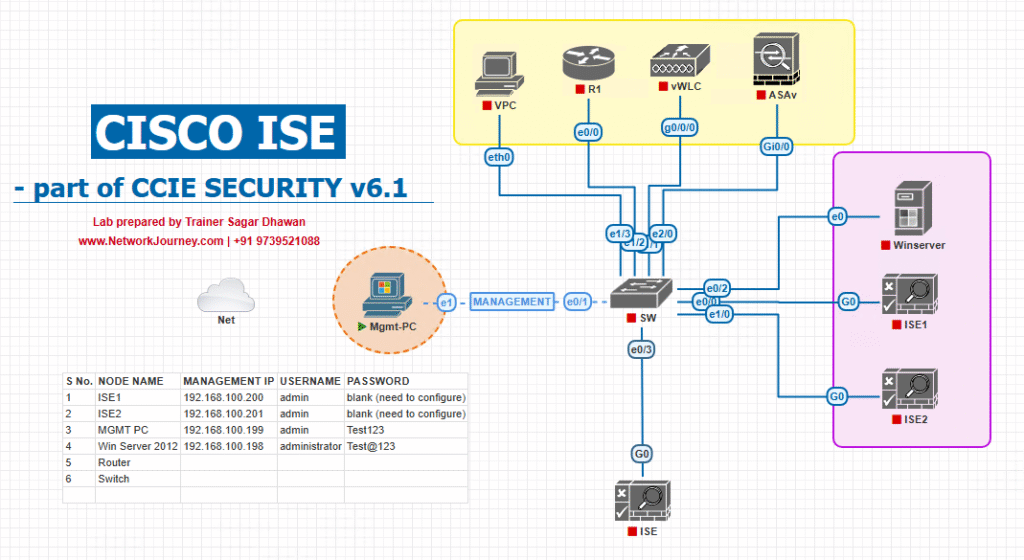
Sample Lab Topology
Platform: VMware/EVE-NG
Nodes
- Cisco ISE 3.x (Admin+PSN)
- WLC 9800-CL + Lightweight AP
- Catalyst L3 Switch (SVIs for user/quarantine)
- DNS/NTP
- Endpoints: Win11 laptop, iPhone/Android
- Rogue: cheap home Wi-Fi router (WAN unplugged) connected to a lab switch access port
Flow (diagram description)
- WLC detects & classifies rogues (over-the-air + on-wire).
- ISE isolates wired rogue AP ports (DACL/VLAN/ANC) and quarantines clients tied to malicious indicators.
Step-by-Step GUI Configuration Guide (with Validation)
A) ISE Hygiene & NAD
- Add WLC as NAD
- Administration → Network Devices → Add
- Device Type: Wireless, RADIUS shared secret, Enable CoA.
[Screenshot: ISE Add Network Device – WLC]
- Enable Profiling + Feed Service
- Administration → System → Settings → Profiling → On
- Work Centers → Profiler → Feed Service → Enable/Sync
[Screenshot: ISE Profiler/Feed Service]
- (Optional) pxGrid
- Administration → pxGrid Services → Enable; approve pxGrid clients (DNA-C/SNA).
[Screenshot: ISE pxGrid Services]
- Administration → pxGrid Services → Enable; approve pxGrid clients (DNA-C/SNA).
ISE GUI Validation: Operations → Live Logs should show WLC as a NAD in new RADIUS records.
ISE CLI Validation:
show application status ise show logging application ise-radius.log | include <WLC_IP>
B) WLC 9800 – Rogue Detection & Classification (GUI)
- Rogue Detection
- Security → Wireless Protection Policies → Rogue Policies
- Enable Rogue AP Detection and Rogue Client Detection
- Set Minimum RSSI (e.g., -80 dBm) and Report Interval (e.g., 10–30s)
[Screenshot: 9800 Rogue Policies]
- On-Wire Rogue
- Rogue Rules/Classification: enable Rogue on Wire detection (uses neighbor correlation).
- Configure DHCP/ARPsnoop/Neighbor correlation if available.
[Screenshot: Rogue On-Wire Settings]
- Containment Policy (caution)
- Security → Wireless Protection Policies → Containment
- Define Auto-Contain for Malicious (NOT Friendly/Neighbor).
- Legal note: follow local regulations and corporate policy before enabling RF containment.
[Screenshot: Containment Policy]
- Syslog (optional)
- Administration → Management → Syslog: add ISE MNT/SIEM as syslog receiver for rogue events.
[Screenshot: WLC Syslog Servers]
- Administration → Management → Syslog: add ISE MNT/SIEM as syslog receiver for rogue events.
WLC CLI Validation
show wireless wps rogue ap summary show wireless wps rogue ap detail mac <ROGUE_AP_MAC> show wireless wps rogue client summary
C) ISE – Wired Rogue Isolation (Authorization + ANC)
- DACL: ROGUE-AP-BLOCK
- Policy → Policy Elements → Results → Authorization → Downloadable ACLs → Add
- Example DACL:
permit udp any any eq 67 permit udp any any eq 68 permit udp any any eq 53 deny ip any any
- Authorization Profile: WIRED-ROGUE-QUARANTINE
- Results → Authorization Profiles → Add
- Set DACL = ROGUE-AP-BLOCK (or VLAN = Quarantine); Reauth = RADIUS (optional).
[Screenshot: ISE AuthZ Profile – Rogue Quarantine]
- Profiler Policy (optional enhancer)
- Work Centers → Profiler → Policies
- Create a policy that matches Device Type = Consumer Router / SOHO AP / Wireless AP (via OUI, DHCP fingerprint). Tag endpoint EndpointIdentityGroup = Rogue-Candidate.
[Screenshot: Profiler Policy Rule]
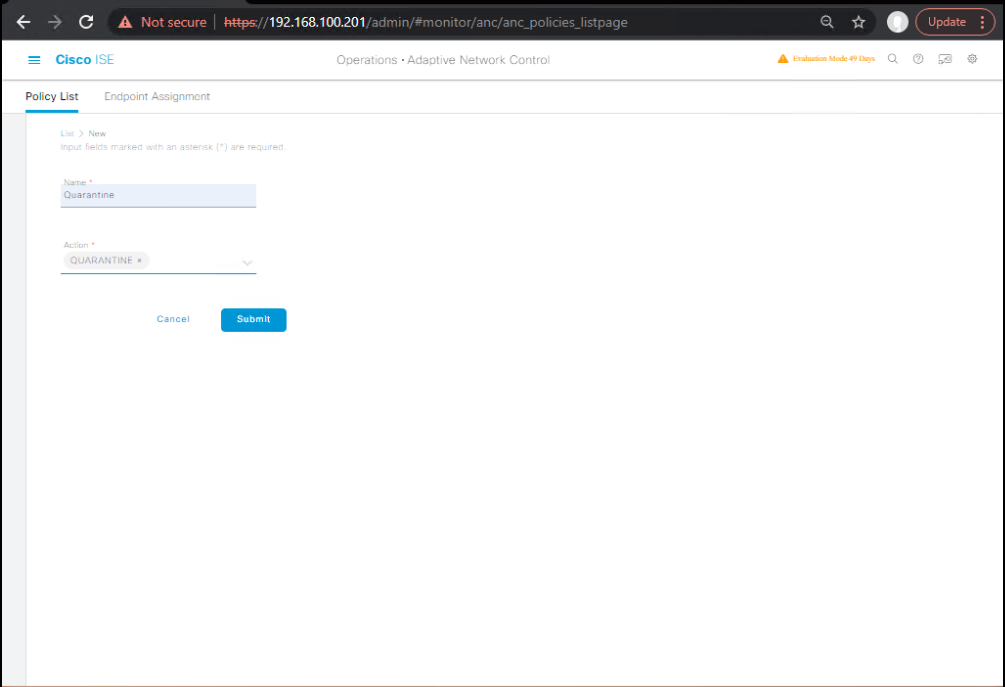
- ANC Policy
- Operations → Adaptive Network Control → Policies → Add
- Name: Quarantine-Rogue; Action: Quarantine (and Port Bounce for wired if needed).
[Screenshot: ANC Policy]
- Authorization Policy (Wired Edge)
- Policy → Policy Sets → (Wired-Edge) → Authorization
- Rules order (top-down):
- IF
EndpointIdentityGroup == Rogue-CandidateORANCPolicy == Quarantine→ WIRED-ROGUE-QUARANTINE - Else normal access
[Screenshot: ISE Authorization Policy – Rogue Match]
- IF
ISE GUI Validation:
- Connect a consumer router to a dot1x/MAB enabled access port → watch Live Logs: initial MAB → profiler identifies → new AuthZ WIRED-ROGUE-QUARANTINE.
- Operations → Adaptive Network Control → Events shows ANC actions.
Switch CLI Validation (access edge)
show authentication sessions interface Gi1/0/10 details ! Expect: METHOD=MAB, STATUS=Authorized, ISE DACL=ROGUE-AP-BLOCK (or VLAN=Quarantine) show mac address-table interface Gi1/0/10 ! Multiple downstream MACs behind the same port suggest an AP/NAT device. show lldp neighbors interface Gi1/0/10 detail show cdp neighbors detail
D) ISE – Wireless Client Mitigation (when users touched a rogue)
- Authorization Profile: WIRELESS-QUARANTINE
- Set DACL=QUARANTINE-WIRELESS (DNS/DHCP/ISE allowed; deny rest).
[Screenshot: ISE AuthZ Profile – Wireless Quarantine]
- Set DACL=QUARANTINE-WIRELESS (DNS/DHCP/ISE allowed; deny rest).
- Policy Condition
- IF
ANCPolicy == QuarantineORContext Attribute from pxGrid indicates Rogue Exposure→ WIRELESS-QUARANTINE. - (With DNA-C/SNA pxGrid, you can map “connected to evil twin”/“C2 beacons” → ANC).
[Screenshot: ISE AuthZ Rule – Threat/ANC]
- IF
Validation
- ISE Live Logs shows CoA then new AuthZ with WIRELESS-QUARANTINE.
- WLC CLI:
show wireless client mac <CLIENT_MAC> detail ! Check Policy, DACL name, VLAN/SGT after CoA
E) Operator Runbooks (Prove It Works)
Drill 1 – Over-the-air Rogue
- Power on a home AP near an office AP.
- On WLC GUI: Monitor → Rogues → verify it appears.
- Mark as Malicious (or let policy auto-contain).
- Validate:
show wireless wps rogue ap detail mac …shows state Contained. - Evidence: export rogue event from WLC; capture ISE logs for any correlated client quarantine.
Drill 2 – Rogue on Wire
- Plug home AP to access port with MAB/802.1X.
- Observe ISE Live Logs → Profiler hit → WIRED-ROGUE-QUARANTINE applied.
- On switch:
show authentication sessions interface …shows DACL/VLAN. - Attempt browsing from a device behind the rogue: blocked except DNS/DHCP/ISE per DACL.
- Clear ANC (ISE) or move device to clean port → reauth → normal profile returns.
F) Helpful Hardening (Wired Edge)
- 802.1X (dot1x) on all access ports; MAB fallback → restricted VLAN/DACL.
- Port-security: limit MACs per port (e.g.,
switchport port-security maximum 2). - Storm-control on access ports.
- IP Device Tracking + DHCP Snooping to catch NAT devices.
- Disable unused ports; use sticky MAC for printers/IP-phones only.
Catalyst CLI snips
interface Gi1/0/10 switchport mode access authentication port-control auto mab dot1x pae authenticator ip dhcp snooping trust ! (only if intended; otherwise keep untrusted) storm-control broadcast level 1.00 storm-control multicast level 1.00 switchport port-security switchport port-security maximum 2 switchport port-security violation restrict
FAQs
Q1. How does Cisco ISE detect rogue access points?
Cisco ISE itself doesn’t scan the RF spectrum; instead, it integrates with the WLC (Wireless LAN Controller) and Cisco MSE/DNA Spaces. The WLC detects suspicious SSIDs/BSSIDs and reports them to ISE for policy action.
Q2. What is the difference between a rogue AP and a neighbor AP?
- Rogue AP → Unauthorized AP connected to the enterprise wired network.
- Neighbor AP → Legitimate APs that are external (e.g., coffee shop Wi-Fi nearby) but not connected to the enterprise LAN.
ISE + WLC helps distinguish them through wired correlation.
Q3. What are the risks of rogue APs in an enterprise network?
- Unauthorized access bypassing NAC policies.
- Man-in-the-middle attacks.
- Data leakage and compliance violations.
- Credential harvesting using SSID spoofing.
Q4. How does WLC classify rogue APs before ISE takes action?
WLC scans RF, discovers SSIDs, checks MAC address OUIs, and performs Rogue Detection with Wired Correlation (whether the rogue is connected to internal LAN). Once classified, ISE can enforce policies.
Q5. Can Cisco ISE automatically block rogue APs?
Yes. With Rogue Detection and Containment Policies, ISE can instruct the WLC to perform:
- Deauthentication attacks against rogue clients.
- Disable rogue switch ports via ISE + TrustSec/SGACL integration.
- Alerts and syslog reporting for SOC.
Q6. How do I validate rogue AP detection in the lab?
- GUI: Navigate to WLC > Security > Rogue Policies > Detected APs. [Screenshot: Rogue AP Detection]
- ISE: Check Context Visibility > Endpoints > Rogue Devices. [Screenshot: ISE Rogue Device Report]
- CLI (WLC):
show rogue ap summary show rogue ap detailed <mac-address>
Q7. What policies should I configure in ISE for rogue AP mitigation?
- Context Visibility rules for rogue AP classification.
- Authorization policy to block rogue MACs.
- Alarms & syslog forwarding to SIEM.
- Optional automatic port shutdown (CoA) if rogue detected on a switch.
Q8. Can I customize the threshold for rogue detection?
Yes. On WLC, you can configure thresholds for RSSI, neighbor count, and wired correlation detection before classifying an AP as rogue. This avoids false positives in dense environments.
Q9. How does ISE integrate with external monitoring tools for rogue AP events?
ISE can export rogue events/logs via:
- Syslog to SIEM tools (Splunk, QRadar).
- pxGrid to Cisco DNA Center or SecureX for automated incident response.
Q10. What are the best practices for managing rogue APs with ISE?
- Always enable wired correlation to avoid misclassifying neighbor APs.
- Configure alerting + reporting in ISE for audit/compliance.
- Use Rogue Containment Policies carefully (avoid accidental denial-of-service).
- Regularly update WLC firmware for better RF scanning capabilities.
YouTube Link
For more in-depth Cisco ISE Mastery Training, subscribe to my YouTube channel Network Journey and join my instructor-led classes for hands-on, real-world ISE experience
Closing Notes
Rogue defense is a two-front war: RF (WLC) and wired (ISE). Detect broadly, classify conservatively, and contain decisively via ISE policies on the port and the user session. Always prove it: WLC rogue tables + ISE Live Logs + switch auth sessions = defensible, auditable action.
Fast-Track to Cisco ISE Mastery Pro
Want a production-ready rogue playbook with one-click ANC, DACL/VLAN templates, and pxGrid automations?
Join 4-Month, instructor-led CCIE Security program to:
- Build 30+ ISE/WLC labs (Rogue, BYOD, Guest, Posture, pxGrid).
- Master WLC rogue tuning and ISE wired quarantine patterns.
- Integrate with DNA-C/SNA/Firepower for auto-mitigation.
- Take home exportable policy packs and validation runbooks.
Course outline & waitlist: https://course.networkjourney.com/ccie-security/
Subscribe to Network Journey on YouTube for weekly ISE deep-dives & live builds.
Enroll Now & Future‑Proof Your Career
Email: info@networkjourney.com
WhatsApp / Call: +91 97395 21088


![[Day 7] Cisco ISE Mastery Training: Configuring Certificates (Self-Signed & CA-Signed)](https://networkjourney.com/wp-content/uploads/2025/08/Day-7-Cisco-ISE-Mastery-Training-Configuring-Certificates-Self-Signed-CA-Signed.png)
