[Day 71] – Cisco ISE Mastery Training: TrustSec Overview & Benefits
Table of Contents
Introduction
Cisco TrustSec (CTS) is a next-generation access control framework that goes beyond traditional IP-based segmentation. Instead of relying on static VLANs and ACLs, it leverages Security Group Tags (SGTs) to dynamically classify traffic, enforce policies consistently across the enterprise, and scale security for modern hybrid networks.
Why this matters:
- In a Zero Trust world, IP addresses are not reliable identity markers.
- Users and devices are mobile, and policies must follow them anywhere in the network.
- Cisco ISE is the policy brain that issues SGTs and TrustSec rules, allowing uniform policy enforcement across switches, routers, wireless controllers, and firewalls.
This is critical for enterprises needing microsegmentation, regulatory compliance, and dynamic access control at scale.
Problem Statement
Without TrustSec, organizations rely on:
- Static VLANs → complex and not scalable for dynamic users.
- Traditional ACLs → explosion in size, hard to manage across devices.
- IP-based policies → fail when users roam or use multiple devices.
Challenges:
- Security policies break with BYOD/mobility.
- High OPEX due to manual ACL maintenance.
- Difficulty in compliance/audit reporting.
Solution Overview
Cisco ISE solves this using TrustSec:
- Security Group Tags (SGTs): Assign user/device a tag (e.g., HR=10, Finance=20).
- SGACLs (Security Group ACLs): Instead of writing hundreds of ACL lines, enforce a simple matrix policy (e.g., HR can talk to Finance = Yes/No).
- Propagation via SXP (SGT Exchange Protocol): Distributes SGTs across devices that don’t support inline tagging.
- Consistent Policy Enforcement: Switches, WLCs, Firewalls apply ISE-issued policies uniformly.
End result: scalable, dynamic, identity-based security enforcement.
Sample Lab Topology
Lab Setup (EVE-NG / VMware):
- Cisco ISE (Policy Brain).
- Switches (Catalyst 9300 / 3650 in EVE-NG).
- WLC + AP (for wireless TrustSec enforcement).
- Endpoints: Windows client, BYOD device.
Diagram Description (Text):
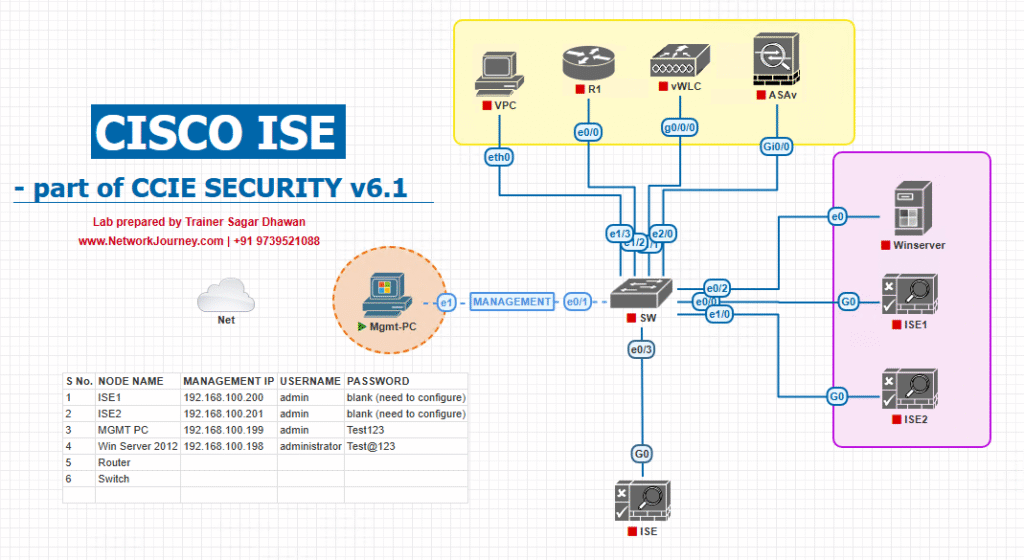
- Endpoints connect to Access Switch.
- Access Switch forwards authentication request to ISE.
- ISE assigns SGT based on identity.
- Switch enforces TrustSec policy via SGACL.
- For unsupported devices, SXP propagates SGT mappings to next-hop capable devices.
Step-by-Step GUI Configuration Guide
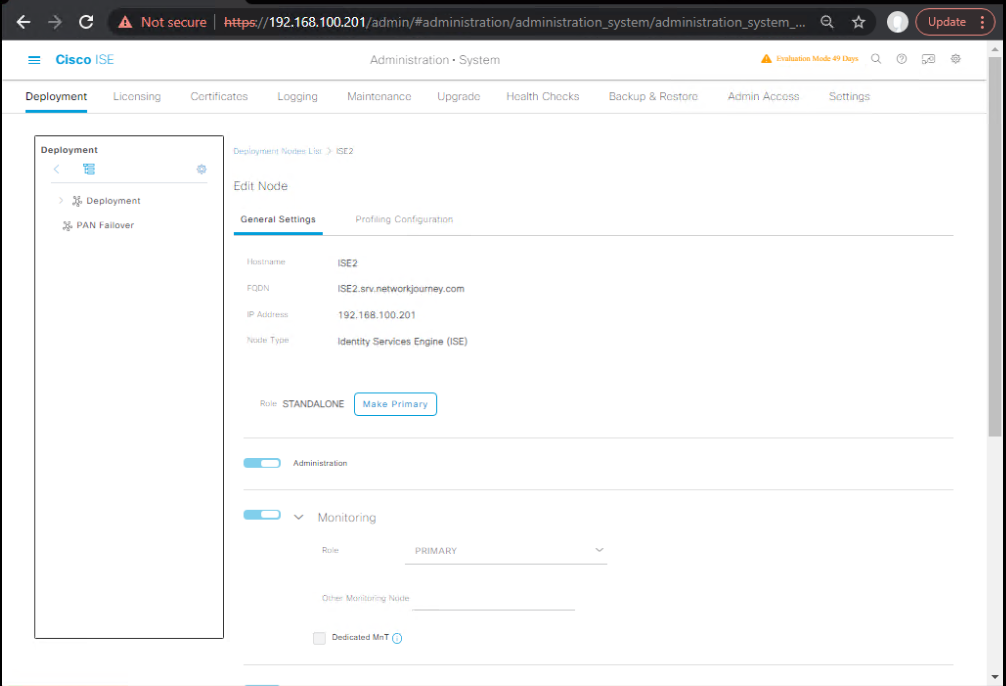
Step 1 – Enable TrustSec in ISE
- Navigate to Administration > System > Deployment.
- Edit ISE Node → Enable TrustSec role.
- [Screenshot: ISE Deployment Node TrustSec Role]
Step 2 – Define SGTs
- Go to Work Centers > TrustSec > Components > Security Groups.
- Click Add → Define groups (e.g., HR, Finance, Guest).
- [Screenshot: Security Groups Creation]
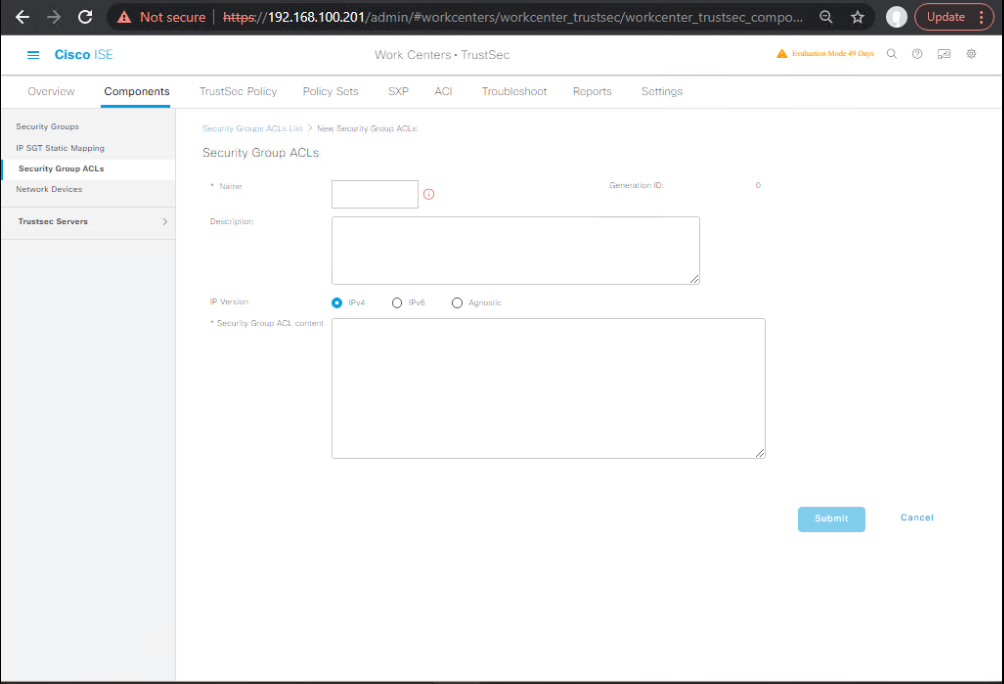
Step 3 – Define SGACLs
- Navigate to Work Centers > TrustSec > Components > Security Group ACLs.
- Create SGACL → e.g.,
HR_to_Finance_ALLOW(permit IP).- [Screenshot: SGACL Creation Screen]
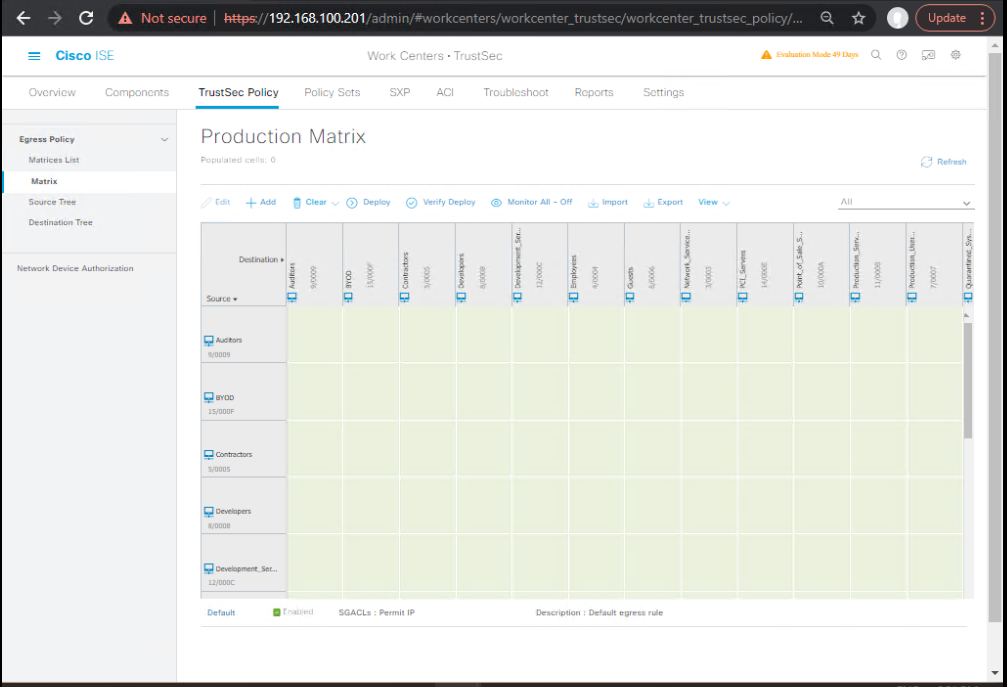
Step 4 – Create TrustSec Matrix
- Go to Work Centers > TrustSec > Policy Matrix.
- Drag and drop SGTs → Assign SGACLs.
- Example: HR (SGT 10) → Finance (SGT 20) → Allow.
- [Screenshot: TrustSec Policy Matrix]
Step 5 – Push Policy to Network Devices
- Ensure switches/WLC are added as Network Devices in ISE.
- Under TrustSec > Devices, assign devices to download policy.
- [Screenshot: Device TrustSec Assignment]
Step 6 – Configure Network Device (Switch CLI)
conf t cts role-based enforcement cts role-based enforcement vlan-list 10-50 cts sxp enable cts sxp default password Cisco123 cts sxp connection peer 10.10.10.10 password Cisco123 mode local
Validate:
show cts role-based permissions show cts role-based sgt-map show cts sxp connections
Step 7 – Validate with Endpoint Authentication
- Connect endpoint to Access Switch.
- Authenticate via 802.1X/MAB → ISE assigns SGT.
- On Switch CLI:
show authentication sessions interface Gi1/0/1 details show cts role-based sgt-mapOutput should display SGT mapped for the user.
FAQs – Cisco ISE TrustSec Overview & Benefits
Q1. What is the key advantage of Cisco TrustSec compared to traditional VLAN/ACL segmentation?
TrustSec uses Security Group Tags (SGTs) instead of IP addresses or VLANs. Policies follow the user/device based on identity, not where they connect, making it far more scalable and dynamic.
Q2. Do I need DNA Center to implement TrustSec?
No. TrustSec can be fully deployed with Cisco ISE + supported switches/WLCs. Cisco DNA Center simply makes policy management and visibility easier, but it is not mandatory.
Q3. How are SGTs assigned to endpoints in ISE?
During the authorization phase of 802.1X, MAB, or Guest login. The ISE authorization policy determines which SGT is applied to the session. Static IP-to-SGT mapping is also possible for servers/printers.
Q4. How do I verify that an SGT is assigned to an endpoint?
- In ISE: Go to Operations > RADIUS > Live Logs, check the “Security Group” field.
- On Switch CLI:
show authentication sessions interface Gi1/0/1 details show cts role-based sgt-map
Q5. What is the difference between inline SGT tagging and SXP (SGT Exchange Protocol)?
- Inline tagging: Switches capable of embedding SGT in the packet header.
- SXP: Used when devices don’t support inline tagging; SGT-IP mappings are exchanged between devices.
Q6. Can TrustSec policies be enforced across a WAN or firewall?
Yes. If both ends support TrustSec, SGTs propagate. If not, SXP can carry mappings across WAN, and firewalls (ASA/FTD) can consume SGTs via pxGrid to apply SGACLs.
Q7. How do I configure a static IP-to-SGT mapping for a server that doesn’t authenticate?
In ISE:
- Navigate to Work Centers > TrustSec > Components > IP-SGT Mapping.
- Add the server IP and assign an SGT.
Validation:
show cts role-based sgt-map
Q8. What happens if two users with different SGTs are on the same VLAN?
TrustSec policies still apply because VLAN/IP doesn’t matter. Traffic between them is controlled by SGACLs, not by VLAN boundaries.
Q9. How do I troubleshoot if traffic is unexpectedly blocked by TrustSec?
- Step 1: Check ISE Live Logs to confirm SGT assignment.
- Step 2: Verify SGACL applied on switch:
show cts role-based permissions - Step 3: Ensure SXP session is up if inline tagging not used.
Q10. Is TrustSec only for large enterprises or can SMBs benefit too?
While often used in large enterprise & campus networks, SMBs with compliance or segmentation needs (e.g., separating POS systems, IoT, and employees) can also benefit from TrustSec without complex VLAN/ACL designs.
YouTube Link
For more in-depth Cisco ISE Mastery Training, subscribe to my YouTube channel Network Journey and join my instructor-led classes for hands-on, real-world ISE experience
Closing Notes
Cisco TrustSec provides dynamic, scalable, and identity-based segmentation far superior to VLANs and ACLs. With ISE as the central brain, enterprises can enforce uniform Zero Trust policies across wired, wireless, and WAN.
Upgrade Your Skills – Start Today
For more in-depth Cisco ISE Mastery Training, subscribe to my YouTube channel Network Journey and join my instructor-led classes.
Want to go Fast-Track to Cisco ISE Mastery Pro?
I run a focused a 4-month instructor-led CCIE Security training program covering Cisco ISE, Firewalls, VPN, and advanced security.
Check the full course outline here: Network Journey CCIE Security Training
This program is designed for engineers who want hands-on labs + exam prep + real-world design expertise → enroll now and accelerate your career!
Enroll Now & Future‑Proof Your Career
Email: info@networkjourney.com
WhatsApp / Call: +91 97395 21088

![Model-Driven Telemetry vs SNMP – Rethinking Network Monitoring [CCNP ENTERPRISE]_networkjourney](https://networkjourney.com/wp-content/uploads/2025/07/Model-Driven-Telemetry-vs-SNMP-–-Rethinking-Network-Monitoring-1.png)
![MST Region Configuration Explained: Streamlining Spanning Tree for Scalable Networks [CCNP Enterprise]](https://networkjourney.com/wp-content/uploads/2025/06/MST-Region-Configuration-Explained_Streamlining-Spanning-Tree-for-Scalable-Networks_networkjourney.png)
