[Day 72] Cisco ISE Mastery Training: Configuring Security Group Tags (SGTs)
Table of Contents
Introduction
Security Group Tags (SGTs) are the identity currency of Cisco TrustSec. Instead of binding policy to IPs/VLANs, ISE assigns an SGT (e.g., HR=10, Finance=20, Guest=30) to users/devices at authentication time. These tags travel (inline) or are distributed (via SXP) so switches, WLCs, and firewalls can enforce role-to-role policy (SGACLs) consistently—no matter where endpoints connect.
Today you’ll build the SGT foundation in ISE, map tags to identities and IPs, propagate them to the network, and validate the end-to-end path with GUI and CLI.
Problem Statement
Traditional NAC deployments hit walls with:
- ACL sprawl & VLAN explosion when modeling many roles.
- Mobility/roaming: IPs/VLANs change; policy shouldn’t.
- Un-auth devices (printers/IoT) still need role-based control.
- Multi-domain consistency (wired, wireless, WAN/DC) is hard.
You need identity-driven segmentation that scales and remains stable even as users roam, devices rotate subnets, and networks grow.
Solution Overview
ISE solves this by making SGT the policy handle:
- Define SGTs (names + numeric tags).
- Assign SGTs dynamically via Authorization Profiles during 802.1X/MAB/Guest/BYOD, or statically via IP-to-SGT for non-auth devices.
- Distribute SGTs to devices supporting inline tagging; use SXP (SGT Exchange Protocol) where inline isn’t available.
- Enforce role-to-role policy with SGACLs at egress devices (switches, WLC, firewalls).
- Operate/Validate with ISE Live Logs, Context Visibility, and device CLIs.
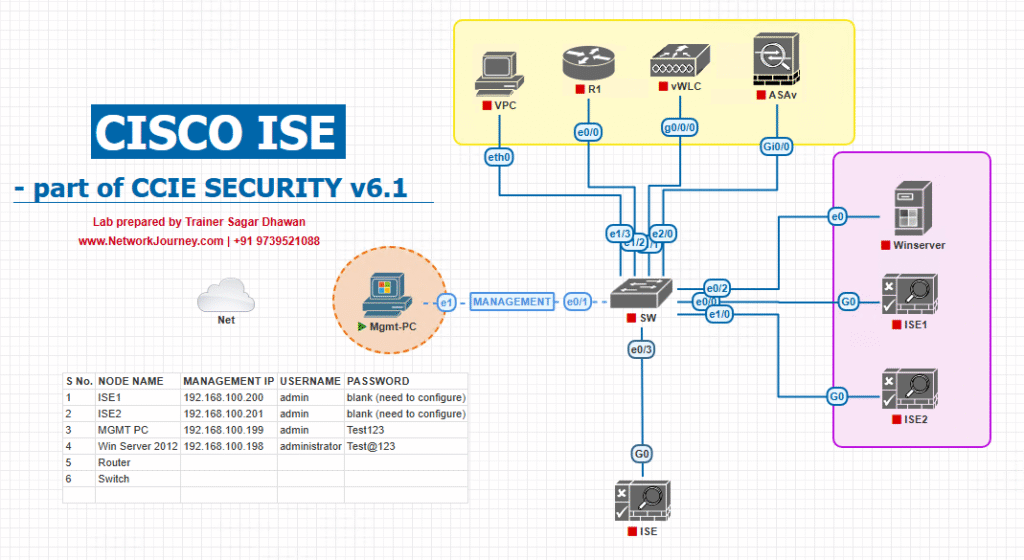
Sample Lab Topology
Platform: VMware/EVE-NG
Nodes:
- ISE 3.x (PAN+MnT) – 10.10.10.5
- AD/CA – 10.10.10.20 (users: HR/FIN groups; PKI optional)
- C9300 (Access) – 10.10.10.31 (inline SGT capable)
- C9500 (Core) – 10.10.10.41 (inline SGT + SXP “hub”)
- WLC 9800-CL – 10.10.10.50 (SSID Corp-WPA2-Ent)
- AP joined to WLC
- ASA/FTD (optional pxGrid/SGT consumer)
- Endpoints: Win10 (802.1X capable), Printer (non-auth), iPhone (802.1X)
Diagram:
Sample SGT plan:
- HR = 10, Finance = 20, IT = 30, Guest = 40, Printers = 50, Servers = 60
Step-by-Step GUI Configuration Guide (with CLI + Validation)
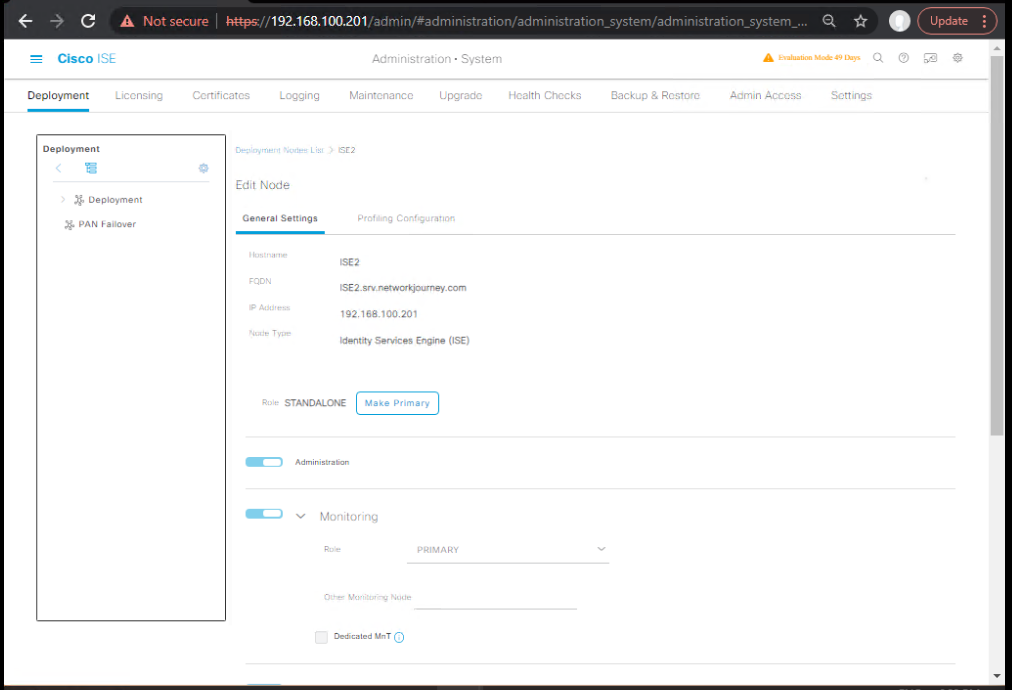
A) ISE Node & Devices Prep
- Enable TrustSec services (ISE):
Administration → System → Deployment → select ISE node → ensure TrustSec is enabled.
[Screenshot: ISE Deployment Node – TrustSec role]
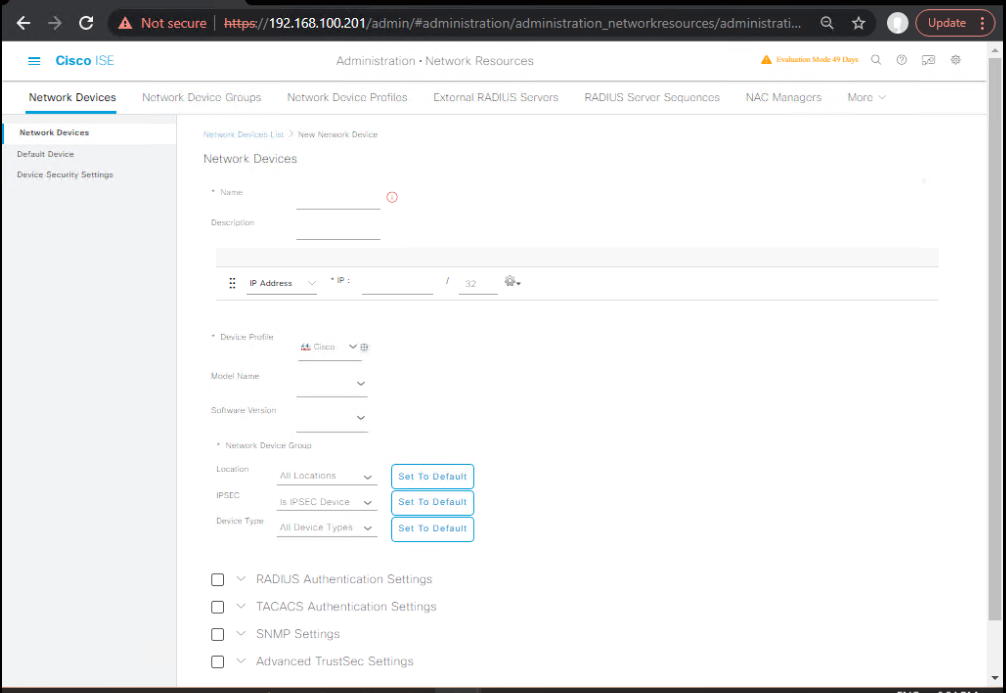
- Add Network Devices (WLC/Switches):
Administration → Network Resources → Network Devices → Add- Name/IP, RADIUS secret, CoA enabled.
- (Optional) TACACS unchecked.
[Screenshot: ISE Add Network Device]
Validation (ISE CLI):
show running-config | include network-device show logging application ise-trustsec.log tail
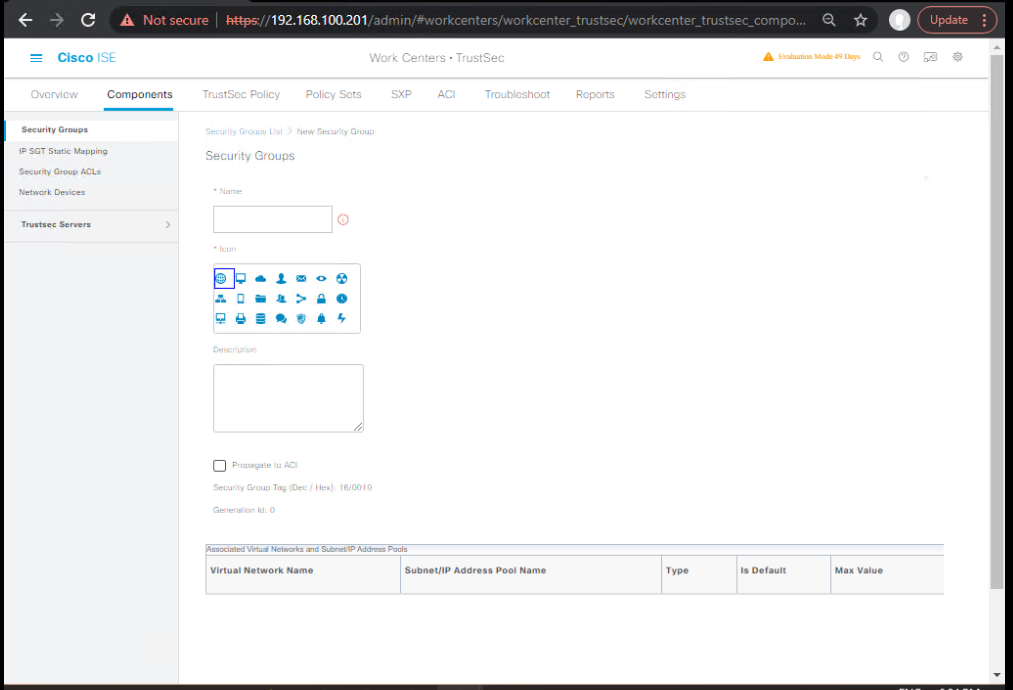
B) Create SGTs (ISE)
- Work Centers → TrustSec → Components → Security Groups → Add
- Create: HR(10), Finance(20), IT(30), Guest(40), Printers(50), Servers(60).
[Screenshot: ISE Security Groups List]
- Create: HR(10), Finance(20), IT(30), Guest(40), Printers(50), Servers(60).
- (Optional) Color/description for reporting clarity.
Validation (GUI): Groups appear with unique numeric tags.
Validation (CLI on Switch after download later):
show cts role-based sgt-map
C) IP-to-SGT Mapping (for non-auth endpoints)
- ISE: TrustSec → Components → IP SGT Static Mappings → Add
- Printer IP 10.20.50.15 → SGT Printers(50)
[Screenshot: ISE IP-SGT Mapping Screen]
- Printer IP 10.20.50.15 → SGT Printers(50)
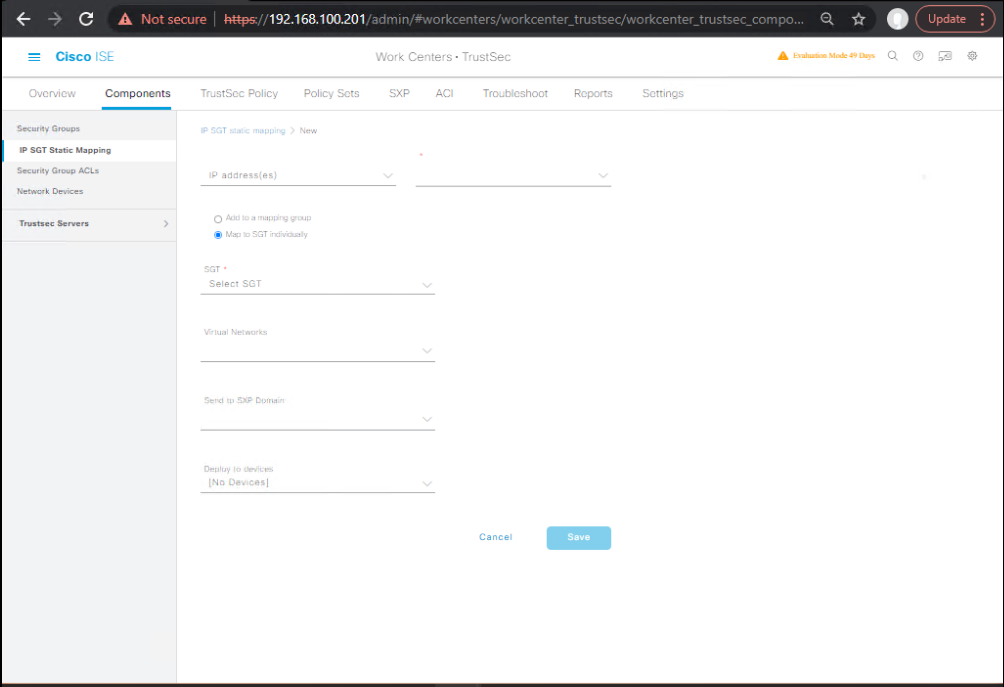
- (Optional) Add Servers subnet 10.30.0.0/24 → Servers(60).
Validation (Device after SXP):
show cts role-based sgt-map
D) Authorization Profiles that Assign SGTs
- Policy → Policy Elements → Results → Authorization → Authorization Profiles → Add
- Name:
AP-HR-SGT10, Security Group: HR(10), DACL/VLAN optional. - Repeat for Finance/IT/Guest.
[Screenshot: ISE Authorization Profile – SGT field]
- Name:
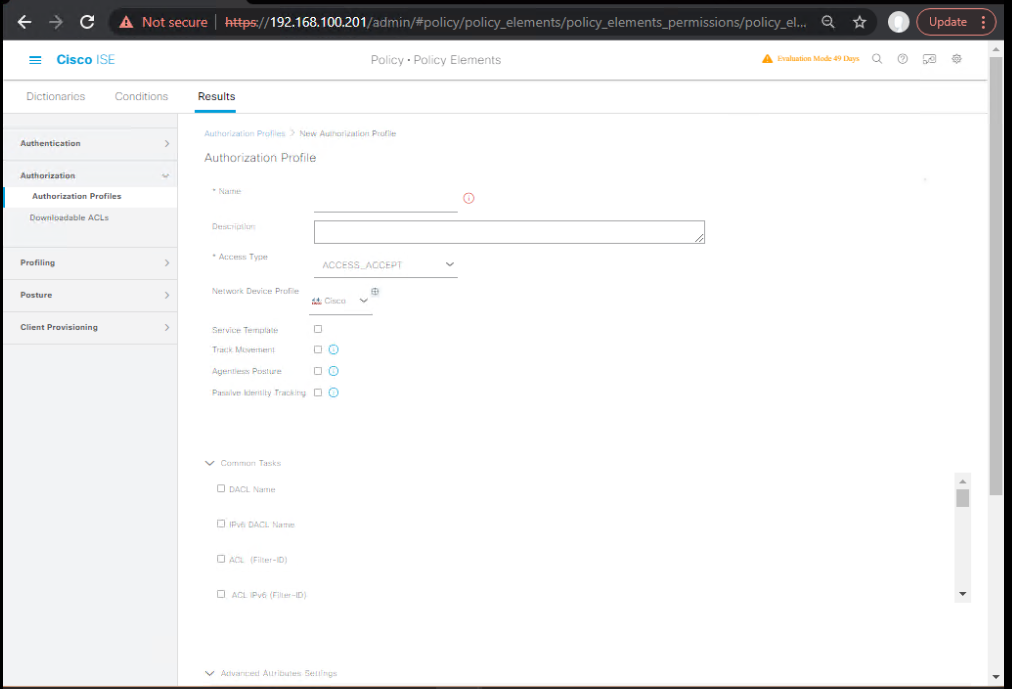
Tip: Keep SGT-only profiles (no VLANs/ACLs) for clean testing.
E) Policy Set for Wired/Wireless (SGT Assignment at AuthZ)
- Policy → Policy Sets → New Set
TrustSec-SGT-Assignment - Authentication Policy:
- 802.1X → AD as ID store
- MAB → Internal Endpoints (for labs)
[Screenshot: ISE Policy Set – AuthN Rules]
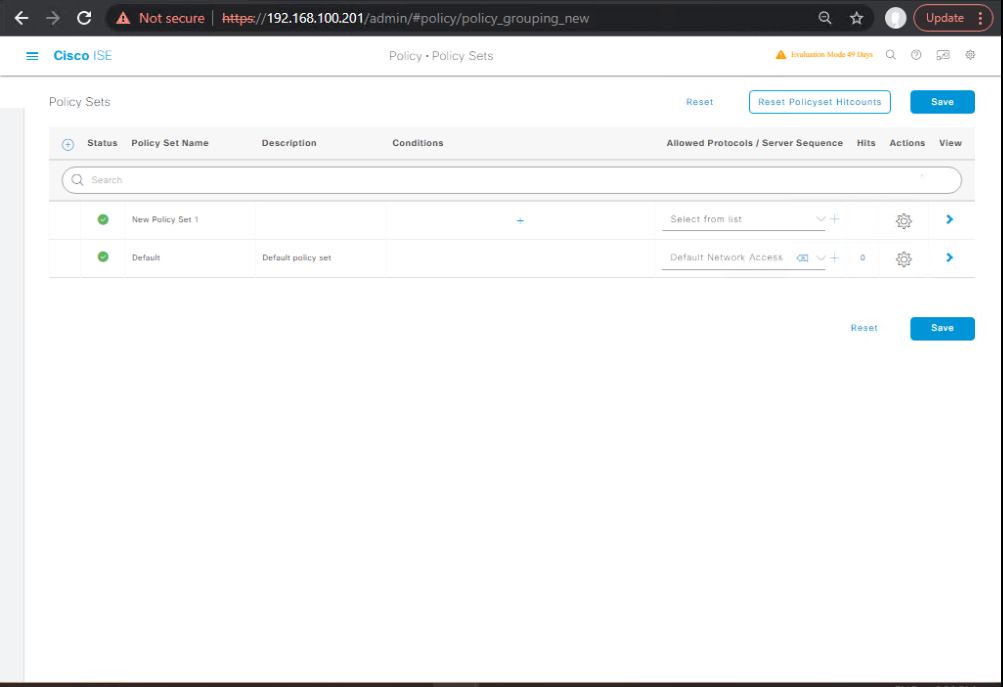
- Authorization Policy (top-down):
If AD:Group = HR→ AP-HR-SGT10If AD:Group = Finance→ AP-FIN-SGT20If DeviceProfile = Printer→ Printers(50) (or rely on IP-SGT)Else→ Guest(40)
[Screenshot: ISE Policy Set – AuthZ Rules with SGT column visible]
Validation (GUI):
Operations → RADIUS → Live Logs → check a successful session → Security Group column shows the tag.
[Screenshot: ISE Live Logs – Security Group column]
F) Push TrustSec Policy/Context to Devices
- Work Centers → TrustSec → Devices → add Access/Core/WLC devices to Download SGT/SGACL.
- Ensure pxGrid (if using ASA/FTD) is connected.
[Screenshot: TrustSec Devices – Download Status]
- Ensure pxGrid (if using ASA/FTD) is connected.
Validation (Switch CLI):
show cts environment-data show cts role-based permissions show cts role-based sgt-map show cts sxp connections ! if using SXP
G) Switch CLI (Access/Core) – Inline &/or SXP
Global:
conf t aaa new-model aaa authentication dot1x default group radius aaa authorization network default group radius radius server ISE1 address ipv4 10.10.10.5 auth-port 1812 acct-port 1813 key C1sco123 ip device tracking ! or 'device-tracking' (platform dependent) dot1x system-auth-control cts role-based enforcement cts sxp enable cts sxp default password Cisco123 cts sxp connection peer 10.10.10.41 password Cisco123 mode local ! Access->Core end wr
Interface (wired user on Gi1/0/1):
int gi1/0/1 switchport mode access authentication port-control auto mab dot1x pae authenticator spanning-tree portfast end
Validate (Switch):
show authentication sessions interface gi1/0/1 details show cts role-based sgt-map show cts role-based permissions show cts sxp connections
H) WLC 9800 – AAA + TrustSec Bits
- AAA/RADIUS:
Configuration → Security → AAA → RADIUS Servers → Add ISE (10.10.10.5, key).
[Screenshot: 9800 RADIUS Server]
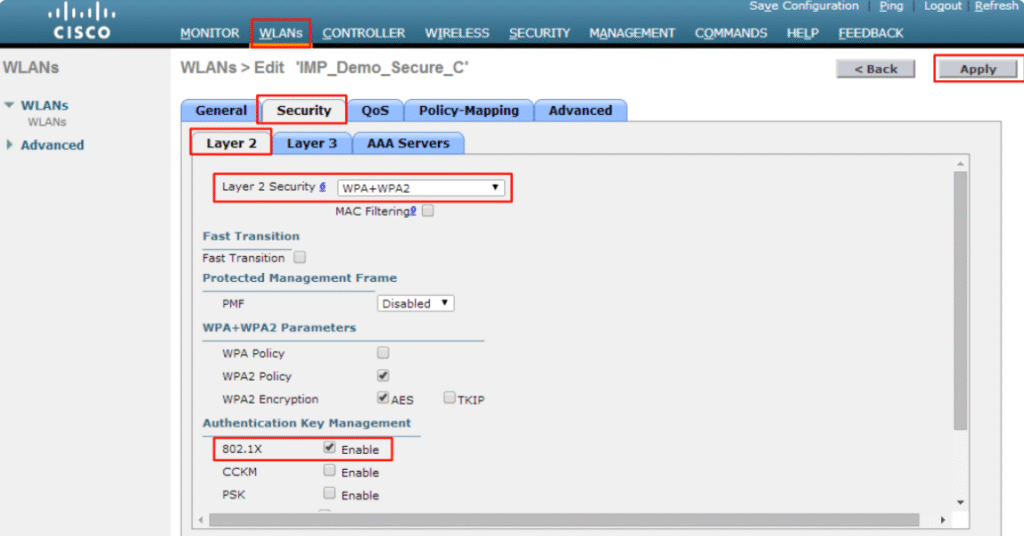
- WLAN (Corp-WPA2-Ent):
- Security → Layer2 = WPA2-Enterprise (802.1X)
- AAA tab → set ISE as AuthN/AuthZ server
[Screenshot: 9800 WLAN Security 802.1X]
- Policy Profile:
- Enable Central Auth (and Central Assoc if used)
- (Platforms/features permitting) enable TrustSec/SGT usage
[Screenshot: 9800 Policy Profile – TrustSec/SGT]*
Validate (WLC CLI):
show wireless client summary show wireless client mac <CLIENT-MAC> detail | include Policy|SGT
I) Functional Validation – End-to-End
- 802.1X user (HR) connects (wired or wireless):
- ISE Live Logs: Auth Success, Security Group = HR(10)
- Switch CLI:
show authentication sessions interface gi1/0/1 details | i Security Group Tag show cts role-based sgt-map | i <client-ip> - WLC CLI (wireless): check client details for applied policy/SGT.
- Printer (non-auth) traffic:
- Ensure IP-SGT mapping is visible on Access/Core (
show cts role-based sgt-map). - Ping/communicate according to SGACL (if configured).
- Ensure IP-SGT mapping is visible on Access/Core (
- Change user from HR→Guest:
- Update group/Authorization match → Reauthenticate in ISE Live Sessions.
- Verify updated SGT on switch/WLC (CoA event seen).
J) (Optional) Minimal SGACL for Proof
In ISE: TrustSec → Components → SGACLs → Add HR_to_Guest_Deny (deny ip).
Matrix: TrustSec → Policy Matrix → HR → Guest = HR_to_Guest_Deny.
Validate (Switch):
show cts role-based permissions | sec "HR(10)->Guest(40)" show cts role-based counters
Attempt HR→Guest traffic → should fail; reverse may succeed if allowed.
FAQs on Cisco ISE – Configuring Security Group Tags (SGTs)
Q1. What is an SGT in Cisco ISE, and how does it differ from traditional VLAN-based segmentation?
- Answer: An SGT (Security Group Tag) is a metadata label assigned to a user, device, or session. Unlike VLANs that segment traffic by network topology, SGTs apply policy dynamically, independent of physical network boundaries. This enables micro-segmentation, identity-based access control, and scalable policies without VLAN sprawl.
Q2. How do I configure a new Security Group Tag (SGT) in Cisco ISE?
- Answer:
- Navigate to Work Centers > TrustSec > Components > Security Group.
- Click Add.
- Provide Name, Description, and Tag ID.
- Save and verify the SGT is available in the list.
[Screenshot: Add New SGT Window]
Q3. Can I assign SGTs dynamically based on authentication results?
- Answer: Yes. You can use Authorization Policies in Cisco ISE to assign an SGT dynamically. For example:
- If a user authenticates via AD and belongs to “Finance”, assign SGT = Finance-SGT.
- If a device authenticates via MAB and is tagged as IoT, assign IoT-SGT.
[Screenshot: Policy Set with SGT Assignment]
Q4. How do I validate that SGTs are being applied to endpoints?
- Answer:
- In ISE, go to Operations > RADIUS > Live Logs.
- Check the Authorization Profile → ensure the SGT value is applied.
- On CLI (switch/WLC):
show cts role-based sgt-map show cts role-based permissions
Q5. How do I propagate SGTs across the network fabric?
- Answer: SGTs are distributed via SGT Exchange Protocol (SXP) or inline tagging (802.1AE / MACsec capable devices).
- Configure SXP on Cisco ISE and switches:
cts sxp enable cts sxp connection peer 10.1.1.5 password cisco mode local speaker[Screenshot: ISE SXP Connection Config Screen]
Q6. Can SGTs be enforced on wireless users?
- Answer: Yes. Cisco WLC integrates with ISE and applies SGTs to wireless sessions. You must configure the WLC as a TrustSec device in ISE and ensure SGT Exchange is enabled. Then, policies apply equally to wired and wireless users.
Q7. How do I configure role-based access policies using SGTs?
- Answer:
- In ISE: Work Centers > TrustSec > Policy Matrix.
- Select Source SGT → Destination SGT.
- Define action: Permit, Deny, or Redirect.
[Screenshot: TrustSec Policy Matrix Window]
On CLI (switch):show cts role-based permissions
Q8. What happens if a device doesn’t receive an SGT?
- Answer: The device will either default to the Unknown SGT (tag 0) or follow the fallback authorization profile. Best practice: always configure a catch-all authorization rule to assign a default SGT for unclassified traffic.
Q9. How do I monitor and troubleshoot SGT deployment in Cisco ISE?
- Answer:
- Use ISE Live Logs to confirm SGT assignment.
- On switches/WLC:
show cts environment-data show cts role-based counters- In ISE GUI: Operations > TrustSec Reports.
Q10. Can SGTs integrate with firewalls for end-to-end policy enforcement?
- Answer: Yes. Cisco Firepower, ASA with Firepower Services, and FTD can consume SGTs via pxGrid integration. This allows end-to-end, identity-based segmentation from access to firewall enforcement.
YouTube Link
For more in-depth Cisco ISE Mastery Training, subscribe to my YouTube channel Network Journey and join my instructor-led classes for hands-on, real-world ISE experience
Closing Notes
You now have a production-grade SGT foundation: tags defined, assigned dynamically at auth, statically for non-auth devices, propagated via inline/SXP, and validated with ISE logs and device CLIs. This is the prerequisite for scalable role-to-role enforcement using SGACLs across wired/wireless/DC.
Upgrade Your Skills – Start Today
Level-up from “working” to “expert.”
- Subscribe to Network Journey on YouTube for weekly ISE deep dives.
- Fast-Track to Cisco ISE Mastery Pro – a 4-month, instructor-led program (labs in VMware/EVE-NG, design + troubleshooting playbooks, interview prep).
- Seats are limited. Review the CCIE Security course outline and apply now:
➤ course.networkjourney.com/ccie-security/ - Bonus for enrollees: TrustSec/SGT Lab Pack (topology, configs, validation worksheets) + live Q&A.
Enroll Now & Future‑Proof Your Career
Email: info@networkjourney.com
WhatsApp / Call: +91 97395 21088



