[Day 74] Cisco ISE Mastery Training: TrustSec Policy Matrix
Table of Contents
Introduction
Cisco TrustSec changes the game by letting us write security policies based on identity (SGT) instead of network constructs like IP or VLAN.
The Policy Matrix is the central brain: a two-dimensional grid where rows = source SGT, columns = destination SGT, and each cell = SGACL rule (Permit/Deny/Custom).
Think of it like a firewall ACL table, but centralized in ISE and pushed automatically to your switches/firewalls.
This eliminates IP ACL sprawl and makes zero-trust segmentation scalable.
Problem Statement
Traditional ACL-based segmentation fails because:
- Every IP change requires ACL edits.
- Rules multiply as endpoints/VLANs grow.
- Policy is fragmented across devices → hard to audit.
- Enforcing “only Finance can talk to DBs” takes 20+ IP ACL entries across multiple firewalls.
TrustSec Policy Matrix solves this by:
- Expressing intent in SGT language (Finance → DB: Permit 443).
- Compiling into SGACLs automatically.
- Distributing from ISE → all devices consistently.
Solution Overview
Cisco ISE lets you:
- Define SGTs = labels for identities (Employees, Guests, Finance, Servers, Printers).
- Write SGACLs = reusable ACL contracts (e.g.,
ALLOW-HTTPS,ALLOW-PRINTING,ALLOW-COMMON-INFRA). - Map SGACLs into the Matrix (SGT→SGT).
- Deploy to Devices (Catalyst, ASA/FTD, WLC).
- Validate enforcement with GUI counters and CLI
show ctsoutputs.
Sample Lab Topology
Platform: VMware ESXi + EVE-NG
ISE: Cisco ISE 3.x (PAN+MnT)
Switches:
- Access: Catalyst 9300 (C9300-A)
- Core/Distribution: Catalyst 9500 (C9500-D)
WLC: 9800-CL in EVE-NG
Endpoints: - Wired: Win10 PC (802.1X → Employees SGT), Printer (MAB → Printers SGT)
- Wireless: Win11 laptop (SSID mapped to Guests SGT)
Optional: ASA/FTD as TrustSec listener
Step-by-Step GUI Configuration Guide + CLI Validation
Step A: Prereqs
- Sync time/NTP across all devices and ISE
- 802.1X/MAB already working (endpoints getting SGTs from ISE)
- Access switches exporting SGT mappings via SXP to ISE (Day 73 config)
Check on switch:
show authentication sessions interface Gi1/0/10 details show cts role-based sgt-map ip 10.10.20.50
Expected: Endpoint 10.10.20.50 has SGT=Employees(2)
Step B: Define Security Groups (SGTs)
ISE GUI:
- Navigate: Work Centers → TrustSec → Components → Security Groups → Add
- Create:
- Employees (2)
- IT-Admins (5)
- Finance (10)
- Printers (15)
- Servers (20)
- Guests (30)
Validation CLI (switch):
show cts role-based sgt
Should list same SGTs synced from ISE.
Step C: Create SGACLs (Reusable Contracts)
ISE GUI:
- Work Centers → TrustSec → Components → Security Group ACLs → Add
Examples:
- ALLOW-COMMON-INFRA
permit udp dst eq 53 permit tcp dst eq 53 permit udp dst eq 67 permit udp src eq 67 permit udp dst eq 123 permit icmp - ALLOW-EMP-TO-SERVERS-HTTPS
permit tcp dst eq 443 - ALLOW-PRINT-MGMT
permit tcp dst eq 9100 permit tcp dst eq 515 permit tcp dst eq 631 - ALLOW-IT-FULL
permit ip
Validation CLI (switch):
show cts role-based access-list
Should show all SGACLs pulled from ISE.
Step D: Build TrustSec Policy Matrix
ISE GUI:
- Navigate: Work Centers → TrustSec → Policy → Policy Matrix
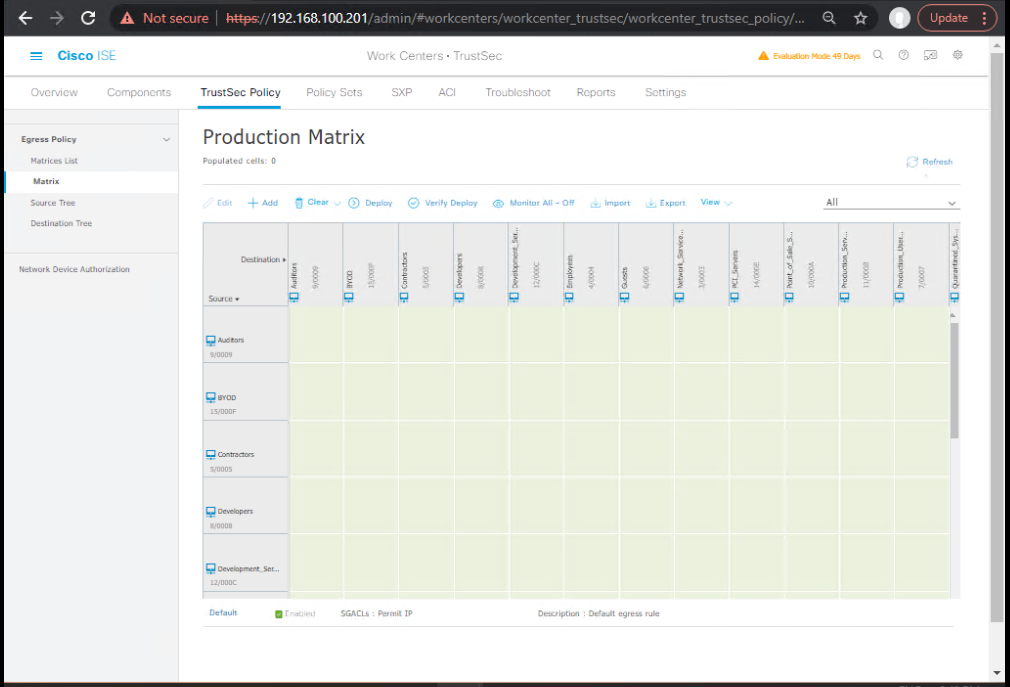
- Configure cells:
| Source SGT | Destination SGT | Action/SGACLs |
|---|---|---|
| Employees(2) | Servers(20) | ALLOW-EMP-TO-SERVERS-HTTPS + ALLOW-COMMON-INFRA |
| Employees(2) | Printers(15) | ALLOW-PRINT-MGMT + ALLOW-COMMON-INFRA |
| IT-Admins(5) | Any | Permit IP |
| Guests(30) | Servers(20) | Deny IP |
| Guests(30) | Finance(10) | Deny IP |
| Employees(2) | Employees(2) | ALLOW-COMMON-INFRA |
| Unknown(0) | Any | Deny IP (Zero-Trust default) |
Step E: Deploy Matrix to Devices
ISE GUI:
- Work Centers → TrustSec → Devices
- Select devices (C9300-A, C9500-D, ASA)
- Click Update/Deploy
Validation CLI (switch):
show cts role-based permissions
Should display compiled matrix, e.g.:
From SGT 2 to SGT 20 : permit tcp dst eq 443
permit udp dst eq 53
permit icmp
From SGT 30 to SGT 20: deny ip
Step F: Generate Traffic + Check Counters
On Catalyst:
show cts role-based counters show cts role-based counters from 2 to 20
- Run curl/https from Employees → Servers = Counter increments in permit.
- Run ssh from Employees → Servers = Counter increments in deny.
- Run ping from Guests → Servers = Counter increments in deny.
On ISE GUI:
- Operations → RADIUS Live Logs = shows SGT assignments.
- Work Centers → TrustSec → Policy → Policy Matrix → Counters = global view.
FAQs – Cisco ISE TrustSec Policy Matrix
1. How is the TrustSec Policy Matrix different from traditional ACLs?
The Policy Matrix is identity-based instead of IP-based. Traditional ACLs depend on IP addresses, VLANs, or subnets, which change frequently. TrustSec uses SGTs (Security Group Tags), which are static and tied to user/device roles. This makes policy simpler, portable, and consistent across the network.
2. Do I need to configure the policy in both directions (source → destination and destination → source)?
Yes. The matrix is unidirectional. If you permit Employees(2) → Servers(20) on HTTPS, the reverse (Servers → Employees) will still be denied unless you explicitly allow it. Always design policies with bidirectional flows in mind.
3. What happens if no SGACL is defined for a source/destination pair?
The default action is deny all traffic. TrustSec works on a zero-trust principle: everything is denied unless permitted by the matrix. That’s why many deployments include an “ALLOW-COMMON-INFRA” SGACL for DNS, DHCP, NTP, and ICMP.
4. How can I confirm if TrustSec enforcement is active on a switch?
Use the CLI:
show cts
Check for:
Global CTS Information
Role-based enforcement: Enabled
If enforcement is disabled, even though the policy matrix is downloaded, it won’t apply.
5. How do I validate if a specific SGT-to-SGT policy is working?
Run traffic and check counters:
show cts role-based counters from <src-sgt> to <dst-sgt>
You’ll see hit counts increment under permit or deny depending on the rule. This is the most reliable validation.
6. Why is traffic not being blocked even though I configured deny rules in the matrix?
Common causes:
- The endpoint doesn’t have an SGT assigned (check with
show cts role-based sgt-map). - The switch is not downloading SGACLs from ISE (
show cts role-based access-list). - Enforcement disabled (
show cts). - The traffic path bypasses a TrustSec enforcement device (e.g., routed via a non-CTS switch).
7. How are SGACLs merged when multiple rules apply?
ISE compiles all SGACLs applied to an SGT pair into a single effective ACL. Within a SGACL, order matters, but across SGACLs, the rules are merged logically. If there’s a conflict, deny takes precedence (secure-first approach).
8. What is the purpose of the “Unknown” SGT in the Policy Matrix?
The Unknown(0) tag represents traffic with no SGT classification (e.g., unauthenticated endpoints, non-SGT capable devices). Best practice: set Unknown → Any = Deny IP to prevent unauthorized traffic from bypassing policy.
9. Can I use the Policy Matrix with wireless users on a WLC?
Yes. Wireless clients get an SGT assigned via ISE (802.1X/MAB). The WLC then propagates the SGT to the network (via CAPWAP). Policies from the matrix will apply the same way as wired endpoints, as long as the WLC supports TrustSec.
10. What happens if a device in the path does not support TrustSec?
If traffic traverses a device that is not TrustSec-aware, SGT information may be lost (unless inline tagging is preserved). In that case:
- Use SXP to propagate mappings to that device.
- Ensure critical policy enforcement happens at the first TrustSec-capable hop after the endpoint.
YouTube Link
For more in-depth Cisco ISE Mastery Training, subscribe to my YouTube channel Network Journey and join my instructor-led classes for hands-on, real-world ISE experience
Closing Notes
- SGTs = identity
- SGACLs = reusable contracts
- Matrix = intent expressed once, enforced everywhere
- Always Deploy → Validate → Traffic Test → Counter Check
- Start with deny-by-default, then add needed contracts
Fast-Track to Cisco ISE Mastery Pro
I run a focused 4-month intensive program (real labs + designs + troubleshooting).
What’s inside:
- End-to-end Cisco ISE: 802.1X, MAB, Profiling, Posture
- Deep TrustSec: SGTs, SXP, Policy Matrix, Firewalls integration
- Brownfield migration scenarios + troubleshooting labs
- Weekly live sessions + recordings + graded workbook labs
- Interview prep + design case studies
For hands-on Cisco ISE Mastery, subscribe to my YouTube channel Network Journey and join live instructor-led labs.
Visit: https://course.networkjourney.com/ccie-security/
Enroll Now & Future‑Proof Your Career
Email: info@networkjourney.com
WhatsApp / Call: +91 97395 21088

![[Day 43] Cisco ISE Mastery Training: Wireless MAB Authentication](https://networkjourney.com/wp-content/uploads/2025/08/Day-43-Cisco-ISE-Mastery-Training-Wireless-MAB-Authentication.png)

