[Day 75] Cisco ISE Mastery Training: Applying TrustSec in Wired Networks
Table of Contents
Introduction
Wired networks still carry most enterprise East/West traffic, printers, IP phones, scanners, and user PCs. Cisco TrustSec replaces sprawling IP/VLAN ACLs with Security Group Tags (SGTs) and role-based enforcement. With ISE assigning SGTs at the port during 802.1X/MAB, your Catalyst switches can tag traffic at ingress and enforce centrally defined SGACL policy from the TrustSec Policy Matrix—right at the first hop.
Problem Statement
- ACL sprawl on access/distribution with overlapping rules and frequent IP churn.
- Mixed endpoints (PCs, printers, IP phones, scanners) often share ports → per-VLAN ACLs break easily.
- Auditing pain: “Who can talk to the DB?” becomes a witch-hunt across devices.
- Guest/contractor/on-boarding needs fast, safe access without new VLAN gymnastics.
Need: A port-anchored, identity-aware policy where SGTs follow the user/device regardless of IP or VLAN, are enforced consistently, and validated quickly.
Solution Overview
- ISE: Authenticates (802.1X/MAB), assigns SGT via Authorization Profiles, hosts the TrustSec Policy Matrix (SGT→SGT), and (optionally) redistributes IP↔SGT via SXP.
- Catalyst Access (C9300/9400): Applies role-based enforcement; inline-tags traffic with SGT on supported hardware.
- Distribution/Core/Firewall: Receives policy + mappings (inline or SXP) and enforces where required.
- You validate policy via ISE GUI counters and
show cts …CLI on switches.
Sample Lab Topology
Virtualization: VMware ESXi host running EVE-NG
ISE: ISE 3.x (PAN+MnT in one VM)
Switches:
- C9300-A (Access) – 802.1X/MAB, role-based enforcement ON, SXP speaker to ISE
- C9500-D (Distribution) – role-based enforcement ON, SXP listener from ISE
Endpoints (wired focus): - Win10-PC on Gi1/0/10 (802.1X → SGT Employees(2))
- Printer on Gi1/0/11 (MAB → SGT Printers(15))
- IP phone + PC on Gi1/0/12 (MDA: phone MAB to Voice-Phones(25), PC 802.1X to Employees(2))
(WLC 9800 optional; kept out of scope for wired focus.)
SGTs (examples): Employees(2), IT-Admins(5), Finance(10), Printers(15), Servers(20), Voice-Phones(25), Guests(30), Unknown(0)
Step-by-Step GUI Configuration Guide (+ CLI)
A) ISE & Device Prereqs
- Time/NTP synced on ISE and switches.
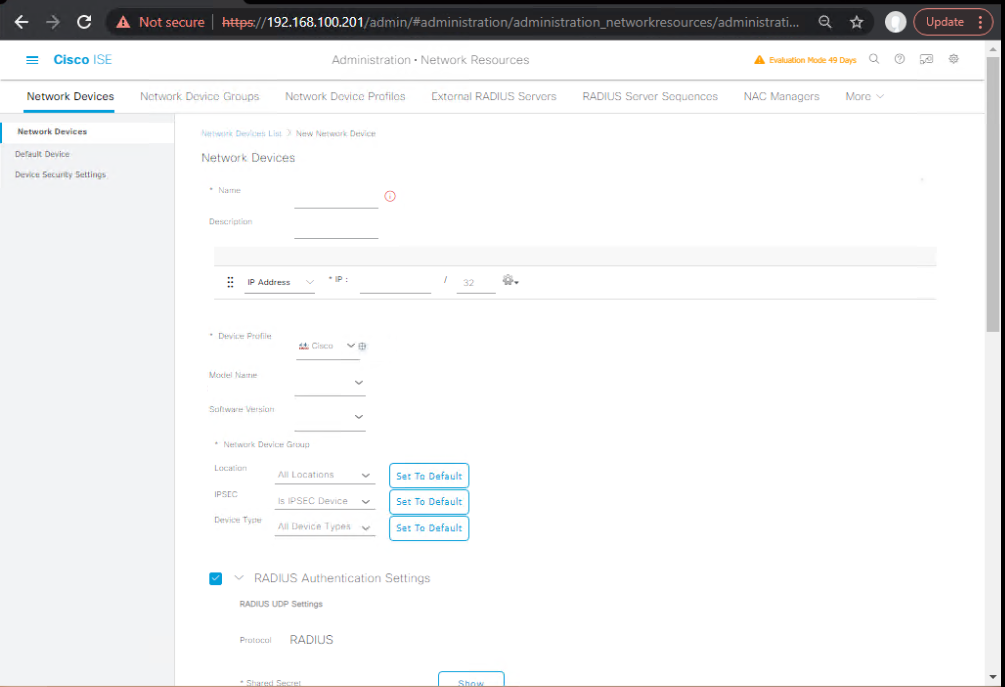
- Add network devices in ISE
- Administration → Network Resources → Network Devices → Add
- Check Enable TrustSec on each device; set RADIUS secret.
- [Screenshot: ISE Add Network Device with TrustSec enabled]
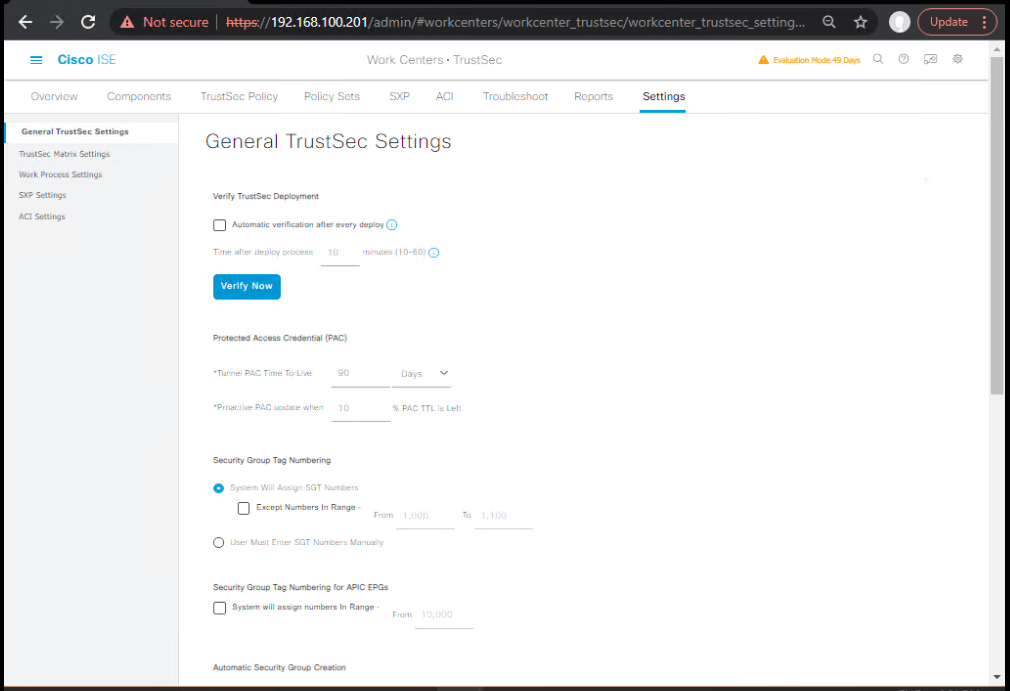
- Enable TrustSec services in ISE
- Work Centers → TrustSec → Settings → General → Enable TrustSec.
- [Screenshot: ISE TrustSec General Settings]
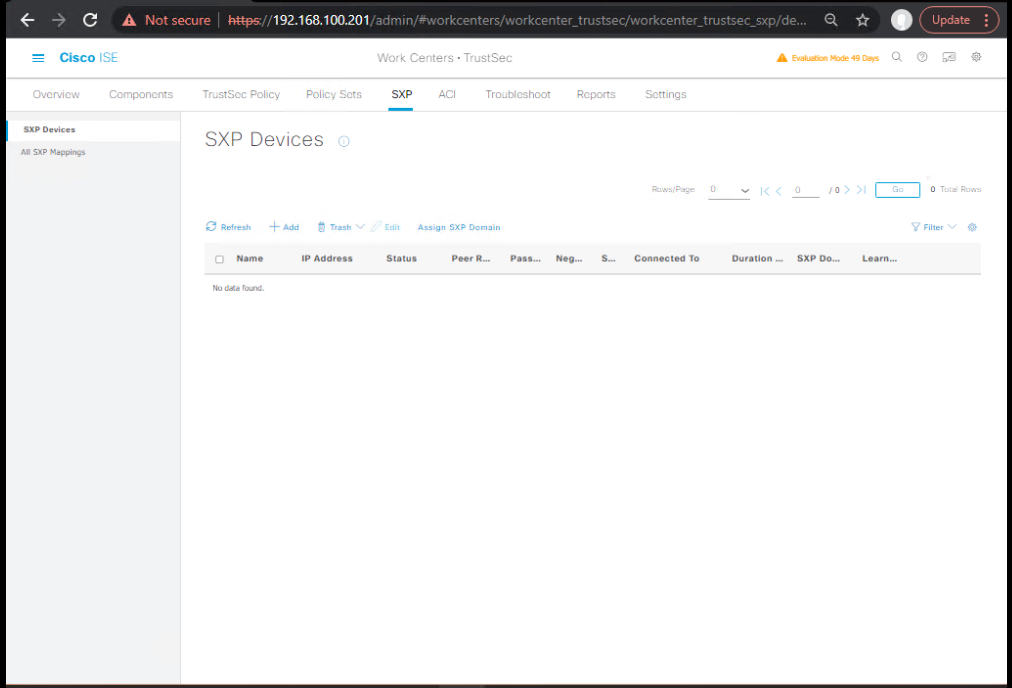
- (Optional for redistribution) Enable SXP
- Work Centers → TrustSec → SXP → Settings → Enabled, Port 64999, Version v4.
- [Screenshot: ISE SXP Settings]
Catalyst global baseline (AAA + CTS)
! AAA/RADIUS base (adapt for your environment) conf t aaa new-model aaa authentication dot1x default group radius aaa authorization network default group radius radius server ISE1 address ipv4 10.10.10.10 auth-port 1812 acct-port 1813 key 7 <your-key> ip radius source-interface Vlan10 ! Wired 802.1X/MAB defaults dot1x system-auth-control ! TrustSec global cts role-based enforcement ! enable RBP engine cts logging verbose ! helpful logs (lab) ! ! (Optional) SXP with ISE cts sxp enable cts sxp default source-ip 10.10.10.21 cts sxp connection peer 10.10.10.10 password 0 C!sco123 mode speaker version 4 end
Validate
show cts | i Role-based show cts sxp summary
Expected: Role-based enforcement: Enabled, SXP ON (if configured).
B) Define SGTs in ISE
- Work Centers → TrustSec → Components → Security Groups → Add
- Create: Employees(2), IT-Admins(5), Finance(10), Printers(15), Servers(20), Voice-Phones(25), Guests(30)
- [Screenshot: ISE Security Groups list]
Validate on switch
show cts role-based sgt
Expected: SGT names/IDs synced from ISE.
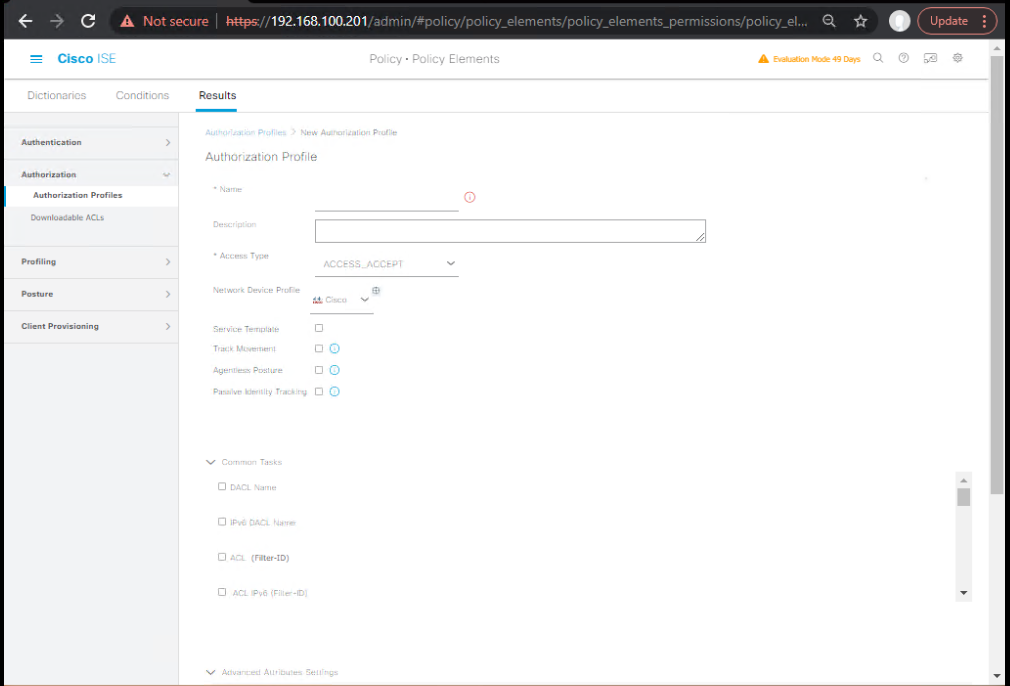
C) Create Authorization Profiles (assign SGT at authz)
- Policy → Policy Elements → Results → Authorization → Authorization Profiles → Add
- AP-EMP-SGT → SGT = Employees(2)
- AP-PRN-SGT → SGT = Printers(15)
- AP-VOICE-SGT → SGT = Voice-Phones(25)
- AP-ADMIN-SGT → SGT = IT-Admins(5)
- [Screenshot: ISE Authorization Profile with SGT attribute checked]
Tip: For MDA (phone+PC), use profiling/LLDP OUI to match phones → Voice SGT; user group → Employees SGT.
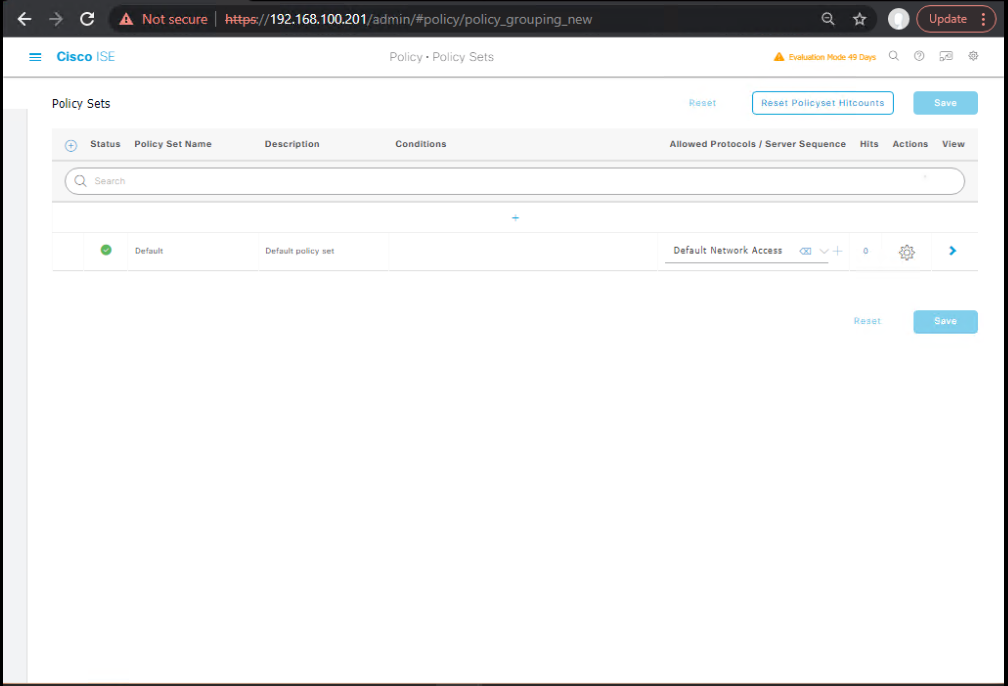
D) Build Policy Set (conditions → authz profile)
- Policy → Policy Sets → Create “WIRED-TRUSTSEC”
- Authentication Policy:
Wired_802.1X(PEAP/EAP-TLS) +Wired_MAB - Authorization Rules (top-down):
If Device-Profile = IP_Phone→ AP-VOICE-SGTIf AD-Group = Domain Users AND 802.1X→ AP-EMP-SGTIf MAB AND OUI=Printer→ AP-PRN-SGTElse→ DenyAccess or Quarantine/Guest as per lab
- Authentication Policy:
- [Screenshot: ISE Policy Set Screen]
- [Screenshot: ISE Authorization Rule with SGT Profile]
Validate in ISE
- Operations → RADIUS Live Logs: check session details show Security Group = Employees (or Printers/Voice).
- [Screenshot: ISE RADIUS Live Logs with SGT column]
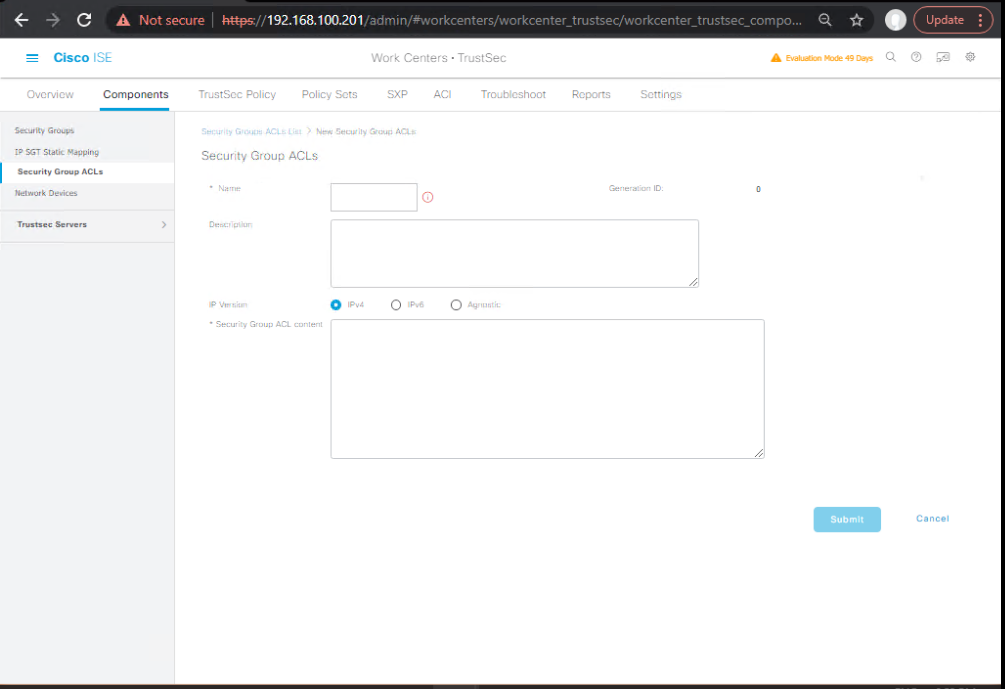
E) Craft SGACLs and the Policy Matrix
SGACLs (Work Centers → TrustSec → Components → Security Group ACLs → Add):
- ALLOW-COMMON-INFRA
permit udp dst eq 53 permit tcp dst eq 53 permit udp dst eq 67 permit udp src eq 67 permit udp dst eq 123 permit icmp - ALLOW-EMP-HTTPS-SSH-TO-SERVERS
permit tcp dst eq 443 permit tcp dst eq 22 - ALLOW-PRINT-MGMT
permit tcp dst eq 9100 permit tcp dst eq 631 permit tcp dst eq 515 - ALLOW-IT-FULL
permit ip - DENY-ALL
deny ip
Policy Matrix (Work Centers → TrustSec → Policy → Policy Matrix):
- Employees → Servers: ALLOW-EMP-HTTPS-SSH-TO-SERVERS + ALLOW-COMMON-INFRA
- Employees → Printers: ALLOW-PRINT-MGMT + ALLOW-COMMON-INFRA
- Voice-Phones → CallManager/Servers (if you have CM SGT): allow SIP/RTP or Permit IP in lab
- Guests → Any internal: DENY-ALL
- IT-Admins → Any: ALLOW-IT-FULL
- Unknown → Any: DENY-ALL
- [Screenshot: ISE TrustSec Policy Matrix Editing]
- [Screenshot: ISE Matrix Cell Details with attached SGACLs]
Deploy to devices
- Work Centers → TrustSec → Devices → All Devices → Select → Update/Deploy.
- [Screenshot: ISE TrustSec Devices – In Sync]
Validate on switches
show cts role-based permissions show cts role-based access-list
Expect to see compiled From SGT X to SGT Y entries and your SGACL names/ACEs.
F) Wire-Port Configs (802.1X/MAB + MDA + TrustSec)
Single host (PC 802.1X) – Gi1/0/10
conf t interface Gi1/0/10 description PC_8021X switchport access vlan 20 authentication port-control auto mab dot1x pae authenticator dot1x timeout quiet-period 5 dot1x max-req 3 access-session host-mode single-host access-session port-control auto spanning-tree portfast end ! ! (No per-port CTS needed; RBP is global and uses session SGT)
Printer (MAB) – Gi1/0/11
conf t interface Gi1/0/11 description Printer_MAB switchport access vlan 30 authentication port-control auto mab dot1x pae authenticator access-session host-mode single-host access-session port-control auto spanning-tree portfast end
Phone + PC (MDA) – Gi1/0/12
conf t interface Gi1/0/12 description Phone_plus_PC switchport access vlan 20 switchport voice vlan 40 authentication port-control auto mab ! for Phone first dot1x pae authenticator ! for PC 802.1X access-session host-mode multi-domain access-session port-control auto spanning-tree portfast end
Validation per port
show authentication sessions interface Gi1/0/10 details show authentication sessions interface Gi1/0/11 details show authentication sessions interface Gi1/0/12 details
Expect: Authorized; SGT present (Employees/Printers/Voice-Phones).
G) End-to-End Traffic & Counters Validation
1) Verify SGT mapping tables
show cts role-based sgt-map all | i 10.10. show cts role-based sgt-map ip 10.10.20.50
Expect: 10.10.20.50 -> Employees(2) (or appropriate IP/SGT).
2) Verify compiled permissions
show cts role-based permissions
Look for From SGT 2 (Employees) to SGT 20 (Servers): permit tcp dst eq 443,22 ...
3) Generate traffic & check counters
- From PC (Employees) to Server:
https://server(should permit),ssh server(permit if added). - From PC (Employees) to Printer: send test print (9100).
- From Guest (if any) to internal: expect deny.
Counters
show cts role-based counters show cts role-based counters from 2 to 20 show cts role-based counters from 2 to 15
Expect permit/deny counters increasing per SGT pair.
4) ISE GUI validations
- Operations → RADIUS Live Logs: sessions show Security Group column.
- Work Centers → TrustSec → Policy → Policy Matrix → Counters: per-cell activity.
- Work Centers → TrustSec → Devices: Status = In Sync.
- [Screenshot: ISE Live Logs with SGT]
- [Screenshot: ISE Policy Matrix Counters]
- [Screenshot: ISE Devices In-Sync]
H) (Optional) Distribution-Only Enforcement Pattern
If you prefer edge tags + core enforcement:
- Keep RBP enabled globally but no per-port special config (already fine).
- Ensure C9500-D has SXP listener from ISE (or receives inline SGT).
- Validate on C9500-D:
show cts sxp connections show cts role-based sgt-map ip 10.10.20.50 show cts role-based permissions show cts role-based counters
I) Hardening & Ops Tips
- Unknown(0) → Any = Deny in Matrix (zero-trust default).
- Use Allow-Common-Infra SGACL everywhere to prevent helpdesk noise (DNS/DHCP/NTP/ICMP).
- MDA: ensure phones profile correctly; LLDP/CDP helps.
- Timers: keep 802.1X defaults in prod; quicker in lab (quiet-period 5).
- Scopes: deploy to one switch first (TrustSec Devices → Update → Selected).
- Logging: export ISE MnT + switch syslog to SIEM for change tracking.
Perfect — here’s a deep-dive 10 FAQ set tailored to Day 75 – Cisco ISE Mastery Training: Applying TrustSec in Wired Networks, focused on real student + engineer lab/practical challenges.
FAQs – Applying TrustSec in Wired Networks
1. How do I confirm if my wired switch supports Cisco TrustSec?
Use:
show version show cts
Check for:
Role-based enforcement: EnabledSGT Exchange Protocol: Supported
Older Catalyst models (pre-3k) may not support inline SGT tagging, in which case you must rely on SXP bindings.
2. What is the difference between SGT assignment and SGACL enforcement on wired switches?
SGT assignment: The switch tags authenticated endpoints with the Security Group Tag received from ISE (show cts role-based sgt-map).
SGACL enforcement: The switch enforces traffic control based on the downloaded TrustSec Policy Matrix (show cts role-based access-list).
Both must be active for full TrustSec functionality.
3. Do I need 802.1X everywhere to use TrustSec in wired networks?
Not strictly. You can use:
- 802.1X → best practice for users/laptops.
- MAB → for printers/IoT.
- Static IP-to-SGT mapping → fallback for non-authenticating devices.
But at least one method is needed to map the device → SGT.
4. How can I verify if an endpoint is receiving the correct SGT after authentication?
On the switch:
show authentication sessions interface Gi1/0/5 details show cts role-based sgt-map
You should see:Assigned SGT: <SGT number and name>
If missing, check ISE authorization rules and ensure the switch is properly registered as a TrustSec device.
5. What happens if a wired switch in the path doesn’t support TrustSec?
SGT tagging is lost unless:
- Inline tagging is supported end-to-end, or
- You configure SXP to forward IP-SGT bindings to the next TrustSec-capable device.
Best practice: enforce SGACLs as close to the access switch as possible.
6. Can multiple endpoints on the same switch port have different SGTs?
No, on wired networks a single switch port can only carry one SGT at a time (port-based SGT assignment).
Workaround: use multi-auth mode on the switch (each device must authenticate separately). Otherwise, all endpoints share the same SGT.
7. How do I troubleshoot when SGACLs are not being enforced on wired switches?
Checklist:
- Run
show cts→ confirm enforcement enabled. - Run
show cts role-based access-list→ confirm SGACLs downloaded. - Run
show cts role-based counters from <src-sgt> to <dst-sgt>→ confirm packet hits.
If still failing → check ISE TrustSec matrix and ensure the policy is not set to “Deny by Default” with missing rules.
8. Is TrustSec applied only on user traffic, or also on control traffic like DHCP/DNS?
TrustSec applies to all IP traffic. That means if you forget to explicitly allow DNS, DHCP, NTP in your matrix → endpoints may lose connectivity.
Best practice: create an infra-allow SGACL for such services and apply it globally.
9. What is the performance impact of enabling TrustSec SGACLs on wired switches?
Minimal on modern Catalyst 9k switches (SGACLs are enforced in hardware TCAM).
On older platforms, scale limitations exist (e.g., max number of SGACL entries). Always check show platform hardware qfp active feature cts for usage and counters.
10. How do I validate end-to-end TrustSec in a wired lab setup?
Step-by-step:
- Authenticate endpoint via 802.1X/MAB.
- On access switch →
show authentication sessions(verify SGT assigned). - On distribution/core →
show cts role-based sgt-map ip <endpoint_IP>(binding present). - On enforcement switch →
show cts role-based counters(check hit counts). - Generate test traffic (e.g.,
ping,curl,iperf) and confirm it matches expected permit/deny rules.
YouTube Link
For more in-depth Cisco ISE Mastery Training, subscribe to my YouTube channel Network Journey and join my instructor-led classes for hands-on, real-world ISE experience
Closing Notes
You now have a wired TrustSec pipeline: ISE assigns SGTs → Catalyst tags & enforces → Matrix drives SGACLs → You prove it with counters and logs. Keep Unknown locked down, reuse Allow-Common-Infra, and always Deploy → Validate → Traffic Test.
Fast-Track to Cisco ISE Mastery Pro
I run a focused 4-month, instructor-led program designed as a hands-on sprint to production readiness.
You’ll master:
- Wired/Wireless 802.1X & MAB, Profiling, Posture
- TrustSec end-to-end: SGTs, SXP, Policy Matrix, wired enforcement patterns
- Brownfield migrations & break/fix playbooks
- Job-ready labs, graded workbooks, and interview prep
Get the full outline & next cohort: https://course.networkjourney.com/ccie-security/
For more in-depth Cisco ISE Mastery Training, subscribe to my YouTube channel Network Journey and join my instructor-led classes for live labs, design reviews, and troubleshooting drills.
Enroll Now & Future‑Proof Your Career
Email: info@networkjourney.com
WhatsApp / Call: +91 97395 21088



