[Day 76] Cisco ISE Mastery Training: Applying TrustSec in Wireless Networks
Table of Contents
Introduction
Cisco TrustSec (CTS) extends identity-based access control to the wireless network, ensuring that security group policies follow users regardless of where or how they connect. In a wireless environment, the challenge is higher: clients roam between access points, switch between VLANs, and scale into thousands of users. Without TrustSec, enforcing consistent policies across wired and wireless domains becomes almost impossible.
With Cisco ISE, SGTs (Security Group Tags) can be dynamically assigned to wireless users based on authentication results, then carried across the wireless fabric (via CAPWAP tunnels, inline tagging, or SXP) to ensure that policy enforcement is identity-based, not IP-based.
Problem Statement
Traditional WLAN security relies on VLAN mapping or ACLs pushed to the WLC (Wireless LAN Controller).
Problems:
- VLAN sprawl when mapping each user group to different VLANs.
- ACL scalability limits on WLCs.
- Difficulty in maintaining consistent policies across wired + wireless.
- Roaming clients often break VLAN-based security models.
The real-world issue: Enterprises need centralized identity-based policy enforcement across wireless and wired users, without VLAN or ACL sprawl.
Solution Overview
Cisco ISE integrates with Cisco WLCs to:
- Authenticate wireless users via 802.1X or MAB.
- Dynamically assign SGTs based on identity, posture, device type, or AD group.
- Enforce policies via TrustSec SGACLs at the WLC or downstream switches.
- Maintain seamless enforcement during client roaming.
Wireless traffic is tagged either inline (CAPWAP SGT) or through IP-to-SGT mapping (SXP) for non-TrustSec devices.
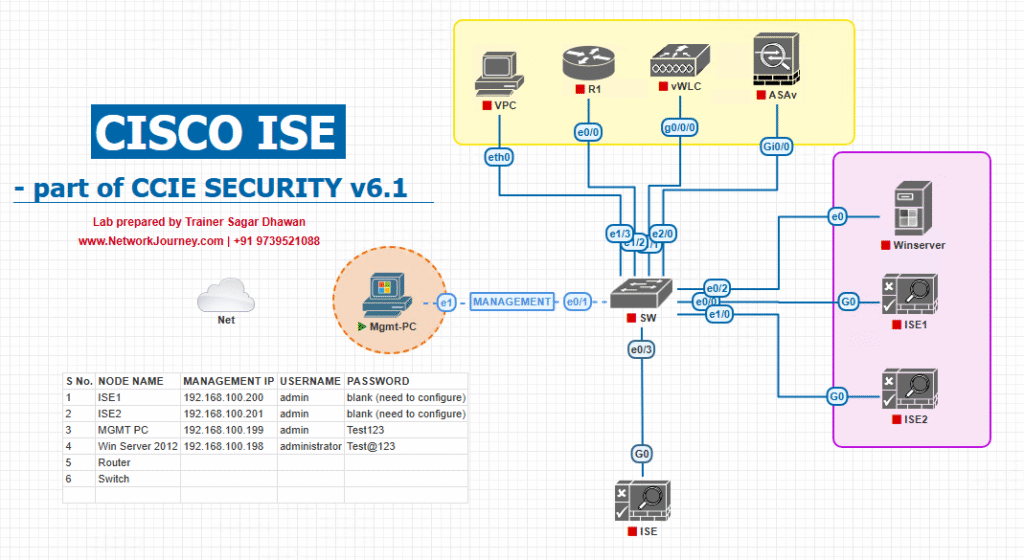
Sample Lab Topology
Lab Setup (EVE-NG / VMware):
- Cisco ISE VM (Policy Node, PxGrid, TrustSec enabled).
- Cisco 9800 WLC VM (or AireOS WLC if older).
- Catalyst Switch (C9300) → TrustSec enforcement enabled.
- Lightweight AP (virtual or physical) connected to WLC.
- Wireless Clients (Windows 10, iPhone, Android).
- AD/DNS Server VM for authentication integration.
Diagram:
Step-by-Step GUI + CLI Configuration Guide
Step 1 – Enable TrustSec on ISE
- Navigate: Work Centers → TrustSec → TrustSec Policy.
- Enable TrustSec.
- [Screenshot: ISE TrustSec Global Enable]
- Sync network devices (WLC, switches).
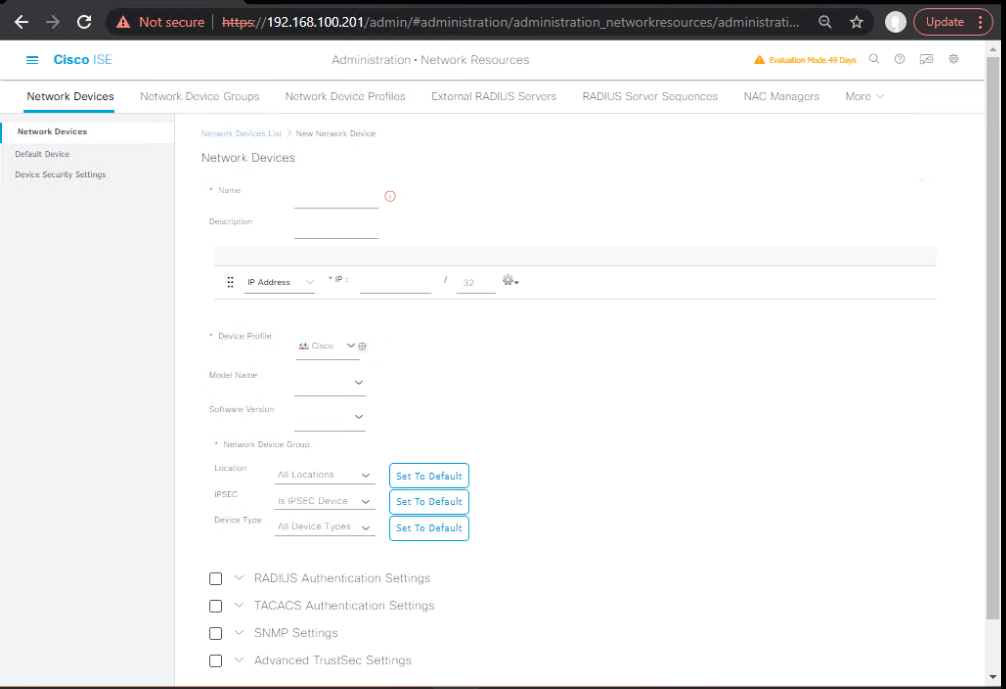
Step 2 – Add WLC to ISE
- Go to Administration → Network Resources → Network Devices.
- Add WLC’s IP, shared secret, enable RADIUS and TrustSec capabilities.
- [Screenshot: ISE Add WLC Screen]
Step 3 – Configure WLC for ISE Integration
On 9800 WLC (CLI):
conf t aaa new-model radius server ISE1 address ipv4 10.1.1.50 auth-port 1812 acct-port 1813 key cisco123 ! aaa group server radius ISE-GRP server name ISE1 ! aaa authentication dot1x default group ISE-GRP aaa authorization network default group ISE-GRP aaa accounting update periodic 5 aaa accounting network default start-stop group ISE-GRP
Step 4 – Enable CTS on WLC
conf t cts authorization list default cts role-based enforcement
Check:
show cts status
Step 5 – Configure WLAN for 802.1X + TrustSec
- In WLC GUI: Configuration → Tags & Profiles → WLANs → Create New.
- SSID:
ISE-TrustSec - Security: WPA2-Enterprise
- Authentication: 802.1X → ISE RADIUS
- Enable AAA Override.
- [Screenshot: WLC WLAN Security Config]
- SSID:
Step 6 – Configure SGT Assignment in ISE
- Navigate: Policy → Policy Sets → Authorization Policy.
- Add rules:
- Condition:
AD_Group = HR→ AssignSGT = HR-SGT. - Condition:
AD_Group = IT→ AssignSGT = IT-SGT. - [Screenshot: ISE Authorization Policy SGT Assignment]
- Condition:
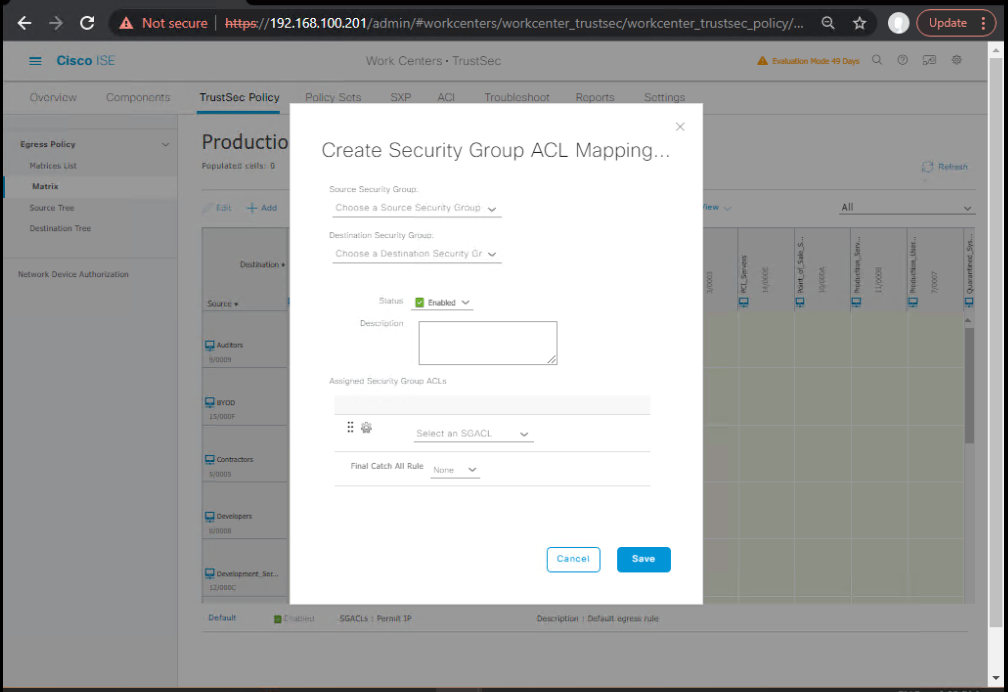
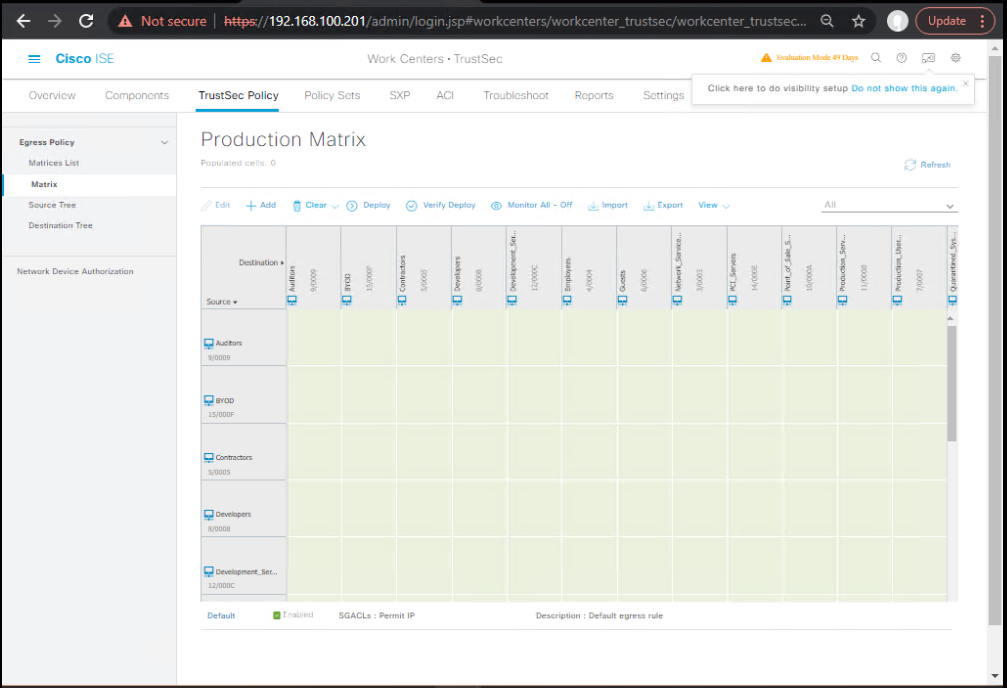
Step 7 – Configure TrustSec Policy Matrix in ISE
- Go to Work Centers → TrustSec → Policy Matrix.
- Define SGACL rules:
- HR → IT: Permit
- IT → HR: Deny
- HR → Internet: Permit
- Guest → Corp: Deny
- [Screenshot: ISE TrustSec Policy Matrix]
Step 8 – Download Policies to WLC
- In ISE → Work Centers → TrustSec → Network Devices.
- Push policy to WLC.
- On WLC CLI:
show cts role-based permissions
Step 9 – Validation (CLI + GUI)
- On ISE: Operations → Live Logs → Verify authentication and SGT assignment.
- On WLC CLI:
show wireless client mac <client-mac>
Check: Security Group Tag: .
- On Catalyst switch:
show cts role-based counters from <SGT-ID> to <SGT-ID>
Step 10 – Testing
- Connect wireless client to
ISE-TrustSecSSID. - Authenticate with AD credentials.
- Verify assigned SGT.
- Ping/curl test between HR and IT clients.
- Validate that SGACLs are enforced according to matrix.
FAQs – Applying TrustSec in Wireless Networks
1. How do I verify if a wireless client has received an SGT from ISE?
- On ISE: Go to Operations → Live Logs and check the authentication details → look for the “SGT” field.
- On WLC (9800 CLI):
show wireless client mac <client-mac> detail | include Security Group Tag - Expected Output:
Security Group Tag: 5 (HR-SGT)
2. Does the WLC enforce SGACLs, or must enforcement be pushed downstream to Catalyst switches?
- Answer: WLC9800 can enforce SGACLs locally.
- However, best practice is to offload enforcement to Catalyst switches for scale.
- Check on WLC:
show cts role-based permissions
3. Can a single SSID assign different SGTs to users based on identity?
- Yes. Same SSID → ISE Authorization Policy maps different AD groups / conditions → assigns different SGTs.
- Example:
- HR users on SSID
Corp-WiFi→ SGT 5 (HR-SGT). - IT users on same SSID → SGT 10 (IT-SGT).
- HR users on SSID
- This eliminates VLAN/SSID sprawl.
4. What happens if my AP or WLC does not support inline SGT tagging?
- Then SXP (SGT Exchange Protocol) is used.
- WLC sends IP-SGT mapping to ISE, which propagates to downstream switches for enforcement.
- Validate SXP:
show cts sxp connections show cts role-based sgt-map
5. How does roaming between APs affect SGT assignment?
- SGT is bound to the client session on WLC.
- When the client roams, the WLC preserves the SGT assignment as long as the RADIUS session remains alive.
- If the client re-authenticates, ISE re-assigns the SGT seamlessly.
6. How do I troubleshoot if SGACLs are not applied for wireless clients?
- Step 1: Confirm client got SGT (Live Logs + WLC client detail).
- Step 2: Check if WLC received SGACLs:
show cts role-based permissions - Step 3: Verify ISE → WLC TrustSec sync in Work Centers → TrustSec → Network Devices.
- Step 4: On Catalyst switch, check enforcement counters:
show cts role-based counters
7. How many SGACLs can a WLC enforce?
- 9800 WLC: Supports thousands of SGACL entries (depends on platform + scale license).
- AireOS: More limited → recommend enforcement at Catalyst switches.
- Always check Cisco scalability guides before production rollout.
8. Can I use MAB for wireless IoT/Headless devices with TrustSec?
- Yes. MAB devices can be profiled in ISE (e.g., printer, IP camera).
- ISE Authorization → assigns SGT based on profiling policy.
- Enforcement (SGACL) then applies normally.
- Validation:
- ISE Live Logs: See MAB + Profiling → SGT.
- WLC CLI: Check SGT binding with client MAC.
9. How do I validate TrustSec policy enforcement between two wireless clients?
- Connect two wireless clients to SSID → ensure different SGTs assigned.
- Use
pingorcurltests:- HR → IT = Denied (if SGACL denies).
- IT → HR = Allowed (if SGACL permits).
- On Catalyst switch/WLC:
show cts role-based counters from <SGT-ID> to <SGT-ID> - Counter increments confirm SGACL hit.
10. How should I handle Guest Wireless in TrustSec?
- Create a dedicated Guest SGT (e.g., 30).
- ISE Authorization Policy:
SSID=Guest-WiFi→ Assign Guest-SGT. - TrustSec Matrix: Guest → Corp = Deny.
- Guest → Internet = Permit.
- This provides clean separation without VLAN complexity.
YouTube Link
For more in-depth Cisco ISE Mastery Training, subscribe to my YouTube channel Network Journey and join my instructor-led classes for hands-on, real-world ISE experience
Closing Notes
- TrustSec in wireless networks eliminates VLAN sprawl and ACL nightmares.
- Policies are identity-based, not IP-based, and consistent across wired + wireless.
- WLCs + Catalyst switches + ISE = unified, scalable NAC + micro-segmentation.
Upgrade Your Skills – Start Today
“For more in-depth Cisco ISE Mastery Training, subscribe to my YouTube channel Network Journey and join my instructor-led classes.”
Fast-Track to Cisco ISE Mastery Pro:
I’m conducting a 4-month instructor-led CCIE Security program covering:
- Cisco ISE end-to-end (NAC, BYOD, TrustSec, PxGrid).
- SD-Access, Firepower, VPNs, and advanced security integrations.
- Real-world labs using VMware/EVE-NG.
Course details: Network Journey CCIE Security Training
Seats limited – reserve your spot today and take your ISE mastery to pro-level.
Enroll Now & Future‑Proof Your Career
Email: info@networkjourney.com
WhatsApp / Call: +91 97395 21088

![How to Lock Down Cisco Switch Ports with Port Security (2025 Guide)[CCNP ENTERPRISE]](https://networkjourney.com/wp-content/uploads/2025/06/nj-blog-post-portsec-switchport.jpg)
![[Day 55] Cisco ISE Mastery Training: EAP-TLS Wireless Certificate Authentication](https://networkjourney.com/wp-content/uploads/2025/08/Day-55-–-Cisco-ISE-Mastery-Training-EAP‑TLS-Wireless-Certificate-Authentication.png)
