[Day 8] Cisco ISE Mastery Training: Integrating ISE with Active Directory
Table of Contents
Introduction
Active Directory (AD) is the source of truth for user identities in most enterprises. Integrating Cisco ISE with AD lets ISE make real-time decisions based on user identity and group membership — mapping AD groups to network access policies, applying departmental VLANs, or enabling different access for contractors vs employees.
This lab shows you how to join ISE to AD, securely connect via LDAP/LDAPS, build identity source sequences, map AD attributes for policy decisions, test authentication flows (RADIUS + 802.1X), and validate everything with both GUI and CLI checks. The goal: after this session your ISE lab will be a fully functioning identity-aware NAC controller tied to AD.
Problem Statement
Without tight AD integration:
- Policies cannot use user/group information — only MAC or IP-based rules are possible.
- Admins resort to static VLANs and manual ACL changes when users change roles.
- Guest, BYOD and contractor workflows can’t provide temporary or role-based access easily.
- Troubleshooting is hard because you can’t correlate network events with usernames or groups.
Integrating ISE with AD removes these blindspots: it provides identity context for RADIUS decisions, enables group-based authorization, and centralizes policy enforcement.
Solution Overview
Cisco ISE integrates with AD by:
- Joining the AD domain (so ISE can authenticate and query the directory).
- Using LDAP / LDAPS to query user/group attributes and nested memberships.
- Building Identity Source Sequences — ordered lists of identity stores (AD → Internal Users) used during authentication.
- Mapping AD attributes into ISE policies (use AD group membership in Authorization Rules).
- Validating and logging all auth attempts (Live Logs) and troubleshooting with standard CLI checks (ping, nslookup, show application status).
We’ll implement a secure LDAPS flow, create a service account for LDAP queries, configure identity source sequences, and validate end-to-end with a test user authenticating via 802.1X or RADIUS.
Sample Lab Topology
Platform: VMware ESXi or EVE-NG.
Components (example IPs):
- ISE VM —
ise.lab.local—10.10.10.5 - Windows Server — AD + DNS + (optional) Certificate Authority —
ad.lab.local—10.10.10.10 - Catalyst Switch (IOSv-L2) —
10.10.10.2 - WLC (optional) —
10.10.10.20 - Windows Client (AD-joined) — DHCP in Employee VLAN — test user
alice@lab.local
Topology Layout:
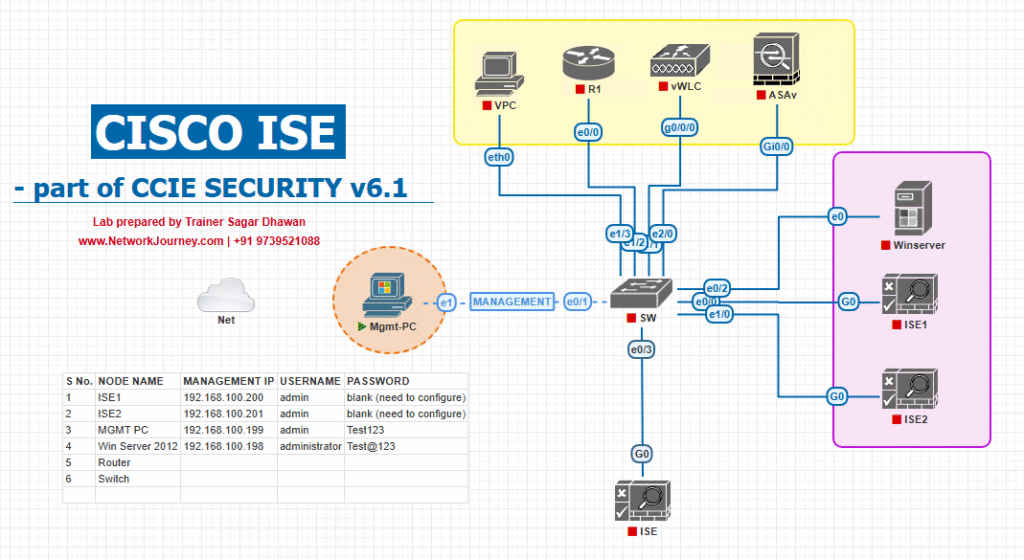
Notes:
- Ensure ISE and AD are on a routable management network and DNS resolves FQDNs.
- AD-joined client machines should trust the AD CA (if using LDAPS certs).
Step-by-Step GUI Configuration Guide (with validations)
Use the ISE Admin GUI for all AD join steps. After each major GUI step, run the CLI validation lines shown.
Pre-checks (console/CLI on ISE)
Run these from the ISE console before attempting to join AD:
ise/admin# ping 10.10.10.10 # confirm network reachability to AD ise/admin# nslookup ad.lab.local 10.10.10.10 # confirm DNS resolution via AD DNS ise/admin# show ntp status # ensure time sync (critical) ise/admin# show application status ise # ensure services running
If any of these fail — fix network/DNS/NTP first (common failure points).
Step 1 — Create a Service Account in AD (Windows Server side, lab guidance)
- On your AD server: open Active Directory Users and Computers.
- Create a user
svc_ise(password: strong & non-expiring for lab). - Permissions: For a simple lab, Domain Join rights are not strictly required if you just need LDAP read access; give
Readpermissions on user and group objects. For domain join (if ISE will actually join domain), the account needs rights to join a computer to the domain (or use Domain Admin for lab). Best practice: precreate an ISE computer account and delegate join rights tosvc_ise.
[Screenshot: ADUC create svc_ise]
Validation on AD: Ensure you can log in with svc_ise (non-interactive) or verify credentials by running:
# On Windows (as admin) Test-ComputerSecureChannel -Credential (Get-Credential DOMAIN\svc_ise)
(Optionally verify LDAP bind using ldp.exe.)
Step 2 — (Optional but recommended) Configure LDAPS on AD (CA & cert)
- If using LDAPS, the AD Domain Controller must have a certificate with Server Authentication EKU. Use AD CS to issue a certificate to the DC or use a public cert trusted by clients.
[Screenshot: AD CS — Issue cert to domain controller]
Validation: From a jump host:
openssl s_client -connect ad.lab.local:636 -showcerts
Expect to see a server certificate and chain.
Step 3 — Add Active Directory as External Identity Source in ISE (GUI)
- ISE GUI:
Administration → Identity Management → External Identity Sources → Active Directory→ Add (or Add Domain)
[Screenshot: Administration → Identity Management → Active Directory → Add]
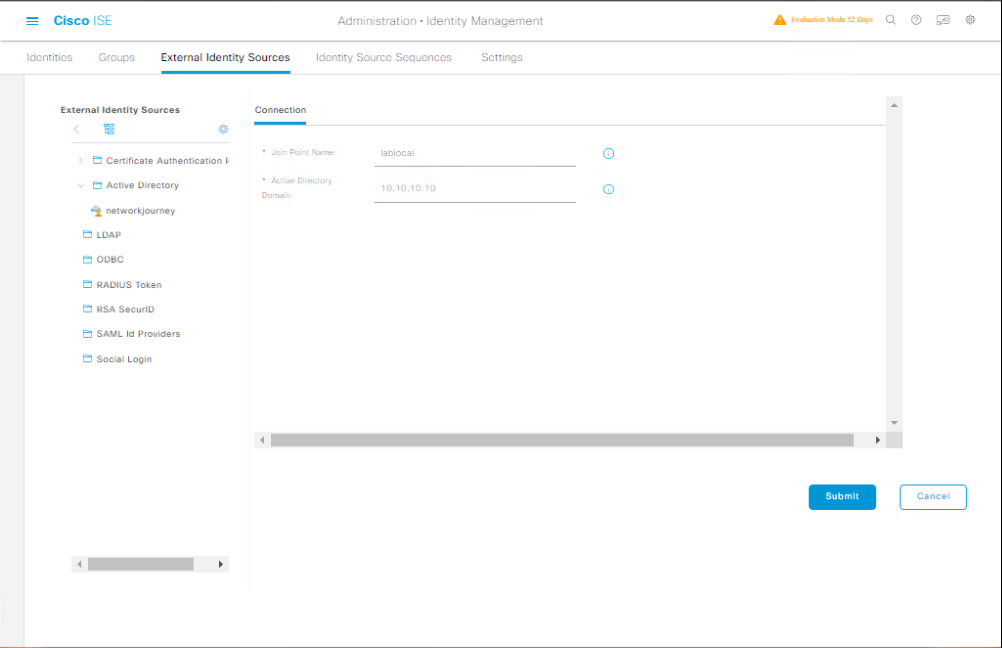
- Fill in:
- Domain Name:
lab.localorad.lab.localdepending on the UI version. - Domain Controller(s): add IP(s) or FQDN(s) e.g.,
10.10.10.10(click + to add multiple). - Service Account:
lab\svc_iseand the password you created. - Click Save (this creates the configuration entry).
- Domain Name:
- Click the Join button (often appears next to the domain entry). Provide the service account credentials again if prompted to join the domain. This performs the domain join operation.
[Screenshot: Active Directory Domain Join button]
Validation (GUI):
- The AD row should show Joined (green) and list reachable domain controllers.
- Expand the domain entry to show controller status and replication health if available.
CLI validation:
ise/admin# nslookup ad.lab.local 10.10.10.10 ise/admin# ping 10.10.10.10 ise/admin# show application status ise
If Join fails: check NTP (time skew), DNS (AD must be resolvable by FQDN), service account credentials, and firewall ports (TCP/UDP 389 for LDAP, 636 for LDAPS, Kerberos 88 if join needs Kerberos).
Step 4 — Test AD Connectivity from ISE
- In the AD domain row in ISE GUI, click Test Connection (or Test). This runs LDAP queries using your service account.
[Screenshot: Active Directory Test Connection]
Validation:
- Test should return success. Errors will show the reason (bad creds, timeout, TLS failure).
- If using LDAPS and test fails because of untrusted cert, import the AD root cert into ISE’s Certificate Authority store:
Administration → System → Certificates → Certificate Authority Certificates → Add.
CLI validation: (on ISE or jump host)
# from ISE console, verify DNS & ping again if GUI test fails ise/admin# nslookup dc1.lab.local 10.10.10.10 ise/admin# ping dc1.lab.local
Step 5 — Configure LDAP Group Lookup & Attribute Mapping (optional but common)
- GUI:
Administration → Identity Management → External Identity Sources → Active Directory→ click the domain → Configure → Attribute Mapping. MapsAMAccountName,memberOf,displayName, etc., as needed for policy.
[Screenshot: AD Attribute Mapping]
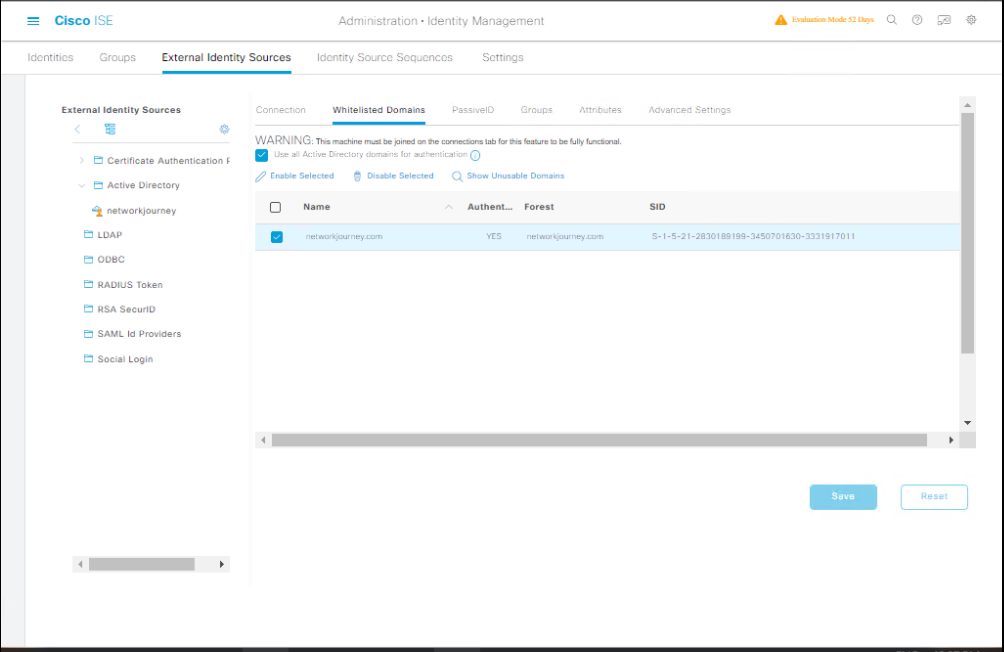
- If you need nested group resolution enable
Enable nested group lookup(ISE supports tokenGroups/global catalog lookups for nested groups). Use global catalog port 3268/3269 as needed.
Validation: Search for a user: Administration → Identity Management → Identities → Search → enter alice and view group membership returned from AD.
Step 6 — Create an Identity Source Sequence
- GUI:
Administration → Identity Management → Identity Source Sequences→ Add.- Name:
AD_then_Internal - Order: Active Directory → Internal Users
[Screenshot: Identity Source Sequence Creation]
- Name:
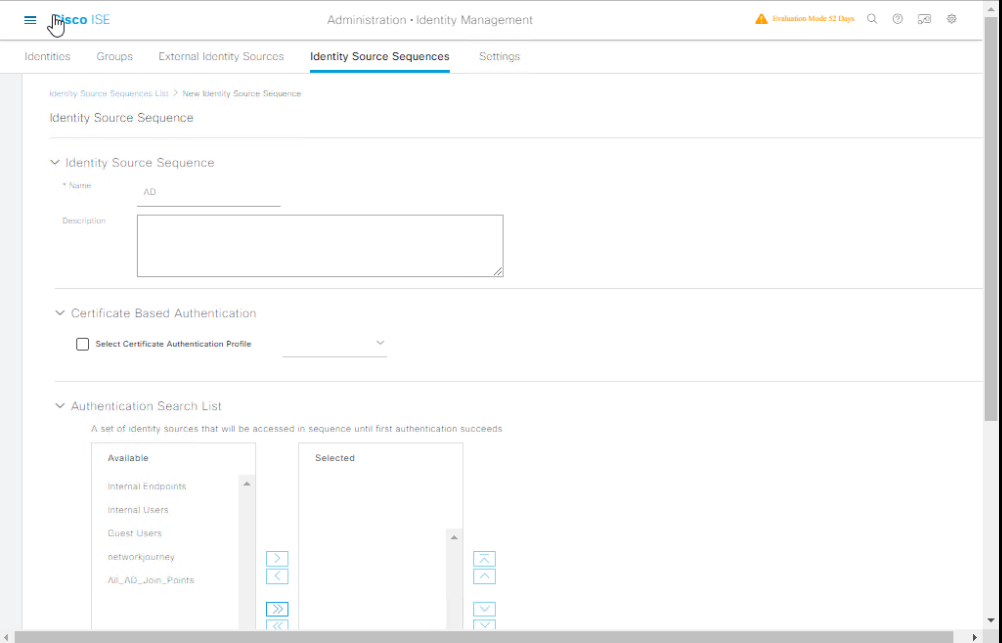
- Set this sequence as the identity source in your Authentication Policy or Policy Set (so ISE checks AD first then internal DB).
Validation: In Policy Sets (Policy → Policy Sets) ensure your authentication rule uses Identity Source Sequence AD_then_Internal.
Step 7 — Use AD Groups in Authorization Policy
- GUI:
Policy → Policy Sets→ open appropriate Policy Set → under Authorization, add rule:- Condition:
Authenticated Identity: Member Of→ select AD group (e.g.,lab\Employees) - Result: Authorization Profile →
Permit-Employee-VLAN10(which sets VLAN ID or downloadable ACL)
[Screenshot: Policy → Authorization Rule using AD group]
- Condition:
- Save & publish.
Validation: Trigger an auth attempt (wired 802.1X or test AAA from switch) and view Operations → RADIUS → Live Logs to verify that user was matched to the AD group and received the correct authorization result.
Step 8 — Test End-to-End Authentication (802.1X / RADIUS)
From a network device (IOS switch) — add ISE as RADIUS server & run a test:
! configure radius server ISE radius server ISE address ipv4 10.10.10.5 auth-port 1812 acct-port 1813 key cisco123 aaa group server radius ISE-GROUP server name ISE aaa authentication dot1x default group ISE-GROUP aaa authorization network default group ISE-GROUP # trigger a test request (IOS) test aaa group radius ISE-GROUP username alice password Al1ceP@ss new-code
Validation:
- On switch: check
show authentication sessionsfor the port that the client used:
show authentication sessions interface Gi1/0/1
- On ISE:
Operations → RADIUS → Live Logs— filter by username or client IP. You should see Access-Request and Access-Accept with attributes (Tunnel-Private-Group-ID or VLAN).
If test fails, check Live Logs for reason (bad credentials, no group match, AD cannot be contacted).
Step 9 — Multi-Domain / Cross-Forest Scenarios (brief)
- Add each domain as a separate Active Directory external identity source in ISE (repeat Step 3).
- Use Identity Source Sequence to order domains (e.g.,
corp.local, thenlab.local), or use global catalog for forest-wide queries.
Validation: Test users from each domain; Live Logs will show which domain resolved the user.
Step 10 — Housekeeping & Monitoring
- Enable AD Health Checks / Alerts:
Administration → System → Deployment→ Node → check health tabs. - Schedule AD Connectivity Tests: use ISE monitoring/alarm facility.
- Document service account credentials & rotate per policy (or use managed service account in production).
Validation CLI checks to run periodically:
ise/admin# show application status ise ise/admin# ping 10.10.10.10 ise/admin# nslookup ad.lab.local 10.10.10.10
FAQs – Cisco ISE & Active Directory Integration
1. Can Cisco ISE integrate with multiple Active Directory domains?
Yes, ISE supports joining multiple AD domains if they have trust relationships. Without trust, you’ll need to add each domain separately and map groups individually.
Tip: Always verify AD domain trust via nltest /domain_trusts on a domain-joined Windows machine.
2. What AD account permissions are needed for ISE integration?
ISE requires an account with permissions to join computers to the domain (Domain Join privilege) and read group membership attributes.
Best Practice: Use a dedicated service account, not your admin account.
3. Why does my ISE fail to join AD with a “Clock Skew” error?
Clock skew occurs if ISE and the AD domain controllers have a time difference of more than 5 minutes.
Fix:
ise/admin# show ntp ise/admin# configure terminal ise/admin(config)# ntp server <IP> prefer
Ensure both ISE and AD point to the same NTP source.
4. How do I validate AD integration from CLI?
After joining the domain, use:
ise/admin# show application status ise ise/admin# show logging application ise-psc.log tail ise/admin# show run | include ad
You can also test a login via the GUI → Administration > Identity Management > External Identity Sources > Active Directory > Test User.
5. Can ISE query nested AD groups?
Yes, ISE can read nested group membership if configured.
Tip: Enable “Retrieve Groups from User’s Primary Group Membership” in AD settings inside ISE.
6. How do I handle users from different OUs?
ISE doesn’t require you to specify OU paths. It queries the AD global catalog by default, but you can limit group search scope in the AD configuration settings.
7. What ports must be open between ISE and AD?
Key ports:
- TCP/UDP 88 (Kerberos)
- TCP/UDP 389 (LDAP)
- TCP 445 (SMB)
- TCP 3268 (Global Catalog)
- TCP 135 + dynamic RPC range
Tip: Test withtelnet <AD-IP> <port>.
8. How do I troubleshoot AD join failures?
- Check DNS resolution:
ise/admin# nslookup ad.domain.local
- Check time sync:
ise/admin# show ntp
- Review logs:
ise/admin# show logging application ise-psc.log
9. Can I map AD groups to ISE authorization policies?
Yes, after integration, ISE retrieves AD groups which can be used in Policy Sets > Authorization Policies. For example, you can map Domain Admins to an “Admin VLAN” and Employees to a “Corporate VLAN”.
10. What happens if AD is down? Will authentication fail?
If AD is unavailable, ISE cannot authenticate AD-based users, but local ISE accounts will still work.
Best Practice: Configure redundant AD servers and enable ISE’s Identity Cache to temporarily cache user group memberships.
YouTube Link
For more in-depth Cisco ISE Mastery Training, subscribe to my YouTube channel Network Journey and join my instructor-led classes for hands-on, real-world ISE experience
Closing Notes (Key takeaways)
- NTP & DNS first. These two items are the most common cause of AD join/authentication failures.
- Use LDAPS for production. Import CA root(s) into ISE trusted store.
- Create a least-privilege service account for LDAP binds; precreate or delegate computer join rights if ISE must join domain.
- Test incrementally: AD join → Test Connection → Identity Source Sequence → Authorization Policy → Live Logs. Validate at each stage with GUI and CLI.
- Add redundancy by specifying multiple DCs and consider global catalog for nested group resolution.
Fast-Track to Cisco ISE Mastery Pro
You’ve taken a critical step by linking identity to network access. If you want step-by-step mentorship, live labs and exam-focused guidance to turn these skills into a career advantage, join my instructor-led program.
I run a 4-month, instructor-led CCIE Security & ISE Mastery program with live labs in VMware ESXi / EVE-NG, graded assignments, one-to-one doubt sessions, and real-world scenarios designed to get you CCIE-ready and job-ready.
- Live weekly labs: deep dives on AD integration, EAP, BYOD, pxGrid.
- Personalized lab review: submit your lab topology; I give feedback during the eligibility call.
- Limited seats to keep instruction focused and detailed.
Reserve your free eligibility call & secure your seat:
https://course.networkjourney.com/ccie-security/ — submit your details and the Network Journey team will schedule a short lab review + roadmap session.
Enroll Now & Future‑Proof Your Career
Email: info@networkjourney.com
WhatsApp / Call: +91 97395 21088
![[Day 8] Cisco ISE Mastery Training: Integrating ISE with Active Directory](https://networkjourney.com/wp-content/uploads/2025/08/Day-8-Cisco-ISE-Mastery-Training-Integrating-ISE-with-Active-Directory.png)
![[Day 14] Cisco ISE Mastery Training: Setting Up a Test Switch for Authentication](https://networkjourney.com/wp-content/uploads/2025/08/Day-14-Cisco-ISE-Mastery-Training-Setting-Up-a-Test-Switch-for-Authentication.png)
![[Day 48] Cisco ISE Mastery Training: BYOD Wireless Onboarding Overview](https://networkjourney.com/wp-content/uploads/2025/08/Day-48-Cisco-ISE-Mastery-Training-BYOD-Wireless-Onboarding-Overview.png)
