[Day 80] Cisco ISE Mastery Training: Threat-Centric NAC Overview
Table of Contents
Introduction
Cisco’s Threat-Centric NAC (TC-NAC) takes network access control beyond authentication and authorization.
It integrates real-time threat intelligence from Cisco ecosystem tools (Firepower, AMP for Endpoints, Cisco SecureX, Talos, Stealthwatch) into Cisco ISE.
Why this matters:
- A user can be authenticated and authorized normally, but later infected by malware.
- Traditional NAC can’t react after initial access.
- TC-NAC enables dynamic session enforcement → Quarantine, block, or restrict the endpoint when it’s flagged as compromised.
This shifts ISE from identity-based NAC to threat-driven adaptive NAC.
Problem Statement
The Challenge:
- NAC grants access at login but has no visibility into post-admission compromise.
- Attackers often bypass traditional NAC by infecting trusted devices after authentication.
- Security teams need:
- Automated detection of compromised endpoints.
- Integration between threat detection tools and NAC enforcement.
- Real-time policy updates without manual intervention.
Without TC-NAC:
- Malware spreads laterally.
- SOC teams rely on manual incident response.
- Networks lack adaptive defense.
Solution Overview
Cisco ISE + TC-NAC Approach:
- Uses pxGrid (Platform Exchange Grid) to integrate with Cisco Threat Intelligence feeds.
- Security partners (Firepower, AMP, Talos, Stealthwatch, SecureX) send threat events to ISE.
- ISE updates endpoint Security Group Tags (SGTs) or Posture Status.
- Network devices enforce policy via SGACLs, VLAN change, dACLs, or quarantine VLAN.
Result:
- Endpoint compromised → flagged in Firepower/Talos → pxGrid → ISE session updated → switch/WLC enforces block/quarantine in real-time.
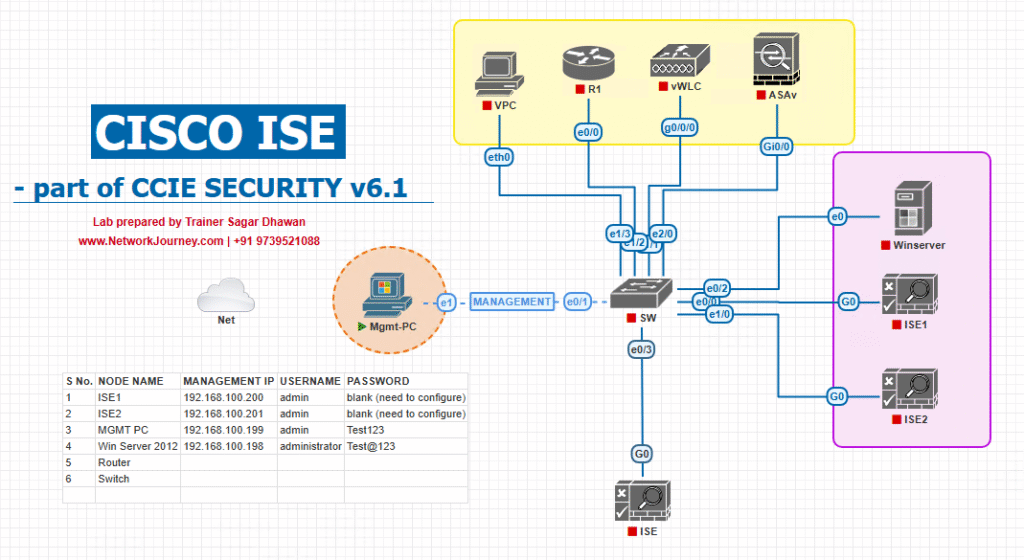
Sample Lab Topology
Lab Components (VMware/EVE-NG)
- ISE 3.x (PAN + PSN roles)
- WLC 9800 for wireless endpoints
- Catalyst 9300 switch for wired integration
- Firepower Management Center (FMC) + Firepower NGFW
- AMP for Endpoints / SecureX
- Endpoints: Windows 10 client + Ubuntu IoT device
Diagram:
Step-by-Step GUI + CLI Configuration Guide
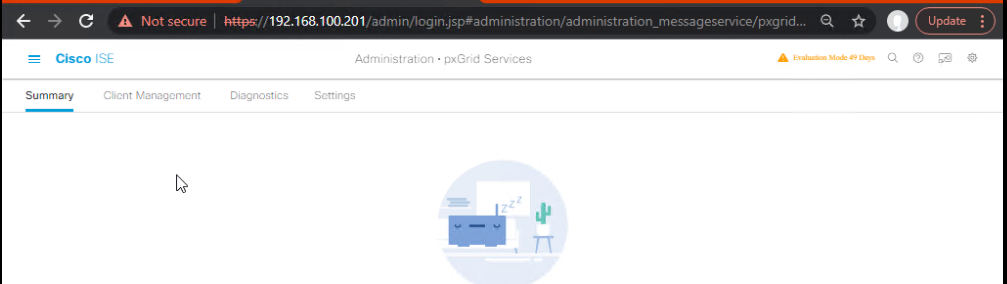
Step 1 – Enable pxGrid on ISE
- Navigate to Administration > pxGrid Services.
- Enable pxGrid Node.
- Check “Enable”
- Select certificate for pxGrid.
- Click Save.
[Screenshot: ISE pxGrid Services]
Step 2 – Register Firepower/AMP with ISE
- On Firepower FMC:
- Go to Integration > Identity Sources > pxGrid.
- Add ISE hostname/IP.
- Upload ISE pxGrid certificate.
- Test connectivity.
[Screenshot: FMC pxGrid Integration]
- On ISE:
- Approve the Firepower pxGrid client under pxGrid Clients.
[Screenshot: pxGrid Client Approval]
- Approve the Firepower pxGrid client under pxGrid Clients.
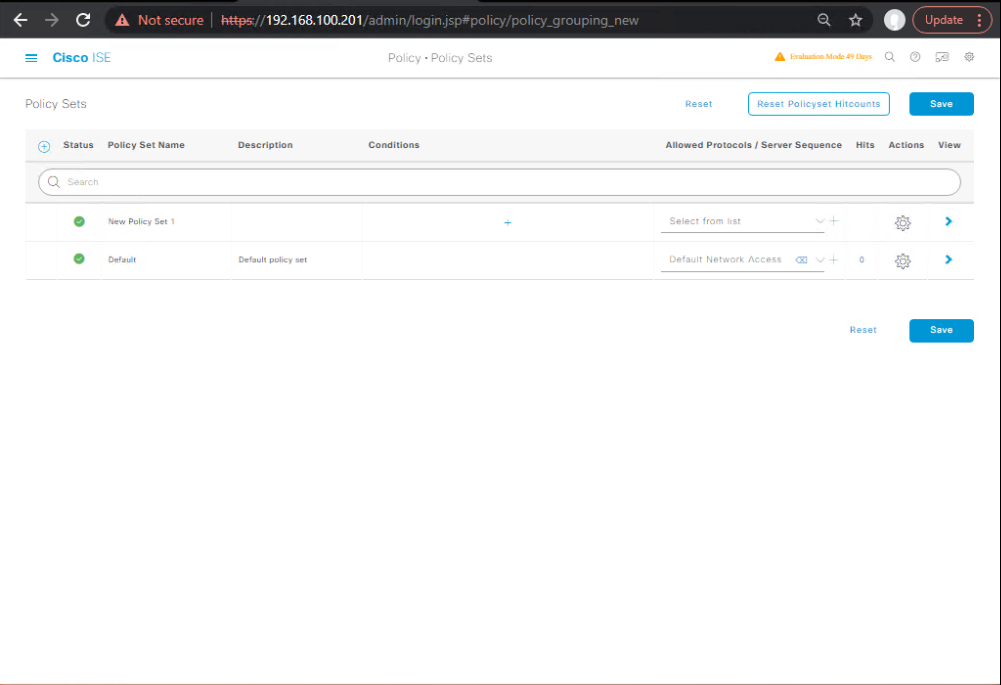
Step 3 – Create Adaptive Network Policy in ISE
- Navigate to Policy > Policy Sets > Authorization Policy.
- Add Rule:
- Condition:
Endpoint Threat = High(received via pxGrid). - Result:
Quarantine VLAN 150ORApply dACL - DenyAll.
[Screenshot: ISE Authorization Rule – Quarantine]
- Condition:
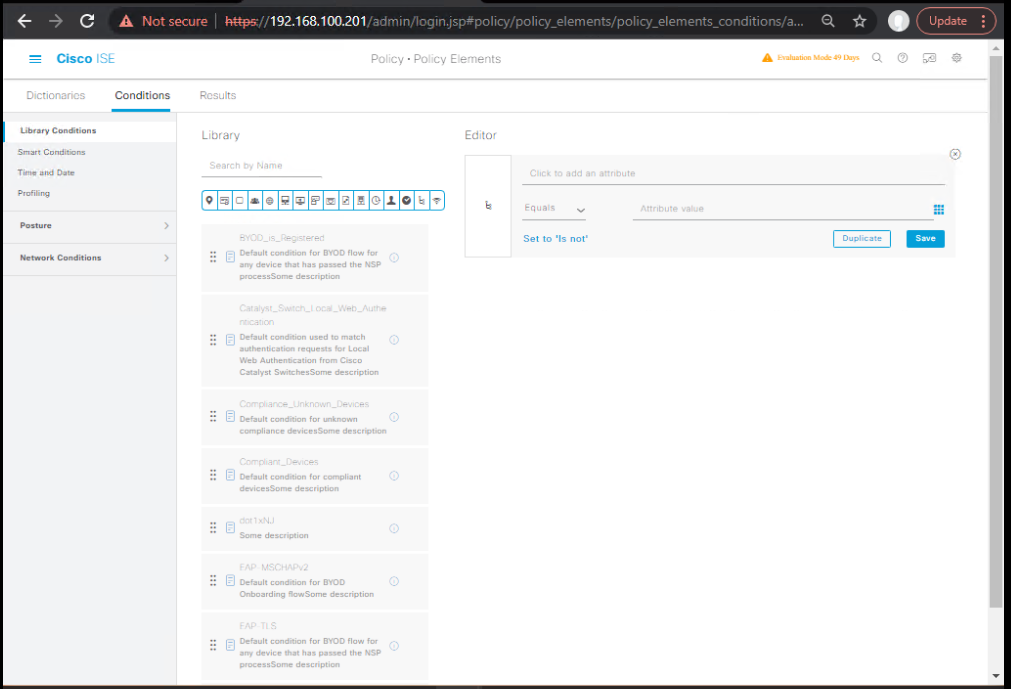
Step 4 – Configure Threat Feed Conditions
- Navigate to Policy > Profiling > Conditions.
- Add Condition:
- Attribute:
pxGrid ThreatCategory. - Operator:
equals. - Value:
Malware.
[Screenshot: ISE Threat Condition Setup]
- Attribute:
Step 5 – Switch/WLC Enforcement
On Catalyst Switch:
conf t cts role-based enforcement cts authorization list ise-auth aaa authorization network ise-auth group radius
On WLC 9800:
radius server ISE address ipv4 10.1.1.10 auth-port 1812 acct-port 1813 key Cisco123 aaa authorization network default group radius
Step 6 – Validation
GUI Validation
- Go to Operations > Live Sessions.
- Select endpoint.
- Verify: Session shows Threat = High and Quarantine Policy applied.
[Screenshot: ISE Live Session – Quarantined Endpoint]
CLI Validation
On Switch:
show cts role-based session show authentication sessions interface Gi1/0/2
On WLC:
show wireless client mac <mac-address> detail
You should see:
- SGT updated or dACL applied.
- VLAN change if configured.
FAQs
1. Q: What licenses are required to enable Threat-Centric NAC in Cisco ISE?
A: At minimum, you need the Plus License (for pxGrid and integrations). The Base License covers identity and auth, but TC-NAC requires pxGrid-based threat feed subscriptions, which fall under Plus. If you add posture/remediation, you also need the Apex license.
2. Q: How does ISE know an endpoint is compromised?
A: ISE itself doesn’t do malware analysis. Instead, it subscribes to external threat intelligence feeds (e.g., Firepower, AMP, Talos, Stealthwatch) via pxGrid. When those tools detect a compromise, they push the threat context into ISE, which updates the endpoint’s session state.
3. Q: What enforcement options does ISE support when a threat is detected?
A: Enforcement is flexible:
- Quarantine VLAN → reassign endpoint to remediation VLAN.
- Downloadable ACL (dACL) → block/allow only specific traffic.
- SGACLs with SGT reassignment → dynamic segmentation-based restrictions.
- Full block/port shut (last resort).
4. Q: Can Threat-Centric NAC apply different actions based on severity?
A: Yes. ISE can consume threat severity levels (Low, Medium, High, Critical) from pxGrid. You can build Authorization Policy rules such as:
- Low → allow with monitoring.
- Medium → apply restricted ACL.
- High → move to quarantine VLAN.
- Critical → deny all access.
5. Q: How quickly does ISE enforce a policy after a threat is detected?
A: In most cases, under 10–15 seconds. The flow is: Threat detected → Partner publishes event → pxGrid notifies ISE → ISE reevaluates session → switch/WLC enforces updated authorization.
6. Q: What happens if the endpoint is cleared by the threat intelligence source?
A: The same integration works in reverse. When Firepower/AMP marks the endpoint as “clean”, pxGrid notifies ISE → session gets re-evaluated → endpoint is restored to its original authorization (normal VLAN/ACL). This is called automatic remediation.
7. Q: Can Threat-Centric NAC work in distributed ISE deployments?
A: Yes. pxGrid is cluster-aware. You can enable pxGrid on one or more nodes. Threat events published on one node replicate to all PSNs in the deployment, ensuring consistent policy enforcement across the network.
8. Q: What’s the best way to validate TC-NAC is working in a lab?
A:
- Connect endpoint to switch/WLC and verify normal access.
- Simulate threat detection in Firepower (e.g., flag host with malware signature).
- Check ISE Live Sessions → endpoint status should change to “Threat High” with new policy.
- On switch:
show authentication sessions interface Gi1/0/2 show cts role-based sessionVerify VLAN change, dACL, or SGT applied.
9. Q: What troubleshooting steps should I take if pxGrid events are not received by ISE?
A:
- On ISE:
- Check pxGrid service:
show application status ise. - Review logs:
show logging application pxgrid.log tail.
- Check pxGrid service:
- On FMC/AMP: Ensure pxGrid certificate trust is established.
- In GUI: Confirm pxGrid Client is “Approved” in ISE.
10. Q: Can non-Cisco tools integrate with Threat-Centric NAC?
A: Yes. Any security product that supports pxGrid API can publish threat events to ISE. Examples: IBM QRadar, Splunk, McAfee ePO. They integrate via pxGrid SDK, and ISE enforces policy the same way.
YouTube Link
For more in-depth Cisco ISE Mastery Training, subscribe to my YouTube channel Network Journey and join my instructor-led classes for hands-on, real-world ISE experience
Closing Notes
- Threat-Centric NAC makes access policies dynamic → not just “who you are” but “are you safe right now.”
- Integration via pxGrid is the backbone.
- Testing and validation are crucial: always verify Live Sessions, switch/WLC session state, and pxGrid logs.
Upgrade Your Skills – Start Today
For more in-depth Cisco ISE Mastery Training, subscribe to my YouTube channel Network Journey and join my instructor-led classes.
I run a focused 4-month Fast-Track Cisco ISE Mastery Pro (part of CCIE Security program).
- Live labs (wired, wireless, pxGrid, Threat-Centric NAC).
- Workbook + Recording Access.
- Direct mentorship to clear your doubts.
Check course outline here: https://course.networkjourney.com/ccie-security/
Take the fast-track route – don’t just learn configs, master real-world NAC deployments!
Enroll Now & Future‑Proof Your Career
Email: info@networkjourney.com
WhatsApp / Call: +91 97395 21088



