[Day 81] Cisco ISE Mastery Training: Integrating Cisco AMP for Endpoints
Table of Contents
Introduction
In Threat-Centric NAC (TC-NAC), Cisco ISE doesn’t “hunt malware” itself—it ingests threat verdicts and enforces. With Cisco AMP for Endpoints (now Cisco Secure Endpoint), ISE subscribes to live threat events and dynamically quarantines or restricts infected hosts using VLAN changes, dACLs, or TrustSec SGACLs—automatically and reversibly when the host is cleaned. This is a cornerstone of closed-loop NAC.
ISE integrates with AMP/Secure Endpoint via the Threat-Centric NAC service using an AMP adapter (cloud), leveraging REST + streaming events and driving enforcement via RADIUS CoA and ANC. (Cisco, Cisco Community)
Problem Statement
Security tools detect threats; the network must respond immediately. Without integration:
- SecOps sees detections in AMP but users keep full access.
- Manual ticketing and VLAN ACL changes are slow and error-prone.
- Infected hosts can move laterally before anyone reacts.
We need detector→enforcer automation: AMP says “compromised” → ISE re-authorizes the active session and restricts it within seconds.
Solution Overview (what ISE actually does)
- Threat-Centric NAC service on ISE (enable on one PSN only) subscribes to AMP Cloud event streams. (Cisco)
- ISE maps events/severity to Authorization Policy results (VLAN, dACL, SGT) and triggers CoA on active sessions.
- ANC (Adaptive Network Control) can be invoked by ISE or ecosystem partners and requires the ISE Advantage tier; TC-NAC with AMP adapter requires the ISE Premier tier. (Cisco)
- ISE exposes dashboards, Threat Events reports, and Live Logs for validation; TC-NAC logs are collected under support/logs/TC-NAC/. (Cisco)
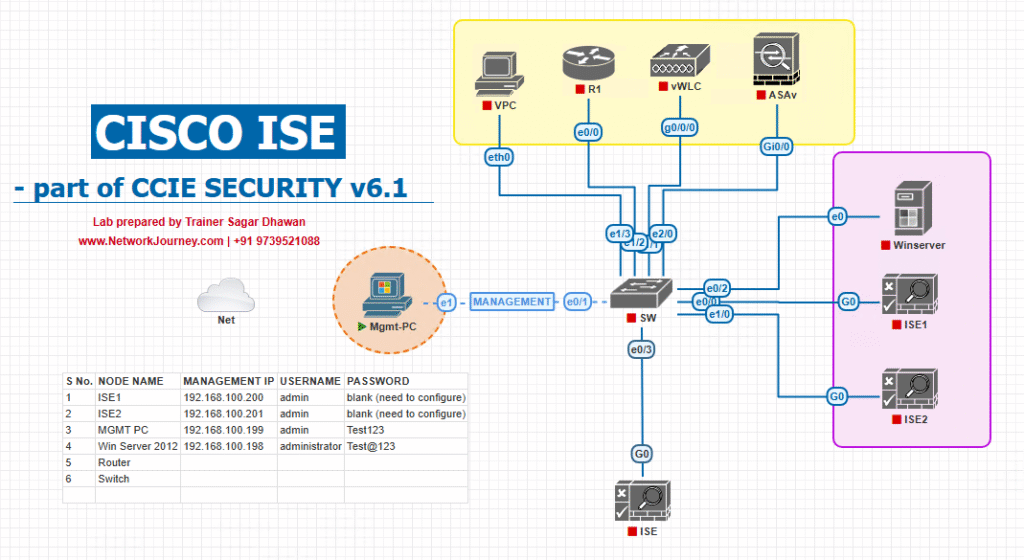
Sample Lab Topology
Platform: VMware Workstation/ESXi or EVE-NG
Nodes:
- ISE 3.2/3.3 (PAN+MnT+PSN or separate PSN for TC-NAC service)
- Catalyst 9300 (IOS-XE 17.x) for wired 802.1X/MAB and CoA
- WLC 9800-CL (wireless enforcement; Airespace ACL or VLAN reassign)
- Router/Firewall (L3 boundary; optional)
- Windows 10/11 VM with Secure Endpoint connector (formerly AMP)
- Test Linux/Windows endpoints (wired & wireless)
Logical diagram :
Pre-req quick list:
- ISE Premier for TC-NAC; Advantage for ANC (dACL/quarantine). (Cisco)
- ISE reachable outbound 443 to AMP Cloud (US/EU) (per your tenant). (Cisco)
- RADIUS/CoA configured on 9300 and WLC; endpoints can successfully authenticate.
Step-by-Step GUI Configuration Guide (with validation)
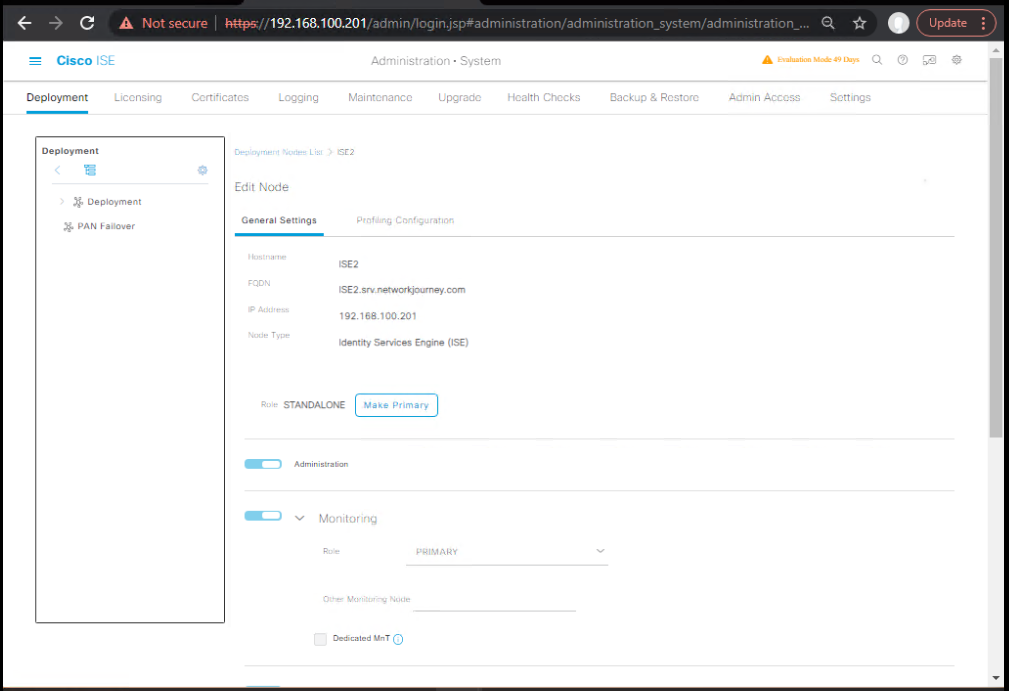
A) ISE — Enable Threat-Centric NAC service
- Administration > System > Deployment → select your PSN → Edit → tick Enable Threat Centric NAC Service → Save.
[Screenshot: ISE Deployment Node Edit]
Note: enable on one node only. (Cisco)
Validation:
- Operations > Reports > Threat Centric NAC > Adapter Status shows service up; no alarms.
- Operations > Reports > Diagnostics > ISE Counters → Total number of events received increments when events flow. (Cisco)
B) ISE — Add the AMP (Secure Endpoint) adapter
- Administration > Threat Centric NAC > Third Party Vendors → Add.
[Screenshot: ISE TC-NAC Third-Party Vendors]
- Vendor = “AMP : Threat” → name it (e.g.,
AMP_Adapter_Prod) → Save.
[Screenshot: Add Vendor – AMP Threat] - Wait for status Ready to Configure → click Ready to configure.
- Optional: set proxy if used.
- Select US or EU cloud as per your AMP tenant.
- Choose event source subscription (AMP only, CTA only, or both); for AMP integration choose AMP events (or CTA+AMP if you use CTA).
- Click the FireAMP link, sign in to your AMP Console, Allow the streaming export authorization, and you’re redirected back to ISE.
- Select which AMP event types to monitor (e.g., Executed Malware, Malicious Connection, Suspicious Download, Java Compromise).
- Pick log level (Info/Debug). Save.
[Screenshot: AMP Adapter Config Wizard]
Mechanics: AMP adapter uses REST and AMQP/streaming over 443. (Cisco)
Validation:
- Adapter Status report shows Connected/Subscribed; no Adapter not reachable (91002) alarms.
- Home > Threat dashboard shows widgets; Context Visibility > Endpoints > Compromised Endpoints populates when events arrive.
- Operations > Reports > Threat Centric NAC > Threat Events shows raw events. (Cisco)
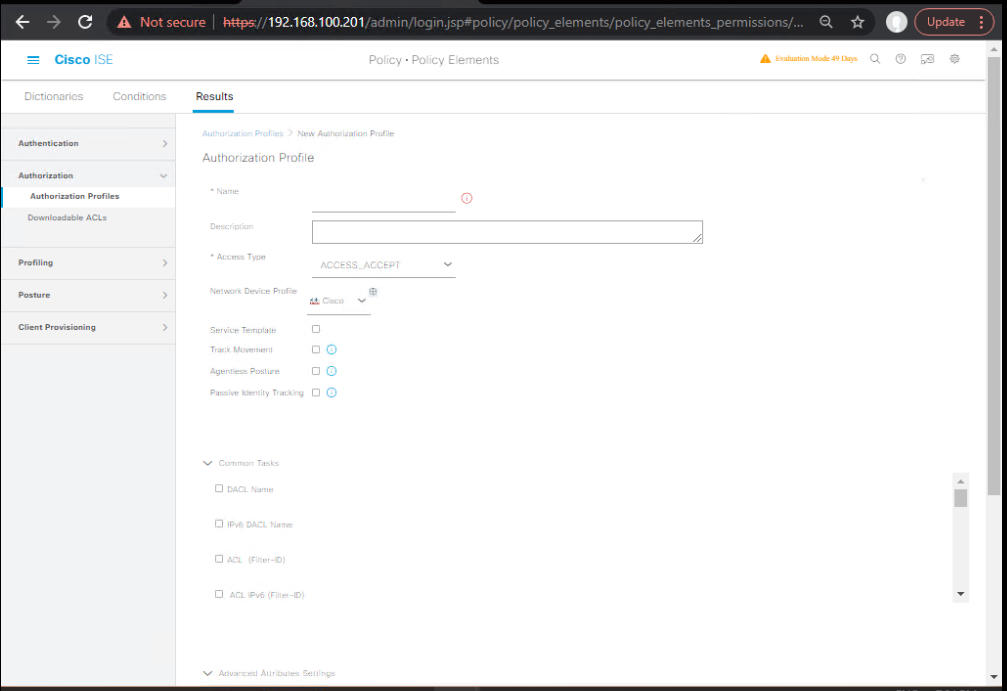
C) ISE — Build Authorization Profiles for Quarantine/Restriction
Create at least three results you can test/compare:
- QUAR-VLAN (wired):
- Policy > Policy Elements > Authorization > Authorization Profiles > Add
- Access Type: ACCESS_ACCEPT
- VLAN: e.g., 530 Quarantine
- Common Tasks: Reauthenticate if needed.
[Screenshot: AuthZ Profile – QUAR-VLAN]
- QUAR-dACL (wired TrustSec optional):
- dACL Name:
AMP-QUAR-DACL(create in Policy > Policy Elements > Results > Authorization > Downloadable ACLs) - Example
AMP-QUAR-DACLcontents:remark Allow DHCP/DNS/AMP-Cloud remediation permit udp any any eq bootpc permit udp any any eq domain permit tcp any host <AMP-cloud-FQDN-or-IP> eq 443 deny ip any any - Apply this dACL in an AuthZ profile named QUAR-dACL.
[Screenshot: dACL Content + AuthZ Profile]
- dACL Name:
- QUAR-SGT (TrustSec):
- Assign a restricted SGT (e.g., SGT 30 – Quarantined) in the AuthZ profile; ensure SGACL enforces isolation.
[Screenshot: AuthZ Profile – SGT Assign]
- Assign a restricted SGT (e.g., SGT 30 – Quarantined) in the AuthZ profile; ensure SGACL enforces isolation.
Validation:
- Policy > Policy Elements > Results > Downloadable ACLs → Verify Deployment shows successful push to devices.
- TrustSec: Work Centers > TrustSec > Verify Deployment clean. (Cisco)
D) ISE — Write Authorization Policy using AMP event attributes
- Policy > Policy Sets > (Your policy set) > Authorization.
- Add ordered rules matching Threat/AMP attributes (Severity/Event Type), for example (top-down):
- Rule:
If NetworkAccess:AuthenticationPassed AND Threat(AMP):Severity >= High→ Result:QUAR-VLAN - Rule:
If AuthenticationPassed AND Threat(AMP):EventType CONTAINS "Executed Malware"→ Result:QUAR-dACL - Rule:
If AuthenticationPassed AND Threat(AMP):EventType CONTAINS "Malicious Connection"→ Result:QUAR-SGT
[Screenshot: ISE Authorization Policy with Threat Conditions]
Tip: CTA “Course of Action” uses CONTAINS logic; same pattern is safe for AMP multi-value events. (Cisco) - Rule:
Validation:
- Trigger a test event (see section G); watch Live Logs: rule hit → CoA → new AuthZ profile applied.
- Threat Events report shows the exact event ISE consumed. (Cisco)
E) Network Devices — RADIUS, CoA, dACL readiness
Catalyst 9300 (global):
aaa new-model aaa authentication dot1x default group radius aaa authorization network default group radius aaa accounting update periodic 5 radius server ISE1 address ipv4 10.10.10.10 auth-port 1812 acct-port 1813 key <SECRET> ! aaa server radius dynamic-author client 10.10.10.10 server-key <SECRET> auth-type any ! ip device tracking ip http server
Catalyst 9300 (interface to test host):
interface Gi1/0/10 switchport mode access authentication host-mode multi-auth authentication order dot1x mab authentication priority dot1x mab authentication port-control auto mab dot1x pae authenticator dot1x timeout tx-period 7 spanning-tree portfast
Validation (wired):
show authentication sessions interface Gi1/0/10 details show access-session interface Gi1/0/10 show ip access-lists | i AMP-QUAR-DACL ! derived dACL name reference show cts role-based session interface Gi1/0/10
Look for Status Authorized, Server Policies with the new dACL/VLAN/SGT, and Latest CoA timestamp after the threat event.
WLC 9800-CL (radius & CoA):
aaa group server radius ISE server name ISE1 ! radius server ISE1 address ipv4 10.10.10.10 auth-port 1812 acct-port 1813 key <SECRET> ! aaa authorization network default group ISE wireless aaa-policy ISE-AAA accounting update interval 5 !
Wireless Enforcement: push Airespace ACL name from ISE AuthZ Profile, or reassign policy profile/VLAN.
Validation (wireless):
show wireless client mac <mac> detail show access-control list name AMP-QUAR-ACL
Confirm Policy Profile, Airespace ACL, or VLAN changed post-CoA.
F) ISE — ANC policies (optional but recommended)
Even though AMP adapter drives TC-NAC, pair it with ANC for manual or API-triggered quarantine.
- Policy > Policy Elements > Results > ANC Policies > Add →
AMP-QUAR-ANC(Action: Quarantine / Port Shut / SGT). - Test Operations > Adaptive Network Control (ANC) → Assign ANC Policy to a test IP/MAC.
[Screenshot: ANC Policy List + Assign]
ANC is an ISE service; partners can invoke it via pxGrid/REST to quarantine an IP/Session. (Cisco DevNet)
Validation:
- Switch shows new dACL/SGT/VLAN; ISE ANC Assignments table shows the mapping.
G) End-to-End Test with Secure Endpoint
Lab-safe trigger: use the EICAR test string or generate a known-benign test detection in Secure Endpoint. Do this only in a controlled lab.
- Ensure the test host is authenticated and has normal access (browse internet).
- In Secure Endpoint console, ensure the connector reports to your US/EU cloud and policy allows detection of your test.
- Trigger the test detection (e.g., EICAR file).
- Observe ISE:
- Operations > Live Logs → the session should re-authorize with your Threat rule.
- Operations > Reports > Threat Centric NAC > Threat Events → new event appears.
- Context Visibility > Endpoints > Compromised Endpoints → host listed. (Cisco)
- Observe network device:
- Wired:
show authentication sessions interface …→ Server Policies shows dACL or VLAN updated. - Wireless:
show wireless client mac … detail→ policy/ACL/VLAN changed.
- Wired:
- Connectivity test: endpoint should have restricted reachability (only remediation destinations as per dACL).
- Auto-remediation: when Secure Endpoint marks host Clean, events flow back; ISE re-evaluates the session and restores the original authorization.
Timing: typical detection→enforcement seconds to low tens of seconds, depending on event pipeline and CoA. (Flow: AMP detect → Cloud event → ISE adapter → AuthZ re-eval → CoA → device enforces.) (Cisco)
H) ISE & Adapter Troubleshooting / Validation
- Service health:
- ISE CLI:
show application status ise(TC-NAC listed under application services).
- ISE CLI:
- Adapter alarms & reports:
- Adapter not reachable (91002), Adapter Connection Failed (91018) visible in Alarms; Adapter Status & Threat Events reports for specifics. (Cisco)
- Logs:
- support/logs/TC-NAC/ in ISE support bundle. (Cisco)
- Common:
CLI Validation for Cisco ISE + AMP for Endpoints Integration
1. Verify AMP Connector on Endpoint (Windows/Linux/Mac)
Check the AMP agent status on the endpoint to ensure it’s registered with AMP Cloud and sending telemetry to ISE.
- Windows (PowerShell/CLI):
cd "C:\Program Files\Cisco\AMP" agentcmd /s # Shows agent status agentcmd /c # Forces a cloud check-in agentcmd /q # Displays quarantine status
Expected Output:
Agent GUID: {xxxxxxxx-xxxx-xxxx-xxxx-xxxxxxxx}
Cloud Connectivity: Connected
Policy Applied: Corporate_Default
Quarantine Status: Not Quarantined
- Linux/Mac:
/opt/cisco/amp/bin/ampcli status /opt/cisco/amp/bin/ampcli policy
2. Verify ISE pxGrid Subscriptions
ISE consumes AMP telemetry via pxGrid. Validate pxGrid session from ISE CLI.
ise/admin# show application status ise ise/admin# show pxGrid sessions
Expected Output:
pxGrid Clients Registered: -------------------------------- Client Name: amp-connector Status: Connected Node: ise01
3. Syslog Flow Validation (ISE <-> AMP)
Check if ISE is receiving AMP event logs (compromised endpoint, malware detected).
ise/admin# less /var/log/ise/pxgrid/pxgrid.log ise/admin# tail -f /var/log/ise/pxgrid/pxgrid.log
Look for events like:
AMP: Threat Detected
Endpoint GUID: {abc123}
File SHA256: <malware hash>
ISE Action: Change of Authorization (CoA) triggered
4. Endpoint CoA Enforcement Check (Switch/WLC)
After ISE receives AMP threat info, it pushes CoA (quarantine or VLAN change). Validate on switch/WLC:
- On Switch (Wired):
Switch# show authentication sessions interface Gi1/0/10 Interface: Gi1/0/10 MAC: 00:1A:2B:3C:4D:5E Status: Authorized VLAN: Quarantine_VLAN (110) ISE Policy Applied: AMP_Quarantine
- On WLC (Wireless):
(WLC)# show client detail <mac-address> Policy Manager State: AUTHORIZED VLAN: Quarantine_VLAN Security Policy: CoA Reauth triggered by ISE
5. ISE Live Log Validation
Confirm actions directly from ISE GUI Operations > RADIUS > Live Logs
- Entry should show:
- User/Endpoint ID
- AuthC Passed
- AuthZ Profile Applied: Quarantine/Restrict
- CoA Issued = YES
With these CLI + GUI checks, you can prove end-to-end flow:
AMP detects threat → pxGrid shares with ISE → ISE issues CoA → Switch/WLC enforces quarantine → Endpoint moved/restricted.
FAQs – Cisco ISE + Cisco AMP for Endpoints Integration
1. How does Cisco AMP for Endpoints communicate with Cisco ISE?
Cisco AMP communicates with ISE via pxGrid. When AMP detects a threat (e.g., malware, ransomware, or suspicious behavior), it publishes the event to ISE over pxGrid. ISE then uses this contextual information to trigger adaptive network access policies such as quarantining, VLAN change, or full access revocation.
2. What licenses are required to integrate Cisco AMP with ISE?
You need:
- ISE Apex license (or Plus in new licensing terms) → required for pxGrid integration.
- Cisco AMP for Endpoints subscription license → to enable cloud connectivity, policy updates, and reporting.
Without Apex licensing, ISE cannot consume AMP threat feeds over pxGrid.
3. Can AMP for Endpoints quarantine an endpoint directly, or does it rely on ISE?
AMP can quarantine an endpoint locally (host isolation at OS level). However, for network-wide enforcement, AMP relies on ISE to push a CoA (Change of Authorization) to network devices (switches, WLCs, or VPN concentrators). This ensures the device is isolated everywhere on the network, not just locally.
4. How can I verify that ISE has received threat intelligence from AMP?
- In the ISE GUI: Operations > Context Visibility > Endpoints, check Threat = Yes.
- In Operations > RADIUS > Live Logs, see if the endpoint authz profile changed due to AMP.
- In CLI:
ise/admin# show pxGrid sessions ise/admin# tail -f /var/log/ise/pxgrid/pxgrid.log
5. What are common use cases for AMP + ISE integration?
- Malware-Infected Host: Automatically quarantine device.
- High-Risk Endpoint: Move device to remediation VLAN.
- Compliance Enforcement: Only allow endpoints with “clean” AMP status into production network.
- SOC Automation: Security alerts from AMP drive real-time ISE policy actions.
6. How does CoA (Change of Authorization) work in this integration?
When AMP flags a device as compromised, ISE triggers a CoA to the network device (switch or WLC). This CoA:
- Forces reauthentication of the endpoint.
- Applies new Authorization Profile (e.g., Quarantine VLAN, dACL, or deny-all).
Validation:
Switch# show authentication sessions interface Gi1/0/10
7. What happens if AMP detects malware but the endpoint is offline?
If the endpoint is offline, AMP still reports to the AMP Cloud. Once the endpoint reconnects to the network:
- AMP status syncs with cloud.
- ISE retrieves updated status from pxGrid.
- Endpoint will be quarantined immediately upon reconnect.
8. How do I troubleshoot if ISE is not receiving AMP events?
- Check pxGrid status in ISE CLI:
ise/admin# show application status ise ise/admin# show pxGrid sessions
- Ensure Apex license is applied.
- Confirm firewall rules allow AMP <-> ISE <-> pxGrid communication (TCP 5222, 8910).
- Verify AMP API credentials configured correctly in ISE.
- Check ISE pxGrid logs:
ise/admin# tail -f /var/log/ise/pxgrid/pxgrid.log
9. Can AMP integration work in a multi-node ISE deployment?
Yes. In a distributed ISE deployment:
- Only pxGrid-enabled nodes (usually PAN/PSN with pxGrid persona) connect to AMP.
- AMP events are synchronized across the deployment.
- Always enable redundancy with multiple pxGrid nodes for HA.
10. How do I validate end-to-end enforcement (AMP → ISE → Network → Endpoint)?
- Trigger a Test Threat: Use a safe test file like EICAR test virus.
- Check AMP Console: Endpoint should show infected.
- Check ISE Context Visibility: Endpoint marked with Threat = Yes.
- Check Live Logs in ISE: CoA triggered with new Authz profile.
- Check Switch/WLC CLI: Endpoint should be in Quarantine VLAN.
- On Endpoint: Network access restricted (e.g., only remediation portal reachable).
YouTube Link
For more in-depth Cisco ISE Mastery Training, subscribe to my YouTube channel Network Journey and join my instructor-led classes for hands-on, real-world ISE experience
Closing Notes
- Enable TC-NAC on one PSN, integrate AMP Cloud via the AMP adapter, and enforce with VLAN/dACL/SGT.
- Build ordered Authorization rules per severity/event, and validate with Live Logs, Threat Events, and device CLI.
- Pair with ANC for manual/API quarantines and automate your closed-loop workflows.
Upgrade Your Skills – Start Today
For more in-depth Cisco ISE Mastery Training, subscribe to my YouTube channel Network Journey and join my instructor-led classes.
Fast-Track to Cisco ISE Mastery Pro
I run a focused 4-month instructor-led program covering end-to-end ISE (NAC, TrustSec, TC-NAC, pxGrid, Posture, BYOD, Wireless, Zero Trust).
Course outline & enrollment: https://course.networkjourney.com/ccie-security/
What you get (sales-funnel highlights):
- Hands-on labs in VMware/EVE-NG with weekly graded exercises
- Design + Deployment blueprints (wired & wireless)
- Job-ready playbooks (AuthC/AuthZ, dACL/TrustSec, TC-NAC, pxGrid/ANC)
- Mock interviews, resume feedback, community forum & office hours
- Get a free ISE Policy Set checklist + TC-NAC runbook when you sign up for the waitlist
Enroll Now & Future‑Proof Your Career
Email: info@networkjourney.com
WhatsApp / Call: +91 97395 21088

![[Day 103] Cisco ISE Mastery Training: High Availability & Failover Testing](https://networkjourney.com/wp-content/uploads/2025/08/Day-103-–-Cisco-ISE-Mastery-Training-High-Availability-Failover-Testing.png)
![[Day 16] Cisco ISE Mastery Training: Understanding 802.1X Authentication Flow](https://networkjourney.com/wp-content/uploads/2025/08/Day-16-–-Cisco-ISE-Mastery-Training-Understanding-802.1X-Authentication-Flow.png)
