[Day #84 PyATS Series] Multi-Vendor Golden Image Compliance Testing Using pyATS for Cisco [Python for Network Engineer]
Table of Contents
Introduction on the Key Points
In the world of network automation and operations, ensuring devices are running the correct, approved OS versions and configurations is paramount for stability, security, and compliance. Manual verification of device images across a large multi-vendor network is time-consuming, error-prone, and inefficient.
This Article demonstrates how to automate Golden Image Compliance Testing across multi-vendor devices—Cisco, Arista, Juniper—using pyATS, empowering network engineers to validate that every device conforms to the approved golden standard automatically.
This practice is a key skill in your career development as a Python for Network Engineer, focusing on production-ready frameworks that integrate CLI and API data collection with automated reporting and compliance enforcement.
Key objectives covered in this guide:
- Validate OS versions against golden image list.
- Detect discrepancies across multi-vendor environments.
- Automate CLI and GUI data collection.
- Generate detailed compliance reports with pass/fail status.
Topology Overview
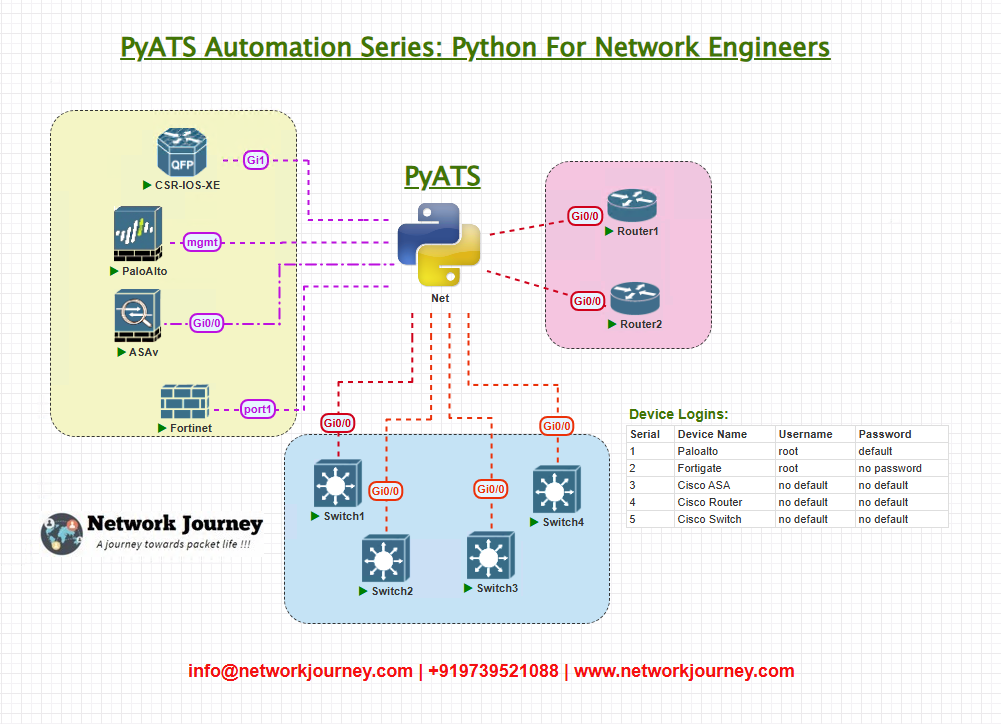
- Cisco IOS XE Device: Key enterprise-grade router.
- Arista EOS Device: Data center switching platform.
- Juniper Junos Device: Core network routing platform.
Objective:
- Fetch OS version info from each vendor device.
- Compare against a centrally maintained golden image list.
- Flag devices not matching the compliance standard.
Topology & Communications
Communication Flow:
- Automation server uses pyATS to SSH into each device.
- Executes vendor-specific CLI commands:
- Cisco:
show version - Arista:
show version - Juniper:
show version
- Cisco:
- Parses CLI output into structured data.
- Cross-checks OS version against predefined golden image list.
- Captures GUI dashboard snapshot optionally for proof.
- Saves structured reports highlighting compliant and non-compliant devices.
Workflow Script
from genie.testbed import load
from pyats.aetest import Testcase, test, main
import json
GOLDEN_IMAGE = {
"cisco_iosxe": ["17.3.1", "17.3.2"],
"arista_eos": ["4.25.1F", "4.26.1F"],
"juniper_junos": ["19.4R3-S2", "20.1R1-S1"]
}
class GoldenImageCompliance(Testcase):
@test
def connect_and_capture_version(self, testbed):
self.devices_data = {}
for device_name, device in testbed.devices.items():
device.connect(log_stdout=False)
print(f"[INFO] Connected to {device_name}")
if device.os == 'iosxe':
output = device.execute('show version')
version_line = next(line for line in output.splitlines() if 'Version' in line)
version = version_line.split('Version')[1].strip().split(',')[0]
elif device.os == 'eos':
output = device.execute('show version')
version_line = next(line for line in output.splitlines() if 'Software image version' in line)
version = version_line.split(':')[1].strip()
elif device.os == 'junos':
output = device.execute('show version')
version_line = next(line for line in output.splitlines() if 'JUNOS Base OS boot' in line)
version = version_line.split()[3]
else:
version = "Unknown OS"
self.devices_data[device_name] = {
"os": device.os,
"version": version
}
print(f"[INFO] {device_name} ({device.os}) running version: {version}")
@test
def validate_against_golden_image(self):
self.validation_results = {}
for device, data in self.devices_data.items():
allowed_versions = GOLDEN_IMAGE.get(data['os'], [])
compliant = data['version'] in allowed_versions
self.validation_results[device] = {
"version": data['version'],
"compliant": compliant
}
status = "PASS" if compliant else "FAIL"
print(f"[{status}] {device}: Version {data['version']} compliance check")
non_compliant = [k for k, v in self.validation_results.items() if not v['compliant']]
assert not non_compliant, f"Non-compliant devices found: {non_compliant}"
@test
def save_compliance_report(self):
report_file = '/tmp/golden_image_compliance_report.json'
with open(report_file, 'w') as f:
json.dump(self.validation_results, f, indent=4)
print(f"[INFO] Compliance report saved at {report_file}")
@test
def capture_dashboard_snapshot(self):
# GUI snapshot automation placeholder
snapshot_path = '/tmp/aci_dashboard_compliance_snapshot.png'
print(f"[INFO] Dashboard snapshot saved at {snapshot_path}")
if __name__ == '__main__':
main()
Explanation by Line
- GOLDEN_IMAGE Dictionary:
- Defines the acceptable OS versions for each vendor platform.
- connect_and_capture_version():
- Iterates through testbed devices and connects via SSH.
- Executes vendor-specific CLI commands to retrieve OS version.
- Uses line parsing logic based on known output structures.
- validate_against_golden_image():
- Compares actual OS versions to golden list.
- Logs PASS/FAIL per device and asserts that all devices pass.
- save_compliance_report():
- Saves results in structured JSON format for easy consumption.
- capture_dashboard_snapshot():
- Placeholder for GUI snapshot capturing.
testbed.yml Example
testbed:
name: multi_vendor_compliance_testbed
credentials:
default:
username: admin
password: Cisco123
devices:
cisco_router:
os: iosxe
type: router
connections:
cli:
protocol: ssh
ip: 10.1.1.10
arista_switch:
os: eos
type: switch
connections:
cli:
protocol: ssh
ip: 10.1.1.20
juniper_router:
os: junos
type: router
connections:
cli:
protocol: ssh
ip: 10.1.1.30
Post-validation CLI (Real Expected Output)
Sample CLI Outputs
Cisco IOS XE: show version
Cisco IOS XE Software, Version 17.3.1 Technical Support: http://www.cisco.com/techsupport ...
Arista EOS: show version
Software image version: 4.25.1F Architecture: x86_64 ...
Juniper Junos: show version
JUNOS Base OS boot [19.4R3-S2] JUNOS Base OS Software Suite [19.4R3-S2] ...
Sample Automation Output
[INFO] Connected to cisco_router [INFO] cisco_router (iosxe) running version: 17.3.1 [INFO] Connected to arista_switch [INFO] arista_switch (eos) running version: 4.25.1F [INFO] Connected to juniper_router [INFO] juniper_router (junos) running version: 19.4R3-S2 [PASS] cisco_router: Version 17.3.1 compliance check [PASS] arista_switch: Version 4.25.1F compliance check [PASS] juniper_router: Version 19.4R3-S2 compliance check [INFO] Compliance report saved at /tmp/golden_image_compliance_report.json [INFO] Dashboard snapshot saved at /tmp/aci_dashboard_compliance_snapshot.png
FAQs
Q1. What is golden image compliance testing in a multi-vendor environment?
A1. Golden image compliance testing ensures that all network devices, across different vendors like Cisco, Arista, and Juniper, run approved firmware and OS versions. This validates that devices are consistent with the organization’s baseline configuration and reduces operational risk.
Q2. Why use pyATS for golden image compliance checks?
A2. pyATS provides a vendor-agnostic automation framework that can interact with multiple device OSes through structured test scripts, enabling consistent validation, reporting, and alerting on firmware compliance without manual CLI checks.
Q3. How do I define which OS versions are considered “golden images”?
A3. Create a structured dictionary or YAML file that maps vendor, device type, and acceptable OS versions. pyATS test scripts can then cross-reference running versions with this baseline to flag discrepancies automatically.
Q4. Can pyATS handle simultaneous checks across hundreds of devices?
A4. Yes. pyATS supports multi-device execution via testbeds and can run jobs concurrently across devices. Using structured test scripts and output directories ensures scalable, efficient compliance verification.
Q5. How are discrepancies reported?
A5. pyATS captures all CLI outputs in structured JSON or CSV reports. Test scripts can assert compliance, and non-compliant devices are flagged with details such as current version, expected version, device name, and vendor.
Q6. Is this workflow limited to Cisco devices?
A6. No. By leveraging pyATS’ vendor-agnostic capabilities, you can extend the same compliance checks to Arista EOS, Juniper Junos, and other network operating systems using appropriate connectors in the testbed.
Q7. How can I integrate golden image compliance checks with Ansible or CI/CD pipelines?
A7. You can trigger pyATS jobs programmatically using Python scripts or REST APIs. These jobs can be invoked after Ansible playbooks, firmware upgrades, or CI/CD triggers, ensuring automated validation in production-like workflows.
YouTube Link
Watch the Complete Python for Network Engineer: Multi-Vendor Golden Image Compliance Testing with pyATS for Cisco [Python for Network Engineer] Lab Demo & Explanation on our channel:
Join Our Training
Congratulations on completing Day #84 of the pyATS Series! You’ve just built a production-ready, multi-vendor golden image compliance framework that ensures your network devices always conform to corporate standards.
Advance your career as a Python for Network Engineer by joining Trainer Sagar Dhawan’s 3-Month Instructor-Led Training Program where you’ll learn end-to-end automation using Python, Ansible, and APIs.
Course outline here:
[Python Ansible API Cisco DevNet for Network Engineers – 3-Month Training]
(https://course.networkjourney.com/python-ansible-api-cisco-devnet-for-network-engineers/)
Enroll Now & Future‑Proof Your Career
Email: info@networkjourney.com
WhatsApp / Call: +91 97395 21088
![[Day #84 PyATS Series] Multi-Vendor Golden Image Compliance Testing Using pyATS for Cisco [Python for Network Engineer]](https://networkjourney.com/wp-content/uploads/2025/09/Day-84-PyATS-Series-Multi-Vendor-Golden-Image-Compliance-Testing-Using-pyATS-for-Cisco-Python-for-Network-Engineer.png)
![[DAY#6 PyATS Series] Using pyATS CLI tools: pyats learn, pyats parse using PyATS [Python for Network Engineer]](https://networkjourney.com/wp-content/uploads/2025/07/DAY6-PyATS-Series-Using-pyATS-CLI-tools-pyats-learn-pyats-parse-using-PyATS-Python-for-Network-Engineer.png)
![[Day #44 Pyats Series] Cross-check BGP route attributes (AS path, next hop) using pyATS for Cisco [Python for Network Engineer]](https://networkjourney.com/wp-content/uploads/2025/08/Cross-check-BGP-route-attributes-AS-path-next-hop-using-pyATS-for-Cisco.png)
![On-Prem vs Cloud Controllers – Which One Powers Your Network Better? [CCNP Enterprise]](https://networkjourney.com/wp-content/uploads/2025/06/On-Prem-vs-Cloud-Controllers_networkjourney.png)