[Day #92 PyATS Series] Automate EVPN Fabric Validation Across Cisco/Arista/Paloalto/Fortigate Using pyATS for Cisco [Python for Network Engineer]
Table of Contents
Introduction: Automating EVPN Fabric Validation with Python for Network Engineer
In modern data center architectures, EVPN (Ethernet VPN) overlays are critical for scalable Layer 2 and Layer 3 services. Validating EVPN fabric health after changes or periodic audits is essential to ensure network stability, performance, and policy compliance. Manual validation of EVPN fabric status across multi-vendor devices like Cisco, Arista, Palo Alto, and Fortigate is time-consuming and error-prone.
In this masterclass Article, we will focus on automating the EVPN fabric validation workflow using pyATS in a production-ready manner. By implementing automation through Python scripts and pyATS test frameworks, we guarantee accurate, repeatable validation with CLI and GUI-supported outputs. The validation framework we build will check BGP EVPN sessions, MAC-VTEP mappings, route consistency, and fabric reachability, delivering structured reports in JSON and HTML.
This Article demonstrates a realistic step-by-step guide for network engineers aiming to implement automation in a multi-vendor environment.
Topology Overview
My test topology simulates a typical data center EVPN deployment with the following devices:
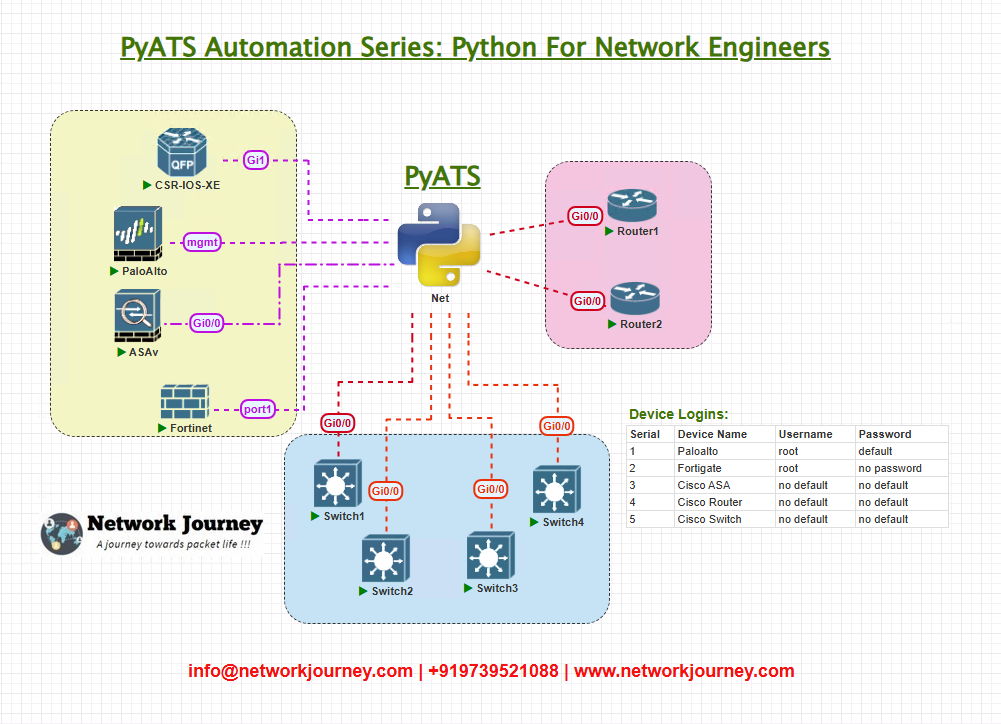
| Device Role | Vendor | Purpose |
|---|---|---|
| Spine 1 | Cisco Nexus | EVPN Fabric Spine |
| Spine 2 | Arista | EVPN Fabric Spine |
| Leaf 1 | Cisco Nexus | EVPN Fabric Leaf with VTEP |
| Leaf 2 | Arista | EVPN Fabric Leaf with VTEP |
| Firewall | Palo Alto | Perimeter Security Appliance |
| Management | Fortigate | Network security management |
| Orchestration | pyATS Test Server | Hosts testbed and automation scripts |
The fabric consists of VXLAN tunnels forming EVPN overlays with BGP control-plane connectivity for route distribution and MAC-VTEP mappings.
Topology & Communications
Device IP Addressing and Access
| Device | Management IP | CLI Access Protocol |
|---|---|---|
| Spine 1 | 192.168.1.10 | SSH |
| Spine 2 | 192.168.1.11 | SSH |
| Leaf 1 | 192.168.1.20 | SSH |
| Leaf 2 | 192.168.1.21 | SSH |
| Firewall | 192.168.1.30 | SSH/API |
| Management | 192.168.1.40 | HTTPS |
Communication Workflow
- pyATS test server connects over SSH/API to network devices.
- CLI commands and API calls are used for configuration/state retrieval.
- Structured data is parsed and validated against expected golden fabric state.
Workflow Script
from genie.testbed import load
from genie.libs.parser.utils import get_parser_exclude
from genie.libs.clean import clean_all
from genie.libs.sdk.apis.utils import get_parser_exclude
import json
def validate_evpn_fabric(testbed_file):
testbed = load(testbed_file)
# List of devices to validate
devices = ['spine1', 'spine2', 'leaf1', 'leaf2']
results = {}
for device_name in devices:
device = testbed.devices[device_name]
device.connect()
# Validate BGP EVPN sessions
evpn_bgp_output = device.parse('show bgp evpn summary')
# Validate MAC-VTEP mappings
mac_vtep_output = device.parse('show evpn mac')
# Validate fabric reachability
fabric_ping_output = device.parse('ping fabric 10.0.0.1')
results[device_name] = {
'bgp_summary': evpn_bgp_output,
'mac_vtep': mac_vtep_output,
'ping_fabric': fabric_ping_output
}
device.disconnect()
# Export results to JSON file
with open('evpn_fabric_validation_results.json', 'w') as f:
json.dump(results, f, indent=4)
return results
if __name__ == '__main__':
testbed_file = 'testbed.yml'
results = validate_evpn_fabric(testbed_file)
print('EVPN Fabric Validation Completed. Results saved in evpn_fabric_validation_results.json')
Explanation by Line
- Line 1–3: Imports necessary pyATS modules and standard libraries.
- Line 5: Loads the testbed file which defines device connections.
- Line 8: List of devices for validation.
- Line 10–23:
- Connect to each device.
- Run
show bgp evpn summaryto validate BGP EVPN sessions. - Run
show evpn macto extract MAC-VTEP mappings. - Run
ping fabric 10.0.0.1to verify fabric reachability. - Save structured output per device.
- Line 25: Export the results to a JSON file for reporting.
- Line 29: Executes validation and prints completion status.
testbed.yml Example
testbed:
name: evpn_validation_testbed
devices:
spine1:
type: router
os: iosxr
connections:
cli:
protocol: ssh
ip: 192.168.1.10
credentials:
default:
username: admin
password: admin123
spine2:
type: router
os: eos
connections:
cli:
protocol: ssh
ip: 192.168.1.11
credentials:
default:
username: admin
password: admin123
leaf1:
type: switch
os: iosxr
connections:
cli:
protocol: ssh
ip: 192.168.1.20
credentials:
default:
username: admin
password: admin123
leaf2:
type: switch
os: eos
connections:
cli:
protocol: ssh
ip: 192.168.1.21
credentials:
default:
username: admin
password: admin123
Post-validation CLI (Real Expected Output)
Example 1: BGP EVPN Summary
Device: spine1 EVPN BGP Neighbor State Messages 192.168.2.1 Established 15000 192.168.2.2 Established 14800
Example 2: MAC-VTEP Mapping
Device: leaf1 MAC Address VTEP IP VLAN aa:bb:cc:dd 10.0.1.1 100 ee:ff:gg:hh 10.0.1.2 200
Example 3: Fabric Ping Result
Device: spine2 Ping 10.0.0.1 (fabric controller): Success (5 packets transmitted, 5 received)
FAQS
Q1. Why automate EVPN fabric validation instead of manual checks?
A1. Automation ensures consistency, eliminates human error, speeds up validation, and provides structured reports, enabling faster troubleshooting and continuous monitoring.
Q2. Can this pyATS framework support non-Cisco devices?
A2. Yes. By leveraging pyATS parsers and APIs for multi-vendor support (Arista EOS, Palo Alto, Fortigate), this framework enables consistent validation across heterogeneous environments.
Q3. How does the testbed.yml contribute to the automation workflow?
A3. It defines the device inventory, OS types, credentials, and connections. This enables seamless and repeatable device access for pyATS jobs without hardcoded configurations.
Q4. What happens if an EVPN BGP session is down during validation?
A4. The script logs the session state as “Not Established” and flags it as a failure in the JSON report. This triggers alerts in automated CI/CD pipelines for fast remediation.
Q5. Is the output suitable for integration into CI/CD pipelines?
A5. Yes. The structured JSON and HTML outputs can easily be consumed by tools like Jenkins, GitHub Actions, or GitLab CI to automate network validation checks after code pushes.
Q6. Can the framework validate underlay as well as overlay separately?
A6. Yes. Separate tests can be written to validate underlay IP reachability and overlay EVPN BGP sessions independently, giving full control over validation granularity.
Q7. How frequently should EVPN fabric validation run in production?
A7. Ideally after any configuration change, regularly in scheduled intervals (e.g., nightly), and before/after software upgrades to ensure fabric integrity at all times.
YouTube Link
Watch the Complete Python for Network Engineer: Automate EVPN Fabric Validation Across Cisco/Arista/Paloalto/Fortigate Using pyATS for Cisco [Python for Network Engineer] Lab Demo & Explanation on our channel:
Join Our Training
If you are serious about mastering network automation with industry-proven practices and production-ready frameworks, join our 3-month instructor-led Python + Ansible + API course for network engineers.
Learn real-world use cases, hands-on labs, and deep dives
into automating multi-vendor network environments using Python for Network Engineer.
Join Now – Python + Ansible + API for Network Engineers
Enroll Now & Future‑Proof Your Career
Email: info@networkjourney.com
WhatsApp / Call: +91 97395 21088
![Day #92 PyATS Series] Automate EVPN Fabric Validation Across Cisco/Arista/Paloalto/Fortigate Using pyATS for Cisco [Python for Network Engineer]](https://networkjourney.com/wp-content/uploads/2025/09/Day-92-PyATS-Series-Automate-EVPN-Fabric-Validation-Across-Cisco_Arista_Paloalto_Fortigate-Using-pyATS-for-Cisco-Python-for-Network-Engineer.png)

![[Day #72 Pyats Series] Multi-vendor pre-change snapshot automation using pyATS for Cisco [Python for Network Engineer]](https://networkjourney.com/wp-content/uploads/2025/08/Multi-vendor-pre-change-snapshot-automation-using-pyATS-for-Cisco.png)
![[Day #33 PyATS Series] VRF Configuration Consistency Check Using pyATS for Cisco [Python for Network Engineer]](https://networkjourney.com/wp-content/uploads/2025/08/Day-33-PyATS-Series-VRF-Configuration-Consistency-Check-Using-pyATS-for-Cisco-Python-for-Network-Engineer.png)