[Day 93] Cisco ISE Mastery Training: Multi-Admin & RBAC
Table of Contents
Introduction
When multiple engineers touch Cisco ISE, who can change what becomes mission-critical. ISE’s RBAC (Role-Based Access Control) lets you carve the admin portal into safe zones (Work Centers, menus, data scopes), while Multi-Admin Approval (MAA) adds a second pair of eyes for high-impact changes (e.g., Authorization Policy edits, Network Devices, Certificates). Today you’ll design personas, build custom roles, map AD groups to Admin Groups, enable MAA, then validate everything via GUI and API.
Problem Statement
- Risk of misconfiguration: One click in Policy Sets can interrupt all access.
- Audit & separation of duties: Security teams must prove change control and least-privilege.
- Scale & consistency: As teams grow (Ops, Helpdesk, Guest, SecOps), privilege creep appears.
- Change control gaps: Emergency changes without review = outages or compliance findings.
Solution Overview (RBAC + MAA)
- RBAC: Create custom Admin Roles with read/write/no-access per area; bind users via Admin Groups to those roles; authenticate admins internally or with AD/LDAP/SAML.
- MAA: Force approval workflows before sensitive changes are committed. Requesters propose; Approvers review; ISE records the full audit trail.
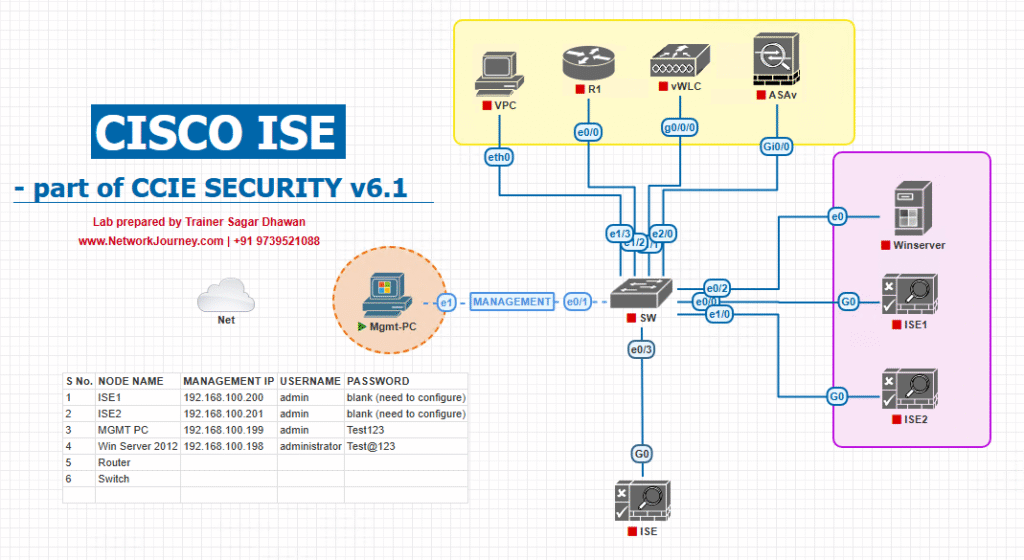
Sample Lab Topology
Platform: VMware for ISE PAN/MnT + PSN; EVE-NG for NADs (Cat9K, WLC), Windows 11 Admin VM with SSH/RDP/Browser.
Nodes:
- ISE PAN/MnT:
10.10.10.10 - ISE PSN (optional):
10.10.10.11 - AD DS:
10.10.20.20(with groupsISE-SuperAdmins,ISE-PolicyAdmins,ISE-Helpdesk,ISE-Auditors,ISE-Approvers) - Catalyst 9300:
10.10.30.30 - 9800-CL WLC:
10.10.30.40 - Admin PC:
10.10.40.10
Topology Diagram :
Personas we’ll implement:
- SuperAdmin – full control
- PolicyAdmin – R/W in Policy Sets & Policy Elements; no System settings
- Helpdesk – read-only Policies; R/W Endpoints/Guest; no System
- Auditor – read-only everywhere
- Approver – can approve MAA requests (separate from SuperAdmin)
Step-by-Step GUI Configuration Guide (with validation)
A) Pre-checks
- ISE licenses & services up
- CLI:
ise/admin# show application status ise - Validate PAN/MnT is running; PSN optional for this lab.
- CLI:
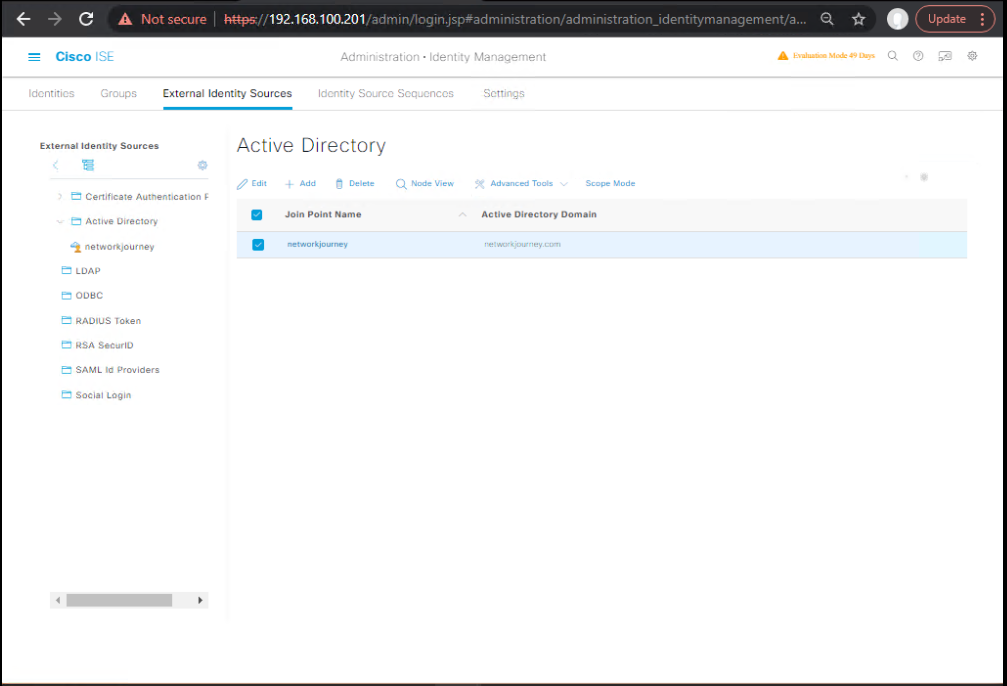
- Time/AD reachability
- CLI:
ise/admin# ntp server sync status(if configured) - GUI: Administration → Identity Management → External Identity Sources → Active Directory → Join Status: Connected.
- [Screenshot: AD Join Status]
- CLI:
B) Plan your RBAC matrix
Create a quick table:
| Persona | Work Centers & Menus | Access |
|---|---|---|
| SuperAdmin | All | Read/Write |
| PolicyAdmin | Policy Sets, Policy Elements, Groups | Read/Write |
| Helpdesk | Endpoints, Context Visibility, Guest | R/W Endpoints & Guest; Read Policies |
| Auditor | All | Read-only |
| Approver | MAA Console | Approve/Deny only |
C) Create Custom Admin Roles (RBAC)
Path: Administration → System → Admin Access → Roles
You can set Menu Access (Work Centers, menus) and Data Access (All, Group, Own). We’ll do 4 roles.
- Role: ISE-PolicyAdmin
- Menu Access:
- Policy → Read/Write
- Policy Elements → Read/Write
- Administration → Network Resources (Network Devices/NDGs) → Read-only
- Administration → System → No Access
- Operations → Reports/Live Logs → Read
- Data Access: All
- Save.
- [Screenshot: Role Editor – PolicyAdmin]
- Menu Access:
- Role: ISE-Helpdesk
- Menu Access:
- Endpoints → Read/Write
- Guest Access (if enabled) → Read/Write
- Policy & Policy Elements → Read
- Administration → System → No Access
- Data Access: Group (optional if you use Endpoint Identity Groups)
- Save.
- [Screenshot: Role Editor – Helpdesk]
- Menu Access:
- Role: ISE-Auditor
- Menu Access: All Read-only
- Data Access: All
- Save.
- [Screenshot: Role Editor – Auditor]
- Role: ISE-Approver
- Menu Access:
- Operations → Multi-Admin Approval → Read/Write
- Everything else Read-only
- Save.
- [Screenshot: Role Editor – Approver]
- Menu Access:
Validation:
- After saving each role, re-open to confirm permissions persisted.
- [Screenshot: Roles list]
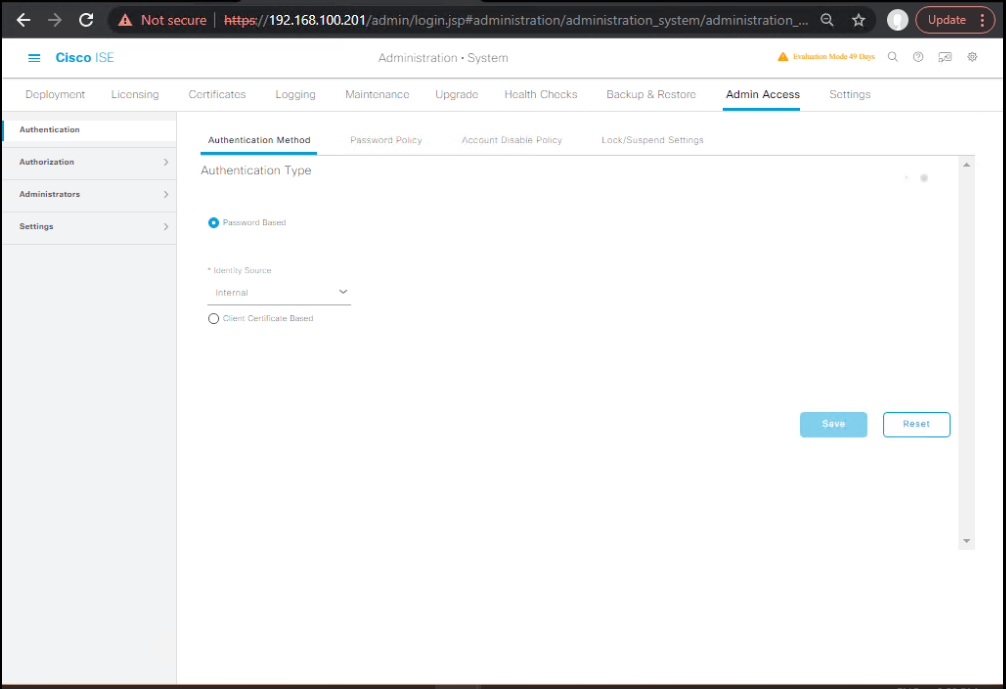
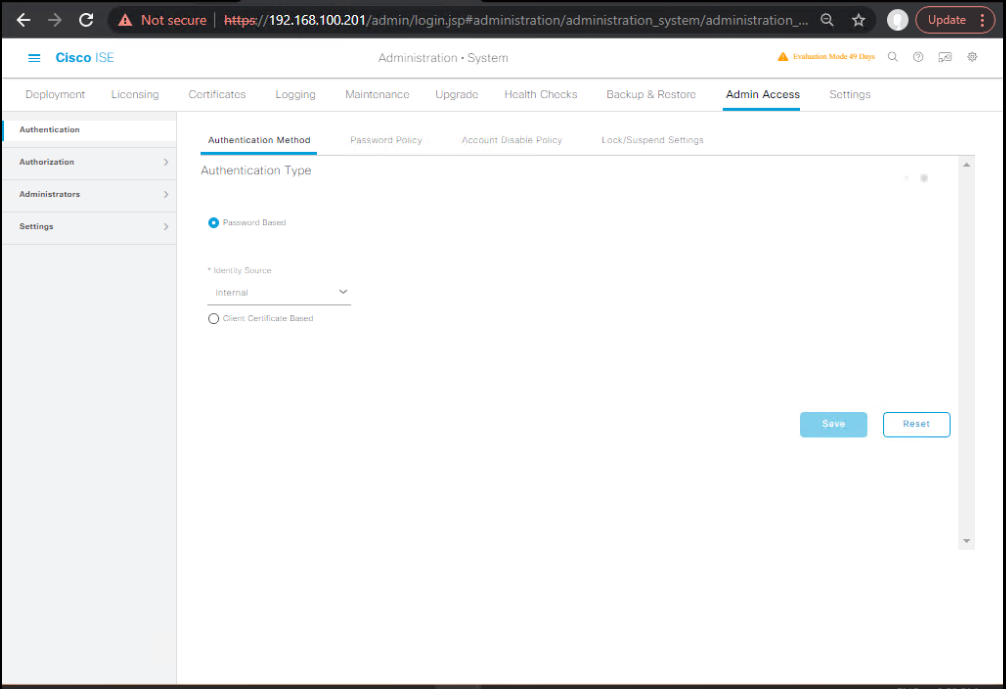
D) Configure Admin Authentication (Internal + AD)
Path: Administration → System → Admin Access → Authentication
- Enable External Authentication:
- Choose Active Directory (your joined domain).
- Select allowed identity stores: AD then Internal Admin as fallback.
- Save.
- [Screenshot: Admin Authentication Settings]
- Map external groups (AD) to ISE Admin Groups next (Step E).
Validation (CLI/API):
- GUI test comes later with real logins.
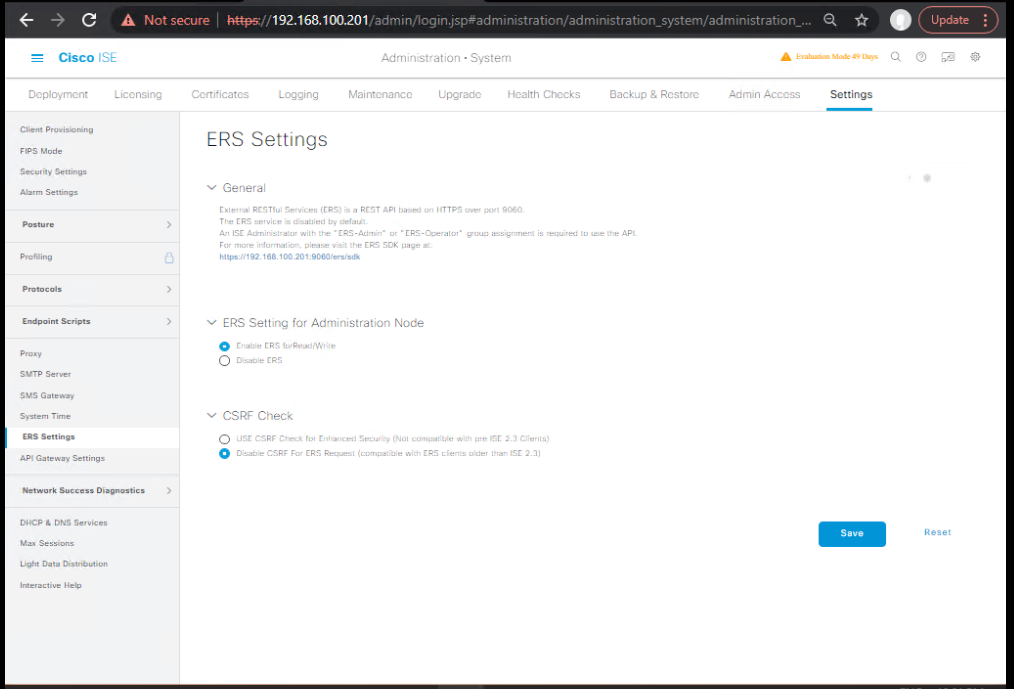
- API quick probe for admin endpoints (optional; ERS must be enabled):
- Administration → System → Settings → ERS Settings → Enable ERS.
- Then from Admin PC:
curl -k -u ers_admin:ERSpass https://10.10.10.10:9060/ers/config/adminuser -H "Accept: application/json" - Expect JSON (200 OK) if ERS is on.
E) Create Admin Groups and bind Roles
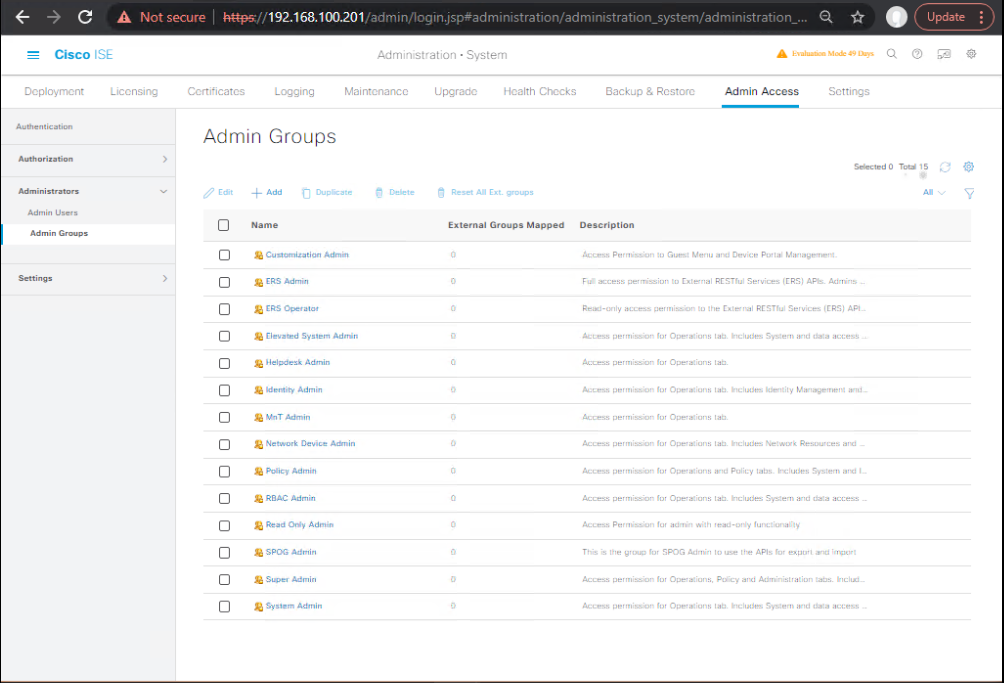
Path: Administration → System → Admin Access → Administrators → Admin Groups
Create 5 admin groups and assign our custom roles:
- AG-SuperAdmins → Role: Built-in Super Admin
- AG-PolicyAdmins → Role: ISE-PolicyAdmin
- AG-Helpdesk → Role: ISE-Helpdesk
- AG-Auditors → Role: ISE-Auditor
- AG-Approvers → Role: ISE-Approver
For each Admin Group:
- Click Add → Name → Assign Role → Under External Groups, click Add and select the AD group that should land here (e.g.,
ISE-PolicyAdmins). - Save.
- [Screenshot: Admin Group – Role + External Groups mapping]
Validation:
- In the Admin Group details, ensure the External Groups list shows your AD group(s).
- [Screenshot: Admin Groups list]
F) Create test admin identities
- AD Users:
paul.policy∈ISE-PolicyAdminsharry.help∈ISE-Helpdeskamy.audit∈ISE-Auditorsapra.approver∈ISE-Approverssue.super∈ISE-SuperAdmins
- Internal Break-glass:
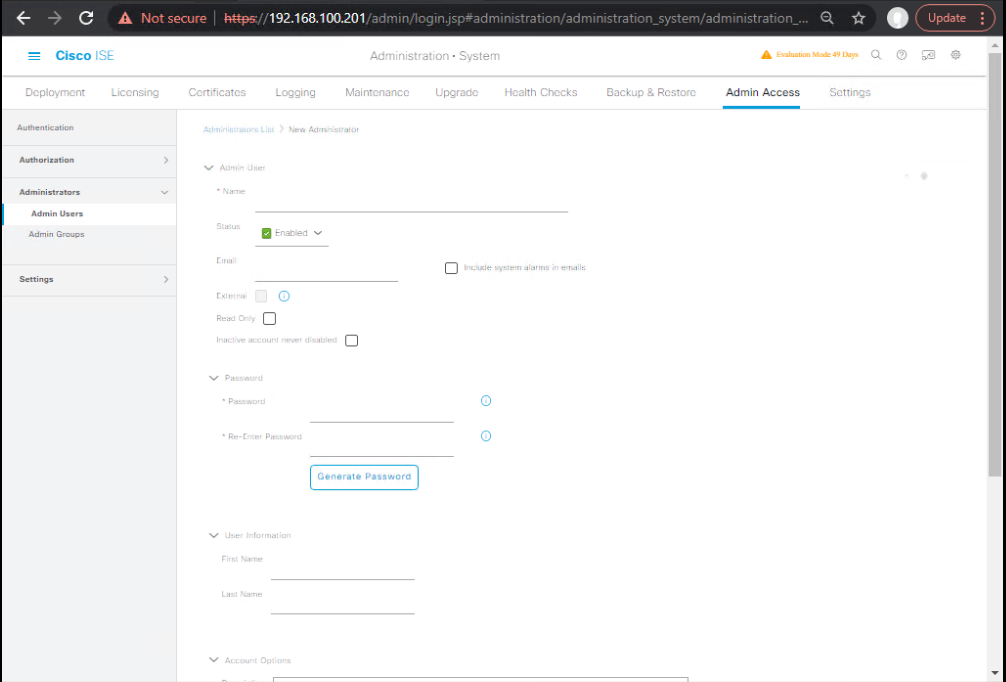
- Administration → System → Admin Access → Administrators → Admin Users → Add
- admin-local (local password, Role = Super Admin)
- [Screenshot: Internal Admin User]
Validation:
- Log out; log in as each persona; confirm menu visibility and edit ability.
- For each login, capture: [Screenshot: Top menu visibility as PolicyAdmin/Helpdesk/Auditor].
G) Enable Multi-Admin Approval (MAA) & build workflows
Path: Administration → System → Settings → Multi-Admin Approval
- Enable MAA → On
- Require Approval for:
- Policy Sets (add/edit/delete rules)
- Policy Elements (e.g., Conditions/Results)
- Network Devices/NDGs
- Certificates (optional)
- Approvals Required:
1(lab) /2(prod) - Approver Group(s): AG-Approvers (or AG-SuperAdmins as backup)
- Request Expiry: e.g., 24h
- Save.
- [Screenshot: MAA Settings]
- Require Approval for:
- MAA Scope/Granularity:
- Use the settings panel to include Create/Update/Delete for each resource type you want gated.
- [Screenshot: MAA Resources/Actions]
Validation:
- Navigate to Operations → Multi-Admin Approval — ensure the console opens (for Approvers).
- [Screenshot: MAA Console – Pending/Approved/Rejected]
H) Generate a MAA change request (Requester flow)
Login as: paul.policy (PolicyAdmin)
- Edit Authorization Policy:
- Policy → Policy Sets → → Authorization Policy
- Add a new rule (e.g.,
If EndpointGroup == BYOD → PermitLimited). - Click Save/Submit → You should see “Submit for Approval” (not immediate commit).
- [Screenshot: Authorization Policy – Pending Approval badge]
- Submit for Approval:
- Enter a comment: “BYOD limited access rule – change ticket #1234”.
- [Screenshot: Submit for Approval dialog]
Validation:
- Operations → Multi-Admin Approval (as
paul.policy): The change appears under Pending with status Awaiting Approval. - [Screenshot: MAA – Request detail (diff view if available)]
I) Approve the change (Approver flow)
Login as: apra.approver (Approver)
- Operations → Multi-Admin Approval → Pending → Select the request.
- Review the diff/summary → Click Approve (or Reject with reason).
- Once approved, ISE commits the change.
- [Screenshot: MAA – Approve action]
- [Screenshot: MAA – Status = Approved/Committed]
Validation:
- Reopen Authorization Policy as
paul.policy— rule is now active (no “Pending” ribbon). - [Screenshot: Authorization Policy – Active rule]
J) Audit & Reporting
- Operations → Reports → Administrative and Operational Audit
- Filter by User, Action, MAA.
- Export to PDF/CSV for evidence.
- [Screenshot: Audit Report – MAA approval trail]
- Versioning (optional):
- If your ISE version tracks policy revisions, capture version IDs pre/post approval.
K) API Validation (ERS) (optional but recommended)
ERS must be enabled (Administration → System → Settings → ERS Settings).
- List Roles:
curl -k -u ers_admin:ERSpass \ -H "Accept: application/json" \ https://10.10.10.10:9060/ers/config/adminrole - List Admin Groups:
curl -k -u ers_admin:ERSpass \ -H "Accept: application/json" \ https://10.10.10.10:9060/ers/config/admingroup - List Admin Users:
curl -k -u ers_admin:ERSpass \ -H "Accept: application/json" \ https://10.10.10.10:9060/ers/config/adminuser
Validation:
- Confirm your custom roles/groups appear with correct UUIDs and mappings.
Troubleshooting:
| Issue | Symptom in GUI/CLI | Root Cause | Fix |
|---|---|---|---|
| Wrong RBAC role assignment | User logs in but has no menu options or sees “Unauthorized” | Admin assigned wrong role or role missing permissions | Edit Admin Access > Roles and assign correct menus |
| Duplicate username conflicts | Login fails, “invalid credentials” error | Same username exists in ISE local DB and external LDAP/AD | Remove duplicate, or enforce identity source sequence |
| Time sync mismatch (NTP issue) | Login works sometimes, fails other times with “authentication failed” | ISE node not in sync with AD/LDAP | Sync NTP across ISE, AD, and devices |
| Locked accounts | Admin login fails, ISE shows “Account locked” | Repeated bad login attempts triggered lockout | Unlock account under Admin > Administrators |
| GUI login succeeds but RBAC policy not applied | User sees default full admin menus | RBAC role not mapped in “Admin Access Policies” | Fix mapping under Administration > System > Admin Access > Admin Access Control |
| TACACS+ fallback behavior | CLI logins succeed with fallback local admin but not with RBAC roles | Device not pointing TACACS to ISE | Check switch/router AAA config |
| Multi-admin conflicts | Changes not visible across nodes | Session stickiness on load balancer or replication delay | Check ISE Deployment > Synchronization Status |
| SSL/TLS mismatch for AD integration | Admins can’t log in via AD, ISE logs show TLS errors | Unsupported TLS version | Enable TLS 1.2/1.3 and upload proper certificates |
2. CLI Troubleshooting Commands
Run these from ISE CLI:
# Check system logs show logging application ise-psc.log show logging application ise-psc-debug.log # Check admin login attempts show logging application ise-admin.log | include <username> # Verify node sync status show running-config ise show application status ise # NTP check show ntp # AD/LDAP integration test test aaa group <groupname> <username> <password> # Certificate validation show crypto pki certificates
3. Log Files to Monitor
| Log File | Location | Purpose |
|---|---|---|
ise-admin.log | /var/log/ise/ | Tracks all admin logins, failures, lockouts |
ise-psc.log | /var/log/ise/ | Policy Service checks, RBAC role mapping |
ise-psc-debug.log | /var/log/ise/ | Debug RBAC authorization decisions |
system.log | /var/log/ | General system-level events |
ntp.log | /var/log/ | NTP sync issues affecting login |
4. GUI Troubleshooting Validation
- Check active sessions:
- Navigate to: Operations > Reports > Audit > Admin Access
- Look for login attempts, roles applied, and errors.
- [Screenshot: ISE Admin Audit Logs]
- Check RBAC Policy Mapping:
- Navigate to: Administration > System > Admin Access > Admin Access Control
- Verify username → group → role mapping.
- [Screenshot: ISE RBAC Mapping Screen]
- Check Lockouts:
- Navigate to: Administration > System > Admin Access > Administrators
- Check status column.
5. Debugging Example (Field Case)
Scenario: AD admin “netops1” cannot log in.
- Step 1 – CLI Test:
test aaa group AD_GROUP netops1 Cisco123Output:Authentication failed – no role mapped. - Step 2 – Check logs:
show logging application ise-admin.log | include netops1Shows:User authenticated but no authorization policy applied. - Step 3 – GUI Check:
In Admin Access Control, role mapping for AD_GROUP missing. - Fix: Add mapping → Assign “Helpdesk Role” → Save → Test login again.
Validation: User logs in with limited Helpdesk menus, not full Super Admin.
6. Validation Workflow (Engineer Checklist)
- Confirm NTP & clock sync across ISE + AD.
- Verify admin added in correct Identity Source.
- Test AAA from CLI.
- Check logs in ise-admin.log.
- Verify RBAC mapping in GUI.
- Perform login test with new admin.
- Confirm correct menus visible (cross-verify with RBAC role definition).
FAQs – Cisco ISE Multi-Admin & RBAC
FAQ 1: What is the difference between a Super Admin and a System Admin in ISE?
- Super Admin has unrestricted access to all ISE functions, including system settings, licensing, RBAC, and nodes.
- System Admin can handle system-level tasks like certificates, deployment, and patching but may not configure all policy-related features.
- In practice, most production teams use Super Admin sparingly and delegate daily operations with RBAC-defined roles.
FAQ 2: Can we create completely custom roles in ISE?
- Yes .
- Navigate: Administration > System > Admin Access > Roles > Add
- You can define which menus/submenus are visible (e.g., only Reports or only Policy Sets).
- Validation: Test login with a new admin → only authorized menus should appear.
FAQ 3: How does Multi-Admin approval workflow work?
- Some sensitive actions (e.g., deleting a node, updating a certificate) can be restricted.
- One admin requests the change.
- Another admin approves/rejects it.
- This prevents insider misuse or accidental misconfiguration.
- Validation: Try deleting a policy set with workflow enabled → system prompts “Approval required.”
FAQ 4: What happens if two admins edit policies at the same time?
- ISE has session locks for certain objects.
- If Admin A is editing a policy, Admin B sees a “Locked by user” warning.
- If both are editing different sections, changes merge during commit.
- Validation: Open two browsers with two accounts and attempt edits simultaneously.
FAQ 5: Can RBAC roles be tied to Active Directory groups?
- Yes .
- Use Admin Access Policies to map AD group → specific role.
- Example:
- AD group Helpdesk → ISE role Helpdesk Operator.
- AD group NetEng → ISE role Policy Admin.
- Validation: Add user to AD group → relogin → check menu restrictions.
FAQ 6: What is the fallback if AD/LDAP goes down?
- ISE falls back to local ISE admin accounts.
- Always keep at least two local Super Admins as break-glass accounts.
- Validation: Temporarily disable AD connector and attempt login with local account.
FAQ 7: Can we restrict admins to manage only certain NADs (network devices)?
- Yes (Granular Device Access Control).
- In RBAC, you can restrict role permissions to specific device groups.
- Example: Operator can only manage Branch Switches, not Core Routers.
- Validation: Assign role → login → try accessing restricted NAD group.
FAQ 8: Where can we monitor which admin did what changes?
- Navigate: Operations > Reports > Audit > Admin Access.
- Each action (login, config change, approval) is logged with username, IP, timestamp.
- CLI check:
show logging application ise-admin.log
FAQ 9: What happens if an admin account gets locked?
- Lockout occurs after repeated failed login attempts.
- Unlock via GUI: Administration > System > Admin Access > Administrators → Unlock.
- CLI recovery: Use local CLI super admin to reset account.
FAQ 10: How do we validate that RBAC is working correctly?
- Create 3 test accounts:
test-super→ Full Super Admintest-helpdesk→ Reports + Endpoint onlytest-ops→ Policy view only, no edits
- Login with each → Verify menu visibility.
- Logs:
- GUI: Admin Access Audit Reports
- CLI:
show logging application ise-psc-debug.log | include <username>
- If mismatch, check Admin Access Control Policy for missing role mapping.
YouTube Link
For more in-depth Cisco ISE Mastery Training, subscribe to my YouTube channel Network Journey and join my instructor-led classes for hands-on, real-world ISE experience
Closing Notes
- Design personas first, then implement roles to match real duties.
- Bind AD groups → Admin Groups → Roles for scalable access.
- Turn on MAA for changes that can impact availability/security.
- Always validate: Log in as each persona, attempt allowed/denied actions, and capture MAA approvals + Audit reports for evidence.
Upgrade Your Skills – Start Today
“For more in-depth Cisco ISE Mastery Training, subscribe to my YouTube channel Network Journey and join my instructor-led classes.”
Fast-Track to Cisco ISE Mastery Pro (4-month ILT)
- 90+ hands-on ISE labs (RBAC, MAA, TrustSec, pxGrid, APIs, SIEM, TACACS+)
- Troubleshooting Bible (logs, workflows, validation)
- Enterprise patterns, interview prep, and capstone projects
Enroll / Course outline: https://course.networkjourney.com/ccie-security/
Enroll Now & Future‑Proof Your Career
Email: info@networkjourney.com
WhatsApp / Call: +91 97395 21088


![[Day 23] Cisco ISE Mastery Training: Guest VLAN & Critical VLAN Configuration](https://networkjourney.com/wp-content/uploads/2025/08/Day-23-Cisco-ISE-Mastery-Training-Guest-VLAN-Critical-VLAN-Configuration.png)
