[Day 94] Cisco ISE Mastery Training: Disaster Recovery & Backup
Table of Contents
Introduction
When Cisco ISE is the policy brain for 802.1X/MAB, VPN, and wireless access, a misstep in backups or a slow, incorrect restore means no logins, no network. Disaster Recovery (DR) in ISE isn’t just “take a backup.” It’s:
- Designing Admin/MnT high availability,
- Capturing the right data (config vs operational),
- Storing encrypted backups off-box, and
- Rebuilding nodes (with the same identity) in a calm, repeatable way.
Your objective today: build a production-grade, fully validated DR runbook for ISE that you can execute blindfolded (almost). We’ll configure repositories, schedule encrypted backups, prove them in the logs, simulate a PAN failure, promote the secondary, and restore a lab node from scratch—all with GUI + CLI evidence.
(ISE separates Configuration backup from Operational/MnT backup; restores are version/patch bound; internal CA private keys are not included in config backups—plan accordingly.) (Cisco)
Problem Statement
Real-world pain this solves in NAC:
- A failed Primary PAN halts policy changes, certificate trust updates, and replication.
- Loss of the MnT database kills compliance/audit evidence; you can’t answer “who got on when/where.”
- PSNs keep authenticating, but if you can’t quickly promote or restore, change windows blow up, audits fail, and execs get grumpy.
- Backups taken incorrectly (wrong repo, wrong encryption, wrong hostname/IP on restore) won’t restore. (Cisco)
Solution Overview (What ISE gives you)
- Two backup types:
- Configuration (PAN database, trust store, policies, and more)
- Operational (MnT) (sessions, RADIUS/TACACS logs, reports).
Both can be scheduled or run on-demand to a remote repository (SFTP/NFS/FTP/disk). (Cisco)
- Encrypted backups (GUI or CLI) with encryption key you manage.
- PAN HA: Secondary PAN can be promoted (“Make Primary”) if the Primary dies; later you reimage/restore the old Primary and rejoin. (Cisco)
- Strict restore rules: Same ISE major/minor/patch, same hostname and usually same IP/FQDN (especially if certs pin identity). Internal CA private keys are not included in config backups—export CA store separately. (Cisco)
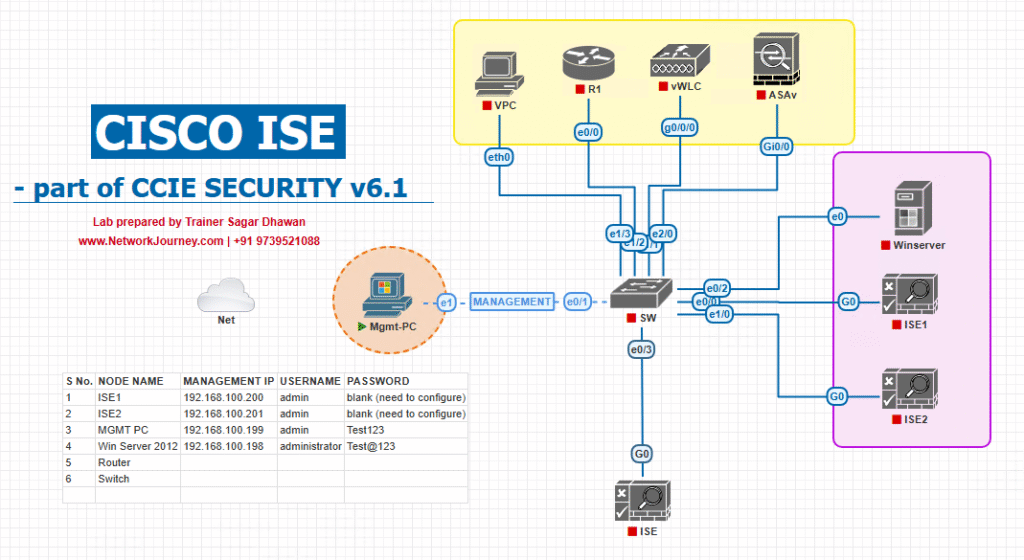
Sample Lab Topology
Platform: VMware ESXi or EVE-NG for virtual ISE/wireless/switch nodes.
Nodes:
- ISE-PAN1 (Primary Admin + Primary MnT)
- ISE-PAN2 (Secondary Admin + Secondary MnT)
- ISE-PSN1/2 (two Policy Service Nodes behind a load-balancer or WLC AAA pointing to both)
- SFTP-Repo (Ubuntu SFTP on VLAN10 with dedicated user/folder)
- AD/DC, DNS/NTP
- Catalyst Switch (dot1x/MAB lab ports)
- Cisco WLC (WLAN using ISE for AAA)
- Endpoints (Win10/11, iPhone/Android)
Topology diagram:
Step-by-Step GUI Configuration Guide (with CLI validation)
Phase A — Prepare a Secure Remote Repository (SFTP)
Goal: Create an off-box encrypted backup location.
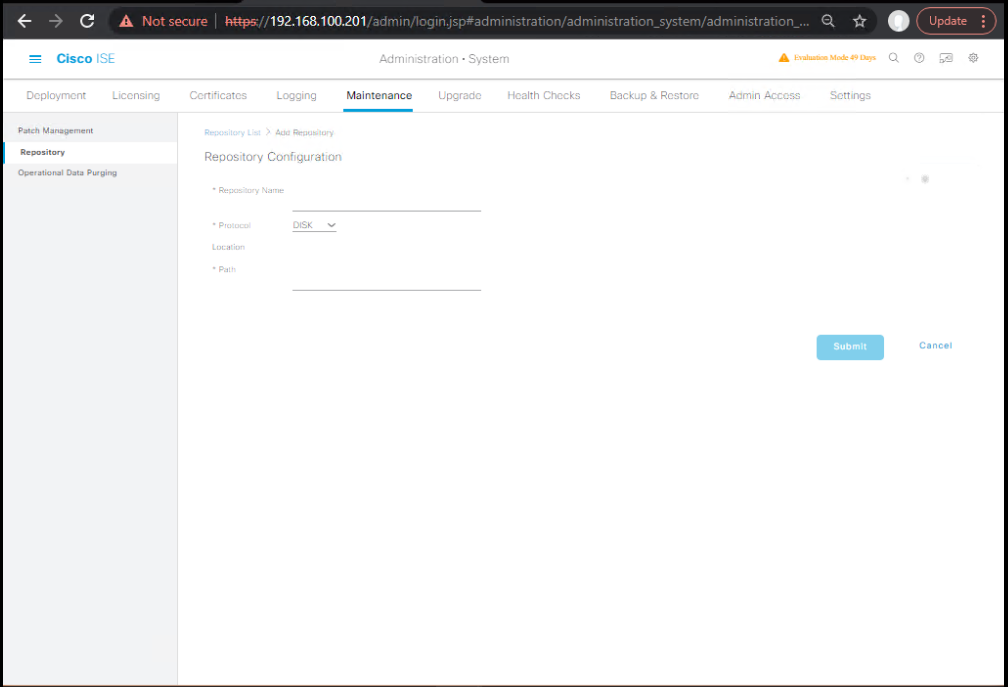
A1. Create repo (GUI):
- Admin > System > Maintenance > Repository → Add.
- Name:
SFTP_REPO - Protocol: SFTP
- Server:
10.10.20.50Path:/ise-backups - Username/Password:
ise-backup/•••• - Submit.
- [Screenshot: ISE Add Repository]
(If ISE prompts about SFTP host key, you must add host key via CLI once.) (Cisco)
- [Screenshot: ISE Add Repository]
A2. Trust the SFTP host key (CLI on any ISE node):
ise/admin# ssh ise-backup@10.10.20.50 # type 'yes' to accept fingerprint (saved in known_hosts), then Ctrl+C
Validate repository (CLI):
ise/admin# show repository SFTP_REPO # Expect URL sftp://10.10.20.50/ise-backups and free space
(Repo config & show commands are standard ISE CLI.) (Cisco)
Phase B — Schedule Encrypted Configuration Backups
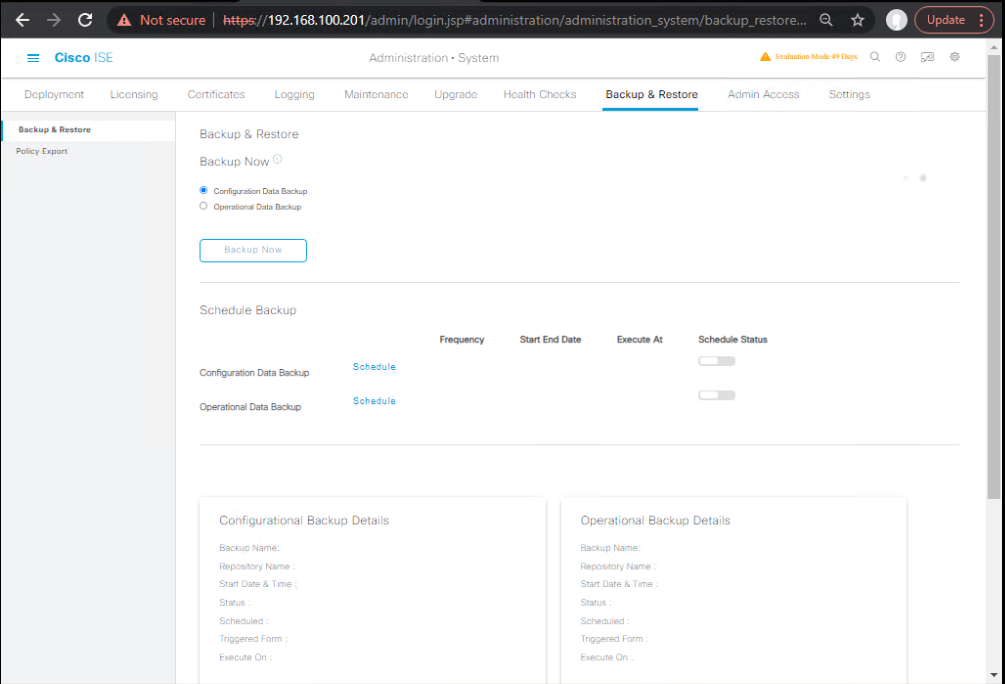
B1. Run an immediate config backup (GUI):
- Admin > System > Maintenance > Backup & Restore → Backup Now.
- Type: Configuration
- Repository:
SFTP_REPO - Filename prefix:
cfg- - Encryption Key: enter strong passphrase
- Start.
- [Screenshot: ISE Backup & Restore – Backup Now] (Cisco)
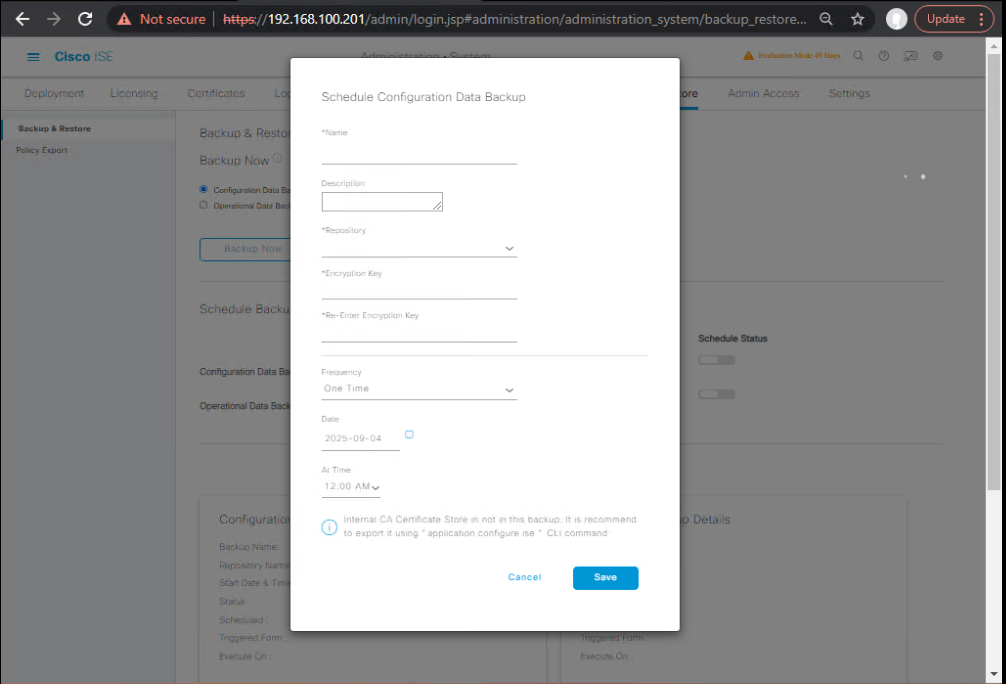
B2. Schedule nightly config backups (GUI):
- On same page, Schedule → Add.
- Type: Configuration; Repository:
SFTP_REPO - When: Daily at 02:15; Retention: 14 copies.
- Encryption Key: (same passphrase)
- Save.
- [Screenshot: ISE Backup Schedule]
B3. Validate (GUI + CLI):
- GUI: Operations/Reports → System → Backup & Restore (or Operational Audit) → confirm Status: SUCCESS with timestamps & file names.
- [Screenshot: ISE Backup Report] (Cisco)
- CLI (3.x):
ise/admin# show backup status ise/admin# dir repository SFTP_REPO ise/admin# dir repository SFTP_REPO | include cfg-
(show-mode “backup” status is in ISE CLI reference.) (Cisco)
Phase C — Schedule Encrypted Operational (MnT) Backups
C1. Immediate MnT backup (GUI):
- Admin > System > Maintenance > Backup & Restore → Backup Now.
- Type: Operational
- Repository:
SFTP_REPO - Filename prefix:
ops- - Encryption Key: enter passphrase → Start.
- [Screenshot: MnT (Operational) Backup Now] (Cisco)
C2. Schedule weekly MnT backups:
- Schedule → Weekly (e.g., Sun 03:00), Retention: based on audit policy (e.g., 8 copies).
- [Screenshot: MnT Backup Schedule]
C3. Validate (GUI + CLI):
- GUI report shows Operational backup success and sizes (large).
- CLI:
ise/admin# show backup status ise/admin# dir repository SFTP_REPO | include ops-
Important: Config and Operational are separate artifacts; you normally restore Config first, then (optionally) Operational. Internal CA private keys are not included in config backups; export the CA store via CLI
application configure iseoptions Export Internal CA Store and keep safe. (Cisco)
Phase D — CLI: Repositories + On-Demand Backups (power-user)
ISE 3.2+ supports the
backup/restorecommands; many engineers still use the olderapplication backup/restoreform in earlier releases—TAB-complete on your exact version. Syntax examples below align to current CLI reference. (Cisco)
D1. Define repository via CLI (if you prefer CLI):
ise/admin# configure terminal ise/admin(config)# repository SFTP_REPO ise/admin(config-Repository)# url sftp://10.10.20.50/ise-backups ise/admin(config-Repository)# user ise-backup ise/admin(config-Repository)# password plain <SFTP_PASSWORD> ise/admin(config-Repository)# exit ise/admin# show repository SFTP_REPO
D2. Run on-demand CONFIG backup (CLI):
# Example filename 'cfg-2025-08-20' ise/admin# backup ise-config cfg-2025-08-20 repository SFTP_REPO encryption-key plain <BACKUP_KEY> # monitor: ise/admin# show backup status ise/admin# dir repository SFTP_REPO | include cfg-2025-08-20
(Backup/Show syntax per ISE CLI Reference.) (Cisco)
D3. Run on-demand OPERATIONAL (MnT) backup (CLI):
ise/admin# backup ise-operational ops-2025-08-20 repository SFTP_REPO encryption-key plain <BACKUP_KEY> ise/admin# show backup status ise/admin# dir repository SFTP_REPO | include ops-2025-08-20
Phase E — PAN High Availability & Promotion Drill
E1. Verify PAN roles (GUI):
- Admin > System > Deployment:
- ISE-PAN1 = Primary Admin, Primary MnT
- ISE-PAN2 = Secondary Admin, Secondary MnT
- [Screenshot: ISE Deployment – Node Roles] (Cisco)
E2. Simulate Primary PAN outage:
- On ISE-PAN1 CLI:
ise-pan1/admin# application stop ise ise-pan1/admin# show application status ise
- Validate authentications continue (PSNs still work).
E3. Promote Secondary PAN to Primary (GUI on ISE-PAN2):
- Admin > System > Deployment → (Actions) → Make Primary.
- Confirm.
- [Screenshot: Make Primary Dialogue]
- Validate: ISE-PAN2 now shows Primary Admin role; policies editable. (Cisco)
E4. Bring PAN1 back later: (after reimage/restore—Phase F)
- Once restored, register it back as Secondary and synchronize.
Phase F — Full Node Restore (Config first, then Operational)
Golden rules: Restore onto same ISE version/patch, and (practically) same hostname/FQDN and IP to avoid certificate/trust issues. Internal CA private keys are not inside the config backup—export/import CA store separately. (Cisco)
F0. Prep the target VM/appliance:
- Fresh ISE install same version/patch as the backup; set hostname/IP to match the original node identity for a clean restore.
- [Screenshot: ISE Setup Wizard Completed]
F1. Re-create repository (CLI): (same as D1)
F2. Restore Configuration (CLI):
# Choose the exact backup filename visible in repository ise/admin# restore cfg-2025-08-20 repository SFTP_REPO encryption-key plain <BACKUP_KEY> # (Optional) include ADE-OS system settings if your backup captured it: ise/admin# restore cfg-2025-08-20 repository SFTP_REPO encryption-key plain <BACKUP_KEY> include-adeos # ISE will restart automatically. Monitor boot: ise/admin# show application status ise
(Restore command and include-adeos option per CLI Reference.) (Cisco)
F3. Restore Operational (MnT) data (optional):
ise/admin# restore ops-2025-08-20 repository SFTP_REPO encryption-key plain <BACKUP_KEY>
F4. Import Internal CA store (if you used ISE as CA):
ise/admin# application configure ise # [7] Export / [8] Import Internal CA Store (use your exported file set)
F5. Rejoin deployment (GUI):
- If this was a PAN: Admin > System > Deployment → Register / Assign Persona (Admin Secondary, MnT Secondary) → Save → Synchronize.
- Validate Replication: SUCCESS and PAN role is correct.
- [Screenshot: Deployment – Replication Success] (Cisco)
Phase G — End-to-End Validation Checklist (print & tick)
Backups exist & are encrypted
- GUI report shows SUCCESS for config & operational backups.
show backup statusreturns last job SUCCESS.dir repository SFTP_REPOshows expected files & sizes. (Cisco)
Repository health
show repository SFTP_REPOshows reachable, free space.- SFTP host key trusted (able to SSH once). (Cisco)
PAN HA
- Secondary can be promoted (GUI “Make Primary”).
- PSNs keep authenticating during PAN outage. (Cisco)
Restore
- Config restore completes; ISE restarts; services RUNNING.
- Optional: MnT restore completes; old reports visible.
- If used ISE-CA, Internal CA store imported.
- Node re-registered and replication = SUCCESS. (Cisco)
FAQs – Cisco ISE Disaster Recovery & Backup
1. What exactly is the difference between a Configuration and Operational (MnT) backup?
- Configuration backup = policies, endpoints, device profiles, trust store (certs), settings.
- Operational backup = Monitoring & Troubleshooting (MnT) logs, RADIUS/TACACS sessions, reports.
- You normally restore Config first, then Operational if audit logs are required.
2. Do I need the exact same version of ISE to restore a backup?
- Yes. Backups are version and patch bound.
- Example: A config backup from ISE 3.2 patch 3 will not restore on 3.2 patch 2.
- Always upgrade new node to the same patch level before restoring.
3. Do I need the same hostname and IP during restore?
- Best practice: same hostname/FQDN and usually the same IP.
- Certificates in trust store are bound to FQDN → mismatches cause trust issues.
- GUI shows restore will fail if hostname doesn’t match.
4. How do I encrypt backups, and what if I lose the encryption key?
- When creating/scheduling a backup, enter an Encryption Key.
- In CLI, append:
backup ise-config cfg-20250820 repository SFTP_REPO encryption-key plain <KEY> - If you lose the key → backup is unusable. Always store in a secure vault.
5. Where do I check if a backup succeeded?
- GUI: Operations → Reports → System → Backup & Restore.
- CLI:
show backup status dir repository SFTP_REPO - Look for Status: SUCCESS and correct file size.
6. How do I promote a Secondary PAN to Primary?
- GUI: Administration → System → Deployment → (Actions) → Make Primary.
- CLI validation:
show running-config iseconfirms new primary. - PSNs continue authentication without disruption during promotion.
7. My SFTP repository fails when I trigger a backup — why?
- Common causes:
- SFTP host key not accepted (fix: SSH once from ISE CLI to repo host).
- Wrong path permissions on server.
- Incorrect credentials.
- Disk space full.
- CLI test:
show repository SFTP_REPO
8. If I use ISE as a Certificate Authority (Internal CA), will backups capture private keys?
- No, Config backup includes only the CA certificates, not private keys.
- Export Internal CA store separately:
application configure ise # Option 7: Export Internal CA Store
9. Can I back up to local disk instead of remote repo?
- Yes, to disk: repository, but it consumes VM disk space.
- Best practice = SFTP/NFS remote repo for secure, redundant storage.
- Use CLI:
dir disk:/
10. What’s the recommended DR test cycle in production?
- Run Config backup nightly + Operational backup weekly.
- Test PAN promotion quarterly.
- Perform a full restore drill (lab or DR node) at least once per year.
- Always validate with
show backup status+ GUI reports.
YouTube Link
For more in-depth Cisco ISE Mastery Training, subscribe to my YouTube channel Network Journey and join my instructor-led classes for hands-on, real-world ISE experience
Closing Notes
- Treat ISE DR as a runbook: repo → encrypted backups → promote/preserve → restore → rejoin.
- Practice the promotion and restore workflows quarterly.
- Keep encryption keys and CA export in a separate vault.
- Monitor backup job health just like you monitor PSNs—no surprises in real incidents. (Cisco)
Upgrade Your Skills – Start Today
Want a guided path, labs, and accountability? I run a focused 4-month, instructor-led progra under Network Journey focused on CCIE Security depth with real-world ISE mastery. Expect structured modules, live labs, community support, and interview-ready artifacts.
“For more in-depth Cisco ISE Mastery Training, subscribe to my YouTube channel — Network Journey and join my instructor-led classes.”
Your next steps
- Apply for the next cohort (limited seats).
- Book a 1:1 discovery call to map your role, timelines, and outcomes.
- Bring your current ISE topology—get a personalized DR/backups improvement plan.
Learn more & register here → (course outline ref: course.networkjourney.com/ccie-security/)
Enroll Now & Future‑Proof Your Career
Email: info@networkjourney.com
WhatsApp / Call: +91 97395 21088
(Note: Program specifics evolve; confirm the latest dates, curriculum, and bonuses on the course page.)



