[Day 95] Cisco ISE Mastery Training: Certificate Lifecycle Management
Table of Contents
Introduction
In Cisco ISE, every control-plane and data-plane handshake you rely on (Admin GUI, EAP-TLS, Guest/BYOD portals, pxGrid, RADIUS DTLS/RADSEC, SAML, ERS/OpenAPI) is anchored to X.509 certificates. A single expired, mismatched, or incorrectly-assigned cert can take down logins, break posture, or sever pxGrid.
Today’s workbook teaches you the full certificate lifecycle in ISE: plan → request (CSR) → sign → import/bind → assign usage → trust chain → revocation (CRL/OCSP) → rotation/renewal → decommission, with step-by-step tasks and validation both in GUI and CLI/client tools.
Problem Statement
Typical field failures:
- EAP-TLS fails because the PSN’s EAP cert lacks proper SAN or chain.
- Admin GUI throws browser warnings; portals break on mobile due to intermediate CA not trusted.
- pxGrid/DNAC/FMC integrations fail due to wrong usage or missing trust.
- Renewals cause outages because Admin/EAP roles were flipped without drain mode.
- Internal CA/EST/SCEP not enabled → BYOD and cert onboarding dead.
- Expiry alerts ignored → weekend outage.
Solution Overview (What ISE Provides)
ISE provides:
- System Certificates per node with explicit Usage (Admin, EAP, RADIUS DTLS, pxGrid, Portal, SAML, etc.). GUI path: Administration → System → Certificates → Certificate Management (System Certificates, Trusted Certificates, CSRs). (Cisco)
- CSR generation & binding workflow (create CSR, get CA-signed cert, bind to private key in ISE). (Cisco)
- Trust store management (Root/Intermediate import/export) and Export with private key when needed. (Cisco)
- Wildcard support (with “Allow Wildcard Certificate”) and SAN best practice for EAP/Admin/Portal. (Cisco)
- Internal CA & EST services for BYOD/managed endpoints, plus CLI export/import of the internal CA store for DR. (Cisco)
- Renewal guidance & outage avoidance (role assignment implications; Admin role triggers GUI service restart). (Cisco)
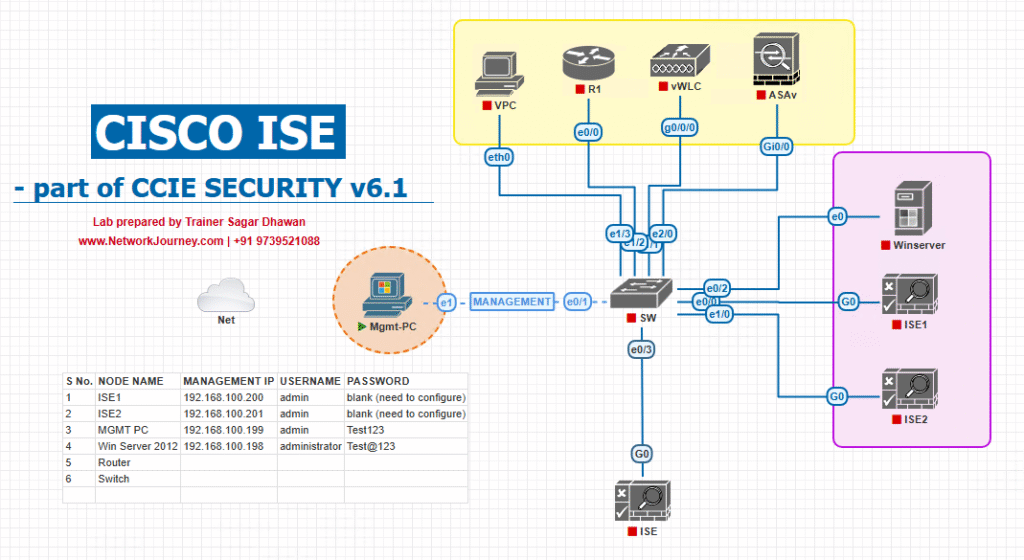
Sample Lab Topology (VMware/EVE-NG)
Text description
- Compute: VMware ESXi (or EVE-NG) hosting:
- ISE-PAN/MnT (Primary)
- ISE-PSN1, ISE-PSN2
- Windows Server (AD DS + AD CS Enterprise CA + NDES optional)
- Linux jump host (OpenSSL/curl) & Windows 11 client (wlan/dot1x tools)
- Network:
- Catalyst Switch (access, 802.1X/MAB)
- WLC (9800/3504) + AP for BYOD & portals
- Integrations: pxGrid consumer (e.g., FMC/DNAC)
- External: Enterprise PKI (Root + Intermediate(s))
Topology diagram:
Step-by-Step GUI Configuration Guide
A) Pre-flight Checklist (Do this once)
- NTP/DNS/FQDN correct for all nodes.
- Time synced with AD/CA.
- Repository to move/export files (SFTP).
- CA hierarchy: Root + Intermediate(s) Base64 available.
- Define which usages per node:
- PAN: Admin, SAML (if used).
- PSNs: EAP Authentication, Portal, RADIUS DTLS/RADSEC (if used).
- pxGrid node: pxGrid usage.
- SAN plan (FQDNs; wildcard if policy approves). Check “Allow Wildcard Certificate” if using wildcard. (Cisco)
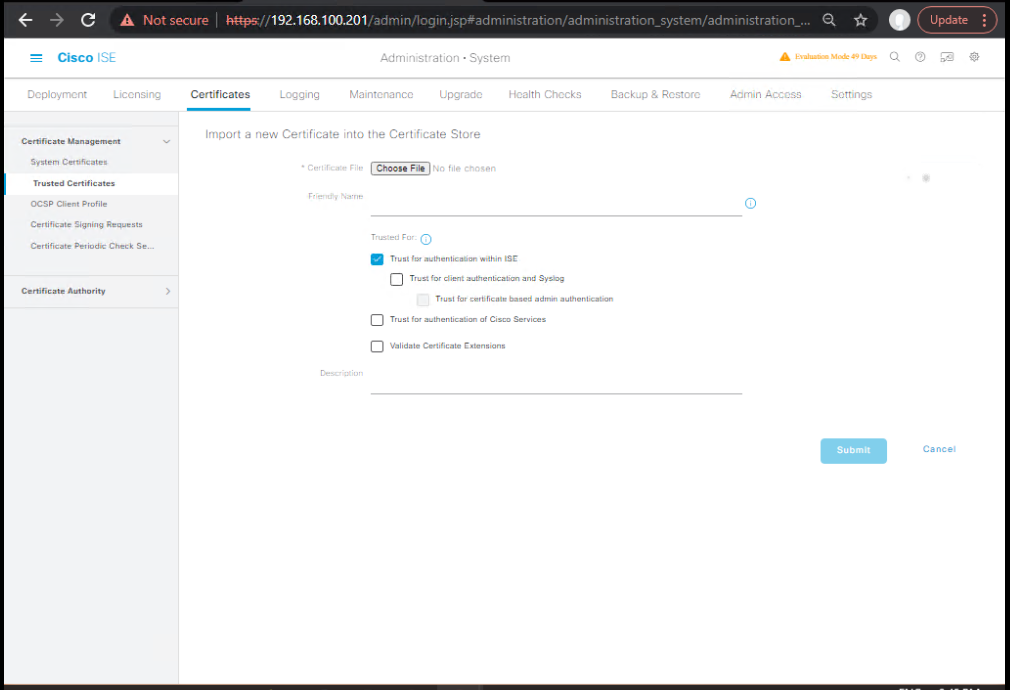
B) Import CA Trust Chain (Root/Intermediates)
- GUI:Administration → System → Certificates → Certificate Management → Trusted Certificates → Import.
- Import Root CA (use cases: Trust for authentication within ISE, EAP, Admin, pxGrid as needed).
- Import Intermediate CA(s).
- Ensure Trust for checkboxes match your usages (EAP, Admin, Portal, etc.).
[Screenshot: Trusted Certificates – Import dialog] (Cisco)
Validate
- GUI: Trusted Certificates list shows Root/Intermediate Enabled.
- Client: From jump host:
# Fetch portal chain openssl s_client -connect ise-psn1.lab.local:443 -showcerts </dev/null | openssl x509 -noout -issuer -subject # Expect to see your CA in chain (after Step D assignment) - Note: If a trusted cert is “in use”, ISE may block delete/disable until references cleared. (Reddit)
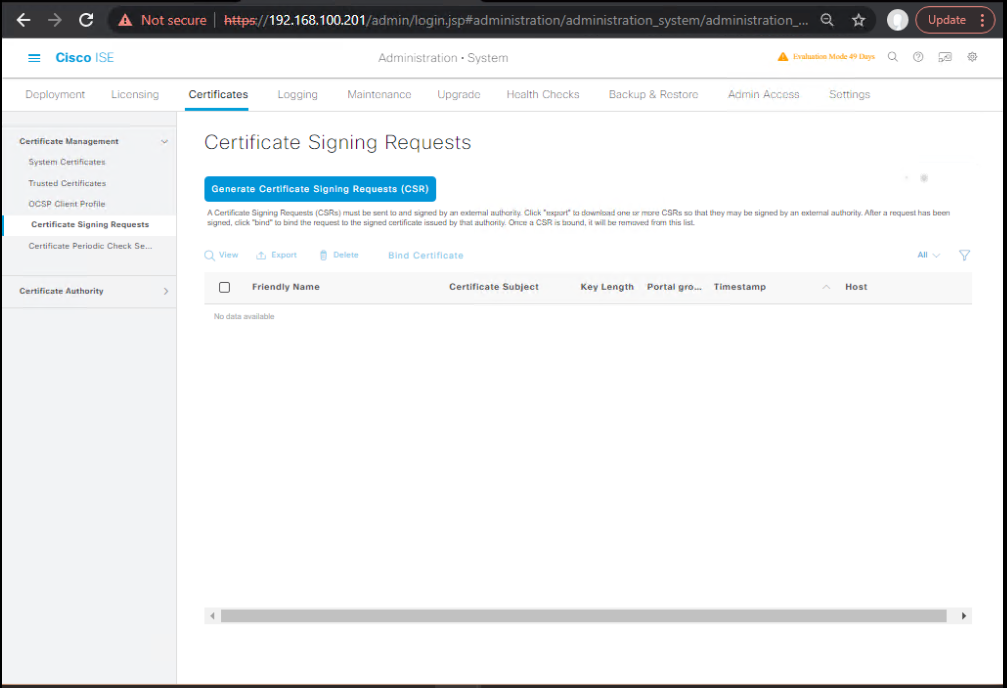
C) Generate CSRs (Per Node)
- GUI:Administration → System → Certificates → Certificate Management → Certificate Signing Requests → Generate CSR.
- Node: choose the specific node (PAN/PSN).
- Key size: 2048/3072 (org policy).
- Subject/SAN: add FQDN (and wildcard if approved).
- Usage (pre-select): for clarity, but final assignment happens on import.
[Screenshot: CSR – Generate] (Cisco)
- Export CSR and submit to your Enterprise/3rd-party CA.
[Screenshot: CSR – Export] (Cisco)
Validate
- GUI: CSR appears in list with Pending status.
- Client: Track request in CA (AD CS pending/request ID).
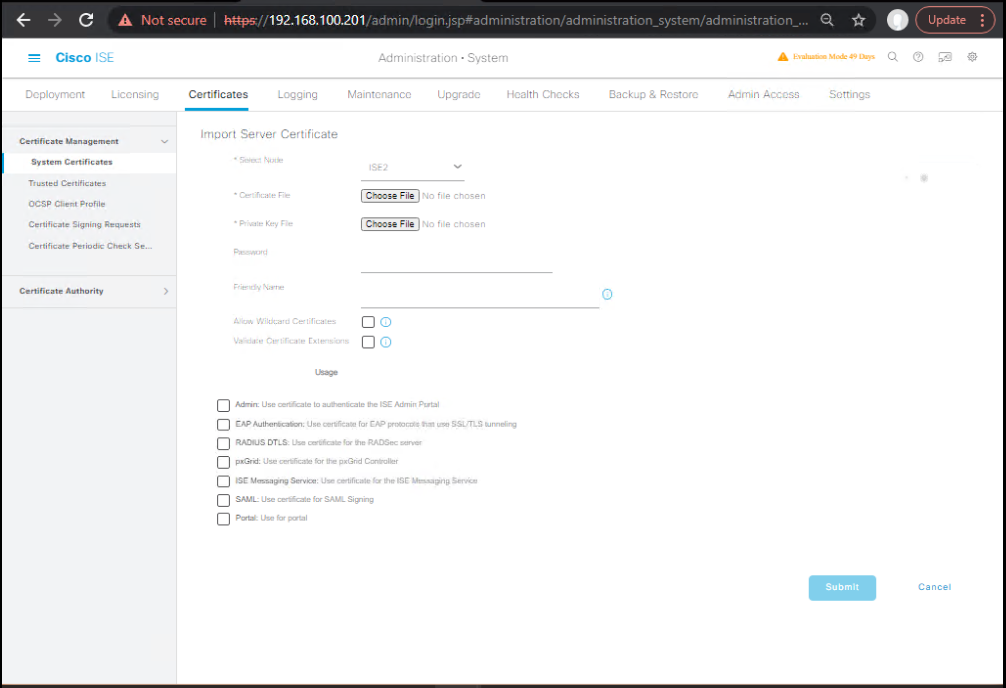
D) Bind/Import the CA-Signed Certificates
- GUI:Administration → System → Certificates → Certificate Management → System Certificates → “Import” → Bind to Existing CSR (for CA-signed).
- Upload server cert (Base64) and include chain if CA provided.
- If Admin usage will be enabled on this cert, expect ISE GUI service restart on that node when you save.
[Screenshot: System Certificates – Import/Bind] (Cisco)
Validate
- GUI: New certificate listed under the node.
- Client:
# Admin GUI chain check curl -vk https://ise-pan.lab.local/ 2>&1 | grep 'subject:' -n -A1 # EAP cert (later after usage assign) via TLS (RADSEC) or test auth
E) Assign Certificate Usage (Per Node)
- GUI:Administration → System → Certificates → Certificate Management → System Certificates → select cert → Edit → assign Usage:
- PAN: Admin (and SAML signing if IdP/SP flows).
- PSNs: EAP Authentication, Portal, RADIUS DTLS/RADSEC.
- pxGrid Node: pxGrid usage.
- Check Allow Wildcard Certificate if applicable.
[Screenshot: System Certificates – Edit Usage] (Cisco)
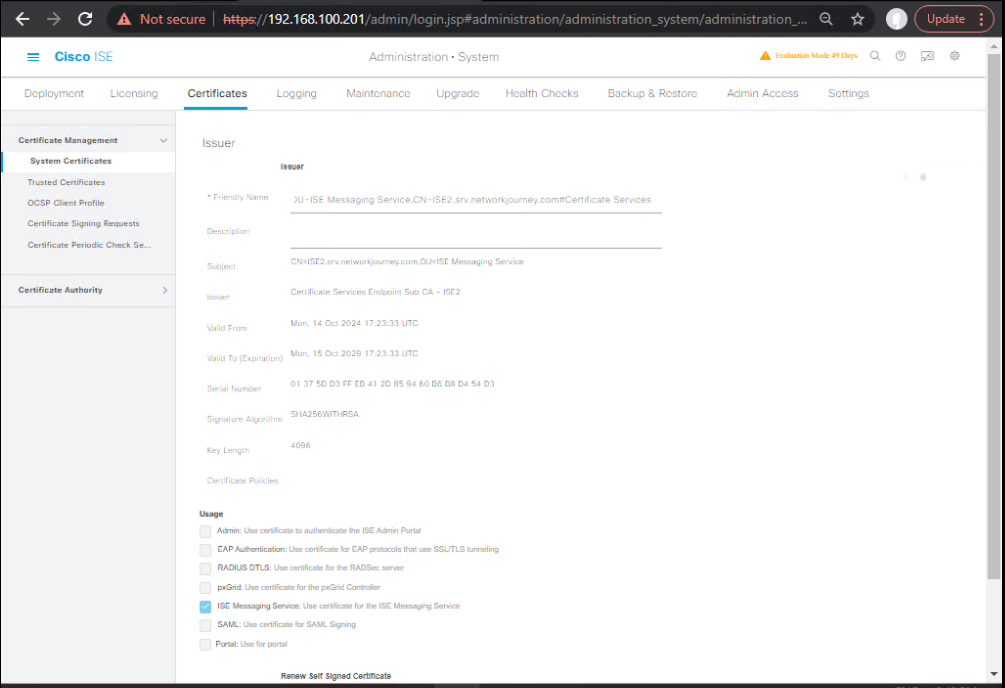
Downtime caution
- Enabling Admin Usage on a cert restarts the Admin web service on that node (brief GUI outage). Plan maintenance/drain. (Cisco)
Validate
- GUI: “Usage” column reflects assignments.
- Client:
- Admin: Browser shows green padlock to FQDN/SAN.
- Portal: Open
https://guest.lab.local:8443/portal(or PSN FQDN) → padlock valid. - EAP: Run a dot1x auth on switch/WLC test client.
- Switch:
test aaa group radius ise-user password plaintext <pw> debug dot1x events show aaa servers - WLC 9800:
test wireless aaa authentication <user> radius <server-name> show wireless client mac <mac> detail
- Switch:
F) pxGrid Certificate (if used)
- GUI: Assign/verify a cert with pxGrid usage on the pxGrid controller node.
- Administration → pxGrid Services → Client Management → Certificates (view/generate as needed).
[Screenshot: pxGrid – Certificates] (Cisco)
- Administration → pxGrid Services → Client Management → Certificates (view/generate as needed).
Validate
- GUI: pxGrid client registration successful.
- Client (FMC/DNAC): Import ISE pxGrid cert/chain as required by integration docs. (docs.defenseorchestrator.com)
G) Enable Internal CA / EST (Optional for BYOD/Onboarding)
- GUI:Administration → System → Certificates → Certificate Authority → Internal CA Settings → enable CA and EST services.
- Ensure services are Running before use.
[Screenshot: Internal CA Settings – Enable] (Cisco)
- Ensure services are Running before use.
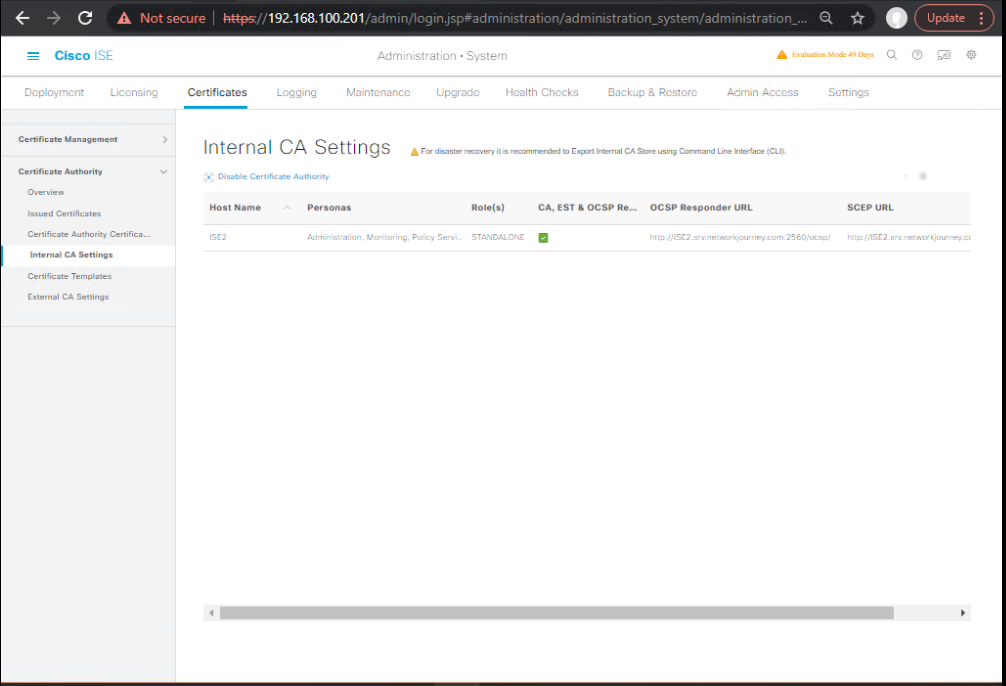
Validate
- GUI: Status shows Enabled/Running.
- Client: Check EST CA certs:
# Retrieve EST cacerts bundle curl -vk https://ise-pan.lab.local:8443/.well-known/est/cacerts(Expect Base64 PKCS7; ensure chain correct.) (Cisco)
H) Revocation (CRL/OCSP) for EAP/Admin/pxGrid
- GUI: In Trusted Certificates, edit each CA → enable CRL (HTTP/LDAP) and/or OCSP as per PKI policy.
[Screenshot: Trusted CA – Revocation Settings]
Validate
- Windows client:
certutil -url <server_cert.cer> # Verify OCSP/CRL reachability - Linux:
openssl ocsp -issuer <issuer.pem> -cert <server.pem> -url <ocsp_url> -resp_text -noverify
I) Renewal / Rotation with Zero (or Minimal) Outage
- Plan:
- Import new cert (or renew CSR) alongside old cert.
- Move Portal usage temporarily if you must delete the old portal cert.
- Assign new cert to EAP/Portal on one PSN → test → roll to other PSNs sequentially.
- Admin role last; expect GUI restart on that node.
[Screenshot: System Certificates – New vs Old side-by-side] (Cisco)
Validate
- Switch/WLC test auths green on the updated PSN before moving on.
- GUI: check Expiration column and Alarms (configure expiry notifications). (Cisco)
J) Export/Backup of System Certs and ISE Internal CA Store
- Export System Certificate (+Private Key if policy allows)
- GUI: System Certificates → select cert → Export → choose Export certificate and private key (password-protected).
[Screenshot: System Certificates – Export with Private Key] (Cisco)
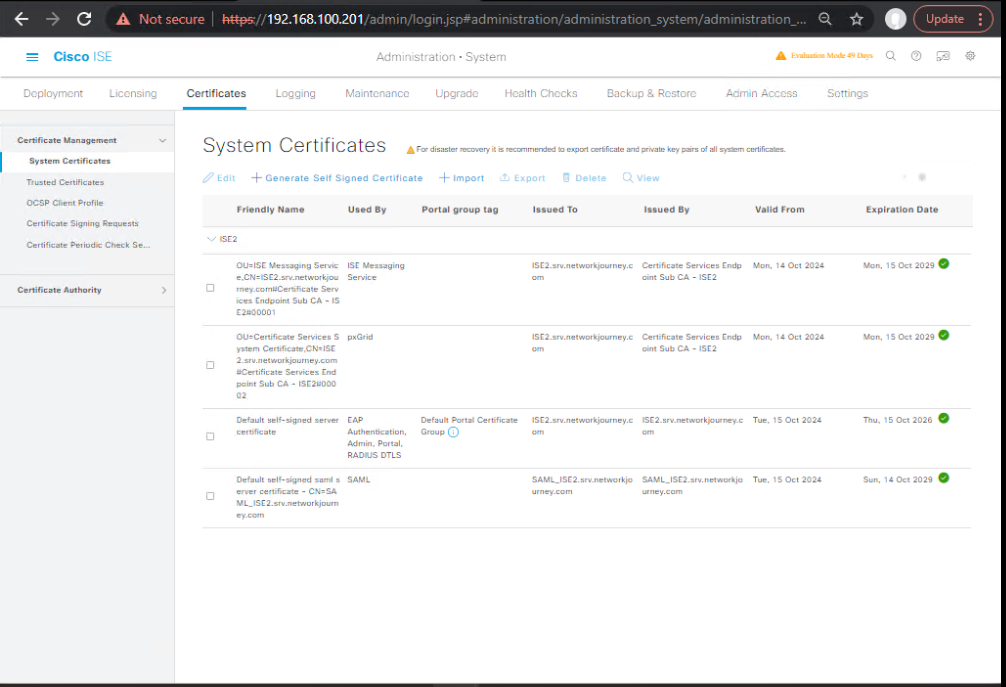
- Export/Import ISE Internal CA Store (for DR)
- CLI (PAN):
application configure ise # Select: Export Internal CA Store (option number may vary by release) # provide repository and encryption key - To restore on new PAN, run Import Internal CA Store from same menu. (Cisco)
Validate
- CLI: observe success message; confirm file present in repository.
- Note: Cisco’s CLI reference documents the Export (opt 7) / Import (opt 8) flow. (Cisco)
K) After-Action Validation Pack (Quick Run Book)
Admin GUI / Portal
- Browser padlock OK for FQDN in SAN (no CN-only). (Cisco)
- Chain resolves to Intermediate + Root, no “unknown issuer”.
- Admin change triggered expected GUI service restart (only on that node). (Cisco)
EAP-TLS
- Dot1X succeeds on test port (switch/WLC debugs clean).
- Supplicant shows server cert to expected FQDN; CRL/OCSP reachable.
pxGrid
- Client registers and subscribes; cert usage = pxGrid. (Cisco)
Internal CA / EST
- EST
cacertsreachable and contains correct chain. (Cisco)
Backups
- System cert(s) + private keys exported (where policy allows). (Cisco)
- Internal CA store exported with encryption key and stored in vault. (Cisco)
FAQs – Certificate Lifecycle Management in Cisco ISE
1. What types of certificates does Cisco ISE require?
Cisco ISE requires:
- System Certificates (for Admin GUI, EAP, pxGrid, SXP, RADIUS DTLS).
- Trusted Certificates (Root/Intermediate CAs that ISE trusts).
- SCEP enrollment certificates (if auto-renewal with Microsoft CA).
2. Do I need a unique certificate for every ISE node?
Yes. Each ISE node (PAN, PSN, MnT) should have its own CSR and certificate with the node’s FQDN as CN/SAN. Wildcards are supported but not best practice for PSNs.
3. Can I use the same certificate for multiple roles (Admin, EAP, pxGrid)?
Yes. Best practice in smaller deployments is to use one multi-purpose certificate. In larger deployments, you may want separate certs for security segmentation.
4. What happens if the EAP certificate expires?
All 802.1X authentication will fail instantly because supplicants reject expired certs.
Always configure expiry alerts and plan renewals before expiry.
5. Does Cisco ISE support wildcard certificates?
Yes, wildcard certs (e.g., *.lab.local) are supported.
However, for PSN authentication, some supplicants (like iOS) prefer exact FQDN matches, so using node-specific CN/SAN is safer.
6. How can I monitor certificate expiry in Cisco ISE?
- GUI: System → Certificates → Expiry Alerts.
- Syslog Alerts: Configure to send alerts when a certificate is nearing expiry.
- CLI:
show logging application ise-psc.log | include CERT_EXPIRE
7. How do I test if clients trust ISE’s certificate?
- From supplicant (Windows/Mac/iOS): Try 802.1X authentication → Verify certificate chain presented.
- Ensure that the Root + Intermediate CAs are in the client’s trusted store.
- CLI test from switch/WLC:
test aaa group radius ISE_PSN testuser password
8. Can ISE automatically renew certificates?
Yes, if integrated with a Microsoft CA via SCEP.
ISE will auto-generate CSRs and retrieve new certs before expiry.
Without SCEP, renewal is manual (CSR → CA → import).
9. What is the difference between “System Certificate” and “Trusted Certificate”?
- System Certificate: Certs that belong to ISE (Admin, EAP, pxGrid).
- Trusted Certificate: Root/Intermediate certs that ISE trusts for validating external servers, endpoints, and CAs.
10. Do I need to restart ISE services after binding a new certificate?
- Admin GUI certificate: Web services restart automatically.
- EAP certificate: Affects RADIUS → requires ISE application service restart on PSNs. GUI will prompt you.
- pxGrid certificate: Requires pxGrid service restart.
YouTube Link
For more in-depth Cisco ISE Mastery Training, subscribe to my YouTube channel Network Journey and join my instructor-led classes for hands-on, real-world ISE experience
Closing Notes
- Treat certificates as code: version, test, roll, and monitor expiries.
- Per-node System Certificates + global Trusted Certificates = your foundation.
- Always plan SAN, usage, and revocation up front; avoid emergency swaps.
- Keep a sealed export of critical keys (where allowed) and the Internal CA store for DR. (Cisco)
Upgrade Your Skills – Start Today
For more in-depth Cisco ISE Mastery Training, subscribe to my YouTube channel Network Journey and join my instructor-led classes.
Fast-Track to Cisco ISE Mastery Pro
- I run a focused 4-month, instructor-led CCIE Security program (labs + live troubleshooting + resume help).
- Read More: Course outline & enrollment
- What you get: weekly live labs, graded workbook submissions, Slack study group, capstone ISE deployment with cert lifecycle drills, and job-ready mock interviews.
Enroll Now & Future‑Proof Your Career
Email: info@networkjourney.com
WhatsApp / Call: +91 97395 21088

![[Day 48] Cisco ISE Mastery Training: BYOD Wireless Onboarding Overview](https://networkjourney.com/wp-content/uploads/2025/08/Day-48-Cisco-ISE-Mastery-Training-BYOD-Wireless-Onboarding-Overview.png)

