[DAY#8 PyATS Series] Parsing show version on Cisco/Arista/Paloalto/Fortigate Using pyATS [Python for Network Engineer]
Table of Contents
Introduction: Why Parsing show version Matters in Cisco Networks
When it comes to validating OS versions, uptime, model information, and license status across multiple vendors, the show version command remains a universal checkpoint. Whether you’re managing Cisco routers, Arista switches, Palo Alto firewalls, or FortiGate appliances, parsing this command automatically can give you a huge productivity and consistency boost. And that’s exactly what we’re learning today using pyATS + Genie parsers in a vendor-agnostic way.
If you’re an aspiring Python for Network Engineer professional, this blog series is your structured journey through the real-world use cases of pyATS. Today’s article teaches you how to run show version and parse it automatically across Cisco, Arista, Palo Alto, and Fortinet devices with a single click.
Topology Overview
In our lab, we’ve connected a set of network devices with management access enabled via SSH:
- Cisco IOS XE Router (R1)
- Arista EOS Switch (A1)
- Palo Alto NGFW (PA1)
- FortiGate Firewall (FG1)
We’ll validate:
- Uptime
- Software version
- Hostname
- Serial number
- Model/platform
Using one centralized Python script via pyATS, regardless of the underlying vendor syntax.
Why Vendor-Agnostic Testing Matters
In real-world enterprise and service provider networks, it’s rarely a single-vendor environment. Today, the average network includes:
- Cisco routers and switches
- Arista leaf-spine data centers
- Palo Alto firewalls at the edge
- FortiGate devices for branch security
This makes manual validation slow, repetitive, and error-prone. A change in one vendor’s OS syntax can break scripts that aren’t abstracted.
That’s where vendor-agnostic testing with pyATS and Genie shines:
- Unified framework
- Extensible CLI parsers
- Automated ping and version checks
- Simplified testing pipelines
We focus on reliability, consistency, and reusability across platforms.
Topology & Communications
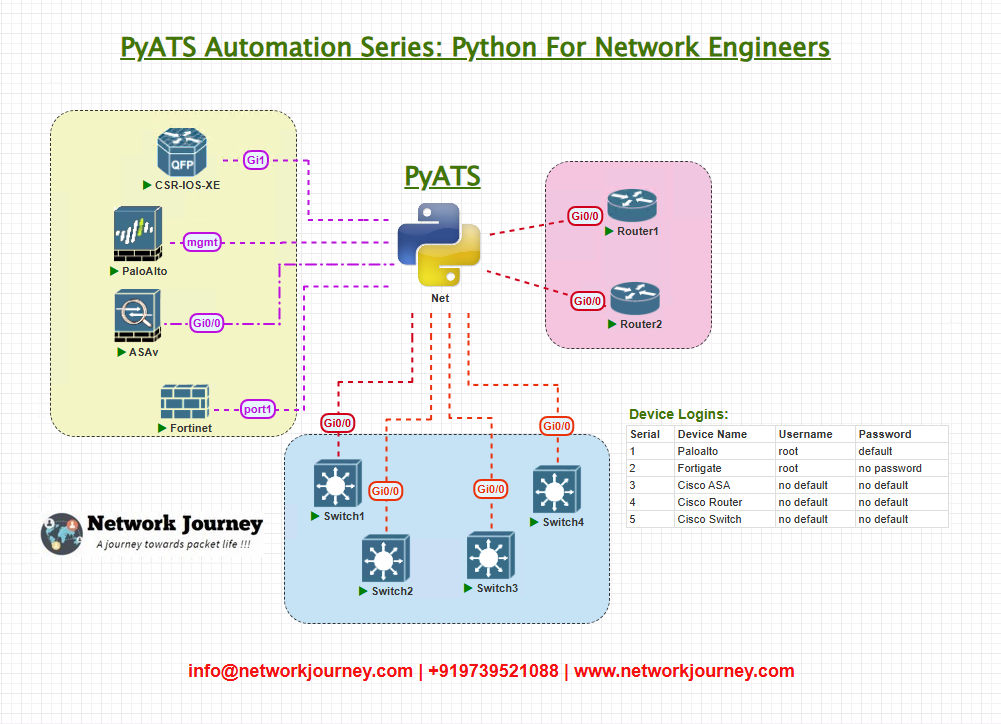
All devices are reachable over SSH with login credentials stored in the testbed.yml.
Workflow Script: parse_show_version.py
from genie.testbed import load
import json
# Load the testbed
testbed = load('testbed.yml')
# List of devices
devices = ['r1', 'a1', 'pa1', 'fg1']
# Result dictionary
results = {}
for dev_name in devices:
device = testbed.devices[dev_name]
print(f" Connecting to {device.name}...")
device.connect(init_exec_commands=[], init_config_commands=[], log_stdout=False)
# Execute and parse show version
try:
output = device.parse('show version')
results[device.name] = output
except Exception as e:
print(f" Error parsing {device.name}: {e}")
results[device.name] = str(e)
device.disconnect()
# Pretty print the parsed results
print(json.dumps(results, indent=2))
Explanation by Line
| Line | Explanation |
|---|---|
from genie.testbed import load | Imports pyATS testbed parser |
testbed = load('testbed.yml') | Loads YAML file with device credentials |
devices = [...] | List of device names defined in the testbed |
device.connect() | Establishes SSH connection |
device.parse('show version') | Runs the command and parses using Genie |
results[...] = output | Stores parsed result in dictionary |
json.dumps(...) | Converts Python dict to pretty JSON format |
testbed.yml Example
testbed:
name: show_version_lab
credentials:
default:
username: admin
password: cisco123
devices:
r1:
os: iosxe
type: router
connections:
defaults:
class: unicon.Unicon
cli:
protocol: ssh
ip: 10.1.1.1
a1:
os: eos
type: switch
connections:
defaults:
class: unicon.Unicon
cli:
protocol: ssh
ip: 10.1.1.2
pa1:
os: panos
type: firewall
connections:
defaults:
class: unicon.Unicon
cli:
protocol: ssh
ip: 10.1.1.3
fg1:
os: fortinet
type: firewall
connections:
defaults:
class: unicon.Unicon
cli:
protocol: ssh
ip: 10.1.1.4
Multi‑Vendor CLI Screenshots (Parsed Outputs)
Cisco Output
"r1": {
"version": "17.6.4",
"uptime": "1 week",
"hostname": "R1",
"serial_number": "FTX1234X1AB",
"model": "ISR4431/K9"
}
Arista Output
"a1": {
"version": "4.28.1F",
"hostname": "A1",
"modelName": "DCS-7050SX3-48YC12",
"uptime": "3 days"
}
Palo Alto Output
"pa1": {
"sw_version": "10.1.4",
"model": "PA-220",
"uptime": "5 days",
"hostname": "PA1"
}
FortiGate Output
"fg1": {
"version": "v7.0.5",
"hostname": "FG1",
"serial": "FGT60FTK12345678",
"uptime": "2 days"
}
FAQs
Q1. Can Genie parse commands from non-Cisco devices?
Yes, Genie supports other platforms via community parsers or custom Python logic. It natively supports Cisco platforms, while PAN-OS and FortiOS need either regex or custom parser extensions.
Q2. What happens if a device doesn’t support show version?
The script will catch exceptions and return an error message like command not recognized or parser not available, helping you to identify unsupported cases.
Q3. How to extend this to export results into a CSV or Excel?
You can use pandas.DataFrame.from_dict(results).to_csv("output.csv") after parsing to export structured data.
Q4. Can this be integrated into CI/CD pipelines?
Absolutely. You can integrate the script with Jenkins, GitHub Actions, or any other CI/CD tool to validate device OS versions post-deployment.
Q5. Will this work if SSH is disabled?
No. pyATS requires network access and SSH/console connectivity. You can use mock devices for dry runs in lab environments.
Q6. Is there a way to visually compare OS versions?
Yes, you can add logic to color-code versions or compare them against a baseline matrix to check for outdated firmware.
Q7. How do I create a custom parser for a vendor not natively supported?
Use genie.parsergen, regex, or extend base classes to create and register a custom parser within your pyATS environment.
Q8. Can we add ping test post validation?
Definitely! Just add device.ping(destination) after parsing to test end-to-end reachability and loopback connectivity.
YouTube Link
Watch the Complete Python for Network Engineer: Parsing show version on Cisco/Arista/Palo Alto/Fortigate (Ping Tests) Using pyATS (Vendor-Agnostic) Lab Demo & Explanation on our channel:
Join Our Training
Want to master pyATS, Python, Ansible, and API integrations for Cisco, Arista, Palo Alto, and Fortinet networks — just like what we’re building here?
Trainer Sagar Dhawan is conducting a 3-month, instructor-led program built for working professionals.
You’ll go from zero to production-ready skills with practical lab exercises, use cases, and automation pipelines.
- Starts every month
- Live instructor guidance
- Hands-on multi-vendor labs
- GitHub access to 100+ scripts
- Support group + certifications
Enroll Now & Future‑Proof Your Career
Email: info@networkjourney.com
WhatsApp / Call: +91 97395 21088
Join the program now to accelerate your Python for Network Engineer journey. Spots fill up quickly!

![EIGRP for IPv6 – Routing Smarter in the Next-Gen Network Era. [CCNP ENTERPRISE]](https://networkjourney.com/wp-content/uploads/2025/06/Why-Are-Enterprises-and-Service-Providers-Moving-to-NFV_networkjourney.png)
![[Day #66 PyATS Series] DHCP Lease Monitoring Across Vendors Using pyATS for Cisco](https://networkjourney.com/wp-content/uploads/2025/09/Day-66-PyATS-Series-DHCP-Lease-Monitoring-Across-Vendors-Using-pyATS-for-Cisco-470x274.png)
![[Day #100 PyATS Series] Production-Grade Automation Audit Reports for Management Using pyATS for Cisco [Python for Network Engineer]](https://networkjourney.com/wp-content/uploads/2025/09/Day-100-PyATS-Series-Production-Grade-Automation-Audit-Reports-for-Management-Using-pyATS-for-Cisco-Python-for-Network-Engineer-470x274.png)