DSCP vs CoS & Trust Boundary: Network Marking Demystified for Engineers [CCNP Enterprise]
If you’re anything like me, you’ve spent late nights wrestling with traffic marking and trust boundaries—wondering which to use where, and how to keep your network playing nice. It’s like juggling apples, oranges, and cherries—but don’t worry, we’ll make it smooth as butter together. Stick with me, and by the end of this guide, you’ll be marking packets like a pro and mastering QoS foundations.
Table of Contents
Theory in Brief
What is DSCP?
DSCP (Differentiated Services Code Point) is a 6‑bit field in the IP header. It allows networks to tag packets into one of 64 classes, enabling routers and switches to treat them differently based on business need—for example, marking voice packets with high priority so they don’t lag behind video or bulk transfers.
What is CoS?
CoS (Class of Service) lives in the Layer‑2 VLAN tag—just 3 bits long—allowing eight traffic priority levels. While less granular than DSCP, CoS is essential in Ethernet LANs where switches can prioritize local VLAN-traffic (like voice or management).
What is a Trust Boundary?
A Trust Boundary marks where devices decide whether to honor incoming markings or overwrite them. Imagine trusting your edge router to mark packets—but once inside the network core, switches may re-mark based on internal policy. Trust boundaries are crucial to avoid spoofed tags and preserve end-to-end QoS.
Why It Matters
Without consistent marking and trust policies, DSCP or CoS tags get lost, traffic priority is misapplied, and performance for voice/video/data gets unpredictable. By understanding these mechanisms, you ensure optimal traffic handling across your domains.
Summary / Comparison / Pros & Cons
| Feature / Topic | DSCP (Layer 3) | CoS (Layer 2) | Trust Boundary |
|---|---|---|---|
| Location in Packet | IP header (6 bits) | VLAN tag (3 bits) | Configurable hop in network |
| Priority Levels | 64 (0–63) | 8 (0–7) | Not directly priority, but trust configuration |
| Scope | End-to-end across IP network | LAN/VLAN-bound | Network/control plane-based |
| Granularity | High—supports multiple classes | Moderate—basic priority classes | N/A |
| Use Cases | Voice, video, data, critical apps | Voice VLANs, data center traffic | Preserve markings, prevent misuse |
| Pros | Flexible, standardized across routers | Fast—switch-hardware optimized | Trustworthy and secure traffic mapping |
| Cons | Overhead, must be honored across hops | Limited tags, VLAN constrained | Must plan zones, added config complexity |
Essential CLI Commands
| Task | Command Example | Purpose |
|---|---|---|
| View DSCP-to-CoS mapping | show mls qos maps dscp-cos | Displays DSCP‑to‑CoS translation table |
| View CoS trust status | show mls qos interface GigabitEthernet0/1 trust | Shows trust state on interface |
| Debug DSCP marking | debug ip dscp | Monitor DSCP decisions in real-time |
| Show VLAN CoS mapping | show mls qos maps cos-dscp | Reverse CoS→DSCP mapping table |
| View applied QoS policies | show policy-map interface GigabitEthernet0/1 | Validates applied marking and queuing |
| Check trust state across VLAN trunk | show interface GigabitEthernet0/2 switchport | Check if trunk ports trust CoS/DSCP markings |
| Explore global QoS config | `show running-config | section mls qos` |
| Clear CoS / DSCP mapping statistics | clear mls qos maps dscp-cos | Reset stats for mapping tables |
Real‑World Use Case
| Scenario | Description | Solution Deployed | Benefits |
|---|---|---|---|
| Voice VLAN to WAN | IP phones use VLAN, DSCP marking is overwritten at the router | Map CoS→DSCP at ingress, trust DSCP in core, re-mark at WAN edge | Consistent DSCP for voice end-to-end |
| Data Center East-West Traffic | Servers tagged with CoS but not honored across multiple switches | Enforce CoS trust across all access/trunk ports | LAN-wide priority and reduced voice jitter |
| Branch Router to HQ | Branch marks DSCP for voice; HQ core doesn’t trust external DSCP | Branch sets QoS, HQ device marks trusted boundary, CoS→DSCP re‑mapping | Prevented misuse, ensured consistent voice priority |
Small EVE‑NG Lab
Lab Diagram
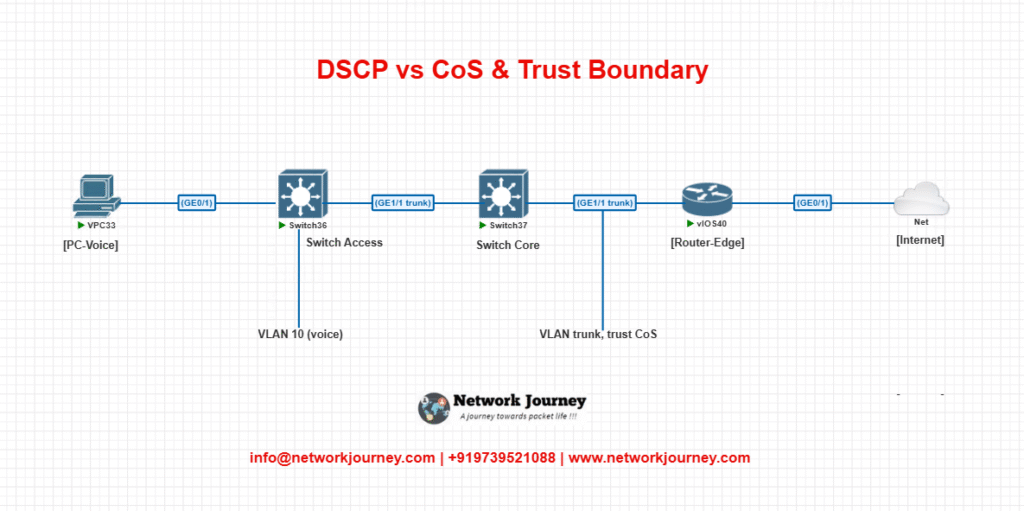
Router‑Edge CLI Snippet
! CLASSIFY/REMARK DSCP on WAN interface
class-map match-any VOICE
match dscp ef
policy-map WAN‑MARK
class VOICE
set dscp ef
interface GigabitEthernet0/1
service-policy output WAN‑MARK
Switch‑Core (trust CoS/DSCP)
interface GigabitEthernet1/1 switchport mode trunk mls qos trust cos
Switch‑Access (map CoS→DSCP on access port)
interface GigabitEthernet0/1 switchport access vlan 10 mls qos trust none mls qos cos 5 ! CoS value sent by phone mls qos queue-set 2
Troubleshooting Tips
| Issue | Possible Cause | Troubleshooting Tip |
|---|---|---|
| Edge switch dropping phone traffic | Missing CoS trust or DSCP mapping | show mls qos interface ... trust, check DSCP mappings |
| DSCP not preserved across core switches | Trust boundary misconfigured | Use show mls qos maps cos-dscp and show mls qos maps dscp-cos |
| All DSCP appear as default (0) at WAN edge | Router isn’t trusting Core’s markings | Confirm mls qos trust dscp on trunk ports |
| Voice jitter and re-marking not applied | Policy-map missing on WAN interface | Validate policy with show policy-map interface … |
| Unexpected traffic classification | ACLs or match statements misconfigured | Validate classes with debug ip dscp and ACL logic |
FAQs
1: What is the main difference between DSCP and CoS?
Answer:
DSCP (Differentiated Services Code Point) is a Layer 3 (Network Layer) marking system used in the IP header. It allows for 64 different priority levels (values from 0 to 63), making it suitable for granular classification and QoS across IP-based networks (LAN, WAN, Internet).
CoS (Class of Service), on the other hand, is a Layer 2 (Data Link Layer) marking found in the 802.1Q VLAN tag. It offers only 8 priority values (0–7) and is limited to Ethernet LAN segments.
In short:
- Use DSCP for end-to-end traffic control across IP networks.
- Use CoS for local prioritization within VLAN-based Ethernet segments.
2: Why do we need both DSCP and CoS in enterprise networks?
Answer:
Both markings serve different layers and purposes:
- CoS is critical on LAN switches (especially access and distribution layers) to prioritize traffic before it hits the router or WAN edge.
- DSCP takes over for WAN, Internet, and IP routing, ensuring traffic maintains its priority across different network domains.
By using both with proper mapping and trust boundaries, you can provide consistent QoS from the end device (like an IP phone) all the way to the cloud or remote site.
3: What is a trust boundary, and where should it be placed?
Answer:
A trust boundary defines where your network starts to accept or overwrite traffic markings (CoS or DSCP). It’s crucial for security and QoS consistency.
For example:
- At the access layer, you may trust an IP phone (let its CoS marking pass) but not a PC, which could spoof high-priority tags.
- At the WAN edge, you might re-mark traffic to enforce SLA policies regardless of upstream markings.
Best practices:
- Trust known and controlled devices (e.g., IP phones, routers).
- Place boundaries at switchports or router interfaces nearest to the traffic source.
4: Can DSCP and CoS values be converted or mapped to each other?
Answer:
Yes! Most enterprise switches and routers support DSCP↔CoS mapping using configurable tables.
- Inbound: CoS → DSCP
- Outbound: DSCP → CoS
These mappings ensure consistency across Layer 2 and Layer 3. For example:
- CoS 5 (voice) might map to DSCP 46 (EF).
- DSCP 10 (AF11) might map to CoS 1.
Use commands like show mls qos maps on Cisco devices to verify or configure these translations.
5: How do I verify if an interface is trusting DSCP or CoS?
Answer:
On Cisco IOS, use the command:
show mls qos interface <interface> trust
This will display whether the interface trusts DSCP, CoS, or none.
- If trust none, the interface will overwrite the packet markings.
- If trust dscp, it honors Layer 3 markings.
- If trust cos, it uses Layer 2 CoS values.
Adjust using commands like mls qos trust dscp or mls qos trust cos depending on your trust policy.
6: What are common DSCP values used in enterprise QoS?
Answer:
Here are commonly used DSCP values:
| DSCP Value | Decimal | Purpose |
|---|---|---|
| EF | 46 | Voice (Low Latency) |
| AF41 | 34 | Video (Streaming) |
| AF31 | 26 | Critical Data (e.g., ERP) |
| AF21 | 18 | Normal Data |
| AF11 | 10 | Bulk Data |
| CS6 | 48 | Network Control |
| Default | 0 | Best Effort |
These values help routers and switches assign bandwidth, queue priority, and drop precedence accordingly.
7: What happens if I don’t configure trust boundaries properly?
Answer:
Improper trust boundaries can result in:
- Priority misuse: End-users or apps may send traffic marked as voice or video even if it’s not, consuming unnecessary bandwidth.
- QoS inconsistency: Devices may overwrite or ignore markings mid-path, causing unpredictable performance.
- Security risk: Attackers can spoof high-priority traffic to gain advantage or disrupt networks.
Properly configured boundaries ensure only trusted devices influence QoS behavior.
8: Is DSCP marking preserved over the Internet?
Answer:
Generally, no. Most Internet Service Providers (ISPs) strip or ignore DSCP markings, treating all traffic as best effort.
However:
- MPLS or private WAN connections often honor DSCP tags if there’s an agreement in the SLA.
- Some SD-WAN solutions can encapsulate DSCP within their overlay headers and maintain QoS policies internally.
Always check with your provider and test using tools like iperf with DSCP flags.
9: How does this apply to Voice over IP (VoIP)?
Answer:
For VoIP:
- The IP phone or softphone marks traffic with CoS 5 and DSCP EF (46).
- The access switch port must trust or re-mark traffic based on policy.
- The core and WAN routers prioritize EF-marked traffic using Low Latency Queuing (LLQ).
This end-to-end consistency ensures voice packets experience low delay, jitter, and packet loss, which are critical for call quality.
10: What’s the best practice for marking and trusting in access networks?
Answer:
Best practices include:
- Trust only IP phones (e.g., via CDP or LLDP detection) on switchports.
- Do not trust PC traffic connected to phones; re-mark or leave as default.
- Use voice VLANs and assign DSCP/CoS mappings at the switch or router.
- Define clear trust boundaries at ingress and egress points (access, WAN edge).
These practices ensure only valid traffic gets priority, keeping your network secure and optimized.
YouTube Link
Watch the Complete CCNP Enterprise: DSCP vs CoS & Trust Boundary: Network Marking Demystified for Engineers Lab Demo & Explanation on our channel:
Final Takeaway
Understanding how to differentiate and implement DSCP vs CoS & Trust Boundary: Network Marking Demystified for Engineers is critical for anyone pursuing CCNP Enterprise (ENCOR) certification or working in enterprise network roles. Use this guide in your practice labs, real-world projects, and interviews to show a solid grasp of architectural planning and CLI-level configuration skills.
If you found this article helpful and want to take your skills to the next level, I invite you to join my Instructor-Led Weekend Batch for:
CCNP Enterprise to CCIE Enterprise – Covering ENCOR, ENARSI, SD-WAN, and more!
Get hands-on labs, real-world projects, and industry-grade training that strengthens your Routing & Switching foundations while preparing you for advanced certifications and job roles.
Email: info@networkjourney.com
WhatsApp / Call: +91 97395 21088
Upskill now and future-proof your networking career!
![DSCP vs CoS & Trust Boundary: Network Marking Demystified for Engineers[CCNP Enterprise]](https://networkjourney.com/wp-content/uploads/2025/07/DSCP-vs-CoS-Trust-BoundaryNetwork-Marking-Demystified-for-Engineers_networkjourney.png)
![Are Hypervisors Replacing Bare Metal in 2025? Here’s What You Should Know. [CCNP ENTERPRISE]](https://networkjourney.com/wp-content/uploads/2025/06/Are-Hypervisors-Replacing-Bare-Metal-in-2025_networkjourney.png)
![Ticket#8 - VOIP Choppy Audio – DSCP Marking Mismatch Fixed [QoS Real World] [CCNP ENTERPRISE]](https://networkjourney.com/wp-content/uploads/2025/07/nj-blog-post-Ticket-8.jpg)
![The Hidden Superpower of Routers – Master Virtual Routing & VRF Today [CCNP ENTERPRISE]](https://networkjourney.com/wp-content/uploads/2025/06/The-Hidden-Superpower-of-Routers-–-Master-Virtual-Routing_VRF-Today_networkjourney.png)