Mastering PortFast, BPDU Guard & Loop Guard: STP Protection Techniques Explained with Lab & CLI [CCNP ENTERPRISE]
If you’ve ever faced STP loops or mystery link flaps in your switching network, you know how frustrating it can be. Early in my networking career, I once spent hours chasing down a looping issue—only to find that someone plugged in a cable between two access ports. That day, I made friends with three powerful features: PortFast, BPDU Guard, and Loop Guard.
These aren’t just buzzwords—they’re lifesavers in real-world LAN environments. Whether you’re prepping for CCNP Enterprise, working on enterprise switches, or just building your EVE-NG skills, this post will give you everything you need: theory, CLI, labs, troubleshooting, and FAQs.
Table of Contents
Theory in Brief – What Are PortFast, BPDU Guard, and Loop Guard?
Let’s start by understanding the problem:
STP (Spanning Tree Protocol) prevents Layer 2 loops, but it takes 30–50 seconds for a port to move from Blocking to Forwarding. This is fine for switch-to-switch links—but unnecessary for host ports like PCs, printers, or phones.
PortFast
PortFast is a Cisco feature that tells the switch:
“This port is connected to a host, not a switch. Don’t wait—just forward traffic immediately.”
It allows the port to skip the STP listening/learning states and go directly to forwarding, reducing boot time for clients.
Danger: If you connect a switch to a PortFast-enabled port, it can cause loops.
BPDU Guard
To prevent loops caused by misconnections, we use BPDU Guard.
If any BPDU (Bridge Protocol Data Unit) is received on a PortFast port, BPDU Guard shuts down the port immediately. It’s a fail-safe for access ports.
Think of BPDU Guard as PortFast’s bodyguard
Loop Guard
Loop Guard is used on trunk or switch-to-switch links. It protects against a scenario where a port unexpectedly stops receiving BPDUs, possibly due to a unidirectional link or misconfiguration.
If BPDUs stop, the port freezes in “loop-inconsistent” state instead of moving to forwarding and creating a loop.
While BPDU Guard shuts down a port that receives BPDUs, Loop Guard protects a port that stops receiving them.
Summary – Comparison of Features
| Feature | Function | Best For | Trigger Condition | Result |
|---|---|---|---|---|
| PortFast | Skips STP states, forwards immediately | Access ports (hosts) | Port comes up | Immediate Forwarding |
| BPDU Guard | Shuts down PortFast port on BPDU receipt | Access ports (security) | BPDU received on PortFast port | Port goes into err-disabled |
| Loop Guard | Prevents port from becoming root port | Trunks/Switch links | BPDU not received unexpectedly | Port goes into loop-inconsistent |
Pros and Cons
| Feature | Pros | Cons |
|---|---|---|
| PortFast | Fast device startup, improves DHCP timing | Unsafe if a switch is accidentally connected |
| BPDU Guard | Prevents misconfigured switches from causing loops | Can cause outages if used on trunk by mistake |
| Loop Guard | Stops silent unidirectional link loops | Not supported on access ports |
Essential CLI Commands
| Task | CLI Command | Description |
|---|---|---|
| Enable PortFast on interface | spanning-tree portfast | Enables PortFast on specific interface |
| Enable BPDU Guard globally | spanning-tree portfast bpduguard default | Applies BPDU Guard to all PortFast ports |
| Enable BPDU Guard on interface | spanning-tree bpduguard enable | For manual control |
| Enable Loop Guard globally | spanning-tree loopguard default | Protects all eligible ports |
| Show STP status | show spanning-tree | View STP roles and states |
| Show err-disabled interfaces | show interface status err-disabled | Ports shut down by BPDU Guard |
| Re-enable interface manually | shutdown, no shutdown | Bring back interface after BPDU Guard |
| Monitor STP BPDUs | debug spanning-tree events | Troubleshooting events and transitions |
Real-World Use Cases
| Scenario | Feature Used | Why It’s Important |
|---|---|---|
| Laptop takes too long to get IP after plug-in | PortFast | Avoids 30-second STP delay |
| Employee connects switch to office wall port | BPDU Guard | Prevents potential loops caused by BPDUs |
| Fiber link between two switches becomes one-way | Loop Guard | Prevents loop by freezing port instead of forwarding silently |
| Office phones reboot with long STP delay | PortFast | Ensures fast DHCP and voice traffic readiness |
EVE-NG LAB – PortFast, BPDU Guard & Loop Guard Configuration
Objective:
- Apply PortFast on access ports
- Enable BPDU Guard and test shutdown on BPDU receive
- Apply Loop Guard on trunk and simulate BPDU loss
Lab Topology
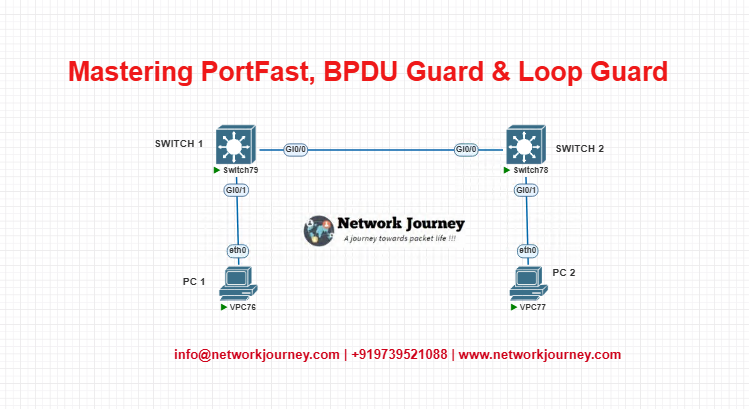
- PC1, PC2: Access Ports (PortFast + BPDU Guard)
- Switch1 <–> Switch2: Trunk with Loop Guard
Configuration
Switch1 Access Port:
interface FastEthernet0/1 switchport mode access spanning-tree portfast spanning-tree bpduguard enable
Switch2 Trunk Port:
interface FastEthernet0/24 switchport trunk encapsulation dot1q switchport mode trunk spanning-tree guard loop
Global Configuration (Optional):
spanning-tree portfast bpduguard default spanning-tree loopguard default
Test Scenarios
- Plug in a second switch to access port – verify shutdown via BPDU Guard.
- Simulate unidirectional link (disable one trunk direction) – verify Loop Guard.
- Use
show spanning-treeto monitor state changes.
Troubleshooting Tips
| Symptom | Possible Cause | Solution |
|---|---|---|
| Access port goes into err-disabled | BPDU Guard triggered | Check for switch connection; use errdisable recovery |
| STP takes 30 sec on access port | PortFast not enabled | Enable PortFast on that interface |
| Switch loop after cable addition | BPDU Guard missing on access port | Add BPDU Guard |
| Port stuck in “loop-inconsistent” | Loop Guard triggered | Investigate BPDU loss on link |
FAQ – PortFast, BPDU Guard, Loop Guard
1. What is PortFast and why is it used in STP?
Answer:
PortFast is a Cisco STP feature that immediately transitions a switch port into the forwarding state, bypassing the listening and learning states. It is used on access ports (connected to end devices like PCs or printers) to speed up connectivity. PortFast should not be enabled on trunk or uplink ports, as it can cause loops if misused.
2. What is BPDU Guard and how does it work?
Answer:
BPDU Guard is a security feature used in combination with PortFast. It monitors for Bridge Protocol Data Units (BPDUs) on PortFast-enabled interfaces. If a BPDU is received, the switch assumes a misconfiguration or attack and automatically shuts down (err-disables) the port to protect the network from loops or rogue switches.
3. When should I enable Loop Guard on a switch port?
Answer:
Loop Guard is enabled on non-designated (blocking or root) STP ports, especially trunk links between switches. It prevents a port from transitioning to the forwarding state if BPDUs are suddenly lost (e.g., due to unidirectional link failure). This stops STP failures from causing Layer 2 loops.
4. What is the difference between BPDU Guard and BPDU Filter?
Answer:
| Feature | Function | Use Case |
|---|---|---|
| BPDU Guard | Err-disables the port if a BPDU is received | Security for user/access ports |
| BPDU Filter | Suppresses sending/receiving BPDUs on an interface | Lab/testing or edge port silence |
BPDU Filter can lead to loops if misconfigured, while BPDU Guard provides proactive protection.
5. Can PortFast be used on trunk ports?
Answer:
No. PortFast is intended only for access ports connected to end devices. Enabling it on trunk ports may cause STP topology loops, as the port immediately forwards traffic without verifying the loop-free path.
However, PortFast trunk is supported on some platforms but should only be used with full understanding of its impact.
6. How do I enable PortFast and BPDU Guard globally on access ports?
Answer:
! Global configuration spanning-tree portfast default spanning-tree bpduguard default
This automatically enables PortFast and BPDU Guard on all access ports. Use this only in trusted environments where all access ports are known to connect to end devices.
7. How can I check if BPDU Guard has shut down a port?
Answer:
Use:
show interfaces status err-disabled show errdisable recovery show spanning-tree interface <interface>
These commands show err-disabled interfaces and recovery configuration. If BPDU Guard triggered shutdown, logs will show it clearly:
%SPANTREE-2-BLOCK_BPDUGUARD
8. What is the behavior of Loop Guard when BPDUs are missing?
Answer:
If BPDUs unexpectedly stop arriving on a blocking port (e.g., root port), Loop Guard moves the port into the ‘loop-inconsistent’ state, preventing it from transitioning to forwarding. When BPDUs resume, the port automatically returns to normal.
This prevents silent link failures from turning into network-wide broadcast storms.
9. Can I use PortFast, BPDU Guard, and Loop Guard together?
Answer:
Yes—but with roles:
- PortFast + BPDU Guard → On access ports
- Loop Guard → On trunk/inter-switch links
They serve different purposes and complement each other to ensure both performance (fast port-up) and protection (no loops or rogue switches).
10. What is the recommended configuration for a secure STP deployment?
Answer:
Here’s a best-practice combo:
! Access ports interface range fa0/1 - 24 switchport mode access spanning-tree portfast spanning-tree bpduguard enable ! Trunk links interface range gi0/1 - 2 switchport mode trunk spanning-tree guard loop
This configuration ensures:
- Fast boot for end devices
- Protection against rogue switches
- Loop prevention across trunks
Always test in a lab (EVE-NG or similar) before deploying in production.
YouTube Link
Watch the Complete CCNP Enterprise: Mastering PortFast, BPDU Guard & Loop Guard Lab Demo & Explanation on our channel:
Final Note
Understanding how to differentiate and implement Mastering PortFast, BPDU Guard & Loop Guard: STP Protection Techniques is critical for anyone pursuing CCNP Enterprise (ENCOR) certification or working in enterprise network roles. Use this guide in your practice labs, real-world projects, and interviews to show a solid grasp of architectural planning and CLI-level configuration skills.
If you found this article helpful and want to take your skills to the next level, I invite you to join my Instructor-Led Weekend Batch for:
CCNP Enterprise to CCIE Enterprise – Covering ENCOR, ENARSI, SD-WAN, and more!
Get hands-on labs, real-world projects, and industry-grade training that strengthens your Routing & Switching foundations while preparing you for advanced certifications and job roles.
Email: info@networkjourney.com
WhatsApp / Call: +91 97395 21088
Upskill now and future-proof your networking career!
![Mastering PortFast, BPDU Guard & Loop Guard: STP Protection Techniques Explained with Lab & CLI. [CCNP ENTERPRISE]](https://networkjourney.com/wp-content/uploads/2025/06/Mastering-PortFast-BPDU-Guard-Loop-Guard_networkjourney.png)
![Your First Step into IPv6: Address Types, Labs, CLI & Real-World Use Cases [CCNP ENTERPRISE]](https://networkjourney.com/wp-content/uploads/2025/07/nj-blog-post-IPV6.jpg)
![Redundancy Unleashed: Keeping Enterprise Networks Always-On [CCNP Enterprise]](https://networkjourney.com/wp-content/uploads/2025/06/Redundancy-Unleashed_-Keeping-Enterprise-Networks-Always-On_networkjourney.png)
![Routing Table Lookup Process – Explained with Lab & CLI [ CCNP ENTERPRISE ]_networkjourney](https://networkjourney.com/wp-content/uploads/2025/06/Routing-Table-Lookup-Process-–-Explained-with-Lab-CLI-CCNP-ENTERPRISE-.png)