Mastering SPAN and RSPAN Configuration – A Deep Dive for Real-World Network Monitoring [CCNP Enterprise]
When it comes to network troubleshooting and traffic analysis, capturing the right packets at the right place makes all the difference. How SPAN and RSPAN work behind the scenes—this post is tailor-made for you. Today, we’ll simplify a topic that often looks intimidating in textbooks but is extremely powerful when used correctly. Let’s get those packets flowing into your analyzer the right way!
Table of Contents
Theory in Brief: SPAN and RSPAN Made Simple
SPAN (Switched Port Analyzer) is Cisco’s feature for mirroring traffic from one or more ports or VLANs to another port where you can capture it using tools like Wireshark. Think of it like plugging a CCTV recorder into a mirror port to “watch” what’s going on.
SPAN operates locally, meaning both source and destination ports must exist on the same switch. It’s useful when your analyzer is nearby.
RSPAN (Remote SPAN) takes it up a notch. It extends traffic mirroring across switches by using a special VLAN. This is perfect when your monitoring device is located elsewhere in the network—like in the core or on a different floor.
Here’s how they differ:
- SPAN is confined to a single switch.
- RSPAN transports mirrored traffic across switches using a dedicated RSPAN VLAN.
These tools are crucial for detecting intrusions, verifying application performance, or analyzing bandwidth bottlenecks.
Important to know: SPAN and RSPAN are passive. They don’t interfere with live traffic, making them ideal for stealth diagnostics and audits.
SPAN vs RSPAN – Summary
| Feature | SPAN | RSPAN |
|---|---|---|
| Scope | Local (same switch) | Remote (across multiple switches) |
| Transport Mechanism | Direct port mirroring | Uses RSPAN VLAN |
| Configuration Complexity | Simple | Moderate (requires VLAN setup) |
| Analyzer Location | On the same switch | Can be on a remote switch |
| Use Case Example | Troubleshooting a nearby server | Monitoring traffic across campuses |
| Traffic Types Supported | Ingress/Egress/All | Ingress/Egress/All |
| Supported Switches | Most Cisco IOS switches | Requires RSPAN-capable switches |
| Pros | Easy to configure, low latency | Centralized analysis, flexible |
| Cons | Not scalable beyond switch | VLAN management overhead |
Essential CLI Commands – SPAN and RSPAN
| Purpose | Command Example |
|---|---|
| Configure SPAN session | monitor session 1 source interface fa0/1 monitor session 1 destination interface fa0/24 |
| Configure SPAN source as VLAN | monitor session 2 source vlan 10 monitor session 2 destination interface fa0/24 |
| Verify SPAN session | show monitor |
| Configure RSPAN VLAN | vlan 999 remote-span |
| Configure source switch for RSPAN | monitor session 1 source interface fa0/1 monitor session 1 destination remote vlan 999 |
| Configure destination switch RSPAN | monitor session 1 source remote vlan 999 monitor session 1 destination interface fa0/24 |
| Verify VLAN RSPAN status | show vlan remote-span |
| Debug traffic if needed | debug sw-vlan remote-span (use cautiously in production) |
| Check interface status | show interface status |
| Remove SPAN/RSPAN config | no monitor session 1 |
Real-World Use Case – Practical Scenarios
| Scenario | Solution Using SPAN/RSPAN |
|---|---|
| Analyzing slowness in local server | Use SPAN to mirror the switch port of the server |
| Monitor suspicious client remotely | Use RSPAN to mirror their VLAN to the security center port |
| Data Center IDS placement | RSPAN allows central monitoring from multiple switches |
| Wireshark live capture in test lab | Use SPAN on the test switch connected to analyzer laptop |
| Centralizing NetFlow or Security feeds | RSPAN directs mirrored traffic to centralized analyzers |
EVE-NG Lab Setup – SPAN & RSPAN Configuration
Lab Diagram Overview
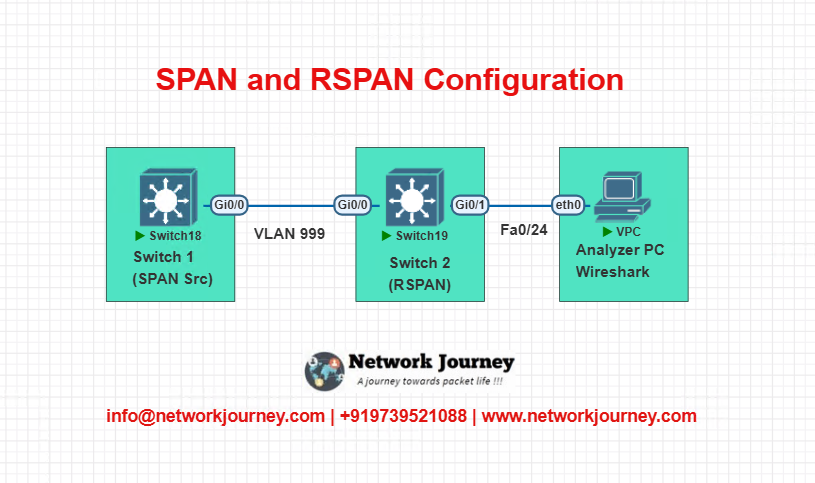
Configurations
Switch 1 – Source
vlan 999 remote-span monitor session 1 source interface fa0/1 monitor session 1 destination remote vlan 999
Switch 2 – Destination
vlan 999 remote-span monitor session 1 source remote vlan 999 monitor session 1 destination interface fa0/24
Connect Wireshark PC to Fa0/24 of Switch 2 to analyze mirrored traffic.
Troubleshooting Tips – SPAN & RSPAN
| Issue | Possible Cause | Fix Command or Action |
|---|---|---|
| No traffic seen on analyzer | Destination port misconfigured | Check show monitor |
| RSPAN VLAN not propagating | RSPAN VLAN missing on trunk | show vlan brief, show interfaces trunk |
| Duplicate packets or too much traffic | SPAN capturing both ingress and egress | Adjust source direction using monitor session |
| Analyzer port not receiving packets | Destination port shutdown | no shutdown on destination interface |
| VLAN not configured as RSPAN | VLAN missing remote-span keyword | vlan <id> followed by remote-span |
| Performance drop on destination port | High traffic rate | Use filters or capture smaller segments |
| Monitor session limit exceeded | Too many active sessions | Remove old ones using no monitor session |
FAQs – SPAN and RSPAN
1. What is the main purpose of SPAN in a Cisco network?
Answer:
SPAN (Switched Port Analyzer) is primarily used to monitor network traffic for troubleshooting or analysis purposes. It allows the switch to copy traffic from one or more source ports or VLANs to a destination port. This destination port is usually connected to a packet analyzer (like Wireshark) to inspect live traffic flows without interrupting the network’s operation.
2. How does RSPAN differ from SPAN, and when should I use it?
Answer:
RSPAN (Remote SPAN) is an extension of SPAN that allows the mirrored traffic to be sent across switches using a dedicated RSPAN VLAN. Unlike SPAN, which is local to a switch, RSPAN is useful when your monitoring tool is located on a different switch in the network. It’s ideal for large campuses or centralized monitoring scenarios.
3. Can I monitor both ingress and egress traffic using SPAN or RSPAN?
Answer:
Yes. By default, both SPAN and RSPAN mirror ingress (incoming) and egress (outgoing) traffic. However, you can control this behavior. Cisco allows you to specify the direction as rx (receive/ingress), tx (transmit/egress), or both when configuring the session.
Example:
monitor session 1 source interface fa0/1 rx
4. Is there a limit to how many SPAN sessions I can configure on a switch?
Answer:
Yes, the number of SPAN sessions depends on the switch model and IOS version. Most Cisco Catalyst switches support up to 2 active SPAN sessions, while high-end models (like 6500 or 9400) may support more. Always refer to the hardware documentation for exact limits.
5. Can the destination port in a SPAN session transmit regular traffic?
Answer:
No. A SPAN destination port, also known as a monitoring port, cannot transmit any traffic except for the mirrored traffic it receives. It essentially becomes read-only and cannot participate in regular switching or forwarding functions while it’s part of a SPAN session.
6. How do I know if RSPAN is supported on my switch?
Answer:
You can verify RSPAN support by checking your switch’s IOS version and model documentation. RSPAN requires:
- VLANs with the
remote-spankeyword enabled - Trunk links between switches
- The ability to configure
monitor sessionwithremote vlanoptions
Run the command:
show monitor
…to check if remote vlan is recognized as a valid destination.
7. Will using SPAN or RSPAN impact network performance?
Answer:
In general, SPAN and RSPAN have minimal performance impact because they are passive. However, under heavy traffic loads, especially when mirroring multiple ports or VLANs, SPAN can consume switch CPU and memory, leading to performance degradation. It’s best to avoid running large SPAN sessions continuously in production.
8. Can I use SPAN to monitor trunk ports or VLANs?
Answer:
Yes. You can configure SPAN to monitor trunk ports or entire VLANs. For VLAN-based mirroring:
monitor session 2 source vlan 10
This is especially useful when you want to monitor all devices within a VLAN without specifying individual interfaces.
9. How do I stop or remove a SPAN or RSPAN session?
Answer:
To remove a monitoring session, use the no keyword:
no monitor session 1
This command deletes the configuration for that session, stopping all traffic mirroring associated with it.
10. What tools can I use to analyze SPAN or RSPAN captured traffic?
Answer:
The most common tool is Wireshark, which is open-source and highly effective for packet analysis. Other tools include:
- Cisco Stealthwatch
- SolarWinds Packet Sniffer
- Snort or Suricata (for IDS use cases)
- tcpdump (Linux CLI-based)
The analyzer must be connected to the SPAN destination port or to the switch carrying the RSPAN VLAN and configured to listen promiscuously.
YouTube Video Link
Final Note
Understanding how to differentiate and implement Mastering SPAN and RSPAN Configuration – A Deep Dive for Real-World Network Monitoring is critical for anyone pursuing CCNP Enterprise (ENCOR) certification or working in enterprise network roles. Use this guide in your practice labs, real-world projects, and interviews to show a solid grasp of architectural planning and CLI-level configuration skills.
If you found this article helpful and want to take your skills to the next level, I invite you to join my Instructor-Led Weekend Batch for:
CCNP Enterprise to CCIE Enterprise – Covering ENCOR, ENARSI, SD-WAN, and more!
Get hands-on labs, real-world projects, and industry-grade training that strengthens your Routing & Switching foundations while preparing you for advanced certifications and job roles.
Email: info@networkjourney.com
WhatsApp / Call: +91 97395 21088
Upskill now and future-proof your networking career!
![Mastering SPAN and RSPAN Configuration – A Deep Dive for Real-World Network Monitoring [CCNP Enterprise]](https://networkjourney.com/wp-content/uploads/2025/07/Mastering-SPAN-and-RSPAN-Configuration-–-A-Deep-Dive-for-Real-World-Network-Monitoring_networkjourney.png)
![[Day #94 PyATS Series] Validate IPv6 Neighbor Discovery Tables Using pyATS for Cisco [Python for Network Engineer]](https://networkjourney.com/wp-content/uploads/2025/09/Day-94-PyATS-Series-Validate-IPv6-Neighbor-Discovery-Tables-Using-pyATS-for-Cisco-Python-for-Network-Engineer-470x274.png)
![Route Redistribution with Tagging – Mastering Controlled Routing Across Protocols [ CCNP ENTERPRISE ]_networkjourney](https://networkjourney.com/wp-content/uploads/2025/06/Route-Redistribution-with-Tagging-–-Mastering-Controlled-Routing-Across-Protocols-CCNP-ENTERPRISE-.png)
![Ticket#8 - VOIP Choppy Audio – DSCP Marking Mismatch Fixed [QoS Real World] [CCNP ENTERPRISE]](https://networkjourney.com/wp-content/uploads/2025/07/nj-blog-post-Ticket-8.jpg)