Troubleshooting STP Flapping: Fix Network Instability with Confidence [CCNP Enterprise]
Today I want to walk you through a problem that many of us face in real-world environments—STP flapping. If you’ve ever dealt with mysterious connectivity drops, unstable MAC tables, or users yelling, “The network is slow!” with no obvious root cause—there’s a good chance Spanning Tree Protocol is silently recalculating in the background. STP is a lifesaver when it works, but when it starts flapping, it can wreak havoc across your network.
In this guide, I’ll break down what STP flapping is, what causes it, how to detect it quickly, and most importantly—how to fix it using proven techniques and Cisco CLI. I’ve also included a hands-on EVE-NG lab, real-world use cases, FAQs, and troubleshooting tips from the trenches.
Table of Contents
Theory in Brief – What Is STP Flapping?
Spanning Tree Protocol (STP) prevents Layer 2 loops in Ethernet networks by electing a root bridge and placing redundant ports in blocking or forwarding state. It constantly monitors the network topology and recalculates paths when changes occur—this is called convergence.
Now, STP flapping refers to a condition where STP frequently changes topology—often due to unstable links, incorrect configuration, or network loops. These frequent recalculations cause devices to constantly flush their MAC address tables, resulting in traffic drops, slow response times, and overall instability.
Why Does It Matter?
- Every time STP recalculates, there is a short disruption.
- End hosts lose connections momentarily.
- VoIP, video, and critical apps feel the impact the most.
- Broadcasts may flood the network if loops occur.
Detecting and stopping STP flapping is critical to ensure network stability and performance.
Summary / Pros and Cons
| Aspect | Details |
|---|---|
| Protocol | Spanning Tree Protocol (802.1D, 802.1w, 802.1s) |
| Purpose | Prevent Layer 2 loops, maintain network redundancy |
| STP Flapping Definition | Frequent STP topology recalculations due to instability |
| Main Causes | Faulty links, loops, misconfigured STP, BPDU issues |
| Impact | MAC flushes, dropped packets, voice/video degradation |
Pros of STP
- Prevents Layer 2 loops
- Automatically reconverges on link failure
- Supports redundant paths
- Available in multiple flavors (RSTP, MSTP)
Cons When Flapping
- High CPU usage on switches
- Random disconnections for users
- MAC address table instability
- Difficult to troubleshoot without visibility
Essential CLI Commands for STP Flapping
| Task | Command |
|---|---|
| Show STP summary | show spanning-tree summary |
| Show STP per VLAN | show spanning-tree vlan <vlan-id> |
| Display port roles/states | show spanning-tree interface <interface> |
| View topology change count | `show spanning-tree detail |
| See root bridge information | show spanning-tree root |
| Enable STP debugging | debug spanning-tree events |
| Disable all debugging | undebug all |
| Interface status check | show interfaces status |
| View MAC address movement | `show mac address-table |
| Check log for TCN events | `show logging |
Real-World Use Case – Where STP Flapping Strikes
| Scenario | How STP Flapping Affects It |
|---|---|
| An access switch has a faulty uplink | Link intermittently bounces, causing TCNs and MAC flushes |
| Users randomly disconnect in one VLAN | STP reconvergence flushes their gateway MACs during every topology change |
| Rogue switch plugged into office port | Forms loop, causes constant STP recalculations without BPDU Guard |
| Server traffic drops periodically | STP flapping resets forwarding path to server’s MAC intermittently |
| VoIP call quality degraded | STP flapping causes jitter, packet loss due to momentary interruptions |
EVE-NG LAB – STP Flapping Simulation & Fix
LAB TOPOLOGY
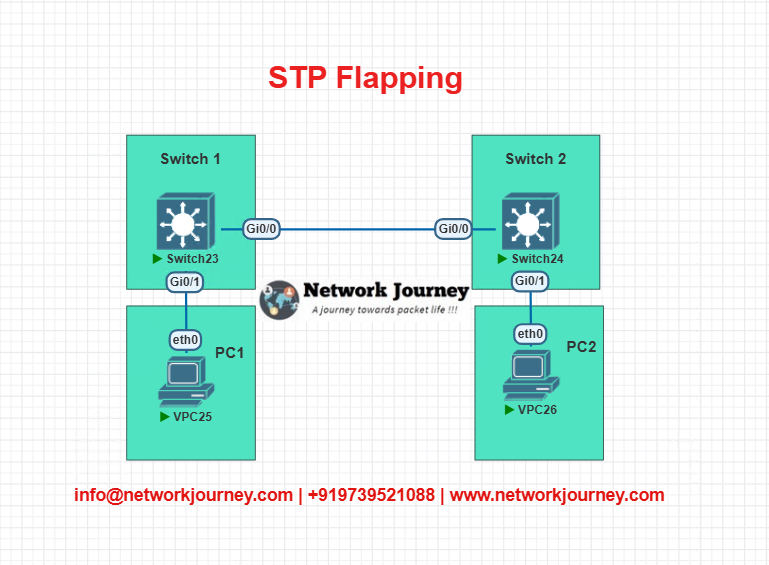
- Switch1 G0/1 <-> Switch2 G0/1 (Trunk)
- PC1 on Switch1 (Access VLAN 10)
- PC2 on Switch2 (Access VLAN 10)
Step-by-Step Configuration
On Switch1:
interface range g0/1, g0/2 switchport mode trunk spanning-tree portfast spanning-tree bpduguard enable
On Switch2:
interface range g0/1, g0/2 switchport mode trunk spanning-tree portfast spanning-tree bpduguard enable
Simulate STP Flapping
- Disconnect and reconnect G0/1 between Switch1 and Switch2.
- Or plug in a Layer 2 loop using a loopback cable.
- Use
show spanning-tree summaryanddebug spanning-tree eventsto watch TCNs.
Troubleshooting Tips Table
| Symptom | Possible Cause | Action to Fix |
|---|---|---|
| High topology change count | Unstable port or frequent disconnects | Use show spanning-tree detail, replace faulty cable |
| Users disconnected during file transfers | TCN causing MAC flushes | Enable portfast on access ports |
| Logs show constant TCNs | Loop or misconfigured trunk | Check trunking, disable unused ports |
| MAC address keeps bouncing between ports | Network loop | Enable BPDU Guard, use port security |
| Both switches claim to be root bridge | No priority set | Use spanning-tree vlan <id> priority 0 on root bridge |
FAQs About STP Flapping
1. What is STP flapping and why does it matter?
Answer:
STP flapping occurs when the Spanning Tree Protocol continuously recalculates the network topology due to frequent link changes or instabilities. This constant state of change causes MAC address table flushes, port state transitions, and ultimately intermittent traffic drops. In a production network, even brief outages can severely impact VoIP calls, video streams, and application performance, making STP flapping a critical issue to troubleshoot and resolve.
2. What are the most common causes of STP flapping?
Answer:
The most frequent triggers of STP flapping include:
- Faulty cables or ports (physical instability)
- Unstable trunk links
- Switch loops from unmanaged devices
- Incorrect or missing PortFast/BPDU Guard settings
- Layer 1 or Layer 2 broadcast storms
These can be exacerbated by having no root bridge priority configured or a rogue switch accidentally introduced into the network.
3. How can I quickly check if STP flapping is happening on a Cisco switch?
Answer:
Use this command to check for frequent topology changes:
show spanning-tree summary
If you see a high count under “Number of topology changes”, it likely indicates STP flapping. You can also use:
show spanning-tree detail | include changed
This tells you which interfaces experienced recent STP events.
4. How does STP flapping impact end-user experience?
Answer:
STP flapping results in:
- Temporary network blackouts
- VoIP jitter or dropped calls
- Slow access to file servers
- Session drops for critical apps
- Video buffering or quality issues
Because the network re-learns MAC addresses during each STP recalculation, even devices on the same VLAN may temporarily lose connectivity.
5. What role does PortFast play in preventing STP flapping?
Answer:
PortFast tells the switch that a port is directly connected to an end device (like a PC or printer), not another switch. When enabled, the port skips STP listening/learning states and immediately transitions to forwarding. This avoids triggering unnecessary topology changes during device reboots or reconnections.
Configure it like this:
interface g0/2 spanning-tree portfast
6. What is BPDU Guard, and how does it help reduce STP flapping?
Answer:
BPDU Guard disables a port if it receives a Bridge Protocol Data Unit (BPDU)—a telltale sign that a switch (or looping device) has been plugged into an access port. This prevents accidental loops and rogue switch participation in STP.
Use this command:
interface g0/2 spanning-tree bpduguard enable
When combined with PortFast, BPDU Guard significantly reduces STP-related instability.
7. How can I simulate and detect STP flapping in a lab?
Answer:
In an EVE-NG lab or physical setup:
- Connect two switches with a trunk.
- Create a loop by bridging an unused access port back to a trunk.
- Observe STP logs and topology changes using:
debug spanning-tree events
and
show spanning-tree vlan 10
You’ll see rapid changes in root port or designated port roles, confirming flapping.
8. What should I do if STP flapping is happening on trunk ports?
Answer:
If trunk links are unstable:
- Check for interface errors using
show interfaces - Ensure native VLANs match on both ends
- Replace or test cables
- Use Loop Guard to prevent port role inconsistencies:
spanning-tree guard loop
Also verify the trunk mode:
show interfaces trunk
9. Should I manually configure the root bridge to prevent STP flapping?
Answer:
Yes, it’s a best practice to manually configure the root bridge to avoid instability caused by dynamic root elections. Set a lower bridge priority on your core/distribution switch:
spanning-tree vlan 10 priority 0
This ensures the same switch always remains root unless it fails, which helps stabilize the STP topology.
10. Can STP flapping be caused by external (non-Cisco) devices?
Answer:
Absolutely. Devices like home routers, unmanaged switches, or Wi-Fi bridges that inject unexpected BPDUs or create loops can easily trigger flapping. These are especially dangerous when plugged into access ports without BPDU Guard. Always restrict device access and use port security features.
YouTube Link
Watch the Complete CCNP Enterprise: Troubleshooting STP Flapping: Fix Network Instability with Confidence Lab Demo & Explanation on our channel:
Final Note
Understanding how to differentiate and implement Troubleshooting STP Flapping: Fix Network Instability with Confidence in Modern Networks is critical for anyone pursuing CCNP Enterprise (ENCOR) certification or working in enterprise network roles. Use this guide in your practice labs, real-world projects, and interviews to show a solid grasp of architectural planning and CLI-level configuration skills.
If you found this article helpful and want to take your skills to the next level, I invite you to join my Instructor-Led Weekend Batch for:
CCNP Enterprise to CCIE Enterprise – Covering ENCOR, ENARSI, SD-WAN, and more!
Get hands-on labs, real-world projects, and industry-grade training that strengthens your Routing & Switching foundations while preparing you for advanced certifications and job roles.
Email: info@networkjourney.com
WhatsApp / Call: +91 97395 21088
Upskill now and future-proof your networking career!
![Troubleshooting STP Flapping: Fix Network Instability with Confidence [CCNP Enterprise]](https://networkjourney.com/wp-content/uploads/2025/07/Troubleshooting-STP-Flapping-Fix-Network-Instability-with-Confidence_networkjourney-1.png)
![SD-WAN vs Traditional WAN: Complete Comparison, CLI Lab & Real Use Cases [2025 Guide]. [CCNP ENTERPRISE]](https://networkjourney.com/wp-content/uploads/2025/06/SD-WAN-vs-Traditional-WAN_-Complete-Comparison_networkjourney.png)
![The Hidden Superpower of Routers – Master Virtual Routing & VRF Today [CCNP ENTERPRISE]](https://networkjourney.com/wp-content/uploads/2025/06/The-Hidden-Superpower-of-Routers-–-Master-Virtual-Routing_VRF-Today_networkjourney.png)
![Cisco Debug vs Show Commands: Deep Dive for Network Troubleshooting [CCNP Enterprise]](https://networkjourney.com/wp-content/uploads/2025/07/Cisco-Debug-vs-Show-Commands-Deep-Dive-for-Network-Troubleshootingnetworkjourney.png)