The Hidden Superpower of Routers – Master Virtual Routing & VRF Today [CCNP ENTERPRISE]
I know how confusing “virtual routing” can sound when you’re just starting to dive deep into enterprise network architecture. Believe me, I’ve been there. When I first stumbled upon concepts like VRF and virtual routers, I thought, “Is this just another fancy way to complicate routing?” But once you break it down, it’s not only logical — it’s super powerful.
In today’s post, we’re not just learning about Virtual Routing — we’re mastering it. From understanding the basic theory to setting up a mini lab on EVE-NG, I’ll walk you through everything you need. So grab your notepad, spin up your lab, and let’s get our hands virtually dirty!
Table of Contents
Theory in Brief: What is Virtual Routing?
Concept Overview
Virtual Routing allows you to run multiple separate routing tables on the same physical router — like having multiple logical routers inside one device. Each instance is isolated, so routes from one table don’t interfere with another. This is especially useful in multi-tenant environments like service provider networks or enterprise segments.
Key Element: VRF (Virtual Routing and Forwarding)
The most popular implementation of virtual routing is VRF in Cisco and other vendor environments. Each VRF instance works like an isolated “mini-router” within the same hardware. It helps avoid overlapping IP address conflicts and gives strict traffic separation.
Where is it Used?
Think of a service provider serving 100 customers. They can’t spin up 100 routers, so they use VRFs to logically separate customer networks while maintaining just one physical router. Same goes for large enterprises — dev, QA, and production can all live peacefully on one router, thanks to VRFs.
Simple Analogy
Imagine a single hotel building (your router) having multiple rooms (VRFs). Each guest (routing table) in each room operates independently and has no idea what the other is doing. That’s the magic of virtualization!
VRF vs Traditional Routing
| Feature | Traditional Routing | Virtual Routing (VRF) |
|---|---|---|
| Routing Table | Single global table | Multiple isolated tables |
| IP Address Overlap Support | Not allowed | Allowed per VRF |
| Security Isolation | Limited | High |
| Used In | Small setups | Enterprise, Data Centers, SPs |
| Configuration Complexity | Simple | Moderate |
| Hardware Resources | Shared | Partitioned logically |
Pros and Cons of Virtual Routing
| Pros | Cons |
|---|---|
| Enables multi-tenant support | Requires more complex configuration |
| Allows overlapping IP ranges | Consumes more memory/CPU on the router |
| Enhances routing security via isolation | Debugging can be harder across VRFs |
| Great for managed services and cloud networks | Needs understanding of route leaking |
Essential CLI Commands
Here are some must-know commands when working with virtual routing, particularly VRFs on Cisco IOS:
| Task | Command Example | Notes |
|---|---|---|
| Create VRF | ip vrf CUSTOMER1 | Older IOS versions |
| Assign VRF to Interface | interface Gig0/0ip vrf forwarding CUSTOMER1 | Binds VRF to interface |
| Add IP Address in VRF | ip address 10.1.1.1 255.255.255.0 | Applied inside VRF-enabled interface |
| Add Routes to VRF | ip route vrf CUSTOMER1 0.0.0.0 0.0.0.0 10.1.1.2 | VRF-specific static route |
| View VRF Routing Table | show ip route vrf CUSTOMER1 | Shows per-VRF routing |
| Ping inside VRF | ping vrf CUSTOMER1 10.1.1.2 | Useful for testing |
| Show Interfaces in VRF | show ip interface brief vrf CUSTOMER1 | Interface-to-VRF mapping |
| Remove VRF | no ip vrf CUSTOMER1 | Clean up unused VRF |
Real-World Use Cases
| Scenario | Description |
|---|---|
| ISP Network | Each customer gets their own VRF instance for full routing control |
| Data Center Segmentation | Separate VRFs for production, dev, QA environments |
| MPLS VPN | Core of the MPLS Layer 3 VPN model relies on VRF separation |
| Hosting Environment | Cloud providers use VRFs to isolate tenant networks |
| Multi-VRF CE (Customer Edge) | Sites using multiple service providers for redundancy |
Small EVE-NG Lab Setup
Lab Topology Diagram
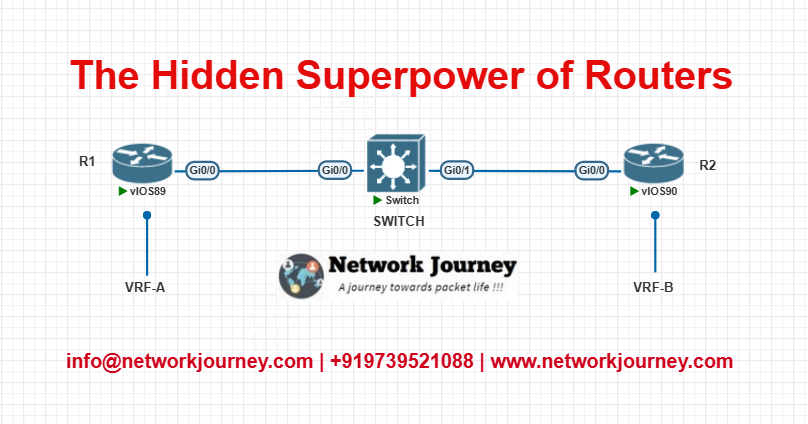
- R1 and R2 are two customer routers connected to a common SW (switch or core router).
- Both use the same subnet
10.1.1.0/24, but assigned in different VRFs.
Configuration Example on Core Router (SW)
ip vrf CUSTOMER1
rd 100:1
!
ip vrf CUSTOMER2
rd 200:1
!
interface Gig0/1
description Link to R1
ip vrf forwarding CUSTOMER1
ip address 10.1.1.1 255.255.255.0
!
interface Gig0/2
description Link to R2
ip vrf forwarding CUSTOMER2
ip address 10.1.1.1 255.255.255.0
!
ip route vrf CUSTOMER1 0.0.0.0 0.0.0.0 10.1.1.2
ip route vrf CUSTOMER2 0.0.0.0 0.0.0.0 10.1.1.2
Configuration on Customer Routers
# R1 (Customer1 side)
interface Gig0/0
ip address 10.1.1.2 255.255.255.0
!
ip route 0.0.0.0 0.0.0.0 10.1.1.1
# R2 (Customer2 side)
interface Gig0/0
ip address 10.1.1.2 255.255.255.0
!
ip route 0.0.0.0 0.0.0.0 10.1.1.1
Even though both use the same subnet and IP, their traffic stays isolated!
Troubleshooting Tips
| Symptom | Cause | Fix |
|---|---|---|
| Can’t ping between routers | They’re in different VRFs | That’s expected behavior unless you do route leaking |
| VRF doesn’t appear in show commands | VRF not bound to interface | Check ip vrf forwarding configuration |
| No route in VRF table | Static or dynamic route missing | Add routes using ip route vrf ... |
| Packet drops after interface config | Interface got reset when VRF assigned | Reconfigure IP address post VRF binding |
| Ping works without VRF but not with | Forgetting ping vrf prefix | Always use ping vrf NAME x.x.x.x |
Frequently Asked Questions (FAQs)
1. What is the main advantage of using VRF?
Answer:
The primary benefit of VRF is that it allows for complete route and traffic isolation on the same physical router. This enables organizations to create multi-tenant environments or separate customer traffic in a service provider setup without the need for additional hardware. Each VRF instance maintains its own independent routing table, ensuring that routes in one VRF are not visible to another by default — offering both security and operational segmentation.
2. Can I use overlapping IPs with VRF?
Answer:
Yes, one of the key capabilities of VRF is the ability to safely use overlapping IP address spaces across different VRFs. Since each VRF has its own dedicated routing table, the same IP prefix (e.g., 192.168.1.0/24) can exist in multiple VRFs without causing any conflict. This is extremely useful in:
- Multi-tenant data centers
- MPLS VPNs
- Customer segmentation scenarios
3. Is VRF available only on Cisco devices?
Answer:
No, VRF is a standard networking feature supported by many vendors. While Cisco popularized it under the name VRF, other vendors offer similar concepts under different names:
- Juniper: Virtual Routing Instances
- Nokia/Alcatel-Lucent: Virtual Routing and Forwarding
- Fortinet: Virtual Domains (VDOMs)
- Arista / Huawei / Palo Alto: VRFs or Virtual Routers
The implementation details may vary, but the core principle of Layer 3 separation remains the same.
4. What’s the difference between VRF and VLAN?
Answer:
The key difference lies in the OSI layer at which each operates:
- VLAN operates at Layer 2, isolating broadcast domains.
- VRF operates at Layer 3, isolating routing tables and traffic between different logical networks.
While VLANs separate traffic based on switch ports and broadcast domains, VRFs allow IP routing separation. In many designs, VLANs are used together with VRFs — especially on SVIs (Switched Virtual Interfaces).
5. Do I need separate interfaces for each VRF?
Answer:
Not necessarily. While you can dedicate physical interfaces to each VRF, it’s more common (and efficient) to use:
- Sub-interfaces (e.g., Gi0/0.10 for VRF-A, Gi0/0.20 for VRF-B)
- Logical interfaces or SVIs
This saves physical ports and provides greater scalability in environments where multiple VRFs need to coexist on a single router or switch.
6. What is Route Leaking in VRF?
Answer:
Route leaking refers to the process of selectively sharing routes between VRFs to enable controlled communication. By default, VRFs are isolated, but sometimes inter-VRF routing is required — for example, when different business units need to access shared services like DNS or Internet.
There are multiple ways to implement route leaking:
- Static routes
- Route-target import/export (in MPLS VPNs)
- VRF-lite route redistribution using dynamic protocols like BGP or OSPF
7. Can I run dynamic routing protocols in VRF?
Answer:
Yes, most modern dynamic routing protocols support VRF instances. You can run separate routing processes or VRF instances of:
- OSPF (using process-id or VRF-aware configuration)
- BGP (multi-instance with separate BGP neighbors per VRF)
- EIGRP, RIP, and IS-IS (depending on platform support)
Each routing protocol maintains routes independently for each VRF, enabling full routing functionality within the isolated environment.
8. How do I verify if traffic stays inside a VRF?
Answer:
You can use the following commands and methods to verify traffic behavior in VRFs:
show ip route vrf <VRF-NAME>– Displays the routing table for a specific VRF.ping vrf <VRF-NAME> <destination IP>– Tests reachability from within a VRF.traceroute vrf <VRF-NAME> <destination IP>– Traces packet path in a VRF.- Packet captures and interface monitoring tools (e.g., NetFlow or SPAN) can also be used to track traffic per VRF.
9. Are VRFs secure enough for production?
Answer:
Absolutely. VRFs are widely used in production-grade environments such as:
- Service provider MPLS networks
- Enterprise WAN segmentation
- Government and military networks
They offer robust logical segmentation and when combined with ACLs, firewalls, and encryption, they provide high levels of security, isolation, and compliance.
10. Is there a performance hit using multiple VRFs?
Answer:
Yes, each VRF instance adds some overhead in terms of:
- CPU usage (especially with multiple routing protocols)
- Memory consumption (each VRF needs its own routing table and interfaces)
However, this impact is minimal on modern routers and switches, especially those designed for multi-tenant or ISP use. Best practices include:
Avoiding excessive VRFs on low-end hardware
Monitoring control plane resource usage
YouTube Video
Watch the Complete CCNP Enterprise: The Hidden Superpower of Routers – Master Virtual Routing & VRF Today Lab Demo & Explanation on our channel:
Final Note
Understanding how to differentiate and implement The Hidden Superpower of Routers – Master Virtual Routing & VRF Today in Modern Networks is critical for anyone pursuing CCNP Enterprise (ENCOR) certification or working in enterprise network roles. Use this guide in your practice labs, real-world projects, and interviews to show a solid grasp of architectural planning and CLI-level configuration skills.
If you found this article helpful and want to take your skills to the next level, I invite you to join my Instructor-Led Weekend Batch for:
CCNP Enterprise to CCIE Enterprise – Covering ENCOR, ENARSI, SD-WAN, and more!
Get hands-on labs, real-world projects, and industry-grade training that strengthens your Routing & Switching foundations while preparing you for advanced certifications and job roles.
Email: info@networkjourney.com
WhatsApp / Call: +91 97395 21088
Upskill now and future-proof your networking career!
![The Hidden Superpower of Routers – Master Virtual Routing & VRF Today [CCNP ENTERPRISE]](https://networkjourney.com/wp-content/uploads/2025/06/The-Hidden-Superpower-of-Routers-–-Master-Virtual-Routing_VRF-Today_networkjourney.png)

![iBGP vs eBGP Differences – A Deep Dive with Real-World Examples [ CCNP ENTERPRISE ]_networkjourney](https://networkjourney.com/wp-content/uploads/2025/06/iBGP-vs-eBGP-Differences-–-A-Deep-Dive-with-Real-World-Examples.png)
![Wireless LAN Controller Architecture – A CCNP Deep Dive [CCNP ENTERPRISE]_networkjourney](https://networkjourney.com/wp-content/uploads/2025/07/Wireless-LAN-Controller-Architecture-–-A-CCNP-Deep-Dive-CCNP-ENTERPRISE.png)