Mastering DHCP Snooping and Binding Table: Secure Your Layer 2 Network Like a Pro [CCNP ENTERPRISE]
I’ve had this discussion countless times with my students — “What if someone plugs in a rogue DHCP server and hijacks the IP allocation process?” Trust me, this isn’t just a theoretical concern. In modern LAN environments like shared offices, college campuses, and enterprise floors, rogue DHCP attacks are real. That’s why understanding DHCP Snooping and the Binding Table is a must for every serious network engineer.
In this post, we’ll demystify the logic behind DHCP Snooping, walk you through CLI examples, a practical EVE-NG lab, and real-world use cases you can relate to. Whether you’re preparing for CCNP, securing your corporate LAN, or just curious about how switches guard DHCP traffic — this article is your one-stop guide. Let’s roll!
Table of Contents
What is DHCP Snooping?
DHCP Snooping is a Layer 2 security mechanism that allows a switch to monitor DHCP traffic and protect against rogue DHCP servers. When enabled, it only permits DHCP offers and acknowledgments from trusted ports, typically the uplink connected to a DHCP server or core switch.
Switches categorize ports as:
- Trusted – DHCP responses are allowed
- Untrusted – Only client-originated requests are allowed
If someone connects a rogue DHCP server to an untrusted port, the switch drops the DHCP replies coming from it. This prevents attackers from assigning malicious IPs, fake gateways, or redirecting traffic through man-in-the-middle attacks.
Now comes the binding table — the star of this article. Every time a valid DHCP lease is handed out, the switch stores:
- Client MAC address
- Assigned IP address
- VLAN number
- Interface
This table is crucial because it serves as the foundation for Dynamic ARP Inspection (DAI) and IP Source Guard (IPSG), both of which use this data to filter packets at the switch level.
So, in a nutshell:
- DHCP Snooping blocks rogue DHCP servers
- The Binding Table builds a list of legitimate client bindings
- It acts as a foundation for other L2 security features
Key Features, Comparisons, and Pros/Cons
Feature Overview
| Feature | Description |
|---|---|
| Layer | Layer 2 |
| Primary Goal | Prevent rogue DHCP servers |
| Core Function | Filters DHCP traffic based on trust levels |
| Supported on | Cisco Catalyst, Nexus (IOS, IOS-XE, NX-OS) |
| Generates | DHCP Snooping Binding Table |
| Works with | DAI, IP Source Guard |
| Typical VLAN Usage | Enabled per VLAN |
Pros and Cons
| Pros | Cons |
|---|---|
| Prevents IP hijacking and rogue DHCP | Requires proper trust configuration |
| Enables tracking of MAC-IP associations | Needs binding table persistence on reboot |
| Integrates with DAI & IPSG | Complex in multi-VLAN environments |
| Fast, hardware-level enforcement | Misconfigured trust = DHCP failure for clients |
CLI Commands
| Task | Command Example |
|---|---|
| Enable DHCP snooping globally | ip dhcp snooping |
| Enable DHCP snooping on VLAN 10,20 | ip dhcp snooping vlan 10,20 |
| Trust port (e.g., uplink to DHCP server) | int Gi0/1ip dhcp snooping trust |
| Set rate limit (prevent DoS) | ip dhcp snooping limit rate 15 |
| Set database storage (for persistence) | ip dhcp snooping database flash:snoop-db |
| Show binding table | show ip dhcp snooping binding |
| Show snooping status | show ip dhcp snooping |
| Clear binding table | clear ip dhcp snooping binding |
Use Cases
| Environment | How DHCP Snooping Helps |
|---|---|
| College Campus | Prevents students from setting up rogue DHCP servers |
| Corporate Office | Stops attackers from handing fake IP/gateway to devices |
| Guest VLANs | Ensures guests only get IPs from authorized DHCP pool |
| VoIP Deployments | Maintains MAC-IP-VLAN mappings for critical devices |
| Dynamic Security Tools | Uses binding table for firewall rules or anomaly detection |
Lab: DHCP Snooping + Binding
Lab Topology Diagram
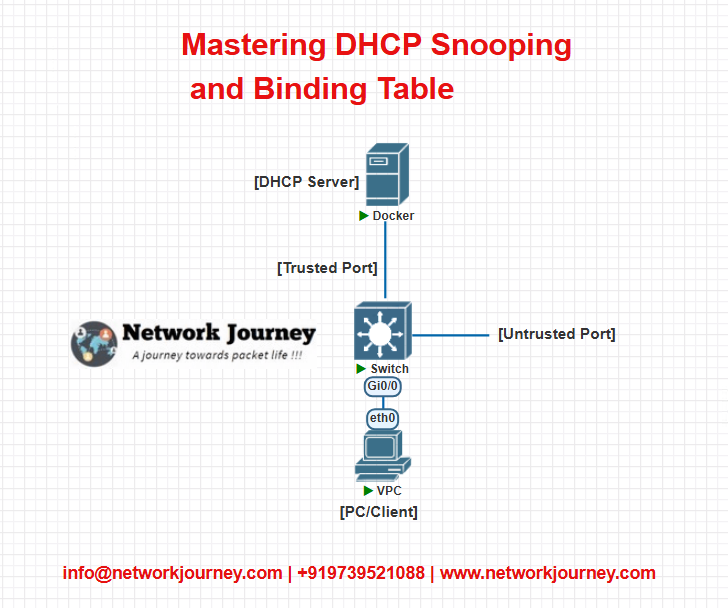
Configuration
On Switch SW1
Enable DHCP snooping globally and for VLAN 10
SW1(config)# ip dhcp snooping
SW1(config)# ip dhcp snooping vlan 10
! Configure trusted port towards DHCP server
SW1(config)# interface Gig0/1
SW1(config-if)# ip dhcp snooping trust
! Configure user-facing port
SW1(config)# interface Gig0/2
SW1(config-if)# switchport access vlan 10
! Enable database file for persistence
SW1(config)# ip dhcp snooping database flash:snoop-db
! Optional: Set rate limit on untrusted port
SW1(config-if)# ip dhcp snooping limit rate 20
Verification
SW1# show ip dhcp snooping
SW1# show ip dhcp snooping binding
SW1# show ip dhcp snooping statistics
Additional Lab Concepts with Diagram & Config
DHCP Snooping + Dynamic ARP Inspection (DAI)
[ DHCP Server ] ---> SW1 (Trusted Port + Snooping + DAI) ---> [ PC/Client ]
SW1(config)# ip arp inspection vlan 10
SW1(config-if)# ip arp inspection trust (on uplinks only)
DHCP Snooping + IP Source Guard
interface Gig0/2
ip verify source
Prevents IP spoofing from the same VLAN.
Troubleshooting Tips Table
Verifies source MAC and IP against the binding.
| Symptom | Suggested Fix |
|---|---|
| Clients not getting IPs | Check VLAN is included and port trust status |
| Binding table not populating | Ensure DHCP process completed, verify correct snooping config |
| Table wiped on reboot | Configure database file for persistence |
| Rogue DHCP still active | Confirm trusted ports aren’t misconfigured |
| Clients using static IPs blocked | Use ip verify source static (if using IP Source Guard) |
FAQs
1. What is the DHCP Binding Table used for?
Answer:
The DHCP Binding Table is a dynamic database that stores lease information for each DHCP client. This table helps switches enforce security at Layer 2. Each entry includes:
- MAC address of the client
- Assigned IP address
- VLAN number
- Interface/port ID on the switch
This data is used by features like Dynamic ARP Inspection (DAI) and IP Source Guard (IPSG) to validate that devices are using the correct IP and MAC addresses.
2. What happens if I forget to trust the uplink port?
Answer:
If the port connected to your DHCP server (uplink) is not marked as trusted:
- The switch will drop all DHCP Offer and ACK packets from that port.
- As a result, clients connected to untrusted ports will not receive IP addresses.
- This is one of the most common DHCP Snooping misconfigurations.
To fix this:
interface GigabitEthernet0/1
ip dhcp snooping trust
3. Is the Binding Table persistent after reboot?
Answer:
No, by default the binding table is stored in RAM and will be lost on reboot.
To make it persistent, configure a database file location:
ip dhcp snooping database flash:snoop-db
This command saves the table in flash memory, so it can be reloaded automatically after a reboot.
4. Can DHCP Snooping work across multiple VLANs?
Answer:
Yes, DHCP Snooping supports multiple VLANs. You must enable it per VLAN:
ip dhcp snooping vlan 10,20,30
Each VLAN will maintain its own entries in the binding table, and this allows for granular DHCP security control across different segments.
5. Does DHCP Snooping work with static IPs?
Answer:
Yes and No — DHCP Snooping itself does not interfere with static IPs because it only monitors DHCP packets. However:
- If IP Source Guard or DAI is enabled, static IP clients may be blocked if their MAC-IP binding isn’t recorded.
- To allow static clients, you must manually configure a static binding or disable IPSG on their port.
6. What kind of attacks does DHCP Snooping prevent?
Answer:
DHCP Snooping is effective against several Layer 2 attacks, including:
- Rogue DHCP Servers – prevents unauthorized devices from assigning IPs.
- DHCP Starvation Attacks – limits the rate of DHCP requests on a port.
- IP/MAC Spoofing – when used with DAI or IPSG, it stops forged IP-MAC address usage.
It’s one of the foundational tools for securing access layer switches.
7. How often is the binding table updated?
Answer:
The table is updated in real-time every time a DHCP handshake completes successfully.
Each new DHCP ACK from a trusted server triggers an entry creation in the table with:
- MAC
- IP
- VLAN
- Interface
When the DHCP lease expires or is released, the entry is automatically removed (unless persistence is enabled).
8. Does DHCP Snooping slow down the switch?
Answer:
Not significantly. DHCP Snooping is implemented in hardware on most modern Cisco switches, which means:
- Minimal performance overhead
- Near-instant DHCP packet filtering and processing
- High scalability even in large campus networks
However, avoid using debug dhcp snooping in production, as it can consume CPU and impact system stability.
9. How can I audit past IP usage from the binding table?
Answer:
You can use the following command to check the current table:
show ip dhcp snooping binding
For persistent tracking:
- Store the binding table to flash: bashCopyEdit
ip dhcp snooping database flash:snoop-log.db - Export logs regularly to a syslog server or use scripting to archive entries periodically for forensic or compliance purposes.
10. Is DHCP Snooping required for DAI (Dynamic ARP Inspection) to work?
Answer:
Yes! DAI depends on the DHCP Binding Table to validate ARP packets. Without DHCP Snooping:
- There is no MAC-IP mapping for DAI to verify against.
- As a result, DAI may drop all ARP traffic unless static ARP ACLs are configured (which is not scalable).
To use DAI with DHCP Snooping:
ip arp inspection vlan 10
Make sure DHCP Snooping is enabled on the same VLAN to populate the required bindings.
YouTube Video
Watch the Complete CCNP Enterprise: Mastering DHCP Snooping and Binding Table: Secure Your Layer 2 Network Like a Pro Lab Demo & Explanation on our channel:
Final Note
Understanding how to differentiate and implement Mastering DHCP Snooping and Binding Table: Secure Your Layer 2 Network Like a Pro in Modern Networks is critical for anyone pursuing CCNP Enterprise (ENCOR) certification or working in enterprise network roles. Use this guide in your practice labs, real-world projects, and interviews to show a solid grasp of architectural planning and CLI-level configuration skills.
If you found this article helpful and want to take your skills to the next level, I invite you to join my Instructor-Led Weekend Batch for:
CCNP Enterprise to CCIE Enterprise – Covering ENCOR, ENARSI, SD-WAN, and more!
Get hands-on labs, real-world projects, and industry-grade training that strengthens your Routing & Switching foundations while preparing you for advanced certifications and job roles.
Email: info@networkjourney.com
WhatsApp / Call: +91 97395 21088
Upskill now and future-proof your networking career!
![Mastering DHCP Snooping and Binding Table: Secure Your Layer 2 Network Like a Pro [CCNP ENTERPRISE]](https://networkjourney.com/wp-content/uploads/2025/07/nj-blog-post-dhcp-snooping-binding-table.jpg)

![QOS Diagnose & Fix Network Performance Issues [CCNP Enterprise]](https://networkjourney.com/wp-content/uploads/2025/07/QOS_Diagnose_Fix-Network-Performance-Issues_networkjourney.png)
