Can ARP ACLs Replace DHCP Snooping for ARP Security? Let’s Find Out! [CCNP ENTERPRISE]
I always say in my trainings — “Security doesn’t start at the firewall; it starts at the access port.” You’d be surprised how easy it is for an attacker to spoof an ARP reply and become the man-in-the-middle in your enterprise network. This is where Dynamic ARP Inspection (DAI) with ARP ACLs becomes your savior.
In this blog, I’ll break down the power of DAI and how ARP ACLs help even when you don’t have DHCP Snooping in place. You’ll learn the concepts, get real CLI, build your own EVE-NG lab, and even troubleshoot like a CCNP engineer. Let’s secure your switches — one MAC-IP pair at a time!
Table of Contents
Theory in Brief: What is DAI and Why Use ARP ACLs?
Dynamic ARP Inspection (DAI) is a Layer 2 security feature used to prevent ARP spoofing or gratuitous ARP attacks. It works by inspecting incoming ARP packets and verifying the sender’s MAC and IP address against a trusted database — typically built by DHCP Snooping.
But what if:
- You don’t have DHCP Snooping enabled?
- You use static IPs in your environment?
- You want to define valid ARP entries manually?
This is where ARP ACLs (Access Control Lists) come in. These ACLs allow you to manually define which MAC-IP pairs are allowed on a given VLAN or port. When DAI is combined with ARP ACLs, the switch can still perform validation even without a DHCP binding table.
In Simple Terms:
- DAI protects your switch against ARP spoofing.
- By default, it relies on the DHCP Snooping binding table.
- If DHCP Snooping is not in use, ARP ACLs can be manually configured to whitelist valid MAC-IP pairs.
Summary : Key Features & Pros/Cons
Key Comparisons
| Feature | DHCP Snooping Required | Static IP Support | Configuration Type |
|---|---|---|---|
| DAI + DHCP Snooping | Yes | No | Dynamic (auto-learned) |
| DAI + ARP ACLs | No | Yes | Manual (static entries) |
Pros and Cons
| Pros | Cons |
|---|---|
| Prevents ARP poisoning and spoofing | Requires accurate MAC-IP mapping |
| Works with or without DHCP | Manual ARP ACL config can be error-prone |
| Lightweight and hardware-based filtering | Not scalable in large networks without DHCP Snooping |
| Flexible — can work with static IP devices | Static ACLs must be updated manually |
Essential CLI Commands
| Task | Command Example |
|---|---|
| Enable DAI globally | ip arp inspection vlan 10 |
| Trust interface (uplinks) | interface Gi0/1ip arp inspection trust |
| Create ARP ACL | arp access-list STATIC_ARP |
| Permit entry in ACL | permit ip host 192.168.10.10 mac host 0011.2233.4455 |
| Apply ACL to VLAN | ip arp inspection filter STATIC_ARP vlan 10 |
| Show DAI bindings | show ip arp inspection |
| Show ACL entries | show arp access-list STATIC_ARP |
| Debug DAI packets | debug ip arp inspection |
Real-World Use Cases
| Scenario | Why DAI with ARP ACLs is Useful |
|---|---|
| Static IP printers or CCTV devices | Define allowed MAC-IP mappings without DHCP Snooping |
| Small branch office | No DHCP server? Use ARP ACLs for static validation |
| Guest VLAN with limited ARP access | Allow only known devices to resolve gateway MAC |
| Campus Wi-Fi controller | Prevent rogue APs from spoofing gateway MAC addresses |
EVE-NG LAB: DAI with ARP ACLs
Topology Diagram
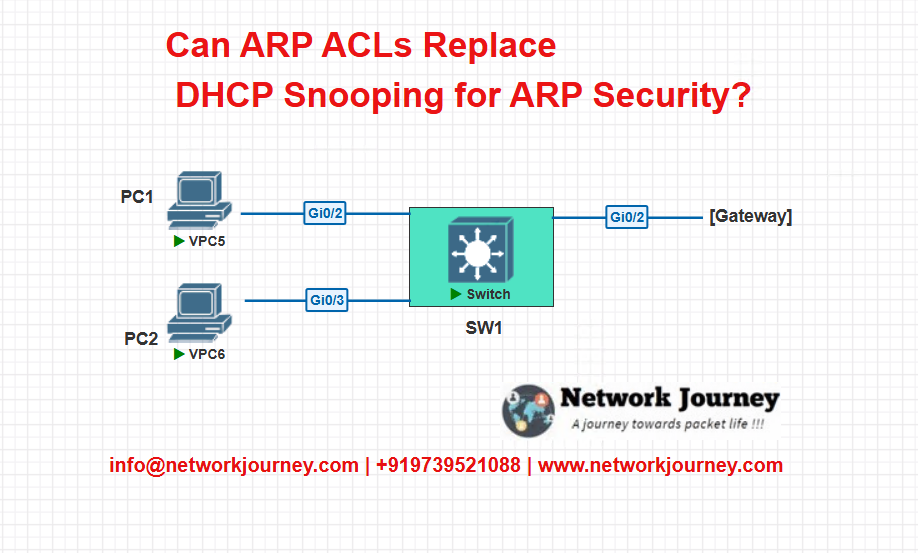
- VLAN 10 on all access ports
- Static IPs on PC1, PC2
- Gateway is a router or firewall
Configuration Steps
1. Create ARP ACL
SW1(config)# arp access-list STATIC_ARP
SW1(config-arp-nacl)# permit ip host 192.168.10.10 mac host 0011.2233.4455
SW1(config-arp-nacl)# permit ip host 192.168.10.11 mac host 0055.6677.8899
2. Enable DAI for VLAN
SW1(config)# ip arp inspection vlan 10
3. Apply ARP ACL to VLAN
SW1(config)# ip arp inspection filter STATIC_ARP vlan 10
4. Trust Uplink Port (toward gateway)
SW1(config)# interface Gi0/1
SW1(config-if)# ip arp inspection trust
Verification Commands
SW1# show ip arp inspection vlan 10
SW1# show arp access-list STATIC_ARP
SW1# debug ip arp inspection
Troubleshooting Tips
| Problem | Solution |
|---|---|
| Valid devices blocked | Check for incorrect MAC address in ACL |
| ARP ACL not applied | Use show ip arp inspection to verify ACL is bound to VLAN |
| Debug shows “ACL deny” | Add missing IP-MAC to ACL or use correct case/format |
| Gateway traffic blocked | Mark gateway-facing port as trusted |
| ACL works for one VLAN only | Define ACL per VLAN or use DHCP Snooping for dynamic learning |
Extra Lab Ideas to Expand Your Knowledge
1. Combine DAI with DHCP Snooping
- Enable DHCP Snooping on VLAN 10
- Let switch auto-learn bindings
- Use DAI without ARP ACLs
2. Test ARP Spoofing Tool (Ettercap/Arpspoof) in EVE-NG
- Try launching spoofing from Kali Linux
- Verify how DAI blocks fake ARP replies
3. Add Logging with Syslog Server
- Capture denied ARP logs in real time
- Analyze security events from Layer 2
Frequently Asked Questions (FAQs)
1. What is the main purpose of Dynamic ARP Inspection (DAI)?
Answer:
DAI is a Layer 2 security feature designed to prevent ARP spoofing or ARP poisoning attacks. It works by validating ARP packets received on untrusted ports, ensuring the source MAC and IP address match known legitimate bindings.
- Without DAI, malicious hosts can send fake ARP replies and hijack traffic.
- DAI inspects each ARP packet and drops any that don’t match an authorized entry.
2. How does DAI work without DHCP Snooping?
Answer:
Normally, DAI relies on the DHCP Snooping binding table to verify MAC-IP relationships. But in static IP environments, you may not have DHCP snooping enabled. In that case, ARP ACLs can be configured manually to specify allowed MAC-IP pairs.
- ARP ACLs act as a whitelist.
- Each ARP request/reply must match a permitted ACL entry.
Example:
arp access-list STATIC_ARP
permit ip host 192.168.1.10 mac host 0011.2233.4455
3. What is the difference between trusted and untrusted ports in DAI?
Answer:
DAI treats switch ports as either trusted or untrusted:
- Trusted ports (like uplinks to routers or DHCP servers): ARP packets are allowed without inspection.
- Untrusted ports (like access ports to clients): ARP packets are inspected and validated against bindings or ACLs.
Use this to trust a port:
interface Gi0/1
ip arp inspection trust
4. What happens if ARP ACL entries don’t match incoming traffic?
Answer:
If a device sends an ARP packet and no corresponding entry exists in the ARP ACL:
- The packet is dropped immediately.
- The switch may log a violation.
- Connectivity issues will occur for that host.
To fix:
- Double-check MAC-IP pairs and correct typos.
- Add static ACL entries using correct syntax.
5. Can DAI and ARP ACLs be used together with DHCP Snooping?
Answer:
Yes. In fact, using both offers flexibility:
- Use ARP ACLs for devices with static IPs (like servers, printers).
- Use DHCP Snooping for dynamically addressed clients.
This hybrid model allows broader protection across mixed environments.
6. Are ARP ACLs scalable in large networks?
Answer:
Not really. ARP ACLs are manual, so they’re best suited for:
- Small networks
- Static IP devices
- Lab environments
In enterprise or campus networks, managing hundreds or thousands of ARP ACL entries becomes difficult. DHCP Snooping with automatic bindings is more scalable.
7. What types of attacks does DAI prevent?
Answer:
DAI protects against several common Layer 2 threats:
- ARP Spoofing / Poisoning
- Attacker sends fake ARP reply claiming to be the default gateway.
- Man-in-the-middle attacks
- Hijacks traffic between two hosts to sniff, alter, or drop data.
- MAC/IP Impersonation
- Attacker tries to mimic a legitimate host’s identity.
8. How do I verify that DAI and ARP ACLs are working?
Answer:
Use the following CLI commands to verify DAI operations:
- Check global DAI status: bashCopyEdit
show ip arp inspection - See if ACL is applied correctly: bashCopyEdit
show ip arp inspection vlan 10 show arp access-list STATIC_ARP - Monitor violations or drops: bashCopyEdit
show ip arp inspection statistics debug ip arp inspection
9. Can ARP ACLs cause valid devices to lose connectivity?
Answer:
Yes. This is a common issue when:
- MAC addresses are mistyped
- Incorrect IPs are configured in ACLs
- Wrong VLAN or port is referenced
To avoid this:
- Use
show mac address-tableto confirm MACs. - Match each ACL entry with actual static IP assignments.
- Always test changes in a lab before deploying in production.
10. How often do ARP ACLs need to be updated?
Answer:
ARP ACLs must be manually updated any time:
- A device gets a new MAC address (NIC replacement)
- The static IP scheme changes
- Devices are relocated to a different VLAN
Unlike DHCP Snooping, there’s no automatic learning. Periodic auditing is required to keep ACLs in sync with real-world topology.
YouTube Video (Lab Walkthrough)
Watch the Complete CCNP Enterprise: Can ARP ACLs Replace DHCP Snooping for ARP Security? Let’s Find Out! Demo & Explanation on our channel:
Final Note
Understanding how to differentiate and implement Can ARP ACLs Replace DHCP Snooping for ARP Security? in Modern Networks is critical for anyone pursuing CCNP Enterprise (ENCOR) certification or working in enterprise network roles. Use this guide in your practice labs, real-world projects, and interviews to show a solid grasp of architectural planning and CLI-level configuration skills.
If you found this article helpful and want to take your skills to the next level, I invite you to join my Instructor-Led Weekend Batch for:
CCNP Enterprise to CCIE Enterprise – Covering ENCOR, ENARSI, SD-WAN, and more!
Get hands-on labs, real-world projects, and industry-grade training that strengthens your Routing & Switching foundations while preparing you for advanced certifications and job roles.
Email: info@networkjourney.com
WhatsApp / Call: +91 97395 21088
Upskill now and future-proof your networking career!
![Can ARP ACLs Replace DHCP Snooping for ARP Security? Let’s Find Out! [CCNP ENTERPRISE]](https://networkjourney.com/wp-content/uploads/2025/07/nj-blog-post-ARP-ACLs.jpg)
![Performance Routing (PfR) Basics: Optimize Traffic Like a Pro [CCNP ENTERPRISE] networkjourney](https://networkjourney.com/wp-content/uploads/2025/06/nj-blog-post-PFR.jpg)
![How Can GRE Tunnel Help Connect Remote Sites? Full Cisco Setup Guide [CCNP Enterprise]](https://networkjourney.com/wp-content/uploads/2025/06/How-Can-GRE-Tunnel-Help-Connect-Remote-Sites_networkjourney.png)
