Ticket#1-Enterprise Slowness: High CPU on Core Switch – Step-by-Step Troubleshooting [CCNP ENTERPRISE]
Table of Contents
Problem Summary
A major enterprise customer reported intermittent slowness across multiple departments. Applications were taking longer to respond, voice quality degraded, and video calls were choppy. This issue seemed to affect users connected to different VLANs and floors. The complaint was urgent and escalated to the Network Operations Team for deep analysis.
Symptoms Observed
- Users complained of lag in internal and internet-based applications.
- High latency when pinging the default gateway (Core Switch).
- SNMP monitoring showed CPU spikes above 90% on the core switch.
- SSH/telnet sessions to the core switch were sluggish or timed out.
- EIGRP adjacencies flapped intermittently with access switches.
- Spanning-tree convergence delays observed via logs.
Root Cause Analysis
Initial suspicion was on upstream congestion, but further analysis revealed that the core switch (Layer 3) was running at dangerously high CPU levels.
Upon CLI inspection and logging, the following key observations were made:
show processes cpu sortedshowed “hulc_cpu” and “arp_input” processes consuming significant CPU.- Continuous flooding of ARP requests from one access switch (misbehaving endpoint or loop).
- High number of broadcast and multicast packets reaching the CPU.
- Spanning Tree Topology Changes every few seconds indicating instability.
- No CoPP (Control Plane Policing) configured to protect CPU resources.
The Fix
The troubleshooting and remediation involved the following steps:
- Isolate the Source
- Used
show interfaces counters errorsandshow mac address-tableto trace the source port. - Identified one access switch uplink generating ARP storms.
- Used
- Mitigate Immediate CPU Load
- Disabled the offending access switch uplink to quickly bring CPU usage down.
- Confirmed CPU dropped to normal levels (~15%).
- Correct Configuration & Controls
- Implemented storm control on all access switch uplinks.
- Enabled BPDU Guard and Root Guard on edge ports.
- Reviewed spanning-tree root placement.
- Apply CoPP (Control Plane Policing)
- Rate-limited unnecessary traffic to the CPU.
- Ensured management and control traffic had prioritization.
EVE-NG Lab Topology
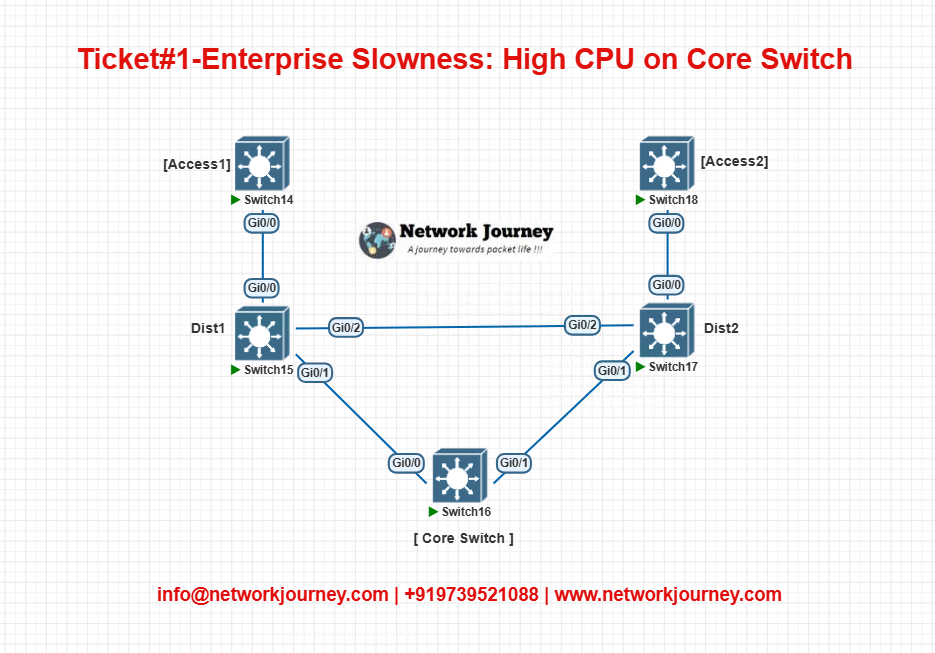
- Core is the Layer 3 switch.
- Access1 simulated the source of ARP storm.
- STP configured for VLANs across access/distribution/core.
CLI Simulation in Lab (Troubleshooting Steps)
Check CPU Usage
show processes cpu sorted
Identify Flood Source
show interfaces counters errors
show mac address-table dynamic
Disable Problem Port
interface Gig1/0/24
shutdown
Enable Storm Control
interface range gig1/0/1 - 24
storm-control broadcast level 5.00
storm-control multicast level 5.00
Apply CoPP
class-map match-any CONTROL-PLANE
match access-group name CONTROL-PLANE-ACL
policy-map CONTROL-POLICY
class CONTROL-PLANE
police 10000000 8000 conform-action transmit exceed-action drop
control-plane
service-policy input CONTROL-POLICY
Verification
| Task | Command / Method | Expected Output |
|---|---|---|
| CPU Check Post-Fix | show processes cpu sorted | CPU < 20% |
| Broadcast/Multicast Validation | show interface counters | Traffic reduced/stabilized |
| MAC Flooding Check | show mac address-table | No excessive unknown MACs |
| STP Stability | show spanning-tree vlan X | No rapid changes in root port/blocking |
| CoPP Operation | show policy-map control-plane | Drops and matches visible |
Key Takeaways
- High CPU on core switches can cripple the entire enterprise.
- Always implement control plane protection (CoPP) in enterprise designs.
- Storm-control and STP protections (BPDU Guard/Root Guard) are critical at the access layer.
- Use
show processes cpu,mac address-table, and interface counters effectively for root cause. - End-user complaints about slowness can often originate from Layer 2 loops or misbehaving clients.
Best Practices / Design Tips
- Design your network with Layer 2 loop prevention in mind.
- Use redundant uplinks + EtherChannels, and not single points of failure.
- Apply storm control on all access interfaces (especially to endpoints).
- Place CoPP policies on distribution/core devices.
- Ensure network monitoring tools catch CPU and STP anomalies early.
- Implement SPAN/RSPAN for deep packet inspection if needed.
- Review Spanning Tree root bridge placements for traffic optimization.
FAQs
1. Why does high CPU on a switch cause slowness across the enterprise?
Answer:
When the switch’s CPU is maxed out, it can’t process control plane functions like routing, ARP, and STP, leading to dropped packets and delays in Layer 2/3 decision-making.
2. Which commands help detect high CPU utilization?
Answer:
show processes cpu sortedshow platform cpu packet statistics(if available)show controllersfor deeper hardware insights
3. Can an ARP storm really bring down an enterprise network?
Answer:
Yes. Unchecked ARP flooding overloads the CPU and MAC address table, leading to erratic forwarding behavior and high CPU.
4. How to differentiate between data plane vs control plane traffic issues?
Answer:
- Data plane: Interface counters, bandwidth issues
- Control plane: CPU spikes, neighbor flaps, delayed management access
5. Why did STP topology keep changing during this incident?
Answer:
A broadcast storm or loop can cause interfaces to flap, forcing frequent STP recalculations.
6. What is CoPP and how does it help?
Answer:
Control Plane Policing (CoPP) protects the router/switch CPU by limiting the rate of traffic reaching it, ensuring essential protocols aren’t impacted by floods.
7. What is the best way to isolate a loop in the network?
Answer:
- Use
show mac address-tableto trace moving MACs - Check for high port utilization and erratic interface counters
8. How often should storm-control be applied?
Answer:
Storm-control should be applied by default on all access ports, especially toward end devices, printers, and unmanaged switches.
9. How do I monitor CPU usage trends over time?
Answer:
Use SNMP tools (like PRTG, SolarWinds) to graph CPU usage and set alerts for threshold breaches.
10. Can CoPP affect legitimate traffic?
Answer:
Yes, if not correctly configured. You must define ACLs carefully to permit essential traffic and apply limits appropriately.
11. Why are Layer 2 loops more dangerous in flat topologies?
Answer:
Flat topologies lack segmentation. One loop can impact the entire broadcast domain and choke core devices.
12. What is the role of BPDU Guard?
Answer:
BPDU Guard disables ports if BPDUs are received unexpectedly, preventing accidental switches from causing loops.
13. How to prevent ARP storms from happening again?
Answer:
- Apply dynamic ARP inspection
- Rate-limit ARP
- Use port security
14. What if multiple devices are generating storms?
Answer:
Use SPAN to sniff traffic at aggregation points and identify patterns. Apply isolation, QoS, and security policies.
15. Is this type of scenario covered in CCNP exams?
Answer:
Absolutely. Topics like CoPP, control plane protection, storm-control, STP behaviors, and high CPU troubleshooting are part of CCNP ENCOR/ENARSI.
YouTube Link
Watch the Complete CCNP Enterprise: Enterprise Slowness: High CPU on Core Switch – Step-by-Step Troubleshooting Demo & Explanation on our channel:
Class 3 Discussion on Various Network Device Components
Final Note
Understanding how to differentiate and implement Enterprise Slowness: High CPU on Core Switch – Step-by-Step Troubleshooting is critical for anyone pursuing CCNP Enterprise (ENCOR) certification or working in enterprise network roles. Use this guide in your practice labs, real-world projects, and interviews to show a solid grasp of architectural planning and CLI-level configuration skills.
If you found this article helpful and want to take your skills to the next level, I invite you to join my Instructor-Led Weekend Batch for:
CCNP Enterprise to CCIE Enterprise – Covering ENCOR, ENARSI, SD-WAN, and more!
Get hands-on labs, real-world projects, and industry-grade training that strengthens your Routing & Switching foundations while preparing you for advanced certifications and job roles.
Email: info@networkjourney.com
WhatsApp / Call: +91 97395 21088
Upskill now and future-proof your networking career!
![Ticket#1-Enterprise Slowness: High CPU on Core Switch – Step-by-Step Troubleshooting [CCNP ENTERPRISE]](https://networkjourney.com/wp-content/uploads/2025/07/nj-blog-post-Ticket-1.jpg)
![PBR Configuration with Match Statements [ CCNP ENTERPRISE ]_networkjourney](https://networkjourney.com/wp-content/uploads/2025/06/PBR-Configuration-with-Match-Statements-CCNP-ENTERPRISE-.png)

![Cisco LISP Protocol Explained with CLI, Labs, and Use Cases. [CCNP ENTERPRISE]](https://networkjourney.com/wp-content/uploads/2025/06/Cisco-LISP-Protocol-Explained-with-CLI_Labs_and-Use-Cases_networkjourney.png)