[DAY#9 PyATS Series] Parsing show ip interface brief across vendors using pyATS [Python for Network Engineer]
Table of Contents
Introduction on the Key Points
We will walk through how to parse the show ip interface brief output across Cisco, Arista, Palo Alto, and FortiGate using pyATS & Genie parsers. This ensures uniformity in data interpretation, enabling us to audit reachability, interface statuses, and detect inconsistencies across platforms—all vendor-agnostically.
This hands-on blog is meant for network engineers getting into automation and building multi-vendor consistency. We’re using Python for Network Engineer automation, leveraging the power of pyATS and Genie to parse raw CLI outputs into structured JSON. No guesswork—just clean, actionable data.
By the end of this post, you’ll be confident in:
- Parsing
show ip interface briefoutputs across vendors - Extracting interface status/description info in JSON
- Running a ping reachability validation
- Aligning multiple vendors in a single script
- Using pyATS testbed for consistent connectivity
Topology Overview
We are working with the following multi-vendor topology in our EVE-NG/PNET/physical lab:
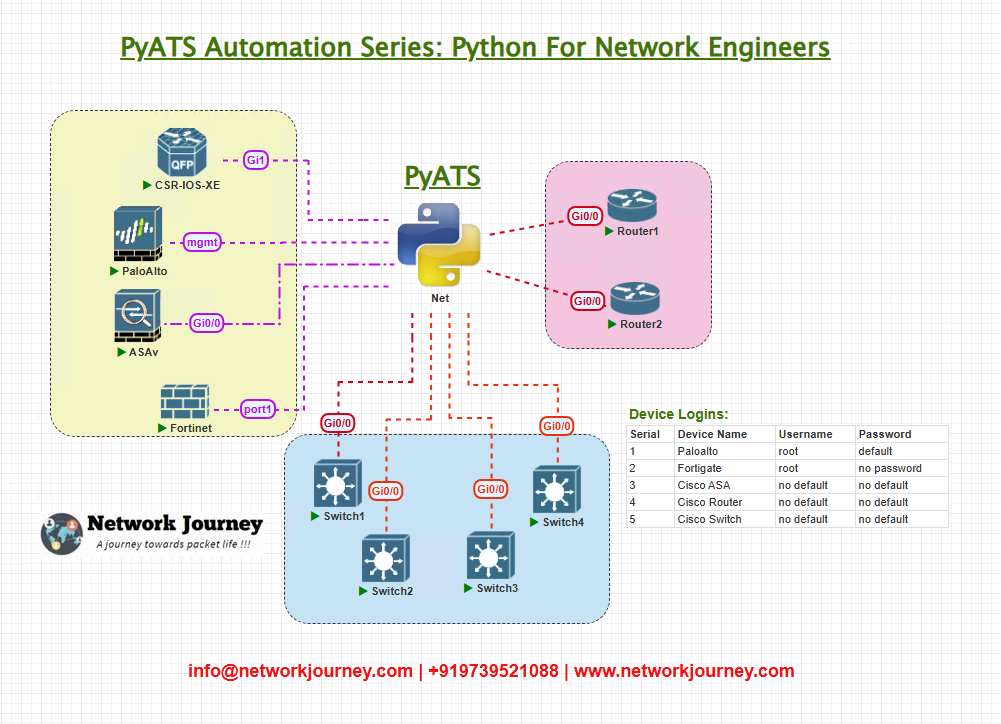
This topology lets us simulate real-world distributed environments where devices from multiple vendors need to be validated together.
Why Vendor‑Agnostic Testing Matters
In a hybrid world with Cisco in DC, Arista at the Edge, Palo Alto in Security, and FortiGate for segmentation, standardizing validation becomes essential.
Vendor-specific commands may differ in structure, syntax, and response formats.
But vendor-agnostic validation with pyATS:
- Reduces CLI inconsistencies
- Enables unified automation pipelines
- Eliminates parsing headaches
- Ensures operational consistency
- Helps in change impact analysis and audits
This makes it an essential skill when working in regulated environments or automation pipelines.
Topology & Communications
- Protocols: SSH for all devices (fallback to Telnet for FortiGate if needed)
- Ping Tests: From pyATS host to each loopback interface
- Command used:
show ip interface briefor its equivalent per vendor
Workflow Script
from genie.testbed import load
from rich import print
import json
# Load testbed
testbed = load('testbed.yml')
# Parse show ip interface brief
for device_name in testbed.devices:
device = testbed.devices[device_name]
device.connect(init_exec_commands=[], init_config_commands=[], log_stdout=False)
print(f"\n[green]Connected to {device_name}[/green]")
try:
output = device.parse('show ip interface brief')
print(json.dumps(output, indent=2))
except Exception as e:
print(f"[red]Parsing failed for {device_name}: {e}[/red]")
device.disconnect()
Explanation by Line
| Line | Explanation |
|---|---|
from genie.testbed import load | Loads the pyATS testbed |
testbed = load('testbed.yml') | Reads device connection details |
device.connect(...) | Establishes connection to the device |
device.parse(...) | Executes and parses the show ip interface brief |
json.dumps(output, indent=2) | Beautifies JSON output for easy reading |
device.disconnect() | Cleanly closes SSH/Telnet session |
testbed.yml Example
devices:
cisco-ios:
os: iosxe
type: router
connections:
cli:
protocol: ssh
ip: 192.168.100.1
port: 22
arista-eos:
os: eos
type: switch
connections:
cli:
protocol: ssh
ip: 192.168.100.2
port: 22
paloalto-fw:
os: panos
type: firewall
connections:
cli:
protocol: ssh
ip: 192.168.100.3
port: 22
fortigate-fw:
os: fortinet
type: firewall
connections:
cli:
protocol: ssh
ip: 192.168.100.4
port: 22
Multi-Vendor CLI Screenshots
Cisco IOS-XE
Interface IP-Address OK? Method Status Protocol GigabitEthernet0/0 10.1.1.1 YES manual up up Loopback0 192.168.0.1 YES manual up up
Arista EOS
Port IP Address Interface Status Et1 10.1.1.2 up Lo0 192.168.0.2 up
Palo Alto PAN-OS
> show interface management Name: management IP address: 192.168.0.3 Status: up
FortiGate
FGT # show system interface
config system interface
edit "mgmt"
set ip 192.168.0.4 255.255.255.0
set status up
next
end
FAQs
Q1. What is the benefit of parsing show ip interface brief across vendors?
A: It helps in creating standardized reports, detecting interface issues proactively, and aligning network health status in multi-vendor environments without needing separate logic per vendor.
Q2. Can pyATS parse commands for non-Cisco platforms like Fortinet or Palo Alto?
A: Yes, with structured CLI output and proper testbed setup, pyATS with Genie plugins can parse data from most major vendors. Some may need custom parsers or unstructured text parsing.
Q3. What if a vendor doesn’t have a native parser in pyATS?
A: You can fall back on unstructured parsing (regex or templates) or write your own parser using pyATS’ extensible APIs.
Q4. Is the show ip interface brief command same across all vendors?
A: No. It varies slightly or significantly. That’s why vendor-agnostic parsing normalizes this data into a common JSON structure, removing human error from manual interpretation.
Q5. Can I use this script in CI/CD pipelines?
A: Absolutely. With proper testbed integration and result handling, this script can become part of a daily health check or validation before/after changes.
Q6. Do I need pyATS Genie parser libraries for each vendor?
A: Yes. Some vendors require specific parser support. Ensure your environment has the correct libraries installed or be ready to handle some parsing manually.
Q7. What if SSH is not working?
A: Fallback to Telnet if allowed. Also ensure:
- Proper username/password in
.pyats.conf - Devices are reachable (ping first)
- Firewall or ACLs are not blocking SSH
YouTube Link
Watch the Complete Python for Network Engineer: Parsing show ip interface brief across vendors using pyATS (Vendor-Agnostic) for Cisco Lab Demo & Explanation on our channel:
Join Our Training
Are you ready to take your Python for Network Engineer skills to the next level?
I, Trainer Sagar Dhawan, have mentored 25,000+ engineers globally, and now invite you to join my 3-Month Instructor-Led Training Program focused on:
- Python Automation (Beginner to Advanced)
- Ansible Playbooks for Network Devices
- APIs for Cisco, Arista, Fortinet, Palo Alto
- Real-World Labs (EVE-NG) + Multi-Vendor Projects
- CI/CD Pipeline Concepts + pyATS + Nornir
Click below to view course outline and enroll:
Enroll Now & Future‑Proof Your Career
Email: info@networkjourney.com
WhatsApp / Call: +91 97395 21088
https://course.networkjourney.com/python-ansible-api-cisco-devnet-for-network-engineers
Transform your career with Vendor-Agnostic Automation Mastery and let’s automate networks together—one script at a time.
![[DAY#9 PyATS Series] Parsing show ip interface brief across vendors using pyATS [Python for Network Engineer]](https://networkjourney.com/wp-content/uploads/2025/07/DAY9-PyATS-Series-Parsing-show-ip-interface-brief-across-vendors-using-pyATS-Python-for-Network-Engineer.png)
![Ticket#24: Routing Table Blackhole – Route Redistribution Loop Detected Between OSPF and BGP [CCNP Enterprise]](https://networkjourney.com/wp-content/uploads/2025/07/Ticket24_Routing-Table-Blackhole-–-Route-Redistribution-Loop-Detected-Between-OSPF-and-BGP_networkjourney.png)