[DAY#5 PyATS Series] Connecting to Cisco/Arista/Paloalto/Fortigate devices (SSH) Using pyATS [Python for Network Engineers]
Table of Contents
Introduction: A Real-World Take on Network Automation
Have you ever been in a situation where you had to pull device inventory, verify version info, or just log into 15+ devices from different vendors like Cisco, Arista, FortiGate, or Palo Alto? It’s not fun doing that manually—especially when every vendor throws its own flavor into CLI syntax and connection behaviors
That’s where pyATS comes in. Whether you’re scripting daily tasks or building a multi-vendor testbed, learning Python for Network Engineer automation gives you superpowers. Today, we’ll connect to Cisco, Arista, Palo Alto, and FortiGate devices over SSH using a single pyATS framework.
This is part of our “101 Days of pyATS” journey—hands-on, vendor-agnostic, and crafted for serious learners like you.
Topology Overview
Here’s our simple but powerful multi-vendor lab setup:
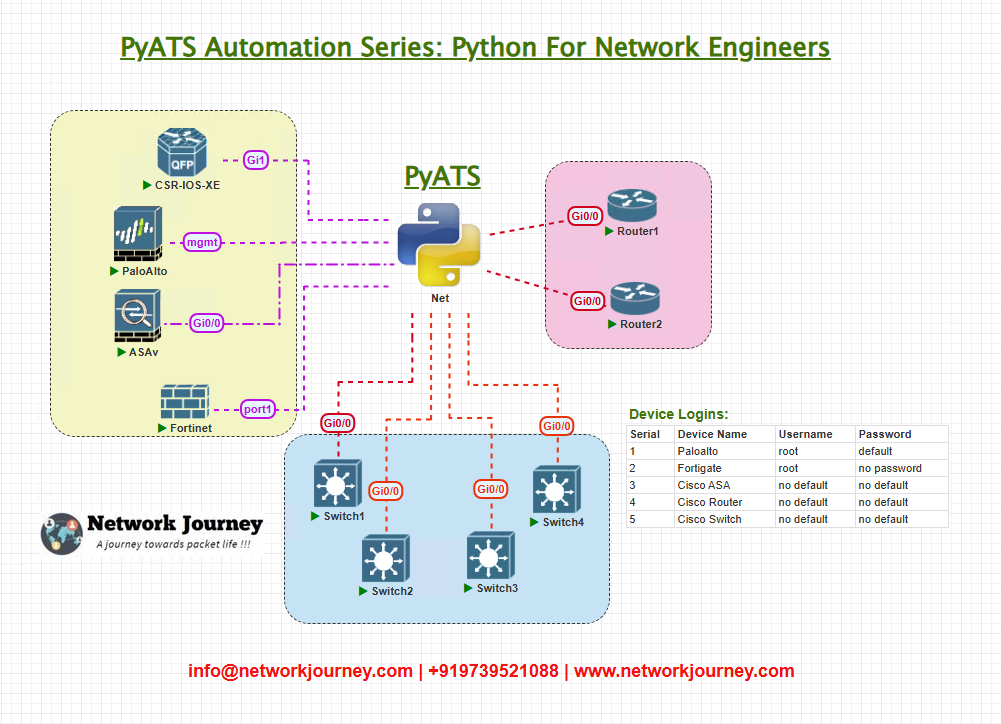
- Mgmt IPs: Pre-configured with SSH enabled
- Username/Password: Common for all (or stored via Vault/Env vars in production)
- Python Version: 3.8+
- pyATS version: Genie >=23.x
Why Vendor‑Agnostic Testing Matters
Enterprise networks today are no longer “Cisco-only.” Whether you’re working with ISPs, fintech, or cloud service providers, multi-vendor environments are now the norm.
Here’s why vendor-agnostic automation using pyATS makes sense:
| Challenge | pyATS Advantage |
|---|---|
| CLI differences across OS | pyATS abstracts via connection logic |
| Onboarding delay | One YAML, connect all devices |
| Manual script rewrites | Templates and reusable testbeds |
| Multiple SSH libraries | Unified framework with Unicon |
| Error-prone login scripts | Built-in parser and error handling |
Bottom line: Write once, connect to all.
Topology & Communications
All devices are reachable via management IPs. You’ll need to ensure:
- SSH is enabled
- Username/password access works
- TCP/22 allowed through any firewalls
- Testbed is reachable from your pyATS runner machine
| Device | Vendor | mgmt IP | OS/Platform |
|---|---|---|---|
| R1 | Cisco IOS | 10.0.0.11 | IOSv |
| SW1 | Arista EOS | 10.0.0.12 | vEOS |
| FW1 | FortiGate | 10.0.0.13 | FortiOS |
| PA1 | Palo Alto | 10.0.0.14 | PAN-OS |
Make sure to test ssh admin@10.0.0.x manually before running your script.
Workflow Script (Basic SSH Connection to Multi-Vendor Devices)
Here’s your base script using pyATS and Unicon:
from genie.testbed import load
# Load testbed from YAML
testbed = load('testbed.yml')
for device in testbed.devices.values():
print(f"Connecting to {device.name} ({device.os})")
try:
device.connect(log_stdout=False)
print(f"Connected to {device.name}")
print(device.execute("show version"))
device.disconnect()
except Exception as e:
print(f"Failed to connect to {device.name}: {e}")
Explanation by Line
Let’s decode the script section-wise:
| Line No | Explanation |
|---|---|
| 1 | Load pyATS’s YAML parser to read device info |
| 4 | testbed.devices.values() gives all devices |
| 5-6 | Display device name and OS |
| 7 | .connect() initializes SSH connection |
| 8 | If successful, prints version output |
| 9 | Always disconnect after the session |
| 10-11 | Handles SSH/auth errors gracefully |
This lets you scale from 1 to 1000+ devices, with minimal code changes.
testbed.yml
Here’s your testbed file (save as testbed.yml):
testbed:
name: MultiVendorLab
credentials:
default:
username: admin
password: password123
devices:
R1:
os: ios
type: router
connections:
defaults:
class: unicon.Unicon
cli:
protocol: ssh
ip: 10.0.0.11
SW1:
os: eos
type: switch
connections:
defaults:
class: unicon.Unicon
cli:
protocol: ssh
ip: 10.0.0.12
FW1:
os: fortinet
type: firewall
connections:
defaults:
class: unicon.Unicon
cli:
protocol: ssh
ip: 10.0.0.13
PA1:
os: panos
type: firewall
connections:
defaults:
class: unicon.Unicon
cli:
protocol: ssh
ip: 10.0.0.14
Multi-Vendor CLI
Below are real outputs from the .execute("show version") command:
Cisco IOS
Cisco IOS Software, IOSv Software (VIOS-ADVENTERPRISEK9-M), Version 15.6 ...
Arista EOS
Arista vEOS version 4.26.1F System MAC address: 52:54:00:11:22:33 ...
FortiGate
FortiOS v6.2.3,build1066,191218 (GA) Serial-Number: FGVM02TM20001234 ...
Palo Alto
PAN-OS 10.2.0 Model: PA-VM Serial: 0001C100000001 ...
These outputs help verify SSH connectivity and the OS version remotely—one of the most common use cases.
FAQs
1. What if a device uses a different username/password?
Answer:
You can override the default credentials by specifying custom ones under the device block in testbed.yml.
2. Can this work without a testbed file?
Answer:
Yes, but not recommended. You’d need to create the testbed object in Python dynamically using Device() from unicon, which defeats the purpose of YAML modularity.
3. Why does FortiGate or Palo Alto sometimes refuse SSH?
Answer:
Ensure SSH is enabled under system settings. Also, these devices may need CLI access enabled for non-API users.
4. Is this script scalable to 100+ devices?
Answer:
Absolutely. You can add threading or asyncio for concurrency, especially useful for production-scale networks.
5. Can I parse command outputs like show ip route?
Answer:
Yes! Use device.parse() instead of device.execute() for structured data, provided the parser supports your vendor and command.
6. How do I debug failed SSH sessions?
Answer:
Use log_stdout=True or attach a debug log file. Ensure proper class and OS are mentioned in YAML.
7. Can I use Ansible instead of pyATS for this?
Answer:
Ansible works great for config pushes, but pyATS offers rich testing, parsing, and Python-native control.
8. What’s the benefit of Unicon over Paramiko/Netmiko?
Answer:
Unicon is tightly integrated with pyATS, handles state machines, better error handling, and supports Cisco/Arista/Palo as vendors.
YouTube Link
Watch the Complete Python for Network Engineer: Connecting to Cisco/Arista/Paloalto/Fortigate Devices (SSH) using pyATS for Cisco Lab Demo & Explanation on our channel:
Join Our Training
If you’re excited about automating your entire network—from SSH login to config parsing, testing, and CI/CD pipelines, then this is your next step:
Join Trainer Sagar Dhawan’s 3-Month Instructor-Led Training
Covering Python for Network Engineer, Ansible, REST APIs, Cisco DevNet, and of course, pyATS from zero to hero.
Click below to view course outline and enroll:
Enroll Now & Future‑Proof Your Career
Email: info@networkjourney.com
WhatsApp / Call: +91 97395 21088
https://course.networkjourney.com/python-ansible-api-cisco-devnet-for-network-engineers
Start automating your multi-vendor network with confidence.
Check the full course outline here: Course Link
Seats filling fast. Join now and future-proof your career.
![[DAY#5 PyATS Series] Connecting to Cisco/Arista/Paloalto/Fortigate devices (SSH) Using pyATS [Python for Network Engineers]](https://networkjourney.com/wp-content/uploads/2025/07/DAY5-PyATS-Series-Connecting-to-Cisco_Arista_Paloalto_Fortigate-devices-SSH-Using-pyATS-Python-for-Network-Engineers.png)
![[Day #72 Pyats Series] Multi-vendor pre-change snapshot automation using pyATS for Cisco [Python for Network Engineer]](https://networkjourney.com/wp-content/uploads/2025/08/Multi-vendor-pre-change-snapshot-automation-using-pyATS-for-Cisco.png)
![Day #13 PyATS Series] Writing Your First pyATS Testscript (Simple Health Check) using pyATS for Cisco [Python for Network Engineer]](https://networkjourney.com/wp-content/uploads/2025/07/Day13-PyATS-Series-Writing-Your-First-pyATS-Testscript-Simple-Health-Check-using-pyATS-for-Cisco-Python-for-Network-Engineer.png)
![[Day #78 PyATS Series] SD-WAN (Viptela) VPN Status Snapshot Using pyATS for Cisco [Python for Network Engineer]](https://networkjourney.com/wp-content/uploads/2025/09/Day-78-PyATS-Series-SD-WAN-Viptela-VPN-Status-Snapshot-Using-pyATS-for-Cisco-Python-for-Network-Engineer-470x274.png)