[Day 32] Cisco ISE Mastery Training: Configuring Cisco AnyConnect NAM for Wired Auth
Table of Contents
Introduction
When it comes to 802.1X-based wired authentication, the supplicant on the endpoint plays a critical role. For most corporate environments, Windows Native Supplicant is sufficient — but it lacks advanced control, flexibility, and multi-profile management.
Enter Cisco AnyConnect Network Access Manager (NAM) — a powerful 802.1X supplicant replacement from Cisco. NAM is part of the AnyConnect Secure Mobility Client suite and allows you to:
- Define multiple wired and wireless profiles
- Control authentication order and failover methods
- Enforce specific EAP methods for maximum security
- Provide a consistent experience across Windows and macOS endpoints
In Cisco ISE deployments, configuring NAM ensures endpoints authenticate consistently, even before user login (machine auth), and can handle advanced setups like EAP-FAST, PEAP, or certificate-based authentication. This is mission-critical for secure wired NAC.
Problem Statement
In many enterprises:
- The Windows built-in supplicant is misconfigured or inconsistent across PCs.
- Engineers struggle with dual-auth (machine + user) scenarios.
- Endpoints fail 802.1X authentication because the supplicant does not automatically reconnect after profile changes.
- IT teams have no central way to push authentication profiles without Group Policy or complex scripts.
This leads to authentication delays, user frustration, and security gaps.
Solution Overview
Cisco AnyConnect NAM solves these issues by:
- Providing a central profile that defines exact authentication settings.
- Supporting machine authentication before logon and user authentication after logon.
- Enforcing strong EAP methods aligned with ISE policy sets.
- Being deployable via SCCM, Intune, GPO, or manual installation.
- Allowing ISE posture and authentication to work seamlessly together.
Sample Lab Topology
Lab Components:
- ISE: v3.2 running on VMware ESXi
- Switch: Cisco Catalyst 9300 (Access Layer) in EVE-NG or physical
- Endpoint: Windows 10 with AnyConnect NAM installed
- AD Server: Windows Server 2019 for identity store
- Syslog Server: For log monitoring
- Connections: Wired 802.1X port authentication
- NAM Profile: Pre-configured XML pushed via ISE or manual import
Diagram Description:
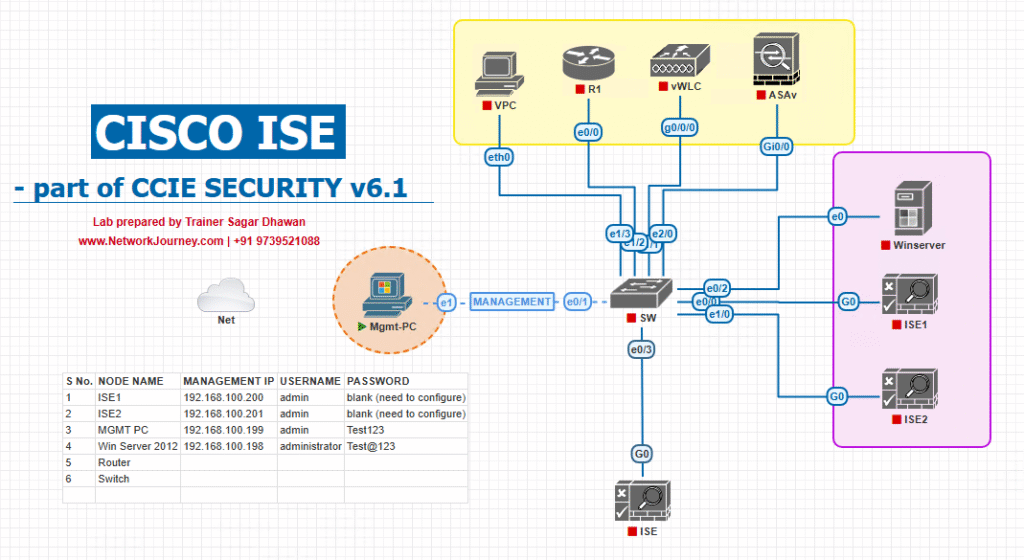
- ISE is the RADIUS server for 802.1X
- Switch handles EAPoL → RADIUS exchange
- NAM controls supplicant behavior on Windows
Step-by-Step GUI Configuration Guide
Part A – Prepare ISE for Wired Auth
- Enable 802.1X on ISE:
- Navigate: Administration → Deployment → Enable 802.1X
- [Screenshot: ISE 802.1X enable screen]
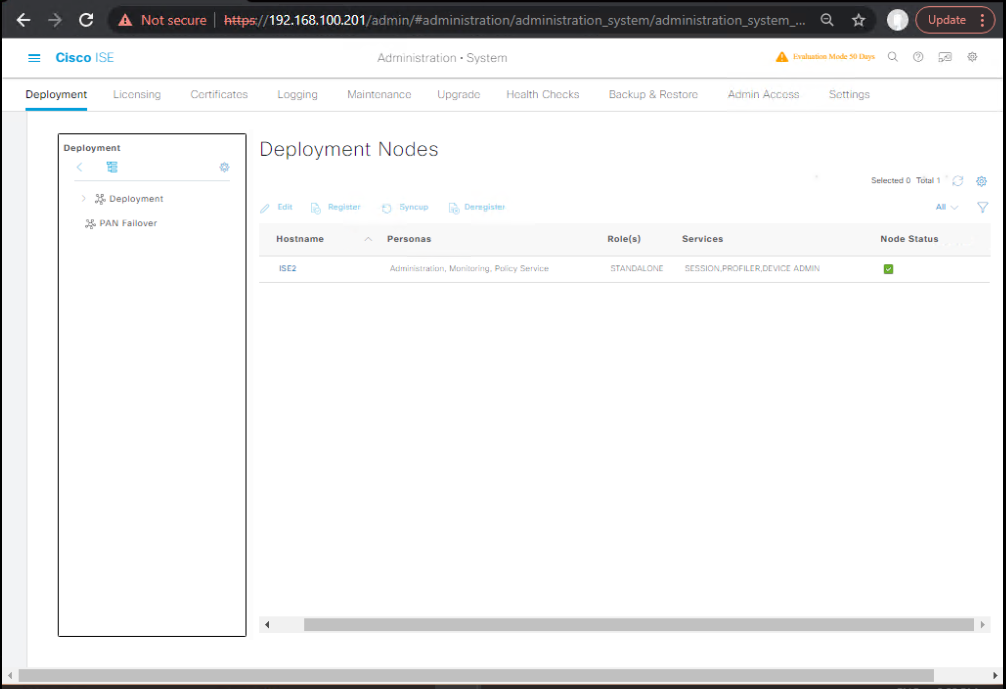
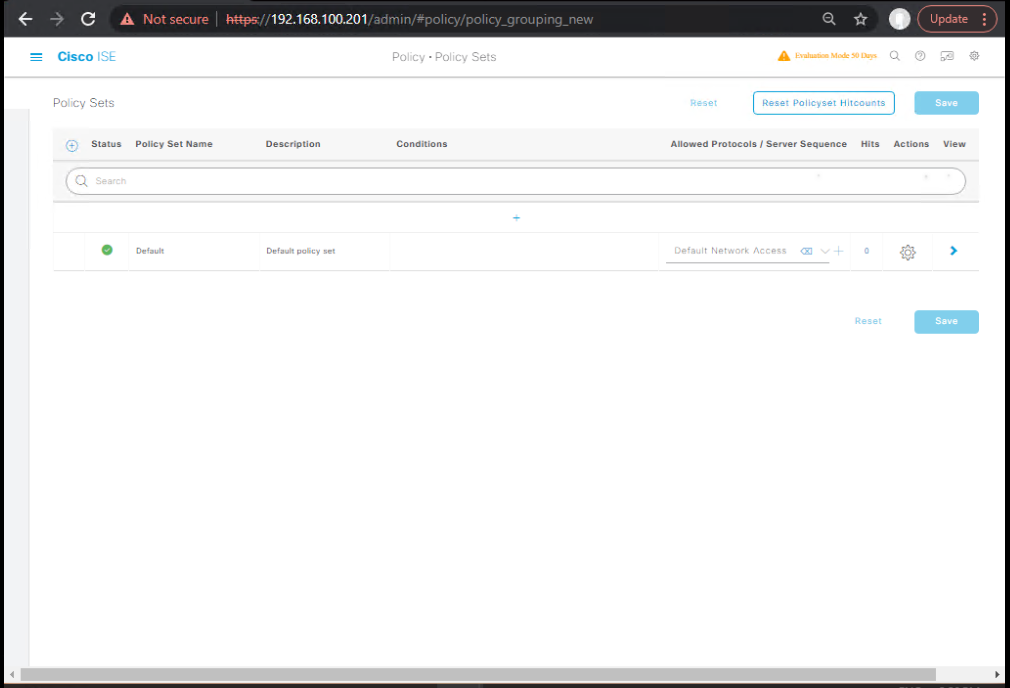
- Create an Auth Policy:
- Policy Sets → Wired_8021X → Authentication Policy
- If EAP-PEAP: Identity Store = AD Join Point
- [Screenshot: ISE Policy Set Screen]
- Configure Authorization Policy:
- Compliant machine → Full access VLAN
- Non-AD machine → Guest VLAN
- [Screenshot: ISE Authorization Rules]
Part B – Configure NAM Profile with Cisco Profile Editor
- Install Cisco AnyConnect Profile Editor (bundled with NAM module).
- Open Profile Editor → Select Network Access Manager.
- Create new Wired Profile:
- Connection Type: Wired
- Authentication Order: Machine → User
- EAP Method: PEAP or EAP-TLS
- Server Validation: Enable & import ISE certificate
- [Screenshot: NAM Profile Settings]
- Save profile as
Wired_8021X.xml.
Part C – Deploy NAM & Profile
- Install AnyConnect NAM module on the endpoint:
msiexec /i anyconnect-nam-win.msi /qn - Copy profile to:
C:\ProgramData\Cisco\Cisco AnyConnect Secure Mobility Client\Network Access Manager\newConfigFiles\ - Restart the NAM service:
net stop acnam && net start acnam
Part D – Switch Configuration
conf t interface Gi1/0/10 switchport mode access authentication port-control auto mab dot1x pae authenticator spanning-tree portfast
Part E – Validation
From Switch:
show authentication sessions interface Gi1/0/10 details
Look for:
- Authc Method: 802.1X
- User Name: host/<machine_name> for machine auth, DOMAIN\user for user auth
- Status: Authenticated
From ISE GUI:
- Operations → RADIUS → Live Logs → Verify EAP method and NAM as supplicant
- [Screenshot: ISE Live Logs Post-Auth]
FAQs – Cisco AnyConnect NAM for Wired Auth
1. What’s the main difference between Cisco AnyConnect NAM and the Windows Native Supplicant for wired 802.1X?
→ Windows Native Supplicant is basic and has limited EAP method support with minimal control over authentication order. NAM allows granular control over wired/wireless profiles, supports advanced EAP methods like EAP-TLS/EAP-FAST, and can enforce machine + user authentication sequencing reliably.
2. Can I use Cisco AnyConnect NAM for both wired and wireless authentication at the same time?
→ Yes. You can create multiple profiles within the same XML — one for wired interfaces, one for wireless SSIDs — and NAM will manage both. Just ensure there are no conflicting EAP methods between wired and wireless profiles.
3. How do I confirm NAM is actually being used instead of the default Windows supplicant?
→
- In ISE Live Logs, check the RADIUS attribute
Cisco-AVPairshowingclient-type=nam. - On the endpoint, check NAM logs in
C:\ProgramData\Cisco\Cisco AnyConnect Secure Mobility Client\Logs\nam.log. - Windows will also show the “Cisco Network Access Manager” service running.
4. Can NAM handle machine authentication before a user logs into Windows?
→ Yes. Configure chained authentication in the profile: Machine auth first (using computer certificate or AD account), then user auth after login. This ensures full network access for logon scripts and GPO application.
5. My NAM client is installed, but wired authentication is failing with “No Valid Server Certificate.” What’s wrong?
→ NAM requires server certificate validation against a trusted CA in the profile. You must import the ISE-issued (or public CA) certificate into the endpoint’s Trusted Root store and enable “Validate Server Certificate” in the profile editor.
6. Can I deploy NAM profiles remotely to 100s of endpoints without manual intervention?
→ Yes. Use SCCM, Intune, GPO, or pre-deployment AnyConnect packages. The XML profile goes into:
C:\ProgramData\Cisco\Cisco AnyConnect Secure Mobility Client\Network Access Manager\newConfigFiles\
Restart the NAM service after placing the profile.
7. Does Cisco NAM support fallback to MAB (MAC Authentication Bypass) if 802.1X fails?
→ NAM itself doesn’t trigger MAB — MAB is handled by the switch if no EAPoL frames are received from the client. If NAM is installed and running, it will always attempt 802.1X unless explicitly disabled for that interface.
8. How can I troubleshoot NAM authentication issues from the endpoint?
→
- Enable debug logging in NAM (
NAM.logandsystem.log). - Use
netsh lan show interfacesto check 802.1X state. - Verify switch logs with
debug dot1x all. - Cross-check ISE Live Logs for EAP failure reasons.
9. Can I use EAP-TLS with NAM for wired authentication without an AD domain join?
→ Yes, but you must manually install both the user and/or machine certificates on the endpoint and configure NAM to use them in the profile. Without domain join, you lose GPO-based automation.
10. If I uninstall NAM, will my endpoint revert to using the Windows Native Supplicant automatically?
→ Yes, but you must re-enable 802.1X in the Windows network adapter properties manually or via GPO. Otherwise, the endpoint will default to unauthenticated access (or MAB if the switch allows it).
YouTube Link
For more in-depth Cisco ISE Mastery Training, subscribe to my YouTube channel Network Journey and join my instructor-led classes for hands-on, real-world ISE experience
7. Closing Notes
Configuring Cisco AnyConnect NAM for wired authentication ensures consistent, secure, and centrally managed endpoint authentication in Cisco ISE deployments. NAM’s ability to handle machine + user auth and advanced EAP methods makes it an indispensable tool for enterprise NAC.
Fast-Track to Cisco ISE Mastery Pro
If you found this lab valuable, imagine mastering every Cisco ISE feature from beginner to CCIE Security level.
I’ve helped thousands of engineers crack ISE deployments in the real world. My 4-month Instructor-Led CCIE Security Mastery Program goes far beyond YouTube — it’s 100% hands-on, lab-focused, and aligned to real enterprise challenges.
- Live Sessions + Recordings
- Full Lab Access (VMware/EVE-NG-ready topologies)
- Certification Roadmap + Job Prep
Check the full course outline here → course.networkjourney.com/ccie-security
Secure your spot today and take your ISE skills from config to expert-level troubleshooting
Enroll Now & Future‑Proof Your Career
Email: info@networkjourney.com
WhatsApp / Call: +91 97395 21088
![[Day 32] Cisco ISE Mastery Training: Configuring Cisco AnyConnect NAM for Wired Auth](https://networkjourney.com/wp-content/uploads/2025/08/Day-32-–-Cisco-ISE-Mastery-Training-Configuring-Cisco-AnyConnect-NAM-for-Wired-Auth.png)


![Ticket#1-Enterprise Slowness: High CPU on Core Switch – Step-by-Step Troubleshooting [CCNP ENTERPRISE]](https://networkjourney.com/wp-content/uploads/2025/07/nj-blog-post-Ticket-1.jpg)