[Day 37] Cisco ISE Mastery Training: Wired Redirection for Non‑Compliant Devices
Table of Contents
Introduction
In the modern enterprise, it’s not enough to just authenticate a device — we must continuously ensure it complies with corporate policies. Cisco ISE’s Wired Redirection for Non-Compliant Devices enables you to catch endpoints that fail posture checks and redirect them to a remediation portal, without granting full network access.
This redirection capability is a cornerstone of advanced NAC because it combines security enforcement with a user-friendly workflow, ensuring endpoints can self-remediate without requiring IT to physically touch them.
For engineers, this lab is critical because it simulates a real-life enforcement flow — detecting a non-compliant wired client, pushing a redirection ACL via ISE, verifying the behavior in both switch CLI and ISE logs, and confirming that the client regains access after fixing the issue.
Problem Statement
In wired corporate networks, unmanaged or out-of-date devices can:
- Introduce malware
- Violate security baselines (missing patches, outdated antivirus, disabled firewalls)
- Create compliance risks for regulatory frameworks like PCI-DSS or HIPAA
Without redirection, these devices either get blocked entirely (frustrating for end-users) or are allowed in (risky for the business). Neither is ideal.
Solution Overview
Cisco ISE solves this by:
- Detecting posture status via the AnyConnect ISE Posture module or agentless posture methods.
- Applying a redirect ACL that limits traffic to the remediation portal and essential update servers.
- Guiding the user to self-remediate (e.g., update antivirus, install patches).
- Automatically re-evaluating posture and granting normal access when compliant.
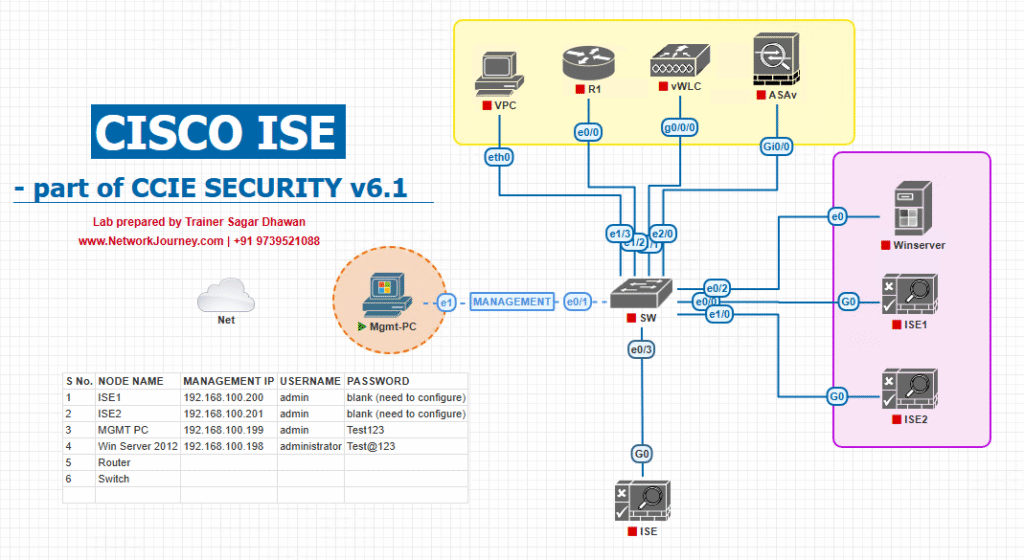
Sample Lab Topology
Lab Description:
We’ll simulate a wired endpoint failing posture, being redirected, fixing the issue, and regaining normal access.
- Platform: EVE-NG or VMware Workstation
- ISE: 3.2
- Switch: Catalyst 9300 (IOS-XE 17.x) or virtual CML switch
- Endpoint: Windows 10 + AnyConnect 4.10 with ISE posture module
- Optional Servers: WSUS or AV update server for remediation testing
Diagram Description:
Step-by-Step GUI Configuration Guide
Switch Configuration (CLI)
conf t ip access-list extended ACL-REDIRECT permit tcp any host <ISE_IP> eq 80 permit tcp any host <ISE_IP> eq 443 permit udp any any eq domain permit udp any any eq bootpc deny ip any any aaa new-model aaa authentication dot1x default group radius aaa authorization network default group radius aaa accounting update periodic 5 aaa accounting dot1x default start-stop group radius radius server ISE1 address ipv4 <ISE_IP> auth-port 1812 acct-port 1813 key cisco123 ip device tracking dot1x system-auth-control interface Gi1/0/10 switchport mode access authentication order mab dot1x authentication priority mab dot1x authentication port-control auto mab dot1x pae authenticator spanning-tree portfast
ISE GUI Steps
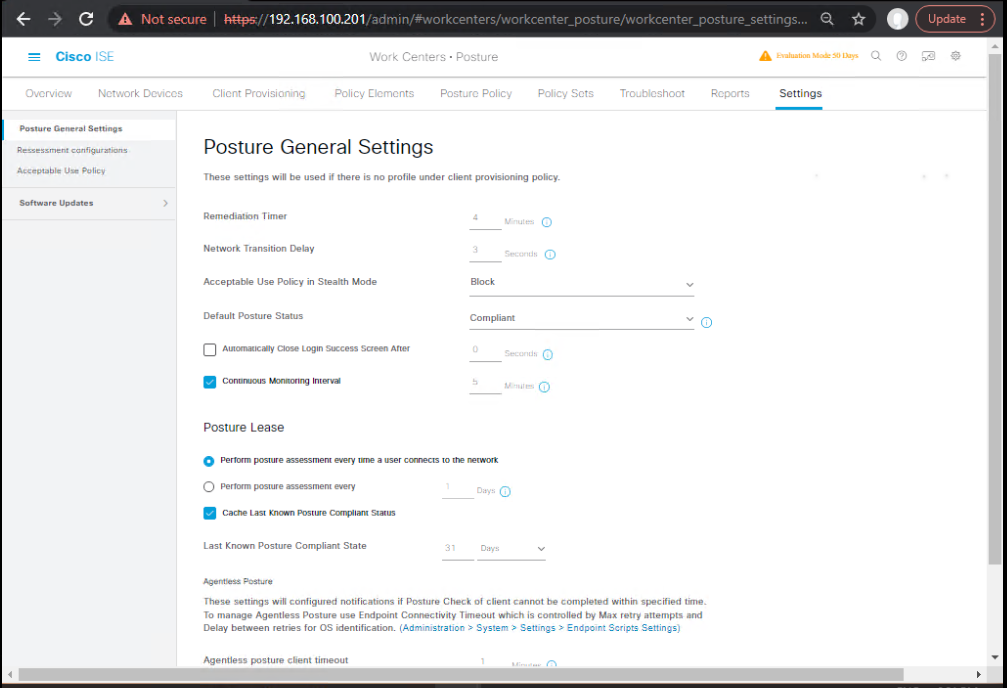
Step 1 – Enable Posture Services
- Go to Work Centers → Posture → Settings
- Enable posture and configure discovery hosts.
[Screenshot: ISE Posture Settings Screen]
Step 2 – Define Authorization Profiles
- Create Redirect_Profile:
- ACL:
ACL-REDIRECT(must match switch) - Redirect URL:
https://<ISE_IP>:8443/portal/PortalSetup.action?portal=Remediation
[Screenshot: ISE Authorization Profile Screen]
- ACL:
Step 3 – Configure Policy Sets
- Under Policy Sets, create posture condition:
- IF posture status = Non-Compliant
- THEN apply
Redirect_Profile
[Screenshot: ISE Policy Set Screen]
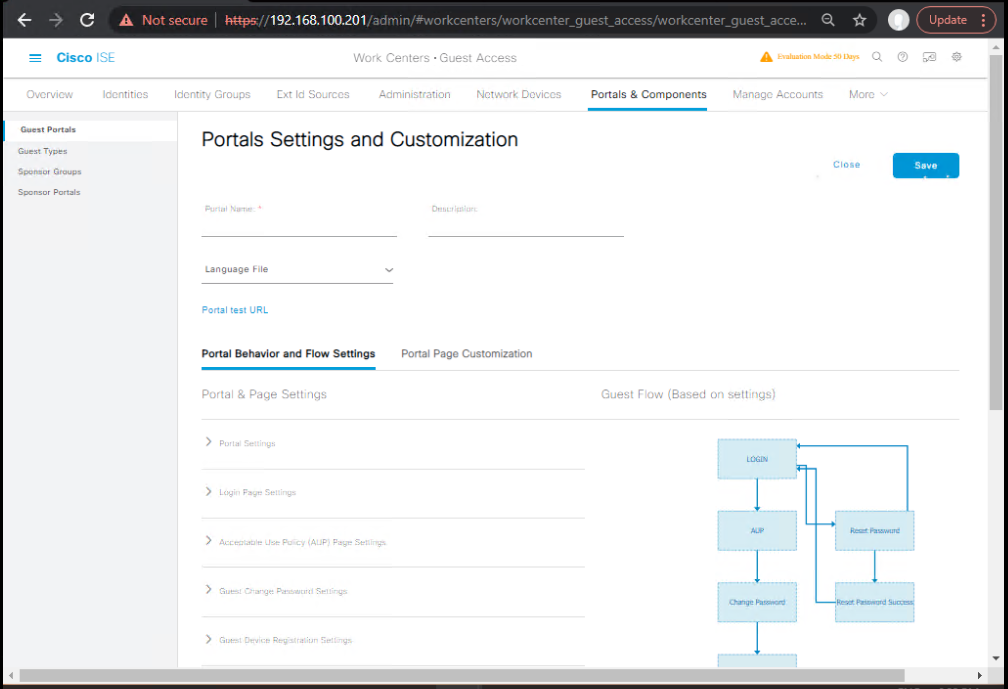
Step 4 – Remediation Portal Setup
- Work Centers → Guest Access → Portals & Components
- Create “Remediation Portal” with instructions for updating AV/patches.
[Screenshot: Remediation Portal Config]
Step 5 – Testing & Validation
CLI Check on Switch:
show authentication sessions interface Gi1/0/10 details
Look for:
Status: Authorized Domain: DATA ACS ACL: xACSACLx-IP-ACL-REDIRECT
ISE Live Logs Check:
- Operations → RADIUS → Live Logs: Verify redirection profile is pushed.
Endpoint Behavior:
- Open browser → Auto-redirects to remediation portal.
- Apply fixes → AnyConnect posture re-check → VLAN/dACL restored to full access.
FAQs
1. How does ISE detect that a wired device is non-compliant?
ISE uses posture assessment via the Cisco AnyConnect ISE Posture module or agentless methods. The posture policy checks endpoint status (antivirus, firewall, OS patch level, registry settings, etc.) against compliance rules defined in ISE. If the result is “Non-Compliant,” ISE triggers a redirection policy.
2. What is the difference between dACL redirection and VLAN redirection?
- dACL Redirection: Pushes a downloadable ACL to the switch that permits only specific traffic (e.g., to the remediation portal) while blocking everything else.
- VLAN Redirection: Moves the endpoint to a separate VLAN with limited access. dACL is preferred for less disruption.
3. Can this work without installing AnyConnect on endpoints?
Partially. Without AnyConnect posture module, you can redirect unknown devices, but you cannot perform full compliance posture checks. In that case, redirection is based only on MAC or authentication method, not actual posture status.
4. What happens if a user closes the browser during remediation?
The ACL remains in place until the endpoint passes a posture re-check. Closing the browser simply stops them from seeing the portal, but access is still restricted.
5. Does posture re-check happen automatically or manually?
By default, AnyConnect periodically re-checks posture automatically. You can also trigger an immediate check by clicking “Check Compliance” in the AnyConnect posture agent.
6. Can I give partial network access during redirection?
Yes. Your ACL can allow DNS, DHCP, and access to specific update servers (e.g., antivirus signature servers, Windows Update). This ensures the device can fix itself while staying isolated from production resources.
7. What’s the CLI command to see if a redirect ACL is applied?
On the switch:
show authentication sessions interface Gi1/0/10 details
Look for ACS ACL: xACSACLx-IP-ACL-REDIRECT or the ACL name you configured.
8. How do I troubleshoot if redirection doesn’t happen?
- Check that ip http secure-server is enabled on ISE.
- Confirm switch ACL name matches the one referenced in ISE Authorization Profile.
- Verify RADIUS CoA (Change of Authorization) is working (
debug radiuson switch). - Review ISE Live Logs for the session.
9. Can I integrate wired redirection with guest onboarding?
Yes. You can have a single redirection policy that detects either “Guest” or “Non-Compliant” and sends both to different portals using Portal Selection policies.
10. What happens if ISE is unreachable during a redirection scenario?
Behavior depends on your switch configuration:
- Critical VLAN → Endpoint is moved to a pre-configured VLAN.
- Fail-closed → Endpoint loses access entirely.
- Fail-open → Endpoint is allowed full access (not recommended for secure networks).
YouTube Link
For more in-depth Cisco ISE Mastery Training, subscribe to my YouTube channel Network Journey and join my instructor-led classes for hands-on, real-world ISE experience
Closing Notes
This lab demonstrates real-world NAC enforcement: detecting a non-compliant wired device, redirecting to remediation, and restoring access upon compliance.
The same workflow applies to guest onboarding and quarantine enforcement in enterprise production networks.
Fast-Track to Cisco ISE Mastery Pro
If you’re serious about mastering Cisco ISE and preparing for CCIE Security, now is the time to act.
I run a focused 4-month, 100% instructor-led CCIE Security Mastery Program — with deep-dive labs, EVE-NG topologies, and production-grade configs that go far beyond theory.
- Check the full course outline here: https://course.networkjourney.com/ccie-security/
- Seats are limited — secure your spot today and transform from ISE learner to ISE expert.
Enroll Now & Future‑Proof Your Career
Email: info@networkjourney.com
WhatsApp / Call: +91 97395 21088
![[Day 37] Cisco ISE Mastery Training: Wired Redirection for Non‑Compliant Devices](https://networkjourney.com/wp-content/uploads/2025/08/Day-37-Cisco-ISE-Mastery-Training-Wired-Redirection-for-Non‑Compliant-Devices.png)

![[Day 41] Cisco ISE Mastery Training: Wireless 802.1X Authentication Overview](https://networkjourney.com/wp-content/uploads/2025/08/Day-41-Cisco-ISE-Mastery-Training-Wireless-802.1X-Authentication-Overview.png)
![VPN 0 and VPN 512 in Cisco SD-WAN: Backbone & Management Explained[CCNP ENTERPRISE]](https://networkjourney.com/wp-content/uploads/2025/06/nj-blog-post-vpn0-vpn512.jpg)