[Day 124] Cisco ISE Mastery Training: Okta Identity Federation
Table of Contents
Introduction
In today’s enterprise world, the identity perimeter is no longer limited to Active Directory or on-prem LDAP directories. Organizations are adopting cloud-first strategies, and identity management is increasingly shifting to modern Identity Providers (IdPs) like Okta. Cisco ISE, being the policy brain of the network, needs to integrate with these IdPs to enforce Zero Trust, adaptive access, and context-aware policies.
By federating Cisco ISE with Okta, we enable seamless SSO (Single Sign-On) for network access, offloading identity management and multi-factor authentication to Okta, while ISE enforces device posture, profiling, and NAC policies. This integration becomes a cornerstone for enterprises that run hybrid-cloud, multi-IdP, and remote workforce environments.
Why does this matter?
Because without federation, you are stuck with siloed identities—cloud apps use Okta, while network devices rely on ISE’s internal database or Active Directory. This creates operational overhead, security blind spots, and compliance gaps. Federation with Okta transforms ISE into a cloud-extended policy enforcement engine, where authentication comes from Okta and authorization decisions are still enforced at the network layer by ISE.
This Article will not only show you how to configure Okta–ISE federation step by step (GUI + CLI) but also give you real-world enterprise use cases like:
- Enforcing MFA from Okta for VPN logins via ISE.
- Integrating Okta Universal Directory groups into ISE policy sets.
- Using Okta for partner/contractor BYOD authentication while employees still use AD.
This is where ISE meets the cloud, and mastering this makes you a true ISE architect.
Problem Statement (real-world challenges)
- Credential sprawl & lifecycle: Teams creating local accounts on ISE or NADs causes orphaned accounts and audit gaps.
- Weak or inconsistent MFA: NADs and VPNs need MFA but integrating heterogeneous systems is hard.
- Guest/onboarding UX vs security: You want simple SSO for guests and contractors while enforcing central policies (MFA, group rules).
- Multiple identity stores: AD, cloud IdP (Okta), contractor directories—keeping them in sync is painful.
- Admin access governance: Admin portal needs centralized SSO + MFA + RBAC (Okta can provide strong auth, groups, and device context).
Okta solves identity & MFA; ISE must consume the identity signals and enforce network policies consistently. That’s the integration problem we solve.
Solution Overview
We cover four practical integration patterns (each fully lab-testable):
- SAML SSO (Okta IdP) → ISE Guest & Sponsor Portals
- Okta is the SAML IdP; ISE is the SP. Users authenticate via Okta and ISE consumes the SAML assertion (username, email, groups) to create guest sessions or provision sponsor flows. (Cisco has a step-by-step for guest SAML with Okta.) (Cisco)
- SAML SSO → ISE Admin Portal (Admin SSO)
- Newer ISE releases support SAML for admin GUI login; Okta provides the IdP and optionally MFA. This centralizes admin authentication and enables RBAC mapping. (ISE 3.x supports admin SAML login flows.) (Cisco, Cisco Community)
- Okta as an External Identity Source (LDAP / LDAPS or Okta LDAP Interface)
- Use Okta’s LDAP interface or LDAPS to have ISE query Okta for group membership or authentication. This is useful when AD is not present or for contractor directories. (NSS Notes)
- Okta RADIUS Agent for MFA in 802.1X / VPN / ISE flows
Each pattern includes policy mapping in ISE (Authorization Rules) that uses Okta attributes (SAML assertions or LDAP attributes) to make access decisions (permit/quarantine/redirect).
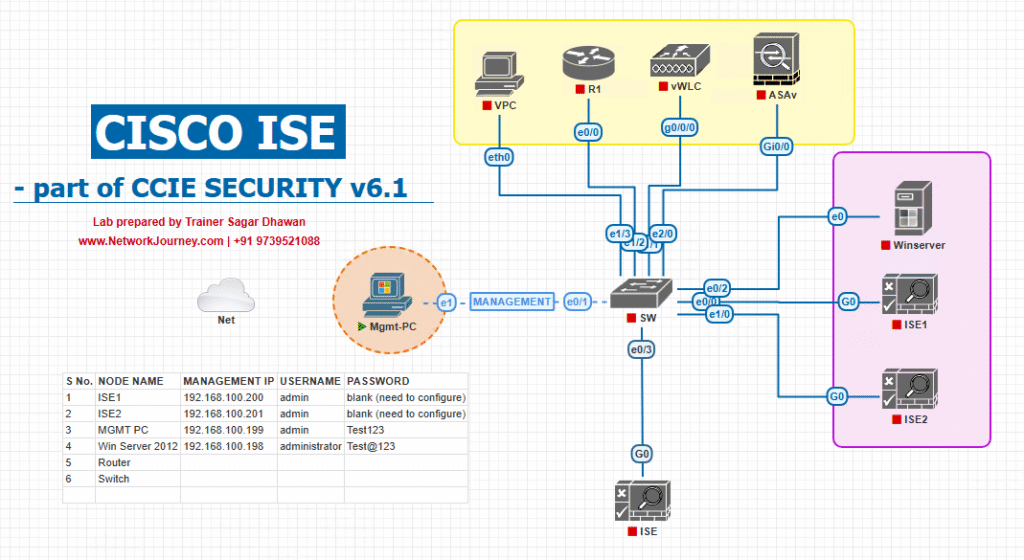
Sample Lab Topology
Platform: VMware for ISE (PAN/MnT/PSN), EVE-NG for NADs (Catalyst 9300, 9800 WLC), Windows Admin VM for Okta admin and Postman, optionally a Windows server for Okta RADIUS agent (if testing RADIUS agent on-prem).
Nodes & IPs (example):
- ISE PAN/MnT:
10.10.10.10 - ISE PSN (RADIUS):
10.10.10.11 - Catalyst 9300 (wired):
10.10.30.30 - WLC 9800-CL (wireless):
10.10.30.40 - Okta Admin Tenant: cloud (use dev Okta tenant)
- Okta RADIUS Agent VM:
10.10.20.20(Windows Server) - Admin PC (Postman/Browser):
10.10.40.10
Topology diagram:
Personas:
- Guest user (Okta SSO for guests), sponsor (sponsor approves), corporate user (Okta SSO for admin or via LDAP), VPN user (Okta RADIUS MFA via Okta RADIUS Agent).
Step-by-Step GUI Configuration Guide
A — Pre-checks & prerequisites
- ISE version: Use ISE 3.x (3.1/3.2+) where SAML admin login is supported.
ise/admin# show version. (Cisco) - Okta dev account: Create an Okta developer tenant (developer.okta.com).
- Browser & Postman: For metadata exchanges and SAML testing.
- Time sync & certs: Ensure ISE & NADs have correct time (NTP) and trusted certificates for TLS (SAML endpoints use HTTPS). CLI:
show ntp status.
B — Pattern 1: Configure SAML SSO for ISE Guest Portal (Okta as IdP)
Goal: Users click the Guest portal, are redirected to Okta, authenticate (with MFA), and return to ISE with a SAML assertion.
- Okta: Create SAML App for ISE
- Okta Console → Applications → Create App Integration → SAML 2.0General: Name
ISE-Guest-SAMLSingle sign on URL (ACS): copy from ISE SAML SP metadata later.Attribute Statements (example):NameID = user.email,firstName,lastName,groups(if you want groups in assertion).Save and View SAML setup → download IdP metadata (or copy IdP SSO URL & certificate).[Okta SAML App – Attribute statements]
- Okta Console → Applications → Create App Integration → SAML 2.0General: Name
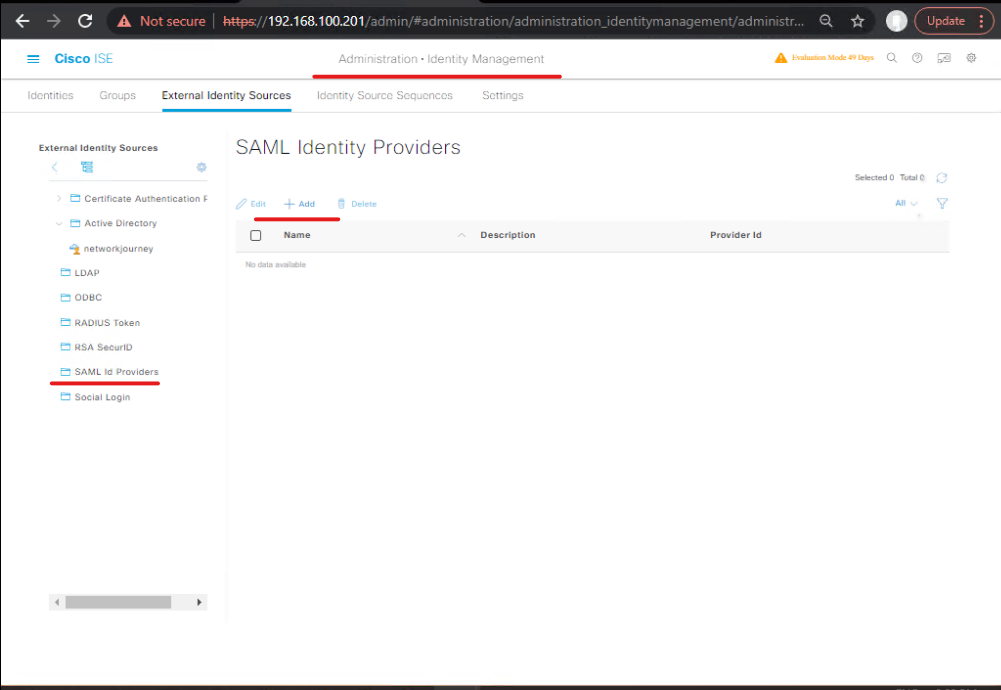
- ISE: Add SAML Identity Provider (SP-side)
- ISE GUI → Administration → Identity Management → External SAML Identity Sources → AddUpload the Okta IdP metadata (or paste SSO URL + certificate). Set Name:
Okta-Guest-IdP.Map SAML attributes to ISE username/email. Save.[ISE External SAML Add]
- ISE GUI → Administration → Identity Management → External SAML Identity Sources → AddUpload the Okta IdP metadata (or paste SSO URL + certificate). Set Name:
- Create Guest Portal referencing SAML IdP
- ISE: Work Centers → Guest Access → Portals & Components → Guest Portals → Create/EditUnder Authentication Source select
Okta-Guest-IdP.Save portal and Publish.[Guest Portal Auth Source]
- ISE: Work Centers → Guest Access → Portals & Components → Guest Portals → Create/EditUnder Authentication Source select
- Validation: Access https://ise-guest-portal-url as external user → redirected to Okta → authenticate (test with Okta MFA) → returned to ISE and given guest session. Check Operations → Guest → Live Logs for successful flow.
CLI/Logs to check (ISE):
ise/admin# show logging application ise-psc.log tail 50 # look for SAML assertions processed
Notes: If using groups in SAML assertions, create Authorization Rules that reference SAML group attributes in ISE to grant appropriate VLAN/dACL.
Citations: Cisco doc outlines SAML SSO integration for guest portal with Okta. (Cisco)
C — Pattern 2: Admin Portal SSO (Okta → ISE Admin login)
Goal: Admins use Okta SSO + MFA to log into the ISE Admin GUI.
- Okta: Create SAML App for ISE Admin
- Create SAML 2.0 app in Okta named
ISE-Admin-SAML. - Configure Assertion Consumer Service (ACS) using ISE Admin SAML SP URL (we will get from ISE). Configure attribute mappings as required (NameID=email or username). Optionally set
Groupsclaim for RBAC mapping.
- Create SAML 2.0 app in Okta named
- ISE: Configure SAML IdP for Admin Login
- ISE GUI → Administration → System → Admin Access → External SAML Identity Providers → Add (path varies by version).
- Upload Okta metadata from step 1. Map SAML NameID claim to Admin Identity. Save.
- [ISE Admin SAML Add]
- Map SAML group → Admin Group
- ISE: Administration → System → Admin Access → Admin Groups → create admin groups and map external SAML groups (from Okta) to ISE Admin Group (and Role). This gives RBAC for SAML users.
- Test: Log out of ISE, click Sign in with SAML or browse to admin SSO URL. Okta login and MFA should appear; after successful login you return to ISE with admin rights.

Validation:
- Operations → Admin Audit shows admin login via SAML and the SAML NameID.
- CLI:
show logging application ise-admin.log | include <username>.
Notes: Not all older ISE versions support Admin SAML — ensure your release does. (Cisco)
D — Pattern 3: Okta as External Identity Source (LDAP/LDAPS)
Goal: Use Okta’s LDAP interface so ISE can authenticate users and read group membership via LDAPS.
- Okta: Enable LDAP Interface (Okta LDAP Interface or LDAP Agent)
- Okta → Directory → LDAP Interface (Okta provides this feature for certain plans) or deploy Okta LDAP agent per Okta docs. Create a service account that ISE will use to bind (username + strong password). (NSS Notes)
- Note: Okta may require special configuration; follow Okta docs.
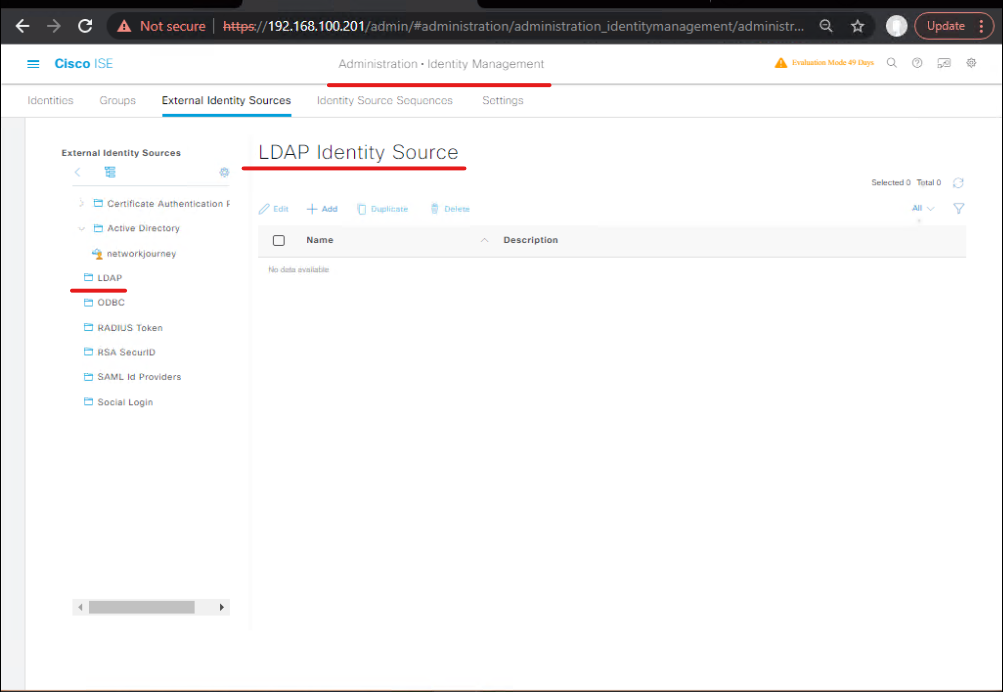
- ISE: Add Identity Source (LDAP/LDAPS)
- ISE GUI → Administration → Identity Management → External Identity Sources → LDAP → Add.
- Enter Okta LDAP endpoint (FQDN or IP) and Enable SSL (LDAPS). Import trust certificate if necessary (Okta LDAP cert).
- Configure base DN and attribute mappings (uid → sAMAccountName/email). Test connection and import groups/users.
- [ISE Add LDAP Identity Source]
- Identity Source Sequence (ISS)
- Configure ISS: Okta LDAP → Internal Users. Place Okta entry in the proper order so RADIUS authentication checks Okta first if desired.
Validation:
- Test authentication: create a user in Okta and attempt network authentication through ISE;
Operations → RADIUS → Live Logsshow authentication result. - CLI:
show ldap connection(ISE CLI) or check Live Logs for LDAP bind success.
E — Pattern 4: Okta RADIUS Agent (MFA) – ISE in the loop
Goal: Use Okta RADIUS agent to add Okta MFA into network authentication flows (802.1X, VPN). Two common topologies: (A) NAD → ISE → Okta RADIUS (ISE proxies to Okta) or (B) NAD → Okta RADIUS → ISE (Okta as upstream auth). We’ll focus on (A): ISE uses Okta RADIUS for secondary verification (or as an external RADIUS identity source).
- Okta: Configure RADIUS App
- Okta Admin → Applications → Add Application → RADIUS (or use Okta RADIUS agent on Windows Server) per Okta docs. Configure RADIUS shared secret and IP of the server that will send requests (ISE PSN IP). (Okta Docs)
- Okta RADIUS Agent (Windows): Install Okta RADIUS agent on a Windows server in your network; register it to your Okta tenant. Configure to accept requests from ISE IP and use the shared secret. See Okta docs for details. (IAMSE)
- ISE: Add Okta RADIUS as External RADIUS
- ISE GUI → Administration → Identity Management → External RADIUS → Add Okta RADIUS host(s) with the shared secret and optionally set Service Type (Authentication/Accounting).
- Alternatively, under Identity Sources → RADIUS add as Identity Source for ISS.
- ISE Authentication Policy
- Policy: On authentication, first check local / AD; if password check passes but second factor needed, forward/validate with Okta RADIUS (or accept Okta RADIUS response as primary MFA condition).
- Use ISE Authorization rules to check for
Okta-MFAattribute in the response and map to full access.
Validation:
- Authentication walk-through: attempt 802.1X login with username/password → Okta push MFA appears on user’s Okta app → approve → ISE receives RADIUS success and authorizes network access.
- ISE Live Logs show RADIUS request to Okta and the resulting attributes.
Notes: There are multiple valid topologies; confirm the one that matches your security posture.
F — Hardening & production considerations
- Certificates & trust: Use proper CA certs; install Okta CA certs if needed for LDAPS/HTTPS trust.
- SAML lifetime & replay: Use short assertion lifetimes; enable audience restrictions and sign/validate assertions.
- RBAC mapping: Map Okta group claims to ISE Admin Groups carefully (least privilege).
- Logging & monitoring: Enable ISE Live Logs + Admin audit; centralize to SIEM.
- Failover: Plan for IdP outage (local admin break-glass). Add local admin accounts and configure fallback authentication sequences.
Expert Level Use Cases
- Admin SSO + MFA + RBAC — Okta as IdP for ISE Admin portal, map Okta groups to ISE Admin Groups; require Okta MFA for high-privilege roles. (Test: break-glass local admin flow.)
- Guest captive portal SSO — Okta authenticates guests; ISE creates sponsored access using attributes returned via SAML; sponsor approvals routed to Okta groups for workflow.
- MFA for 802.1X & VPN — ISE proxies to Okta RADIUS agent for second-factor verification; create flow where password validated against AD and second factor via Okta. (Okta Docs)
- Okta LDAP for contractor identity — contractors managed in Okta LDAP Interface; ISE uses LDAPS for authentication & group membership for VLAN assignment. (NSS Notes)
- Device trust pass-through — Okta device trust claims included as SAML attributes; ISE uses them to enforce device posture on wired/wireless/VPN.
- Automated deprovisioning — Okta lifecycle event triggers ISE to remove network privileges or quarantine via API when account is deactivated.
- CI/CD for SAML apps — Automate Okta app creation & certificate rotation using Okta APIs; use automation to update ISE SP metadata and restart SSO tests.
- Hybrid flow — Use Okta as primary IdP and fallback to AD/LDAPS in ISE ISS for on-prem resilience; script failover test drills.
- SIEM correlation — correlate Okta SSO events with ISE authorization decisions in Splunk for threat hunting (e.g., admin SSO but unusual policy changes).
- Okta Device Trust + ISE Enforcement — combine Intune/Okta device attestations with Okta SSO claims to apply device-aware network policies in ISE.
Quick validation checklist
ISE CLI & GUI checks
# Verify ISE version ise/admin# show version # Tail PSC logs for SAML or Admin login issues ise/admin# show logging application ise-psc.log tail 100 # Admin audit (GUI): Operations -> Admin Audit
Okta checks
Use Okta System Log to validate assertions and MFA prompts.
Preview SAML assertion in Okta SAML app.
Confirm RADIUS agent logs show inbound request from ISE IP.
FAQs – Cisco ISE & Okta Identity Federation
Q1. How do I configure ISE to trust Okta as the SAML Identity Provider?
Steps:
- In Okta Admin Console → Applications → Create SAML App.
- Download the IdP metadata XML file.
- In ISE GUI → Administration → Identity Management → External Identity Sources → SAML IdPs.
- Click Add, upload the metadata XML.
- Save → Validate connection.
Validation:
- GUI: Go to Operations → RADIUS → Live Logs and check if authentication request redirects to Okta.
- CLI:
show logging application saml all
Q2. Which attributes must be passed from Okta to ISE for authorization policy mapping?
Common attributes:
uid(username)mail(email address)groups(Okta group membership)employeeTypeor custom attributes
Validation:
- GUI: After successful login, go to Operations → RADIUS → Live Logs → Authentication Details.
- Look at the Attributes Tab → confirm Okta attributes appear.
Q3. How do I enforce Okta MFA for AnyConnect VPN via ISE?
Steps:
- In Okta → enable MFA policies (Okta Verify, Push, SMS).
- Link MFA policy to the SAML app configured for Cisco ISE.
- In ISE → VPN Policy Set uses the SAML IdP for authentication.
Validation:
- Connect via AnyConnect → login with username/password.
- Okta will trigger MFA challenge → only after successful MFA does SAML assertion get sent to ISE.
Q4. Can I map Okta groups directly to ISE authorization profiles?
Yes.
- In Okta → Add user to group (e.g., “Contractors”).
- Ensure group membership is included in SAML assertion.
- In ISE → Policy Sets → Authorization Rules → Condition:
ExternalGroups CONTAINS Contractors. - Map to an Authorization Profile (e.g., limited VLAN).
Validation:
- GUI: Live Logs → Check “Matched Authorization Rule”.
- CLI:
show logging application ise-psc all
Q5. How do I integrate Okta for Guest/BYOD flows in ISE?
Steps:
- In ISE → Guest Access → Portal Settings → Authentication Source = SAML IdP (Okta).
- Configure Okta app to accept ISE portal as SP (Service Provider).
- Redirect guest login to Okta.
Validation:
- Guest connects → redirected to Okta login page.
- Successful login returns to ISE portal with SAML assertion.
Q6. What happens if Okta is unreachable during authentication?
Behavior:
- Default = fail-closed (user denied).
- Best Practice: Configure a fallback source in ISE → “If SAML fails → check AD/Local DB”.
Validation:
- Temporarily block Okta URL from ISE.
- Test login → confirm fallback method triggers.
Q7. Can I use Okta for ISE Admin Logins (RBAC)?
Yes.
- Configure Okta → new SAML app for ISE Admin Access.
- In ISE → Administration → Admin Access → Authentication Method → SAML IdP.
- Map Okta groups → ISE Admin Roles (e.g., Read-Only, SuperAdmin).
Validation:
- Login to ISE GUI → Okta login page appears.
- Successful login → check ISE GUI → Top-right corner → Admin Role shown.
Q8. How do I troubleshoot SAML authentication failures between Okta and ISE?
CLI Debug:
ise/admin# show logging application saml all ise/admin# debug saml trace
GUI Debug:
- Operations → Live Logs → Failure Reason (e.g., “Invalid Assertion” or “Audience Mismatch”).
Common issues: - Metadata not updated.
- Wrong Entity ID or ACS URL.
- Clock skew between ISE & Okta (check NTP).
Q9. Can I use Okta + ISE for TACACS+ Device Admin (network device logins)?
Yes.
- Configure Okta groups for Network Admins, Operators.
- Map Okta groups → ISE TACACS+ Shell Profiles + Command Sets.
- Use Okta SAML as identity source for TACACS+.
Validation:
- Login to switch with TACACS+.
- GUI: Live Logs → check “Authorization Result = TACACS Shell Profile: Network-Admin”.
Q10. Does ISE support Just-In-Time (JIT) user provisioning from Okta?
No direct JIT sync. Instead:
- ISE consumes SAML assertions dynamically.
- Users don’t need pre-creation in ISE.
- Policies are applied based on attributes received during authentication.
Validation:
- Create new user in Okta → assign to group.
- Attempt login → even though user doesn’t exist in ISE DB, ISE enforces policy from SAML assertion.
YouTube Link
For more in-depth Cisco ISE Mastery Training, subscribe to my YouTube channel Network Journey and join my instructor-led classes for hands-on, real-world ISE experience
Closing Notes
- Pick the right pattern: SAML for portals & admin SSO, LDAPS/LDAP for attribute queries, RADIUS agent for MFA—don’t mix unless your design demands it.
- Test in a lab with IdP dev tenant before production. Use short assertion lifetimes and strict audience/recipient checks.
- Monitor & log: centralize SAML & admin audit logs into SIEM. Keep break-glass accounts and a tested failover plan.
- This masterclass equips you to move from “IdP proof-of-concept” to a hardened, auditable Okta ↔ ISE federation architecture.
Upgrade Your Skills – Start Today
“For more in-depth Cisco ISE Mastery Training, subscribe to my YouTube channel Network Journey and join my instructor-led classes.”
Fast-Track to Cisco ISE Mastery Pro — I run a focused 4-month instructor-led course (TrustSec, pxGrid, ISE APIs, Intune, Okta SSO, TACACS+, SIEM integrations).
Course outline & enroll: https://course.networkjourney.com/ccie-security/
Enroll Now & Future‑Proof Your Career
Email: info@networkjourney.com
WhatsApp / Call: +91 97395 21088



