[Day 125] Cisco ISE Mastery Training: Azure AD Cloud Integration
Table of Contents
Introduction
Integrating Cisco Identity Services Engine (ISE) with Microsoft Entra ID (formerly Azure AD) brings your network access control into the cloud identity era. Instead of relying only on on-prem AD or local accounts, you can:
- Authenticate and authorize network users (or admins) using Azure credentials and group membership.
- Use SAML/OAuth for admin SSO, REST-ID (ROPC) or certificate-based flows for user authorization tied to Azure AD groups, and SCIM for provisioning where supported.
- Combine ISE’s NAC policy engine with Entra ID’s identity, group, and device signals to implement consistent Zero-Trust access controls across wired, wireless and VPN.
This Article goes beyond overview — you’ll build the lab, register Azure apps, configure ISE (SAML IdP + REST ID / TEAP/EAP-TLS flows), validate with both GUI and CLI, and troubleshoot real issues you’ll hit in production. (Cisco)
Problem Statement
Real world challenges this integration solves:
- No single source of truth for user/group data: many orgs have cloud identity (Entra) and on-prem AD — mapping both into NAC is hard.
- Lack of centralized admin SSO & RBAC: admins and sponsors want to use corporate SSO and group-based RBAC for ISE GUI access.
- Guest / BYOD / contractor flows require consistent group attributes to drive authorization profiles across locations.
- Cloud device posture & conditional access: Microsoft Conditional Access or Intune device signals need to be respected in NAC decisions.
- Automated provisioning / deprovisioning: HR or IT systems change identities in Entra — you want those changes reflected in access policy without manual steps.
ISE + Entra ID integration reduces manual mappings and provides programmatic/standard ways (SAML, REST, SCIM) to use cloud identity within NAC. (Cisco, Microsoft Learn)
Solution Overview (how ISE addresses it)
High-level integration methods you’ll use in this masterclass:
- SAML IdP (Admin GUI SSO / External IdP): Configure Entra as a SAML IdP so administrators (and optionally end-users for captive portals) log into ISE using Azure credentials. ISE can export SP metadata and you upload to Azure. (Cisco Secure Access, Cisco)
- REST ID (ROPC) for group retrieval / user auth (ISE 3.0+): ISE’s REST Auth service (REST ID) uses the OAuth ROPC flow to authenticate users against Azure AD and retrieve group membership at authentication time. Useful when you must evaluate Azure AD groups during EAP-TLS/TEAP or VPN flows. Note: ROPC has important limitations (does not support MFA interactive flows) — test and design accordingly. (Cisco, Cisco Live)
- SCIM provisioning (where supported): For Cisco cloud services (Secure Access / Secure Connect etc.) you can use Entra’s provisioning (SCIM) to push users/groups to Cisco cloud apps. SCIM is standard (RFC 7644) and works well for cloud products; on-prem ISE typically uses REST ID / SAML rather than SCIM. (Microsoft Learn, Cisco Secure Access)
- Certificate-based flows (EAP-TLS/TEAP + Azure group evaluation): ISE 3.2+ supports certificate inner-auth combined with Azure AD group evaluation to authorize TLS-based wireless authentication based on Azure group claims. (Cisco)
Sample Lab Topology
Lab can be done on VMware ESXi/Workstation or EVE-NG.
Text topology (recommended IPs for lab):
- ISE PAN (VM):
10.20.1.10(Admin GUI/API) — ISE 3.2+ recommended - ISE PSN (VM):
10.20.1.11(Policy services) - WLC (virtual or physical) or Meraki:
10.20.1.20(captive portal / 802.1X) - Access Switch (Catalyst/NX-OSv):
10.20.1.5 - Guest/Client (laptop with 802.1X client): DHCP on VLAN 100 (192.168.100.0/24)
- Admin workstation (Postman/curl/Python):
10.20.1.100 - Azure Entra ID (cloud tenant) — you must have an admin account and ability to create App Registrations / Enterprise Applications (Tenant ID required).
Diagram:
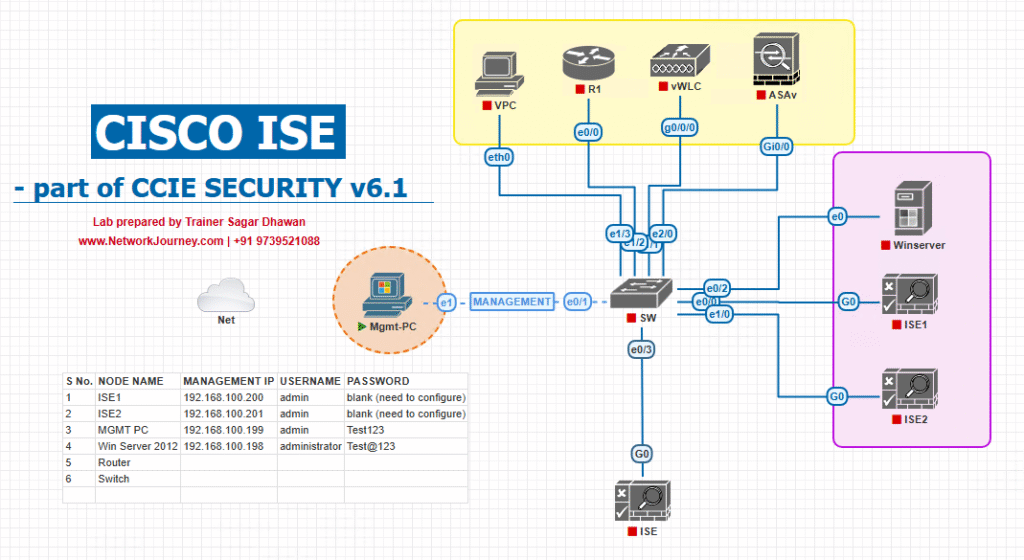
Notes:
- Ensure your lab network (or NAT) allows ISE to reach
https://login.microsoftonline.com/andhttps://graph.microsoft.com/for REST/ROPC and group claims. - If you want device posture + Intune signals, include a Microsoft Intune managed device in the lab (optional).
Step-by-Step GUI Configuration Guide
A — Azure (Microsoft Entra ID) prep — App Registration / Enterprise App
Objective: create app(s) that ISE will use for SAML (SSO) and for REST ID (ROPC + group retrieval).
1 — Create App Registration for REST ID (ROPC / Graph access)
- Login to Azure Portal → Microsoft Entra ID → App registrations → New registration.
- Name:
ISE-REST-ID-ROPC - Supported account types: choose as per tenant.
- Register → copy Application (client) ID and Directory (tenant) ID.
[Validation] Copy Client ID and Tenant ID to text file.
(This follows the ISE REST ID guide.) (Cisco)
- Name:
- Certificates & secrets → New client secret → create secret (copy value — you’ll need it in ISE). (Cisco)
- Authentication → Advanced settings → Treat application as a public client / enable ROPC support. (This toggle is needed for the ROPC flow in Azure.) (Cisco)
- API permissions → Add a permission → Microsoft Graph → Application permissions → add
Group.Read.All(or GroupMember.Read.All as recommended). Then Grant admin consent. (Graph permissions are needed to fetch group membership.) (Cisco)
2 — Enterprise Application for SAML SSO (Admin GUI SSO)
- In Azure Portal → Enterprise applications → + New application → choose Create your own application → name:
ISE-SP-SAML. - Single sign-on → Choose SAML → upload ISE Service Provider metadata (you’ll export SP metadata from ISE in later steps). Configure Identifier (Entity ID) and Reply URL per ISE SP metadata. Configure claims (NameID = user.userprincipalname). Assign a test admin user to the app. (Cisco Secure Access)
B — ISE prep — SAML (Admin SSO) + REST ID (Azure)
Important: Work in this order — create App(s) in Azure first, then configure ISE.
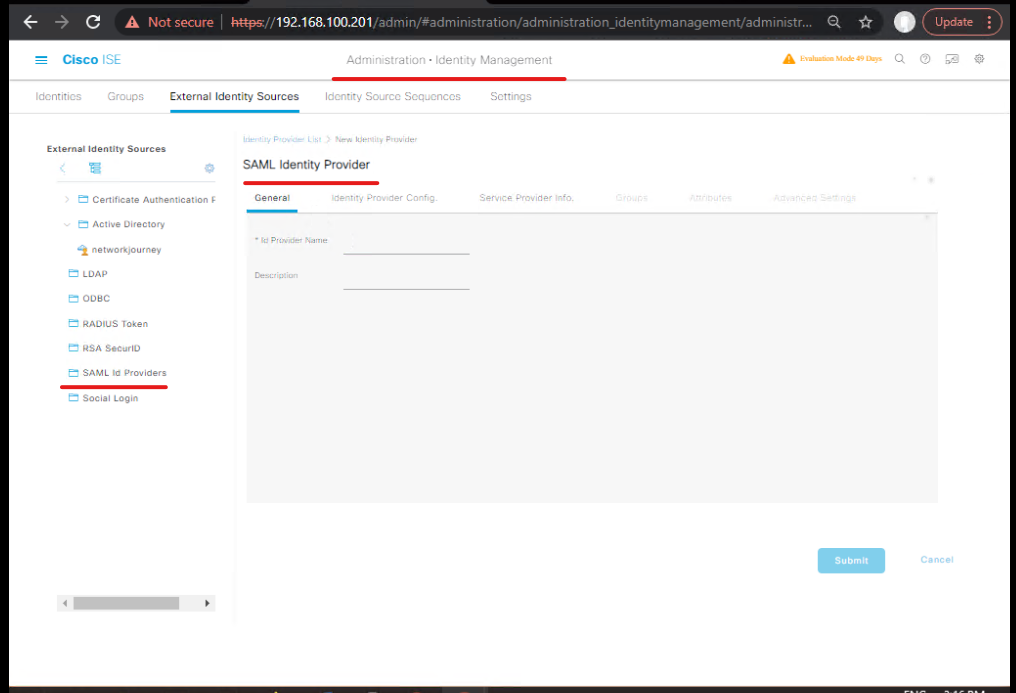
1 — Export ISE SP metadata (so Azure can trust ISE)
- ISE GUI: Administration → Identity Management → External Identity Sources → SAML Id Providers → Add (General tab: give a name), then click Service Provider Info → Export to get SP metadata XML. Save it. (Cisco)
2 — Configure Azure SAML SSO using exported SP metadata
- In Azure Enterprise App (ISE-SP-SAML) → Single sign-on (SAML): Upload SP metadata (from previous step). Configure required claims and set SAML Signing Certificate as appropriate.
- Copy the IdP metadata (Azure provided) or SAML signing cert for ISE. (Cisco Secure Access)
3 — Add SAML Id Provider in ISE and link to portal/admin access
- ISE GUI: Administration → Identity Management → External Identity Sources → SAML Id Providers → Add.
- Fill IdP name, upload IdP metadata (from Azure), set assertion mappings (NameID → username). Save. (Cisco)
- Make SAML an authentication option for admins: Administration → System → Admin Access → Authentication → set
Password Based→ choose the new SAML IdP from Identity Source drop-down (this ties admin login to Entra ID). (Cisco)
Validation — SAML admin SSO
- Open ISE admin GUI in private browser. Click SSO or try to login using the Entra ID test admin user assigned earlier. You should be redirected to Azure and back to ISE.
- ISE GUI: Administration → System → Admin Access → Administrators → Admin Audit to verify SAML login events. (Cisco)
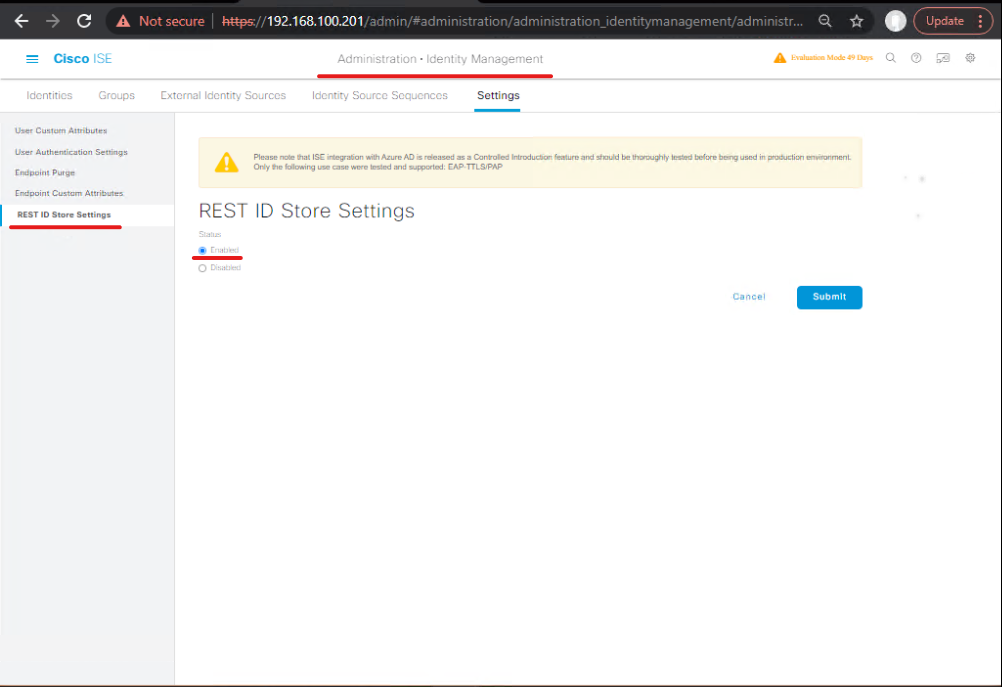
4 — Enable REST Auth Service in ISE (ROPC support) — critical for group retrieval at auth time
ISE default: REST ID (REST Auth Service) is disabled; enable and configure before adding REST ID store.
ISE GUI steps
- Administration → Identity Management → Settings → REST ID Store Settings → Enable → Submit. (Service will start across nodes; allow a few minutes). (Cisco)
- Administration → Identity Management → External Identity Sources → REST (ROPC) tab → Add.
- Name:
Azure-REST-ID - Client ID: (from Azure App Registration)
- Client Secret: (from Azure)
- Tenant ID: (Azure Tenant ID)
- Username suffix (if users will supply short names): set suffix to
@yourtenant.onmicrosoft.comor use UPN. - Click Test connection (ISE will call Azure token endpoint and validate).
- Click Load Groups — this will fetch group list into ISE external groups dictionary. (Cisco)
- Name:
Validation — REST ID
- In ISE GUI: Administration → Identity Management → External Identity Sources → REST (ROPC) → you should see the store and groups loaded.
- CLI check: SSH to ISE node and run:
show application status iseconfirmREST Auth Service(REST Auth Service/REST ID) is running. (Cisco)
5 — Build Identity Store Sequence and Authentication Policy
- Administration → Identity Management → Identity Source Sequences → Add → create a sequence that includes
Azure-REST-ID(or a sequence where Azure REST ID is checked for required flows). Save. (Cisco) - Policy → Authentication: Add rules that forward the appropriate EAP inner methods to the REST ID store — e.g., EAP-TTLS (PAP) or TEAP/EAP-TLS inner mapping as required by ROPC constraints. Cisco documents list supported inner auth methods because ROPC requires password be available at ISE (or you must use certificate inner methods where group queries are still possible). Change Process Failure default action from DROP to REJECT for REST flows to avoid PSN marking dead on failures. (Cisco)
- Policy → Authorization: In rules where you match external groups (REST ID groups) set the Authorization Profile (VLAN, ACL) accordingly. Use
All Dictionary → External Groupsto select groups loaded from Azure. (Cisco)
Validation — Authentication / Authorization
- Client test 1 (EAP-TTLS/PAP sample): Attempt to authenticate with a user/password that exists in Entra. On success: check Operations → RADIUS Live Logs — you should see the authentication flow, group retrieval and the Authorization Profile applied. (Cisco)
- Client test 2 (EAP-TLS/TEAP certificate): Authenticate using a client cert. If the authorization policy uses Azure groups (via REST ID), verify groups were retrieved and mapped to result. Check RADIUS Live Logs for
External Groupattributes.
6 — Optional: SCIM provisioning (for Cisco Cloud / Secure Access)
- If your target is a Cisco cloud app (e.g., Cisco Secure Access / Secure Connect), you can enable SCIM provisioning from Entra by creating an Enterprise App, setting Provisioning → Automatic, and entering the SCIM Tenant URL and Secret Token supplied by Cisco cloud portal. Test connection. SCIM will push users/groups to the Cisco app. Note: SCIM is for Cisco cloud products — on-prem ISE uses REST ID / SAML. (Microsoft Learn, Cisco Secure Access)
Validation — SCIM
- Azure Enterprise App → Provisioning → Provisioning logs show successful sync. Cisco cloud portal shows provisioned users/groups. (Microsoft Learn)
7 — Troubleshooting checklist (quick GUI + CLI checks)
- ISE: REST Auth Service enabled?
Administration → Identity Management → Settings → REST ID Store Settings. CLI:show application status ise. (Cisco) - Azure: Client secret copied, API permissions granted (Group.Read.All) and Admin consent given. Token config includes group claims. (Cisco)
- ISE Policy: Identity Store Sequence assigned to Authentication policy; Authorization policy referencing external groups. Check Process Failure default action changed to REJECT for REST flows. (Cisco)
- Logs: Use Operations → RADIUS Live Logs and Administration → System → Admin Audit for SAML admin SSO events. (Cisco)
Expert Level Use Cases
Case1: Validate: Remove group in Entra → ISE logs show authorization change → Access revoked.
BYOD onboarding using Entra group-based VLAN assignment
Steps: Enroll device certificate, use TEAP/EAP-TLS, REST ID to fetch user’s Entra groups, map to VLAN in Authorization profile.
Case2: Validate: RADIUS Live Logs show group match → VLAN assigned.
AnyConnect VPN auth using Azure SAML + ISE for dACLs
Steps: Use Azure SAML for VPN SSO (interactive + MFA), then forward user attributes to ISE for policy application.
Case3: Validate: VPN successful + ISE shows SAML assertion + correct dACL applied.
Hotel / Campus provisioning: SCIM to Cisco cloud + ISE guest mapping
Steps: SCIM sync of users to Cisco Secure Access (cloud), generate guest tokens, integrate with ISE for campus Wi-Fi.
Case4: Validate: Azure provisioning logs + Cisco cloud users list + ISE guest auth.
Temporary contractor accounts with automated expiry
Steps: Provision account in Entra, REST ID picks up group change, ISE policy maps to limited access role; use Azure lifecycle workflows to remove group to revoke access.
FAQs – Cisco ISE with Azure AD Cloud Integration
1. Q: How is Azure AD integration different from on-premises Active Directory integration in Cisco ISE?
A:
- On-prem AD: ISE uses LDAP/Kerberos to directly query domain controllers. Requires line-of-sight connectivity.
- Azure AD: No Kerberos/LDAP. Instead, ISE integrates via SAML or OIDC federation → Azure AD acts as the Identity Provider (IdP), ISE acts as the Service Provider (SP).
- Validation:
- GUI: Administration → Identity Management → External Identity Sources → SAML IdPs.
- Run test login → should redirect to Microsoft login page.
- CLI:
show logging application samlfor authentication debug.
2. Q: Do I need Azure AD Premium (P1/P2) for Cisco ISE integration?
A:
- For basic SAML federation, any Azure AD edition works.
- For Conditional Access Policies, MFA, Risk-based Authentication, you need Azure AD Premium P1/P2.
- Validation:
- Azure Portal: Azure AD → Licenses → All products.
- Try enforcing MFA → if blocked, subscription level is the reason.
3. Q: How do I test if SAML metadata exchange between ISE and Azure AD is working?
A:
- After configuring federation:
- Download ISE SP metadata from:
https://ISE-PAN-FQDN:8443/portal/SAMLMetadata - Import into Azure AD Enterprise App.
- Download Azure AD IdP metadata (XML) and upload into ISE.
- Download ISE SP metadata from:
- Validation:
- GUI: In ISE → SAML IdPs, metadata status should show valid.
- CLI:
show application samlconfirms loaded IdP entity ID and cert.
4. Q: My test login redirects to Microsoft but fails after authentication. Why?
A:
- Common causes:
- Entity ID mismatch (ISE SP name must match Azure AD app ID).
- Wrong redirect URI (must exactly match ISE portal URL).
- Certificate trust issue.
- Validation:
- GUI: Operations → RADIUS Live Logs → Look for
SAML assertion validation failed. - CLI:
show logging application saml→ check reason (invalid audience,signature mismatch).
- GUI: Operations → RADIUS Live Logs → Look for
5. Q: Can I map Azure AD groups to ISE authorization policies?
A:
- Yes. Azure AD returns group claims in the SAML assertion.
- In ISE, you must map claim values to ISE attributes under Identity Source Sequences.
- Validation:
- Run test login, download SAML assertion (use browser SAML tracer extension).
- Confirm group claim values appear → then in ISE, check Live Logs → Authentication Details → Attributes → Group claim.
6. Q: Does ISE support Azure AD as an IdP for both wired/wireless access and guest portals?
A:
- Yes:
- Wired/Wireless: Use ISE SAML redirection flow for authentication.
- Guest Portals: You can configure Azure AD as IdP for external user onboarding.
- Validation:
- Connect endpoint to SSID → should redirect to Microsoft login page.
- After success, Live Logs should show authentication source = Azure AD SAML IdP.
7. Q: How do I troubleshoot “No SAML Response received” errors?
A:
- Possible issues:
- Firewall/NAT blocking HTTPS redirect from Azure AD.
- Wrong FQDN in ISE (must be externally reachable).
- Clock skew between ISE and Azure (must be <5 mins).
- Validation:
- CLI:
show ntp→ confirm time sync. - Browser dev tools → check if POST to
/portal/SAMLResponseis happening. - ISE logs: Look for missing assertion entry.
- CLI:
8. Q: Can I enforce MFA for Azure AD logins through ISE?
A:
- Yes, if Azure AD Conditional Access policy requires MFA, it triggers before returning SAML assertion to ISE.
- ISE itself doesn’t enforce MFA but consumes the result.
- Validation:
- Enable CA policy → log in to SSID → Azure AD prompts MFA.
- Live Logs in ISE → Authentication passed with Azure AD → Success.
9. Q: Can I use Azure AD Join (Intune-managed) device compliance in ISE authorization?
A:
- Yes, via Intune + ISE pxGrid integration.
- Azure AD provides user identity, Intune provides device compliance status, ISE uses both for policy.
- Validation:
- In ISE: Work Centers → Posture → Compliance → Intune Connector.
- Live Logs: Authorization matched based on
Intune:Compliant = TRUE.
10. Q: How do I monitor or debug SAML integration logs in ISE?
A:
- GUI: Operations → Reports → Authentication → SAML Authentication.
- CLI:
show logging application saml show logging application ise-psc - Export SAML assertion using browser SAML-tracer plugin for deep debugging.
- Cross-check timestamps in ISE vs Azure AD sign-in logs (Azure AD → Monitoring → Sign-ins).
YouTube Link
For more in-depth Cisco ISE Mastery Training, subscribe to my YouTube channel Network Journey and join my instructor-led classes for hands-on, real-world ISE experience
Closing Notes — Key takeaways
- Plan flows first: decide which use case needs SAML (interactive SSO), REST ID (runtime group lookup), or SCIM (provisioning). Mix methods where needed. (Cisco Secure Access, Cisco)
- ROPC is powerful but limited — it is suitable when non-interactive password authentication and group retrieval are required, but it cannot satisfy MFA interactive requirements. Test for latency & failure modes. (Cisco, Cisco Live)
- Enable REST Auth Service in ISE and test early — use the
Test connectionandLoad groupsbuttons and verify via GUI &show application status ise. (Cisco) - For cloud provisioning, use SCIM for Cisco cloud apps; for on-prem ISE, rely on REST ID and SAML. (Microsoft Learn, Cisco Secure Access)
Upgrade Your Skills – Start Today
For deeper Cisco ISE Mastery, subscribe to Network Journey on YouTube and join the instructor-led classes. I run a focused 4-month instructor-led CCIE/ISE track — the course funnel and outline are at: https://course.networkjourney.com/ccie-security/.
Enroll to get lab topologies, step-by-step video walkthroughs, and the POC scripts used in this masterclass.
Enroll Now & Future‑Proof Your Career
Email: info@networkjourney.com
WhatsApp / Call: +91 97395 21088



![DevNet Sandboxes Overview – Test, Learn, Automate Without Fear! [CCNP ENTERPRISE]_networkjourney](https://networkjourney.com/wp-content/uploads/2025/07/DevNet-Sandboxes-Overview-–-Test-Learn-Automate-Without-Fear-1.png)