[Day 36] Cisco ISE Mastery Training: Multi-Domain Authentication (Voice + Data VLAN)
Table of Contents
Introduction
In modern enterprise environments, a single Ethernet port often serves two devices simultaneously:
- An IP phone (using the Voice VLAN)
- A user endpoint like a PC or laptop connected through the phone’s internal switch port (using the Data VLAN)
Multi-Domain Authentication (MDA) enables these two devices to authenticate independently using 802.1X or MAB, ensuring role-based access control while maintaining proper VLAN segmentation.
Without MDA, your security posture weakens — either the phone gets unauthenticated access or the PC rides on the same VLAN without compliance enforcement.
Cisco ISE integrates seamlessly with MDA to:
- Authenticate both devices separately
- Apply correct VLANs (voice/data) dynamically
- Enforce posture/security policies for the data VLAN user without affecting voice traffic
Problem Statement
When a switchport connects to both an IP phone and a PC:
- If authentication is per-port, the PC can bypass security using the phone’s session.
- Voice devices may be blocked or delayed if strict NAC rules are applied to both.
- Network segmentation for voice QoS and user security becomes impossible without per-device policies.
Result: Security gaps, VLAN leaks, compliance failures, and poor VoIP quality.
Solution Overview
Cisco ISE + Catalyst Switch MDA:
- Per-domain authentication: Voice devices authenticate in the voice domain, PCs in the data domain.
- VLANs are dynamically assigned per device based on ISE Authorization Profiles.
- IP phones often use MAB (OUI-based), while PCs use 802.1X/EAP-TLS.
- Ensures zero VLAN hopping and correct QoS tagging for voice traffic.
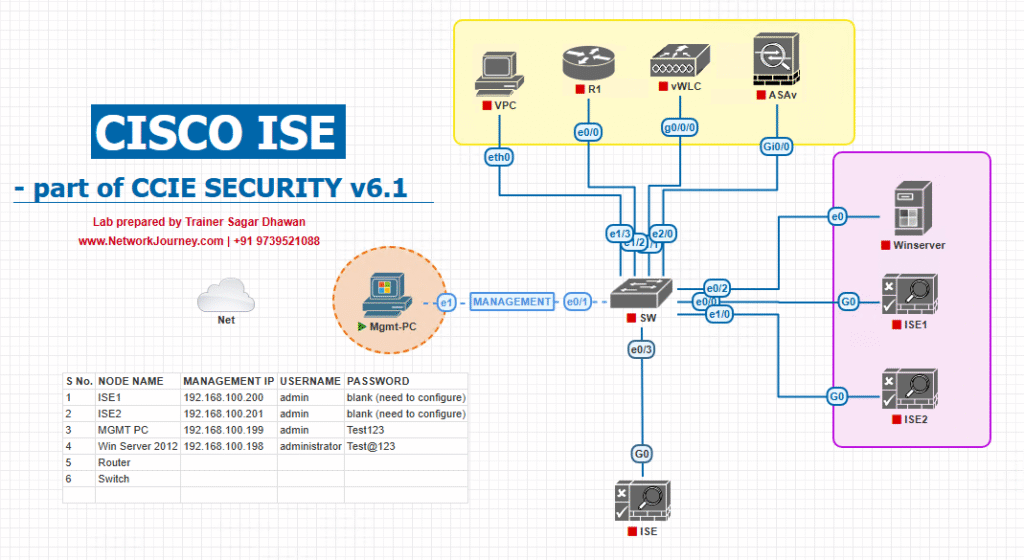
Sample Lab Topology
Lab Components:
- Platform: VMware/EVE-NG
- Cisco ISE: v3.x (Policy Node + Admin Node)
- Switch: Catalyst 9300/3650 (IOS-XE 16.x) in EVE-NG or physical
- Endpoints:
- Cisco IP Phone 88xx/79xx series (or simulated via MAB MAC)
- Windows 10 PC with AnyConnect NAM for 802.1X
- AD Server for user authentication
Topology Diagram:
Step-by-Step GUI Configuration Guide
A. Switch CLI Configuration for MDA
! Enable AAA aaa new-model aaa authentication dot1x default group radius aaa authorization network default group radius ! Define RADIUS Servers radius server ISE1 address ipv4 10.10.10.10 auth-port 1812 acct-port 1813 key C1sc0ISE ! Interface MDA config interface Gi1/0/10 switchport mode access switchport voice vlan 20 authentication host-mode multi-domain authentication order mab dot1x authentication priority mab dot1x authentication port-control auto mab dot1x pae authenticator spanning-tree portfast
B. ISE GUI Configuration
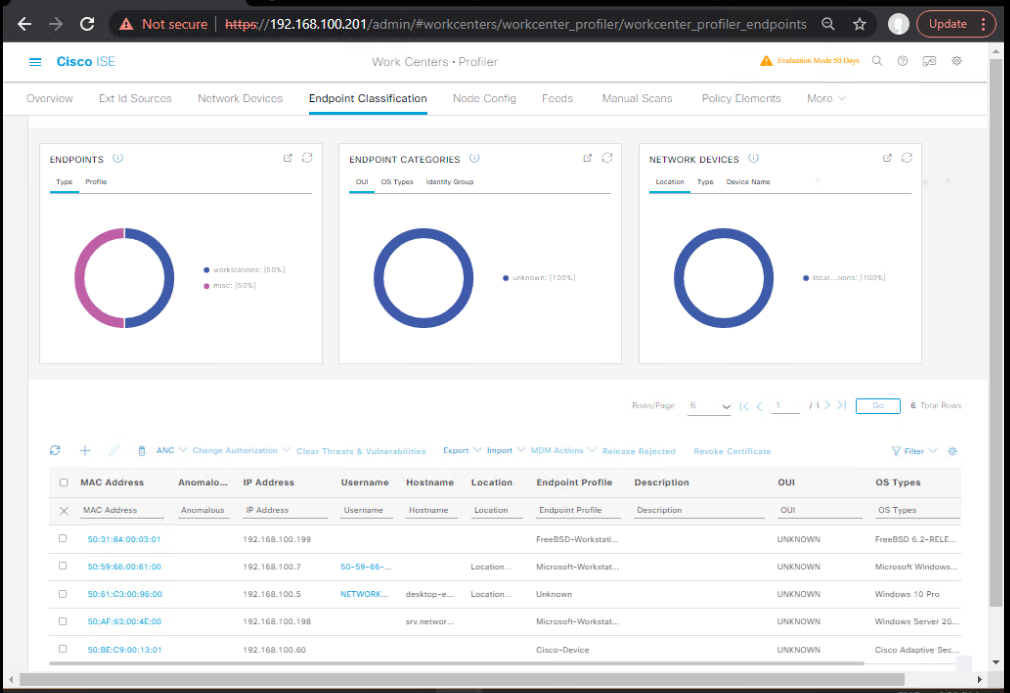
Step 1 – Add IP Phone OUI to Endpoint Identity Group
- Work Centers → Profiler → Endpoint Identity Groups
- Create group:
IP_Phones - Add condition:
OUI CONTAINS 00:1B:54(example Cisco phone OUI)
[Screenshot: Endpoint Identity Group Creation]
Step 2 – Create Authorization Profiles
- Voice AuthZ Profile:
- Name:
VOICE_VLAN_20 - VLAN: 20
- DACL: Permit voice services
- QoS marking optional
- Name:
- Data AuthZ Profile:
- Name:
DATA_VLAN_30 - VLAN: 30
- Apply posture policy if needed
- Name:
[Screenshot: AuthZ Profile Screen]
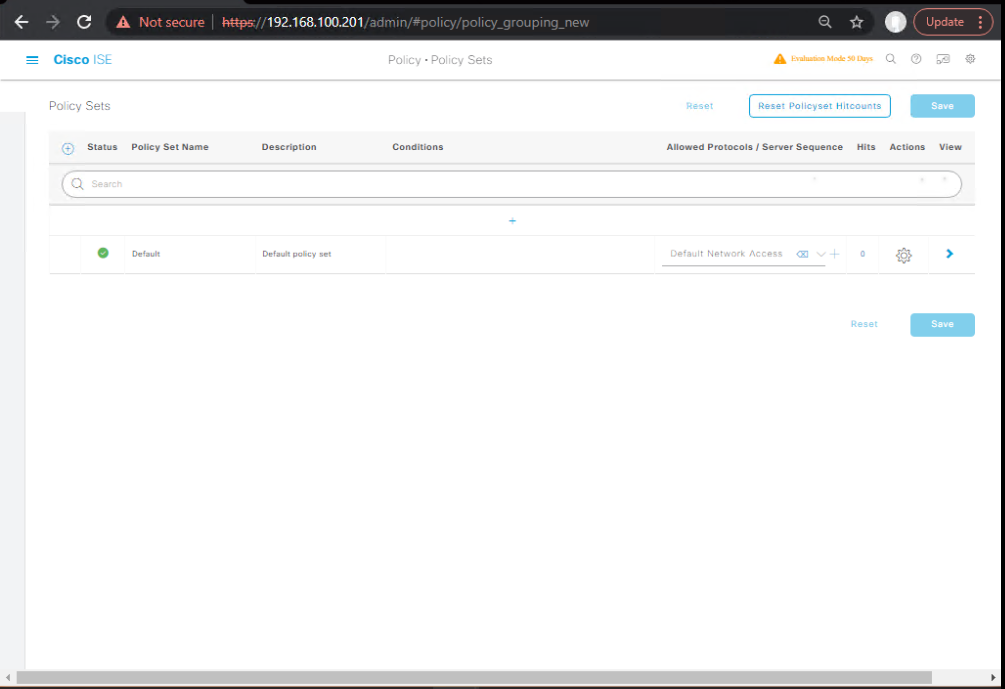
Step 3 – Create Policy Set
- Go to Policy → Policy Sets
- Create new Policy Set:
MDA-Voice-Data - Conditions:
- Voice Domain: IF
EndpointGroup == IP_PhonesTHENVOICE_VLAN_20 - Data Domain: IF
Wired_802.1X_EAP-TLSTHENDATA_VLAN_30
[Screenshot: Policy Set Screen]
- Voice Domain: IF
Step 4 – Test Authentication
- Connect IP phone → Should authenticate via MAB, get VLAN 20
- Connect PC through phone → Should authenticate via 802.1X, get VLAN 30
FAQs – Multi-Domain Authentication
1. What is the main difference between MDA and Multi-Auth?
- MDA allows exactly one voice device in the voice domain and one data device in the data domain on a single port.
- Multi-Auth allows multiple authenticated devices in the data domain only — no separate voice domain.
2. Can an IP phone and PC use the same VLAN in MDA?
- Technically yes, but it defeats the purpose of MDA. Best practice is to assign a dedicated voice VLAN for QoS and security, and a separate data VLAN for endpoints.
3. How does ISE differentiate between a phone and a PC?
- Via profiling methods: OUI MAC database, CDP/LLDP info, DHCP fingerprinting. Most Cisco phones advertise
device-type=IP Phonein CDP/LLDP packets.
4. What happens if the IP phone fails authentication?
- If MAB for the voice domain fails, the phone won’t get the voice VLAN and calls will fail. The PC can still attempt authentication in the data domain independently.
5. Which authentication method should be used for IP phones?
- Most deployments use MAB for phones (fast, low-touch). Some organizations enforce 802.1X EAP-TLS on newer phones for higher security.
6. Can I apply posture assessment to phones in MDA?
- Not recommended — posture assessment is designed for user endpoints. Phones are usually exempted from posture to avoid call disruption.
7. How do I verify MDA is working on the switch?
Run:
show authentication sessions interface Gi1/0/10 details
You should see two sessions:
- One with
Domain: VOICE - One with
Domain: DATA
8. How do I check in ISE that both domains are authenticated?
- Go to Operations → RADIUS → Live Sessions and search for the switch port. You should see two separate RADIUS sessions tied to the same interface.
9. What VLAN is assigned if the PC fails authentication?
- It depends on your policy:
- Critical VLAN if configured (for failed auth but essential connectivity)
- Guest VLAN if unauthenticated users are allowed
- Or port remains blocked if strict NAC is enforced
10. Does MDA work with downloadable ACLs (dACLs)?
- Yes. You can push separate dACLs for the voice and data domains from ISE. For example, voice domain may only allow SIP/RTP, while data domain follows corporate policy.
YouTube Link
For more in-depth Cisco ISE Mastery Training, subscribe to my YouTube channel Network Journey and join my instructor-led classes for hands-on, real-world ISE experience
Closing Notes
Multi-Domain Authentication is critical in environments where IP phones and PCs share the same access port. With proper ISE policies, you can:
- Maintain VLAN isolation
- Enforce security per device
- Preserve QoS for voice
- Keep compliance posture checks intact for data users
Fast-Track to Cisco ISE Mastery Pro
Ready to master Cisco ISE in real-world deployments?
I run a focused 4-month, instructor-led CCIE Security Mastery Program that takes you from foundations to advanced production-grade designs — with live labs, 40+ hands-on scenarios, and 1:1 mentoring.
Seats are limited. Reserve yours now at course.networkjourney.com/ccie-security and start building the NAC skills that top network security engineers use daily
Enroll Now & Future‑Proof Your Career
Email: info@networkjourney.com
WhatsApp / Call: +91 97395 21088

![The Ultimate IPv6 Troubleshooting Guide: Tools, Tips, and Labs [CCNP ENTERPRISE]](https://networkjourney.com/wp-content/uploads/2025/07/nj-blog-post-ipv6-troubleshooting-guide.jpg)
![[Day 42] Cisco ISE Mastery Training: Integrating Cisco WLC for Wireless Access Control](https://networkjourney.com/wp-content/uploads/2025/08/Day-42-Cisco-ISE-Mastery-Training-Integrating-Cisco-WLC-for-Wireless-Access-Control.png)
![OSPFv3 Configuration – The IPv6 Way[ CCNP ENTERPRISE ]](https://networkjourney.com/wp-content/uploads/2025/06/OSPFv3-Configuration-–-The-IPv6-Way_networkjourney.png)