[Day 40] Cisco ISE Mastery Training: End-to-End Wired Authentication Lab Validation
Table of Contents
Introduction
In Cisco ISE deployments, lab validation is not just a “nice to have” — it’s the only way to confirm that your authentication policies work exactly as intended before you deploy them in production.
End-to-end wired authentication lab validation means verifying every step of the authentication workflow:
- Supplicant configuration (Windows/macOS/Linux)
- Switch 802.1X control plane
- RADIUS request/response flow
- ISE policy matches and authorization results
Skipping this validation step is like building a bridge without a load test — it might look fine, but the moment traffic flows, cracks appear. Today, we’re going beyond theory — performing hands-on validation using both ISE GUI and switch CLI.
Problem Statement
Many engineers configure wired authentication in Cisco ISE, see “Success” on one test device, and assume all is well.
In reality:
- A policy mismatch might still allow some devices through in “Monitor Mode” without enforcing security.
- Certificates might be valid on one OS type but fail on another.
- Switchports might silently default to MAB when EAP packets drop.
- Timeouts and VLAN assignments might work in one VLAN but fail in another.
Without full end-to-end lab validation, these issues reach production and cause either:
- Security holes (bypass of NAC enforcement), or
- Access outages (critical devices losing network).
Solution Overview
Cisco ISE’s Live Logs, Live Sessions, RADIUS Diagnostics, and Endpoint Identity Groups combined with switch CLI session checks provide a full chain of visibility.
We validate:
- Supplicant sends EAPOL-Start
- Switch relays authentication to ISE
- ISE matches correct policy set
- RADIUS Access-Accept returns correct authorization profile
- Switch applies ACL/VLAN/DACL dynamically
- Session stays active and re-authenticates when needed
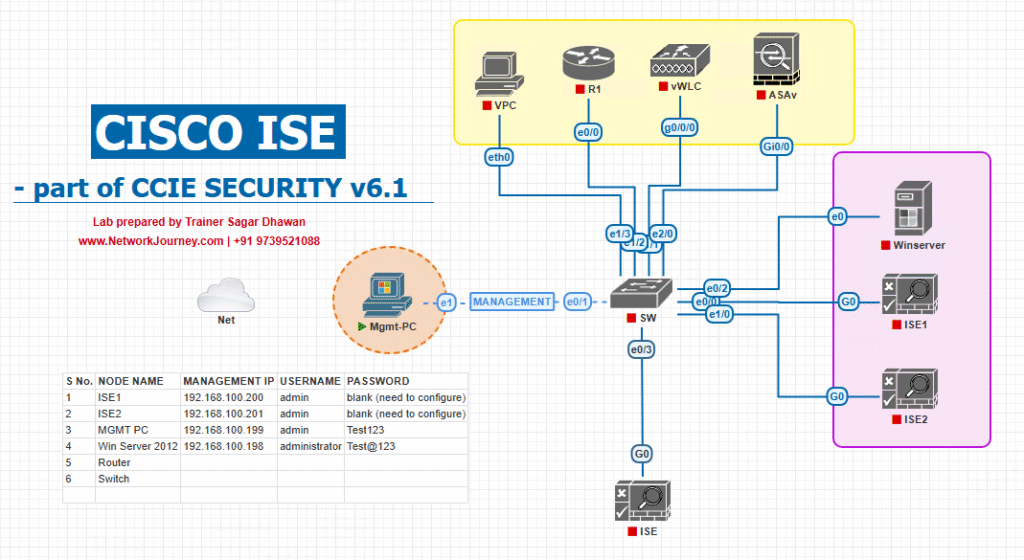
Sample Lab Topology
Text Description:
- Platform: VMware ESXi or EVE-NG
- ISE: Cisco ISE 3.x VM (2 vCPU, 16GB RAM)
- Switch: Catalyst 9300 (EVE-NG or physical)
- Endpoints:
- Windows 10 wired supplicant
- macOS wired supplicant
- Linux wired supplicant
- Connectivity: Switch uplink to ISE, endpoints in access VLAN with 802.1X enabled.
Diagram Description:
Step-by-Step GUI & CLI Validation Guide
Step 1 – Check Switchport Authentication Status
show authentication sessions interface Gi1/0/10 details
Look for:
Status: Authc SuccessMethod: dot1xVLAN: 20(matches ISE authorization profile)
Step 2 – Verify ISE Live Logs
- Navigate to:
Operations → RADIUS → Live Logs
[Screenshot: ISE Live Logs Success Entry]
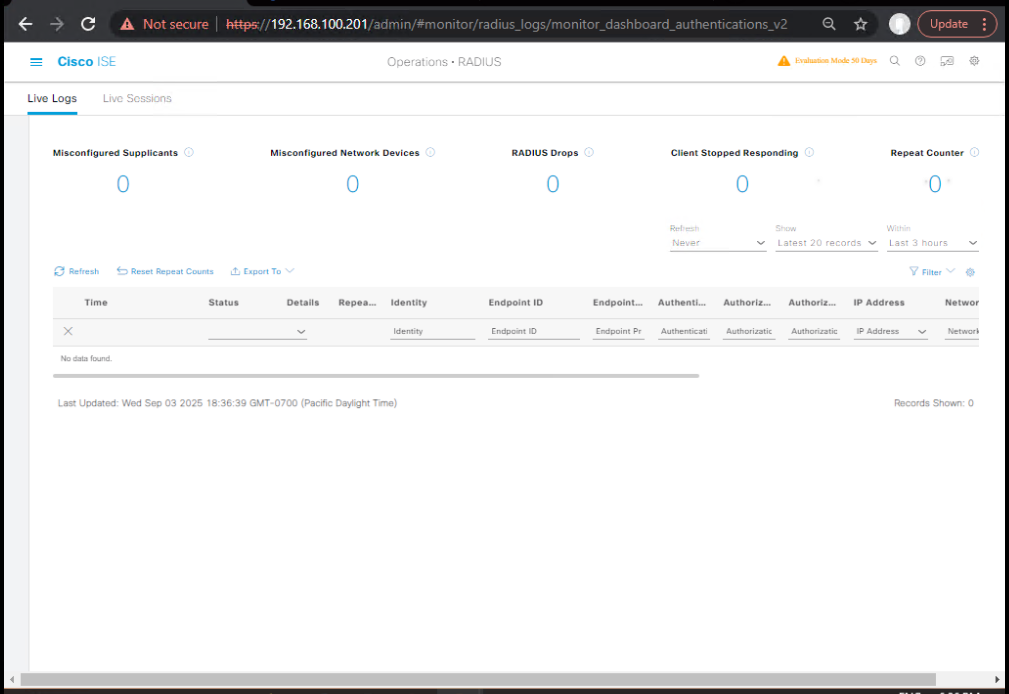
- Confirm:
- Authentication method (EAP-TLS, PEAP)
- Policy Set name matched
- Authorization Profile applied
Step 3 – Check ISE Live Sessions
- Go to:
Operations → RADIUS → Live Sessions
[Screenshot: ISE Live Sessions Active State]
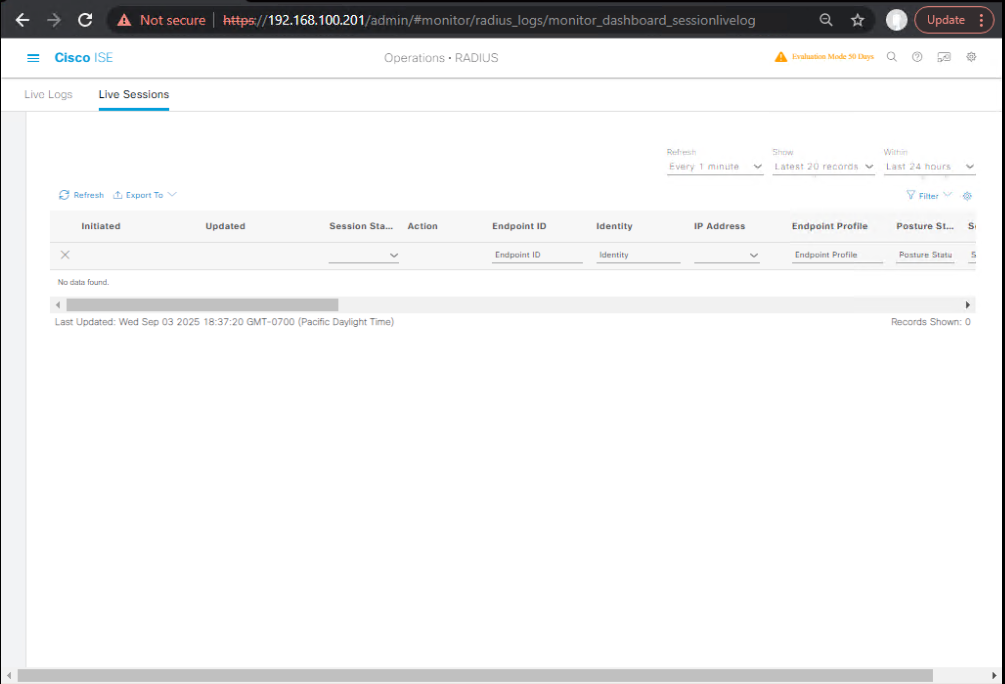
- Verify:
- Active session for each endpoint
- Endpoint MAC, IP, and assigned VLAN/DACL
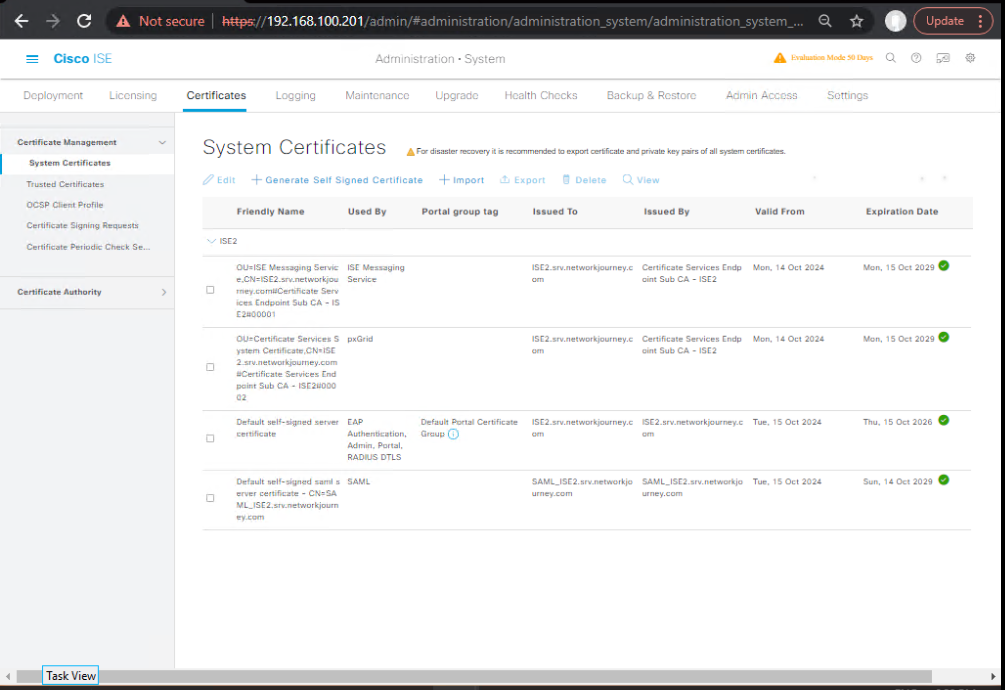
Step 4 – Verify Certificate Authentication
For EAP-TLS:
- Go to Administration → Certificates → Certificate Management → System Certificates
- Ensure CA cert is trusted and endpoint cert is valid.
- From endpoint:
openssl s_client -connect ise.domain.com:443 -showcerts
Confirm the CA chain.
Step 5 – Force Re-Authentication
On switch:
clear authentication session interface Gi1/0/10
Re-check Live Logs for EAPOL start and Access-Accept.
Step 6 – Test Authorization Profile Enforcement
- Change the user group in AD or ISE Endpoint Identity Group.
- Disconnect/reconnect endpoint.
- Confirm new VLAN/DACL applied via:
show authentication sessions interface Gi1/0/10 details
Step 7 – Negative Testing
- Intentionally fail authentication (wrong password/cert).
- Confirm ISE returns Access-Reject and switch moves to Restricted VLAN.
- [Screenshot: ISE Live Logs Failure Reason]
Step 8 – Multi-OS Validation
- Test on Windows, macOS, and Linux to ensure policy hits are consistent.
- Review logs for each OS in ISE.
Step 9 – Log Export
From ISE:
Operations → Reports → RADIUS Authentication → Export for audit.
Step 10 – Final Health Check
On switch:
show access-session show run | section interface Gi1/0/10
On ISE:
Administration → System → Logging → Log Configuration to ensure future troubleshooting is possible.
FAQs
1. Why does my switch show “Authc Success” but ISE Live Logs don’t have an entry?
Answer: This happens when the session was already authenticated earlier and is cached in the switch’s session table. The switch does not re-trigger RADIUS unless you clear the session:
clear authentication session interface Gi1/0/x
Then check Live Logs again.
2. My ISE policy hits for Windows but fails for macOS/Linux. What’s different?
Answer: Different OSes have different 802.1X supplicant defaults.
- Windows uses PEAP-MSCHAPv2 unless changed.
- macOS often defaults to EAP-TLS if a certificate exists.
- Linux depends on wpa_supplicant config.
Match your policy conditions accordingly.
3. How do I confirm if a DACL from ISE is actually enforced on the switch?
Answer:
- Run:
show authentication sessions interface Gi1/0/x details
Look for IPv4 ACL Name: <dacl_name>
2. Verify ACL existence:
show ip access-lists <dacl_name>
If not present, the switch didn’t download it — check RADIUS and CoA logs.
4. Why does MAB fallback trigger even when my device supports 802.1X?
Answer: Likely due to EAP timeout or supplicant not sending an EAPOL-Start. Increase timers on the switch:
dot1x timeout quiet-period 5 dot1x timeout tx-period 10
Ensure supplicant is enabled before the port comes up.
5. How do I see the exact ISE policy rule matched for a session?
Answer: In ISE Live Logs, click the timestamp → Details → Steps tab.
It shows each policy condition check and where it matched/fell through.
6. My VLAN assignment from ISE works for some users but not others. Why?
Answer: Common reasons:
- Switchport is not in
switchport mode access. - VLAN is not present or allowed on uplinks.
- Voice VLAN conflict (if IP phone connected).
Verify switch config and trunking.
7. How can I test certificate expiry enforcement in ISE?
Answer:
- Issue a short-lived cert (1–2 days) from your CA.
- Assign it to the endpoint.
- Wait for expiry and force re-authentication.
ISE will fail EAP-TLS if cert is expired.
8. Why is my ISE showing “RADIUS Request Dropped” during testing?
Answer: Usually due to:
- Incorrect RADIUS shared secret
- Mismatched source interface on switch
- Missing network device entry in ISE
Run:
show run | include radius-server
and verify ISE Network Devices config.
9. Can I validate authentication without kicking live users off?
Answer: Yes. Use an unused switchport for testing. Or set the port in Monitor Mode (authentication open) to log auth attempts without enforcement.
10. What’s the fastest way to export my validation results for audit or training?
Answer:
- Go to ISE Reports → RADIUS Authentication
- Filter by device MAC or username
- Click Export CSV
- Include switch CLI outputs for proof of enforcement
YouTube Link
For more in-depth Cisco ISE Mastery Training, subscribe to my YouTube channel Network Journey and join my instructor-led classes for hands-on, real-world ISE experience
7. Deep-Dive Closing Notes
End-to-end lab validation ensures your Cisco ISE wired authentication isn’t just “configured” — it’s proven.
You’re not relying on assumptions; you’re working from hard data, cross-validated between switch CLI and ISE GUI.
This process catches 90% of policy, supplicant, and switch config issues before production.
Upgrade Your Skills – Start Today
Ready to become an enterprise-level Cisco ISE & CCIE Security expert?
Join 4-Month Instructor-Led CCIE Security Mastery Program — a step-by-step, lab-driven journey covering ISE, Firepower, ASA, VPNs, Secure SD-WAN, and more.
- Live classes + Lifetime lab access
- 100% practical with enterprise-grade scenarios
- Direct mentoring & interview prep
Seats are limited for the next batch.
Check the complete course outline here: https://course.networkjourney.com/ccie-security/
Fill out the form to reserve your spot today — and start your path to CCIE Security success.
Enroll Now & Future‑Proof Your Career
Email: info@networkjourney.com
WhatsApp / Call: +91 97395 21088
![[Day 40] Cisco ISE Mastery Training: End-to-End Wired Authentication Lab Validation](https://networkjourney.com/wp-content/uploads/2025/08/Day-40-Cisco-ISE-Mastery-Training-End-to-End-Wired-Authentication-Lab-Validation.png)
![[Day 48] Cisco ISE Mastery Training: BYOD Wireless Onboarding Overview](https://networkjourney.com/wp-content/uploads/2025/08/Day-48-Cisco-ISE-Mastery-Training-BYOD-Wireless-Onboarding-Overview.png)

