[Day 42] Cisco ISE Mastery Training: Integrating Cisco WLC for Wireless Access Control
Table of Contents
Introduction
Wireless networks are the lifeline of modern enterprises — but also a massive attack surface. Without centralized authentication and policy enforcement, wireless SSIDs become easy entry points for unauthorized users, rogue devices, and security breaches.
Cisco Identity Services Engine (ISE) brings RADIUS-based 802.1X/WPA2-Enterprise authentication to the wireless edge, integrating directly with Cisco Wireless LAN Controllers (WLCs) to enforce access policies, posture checks, VLAN assignments, and dynamic ACLs — all in real-time.
By mastering WLC-ISE integration, you gain the ability to:
- Authenticate users with AD/LDAP credentials.
- Differentiate corporate, BYOD, and guest devices automatically.
- Enforce role-based access policies without manual VLAN/SSID sprawl.
- Centrally log and monitor all wireless access events.
Today’s lab will walk you through end-to-end WLC integration with ISE, so you can authenticate and control wireless access at enterprise scale.
Problem Statement
Without ISE integration, a WLC can only do pre-shared key (PSK) or simple MAC filtering — neither is secure or scalable:
- PSKs are static, can be shared, and require rekeying for every change.
- MAC filtering is easily bypassed with spoofing.
- No dynamic policy: All users/devices are treated the same, regardless of their identity or posture.
In regulated industries (finance, healthcare, government), compliance demands centralized authentication, authorization, and accounting (AAA) with audit logs — exactly what WLC-ISE integration delivers.
Solution Overview
The WLC communicates with ISE over RADIUS (AAA):
- User/device connects to SSID.
- WLC forwards credentials to ISE.
- ISE validates identity against AD, local DB, or certificates.
- ISE sends authorization attributes back to WLC (VLAN, ACL, QoS).
- WLC applies policy instantly.
We will configure:
- WLC as a RADIUS client on ISE.
- WLC SSID for 802.1X authentication.
- ISE policy sets for wireless access control.
- CLI + GUI verification for successful integration.
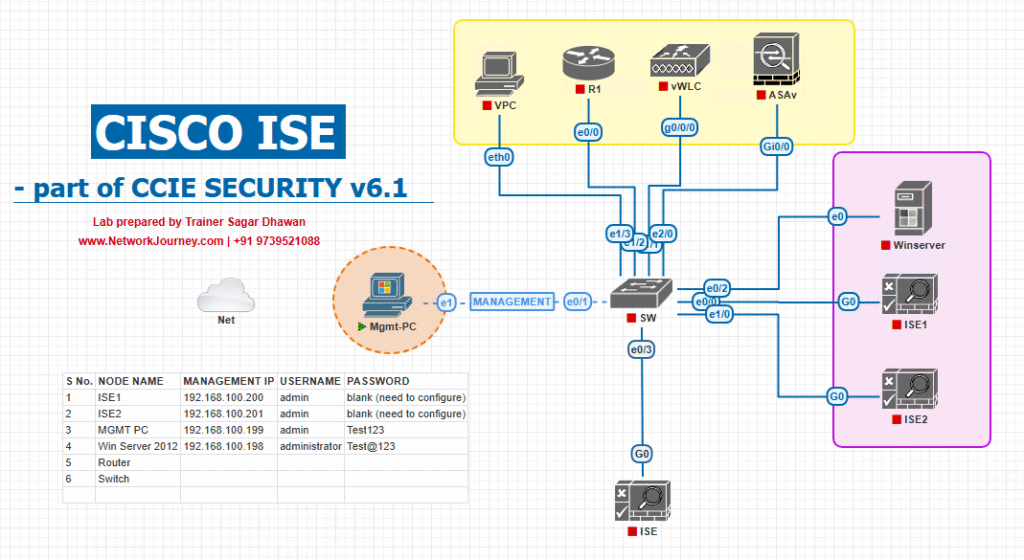
Sample Lab Topology
Platform:
- VMware Workstation / EVE-NG hosting:
- Cisco ISE 3.x VM
- Cisco WLC (v8.x or v9800 if IOS-XE based)
- Catalyst Switch for trunking
- Windows Server (AD + DNS + DHCP)
- Wireless endpoint (Windows 10 laptop, smartphone)
Diagram:
Step-by-Step GUI & CLI Configuration Guide
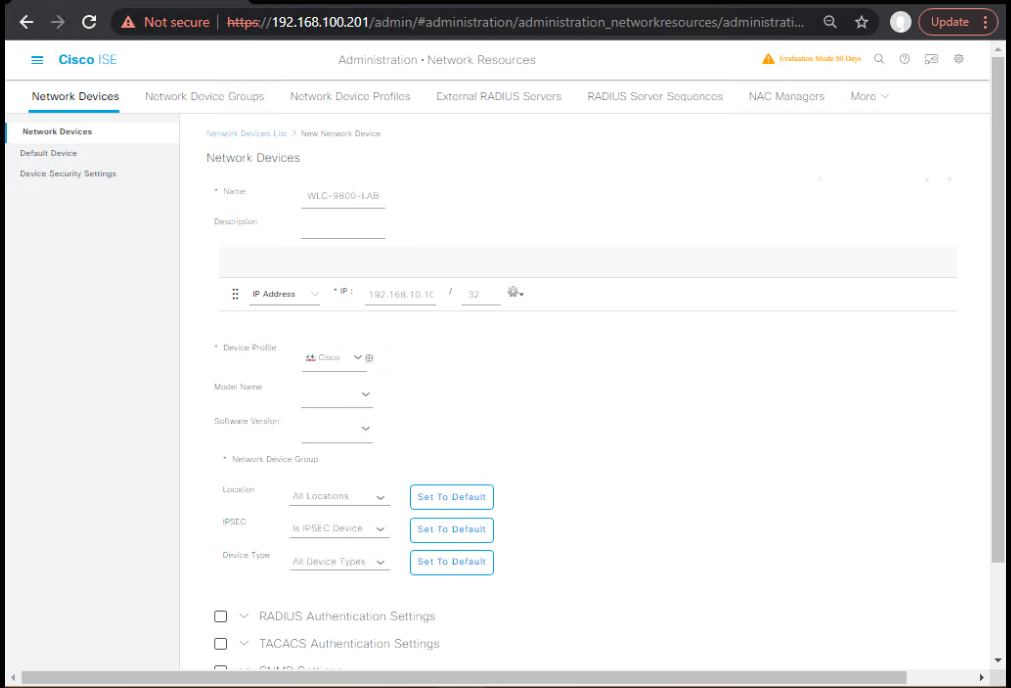
Step 1 – Add WLC as a RADIUS Client in ISE
- Go to Administration → Network Resources → Network Devices.
- Click Add.
- Name: WLC-9800-LAB
- IP Address: Management IP of WLC (e.g., 192.168.10.10).
- Shared Secret:
ISEradius@123(must match WLC). - Check RADIUS Authentication Settings.
- Click Save.
[Screenshot: ISE Add Network Device Screen]
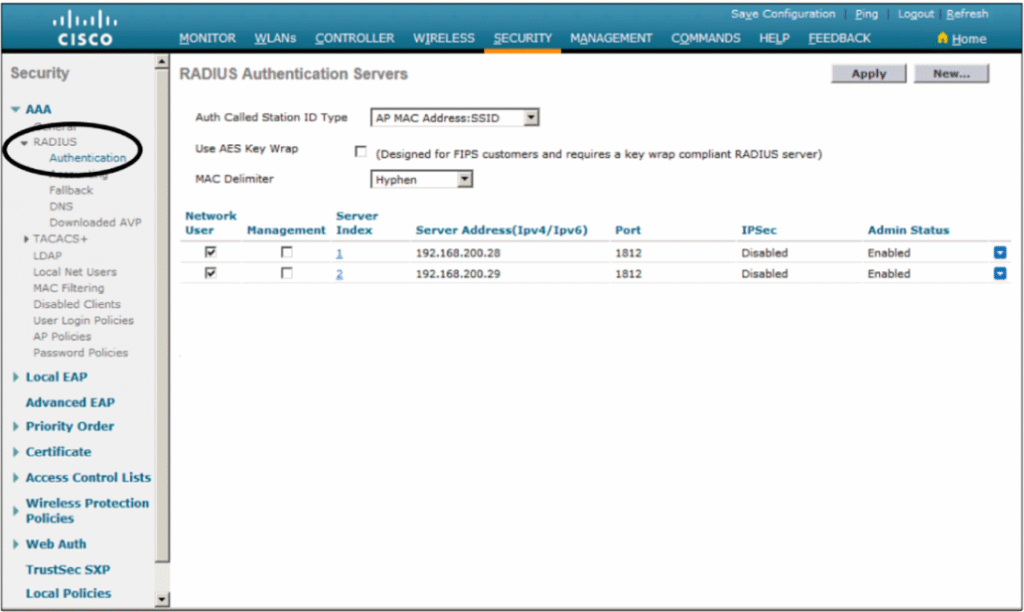
Step 2 – Configure WLC for RADIUS with ISE
GUI Method
- Login to WLC GUI → Security → AAA → RADIUS Authentication.
- Click New.
- Server Address: ISE IP (192.168.10.20).
- Shared Secret: Same as in Step 1.
- Enable Support for CoA (Change of Authorization).
[Screenshot: WLC RADIUS Auth Server Config]
CLI Method
config radius auth add 192.168.10.20 1812 ascii ISEradius@123 config radius auth enable 192.168.10.20 config radius auth port 192.168.10.20 1812 config radius auth network-timeout 5 config radius auth retransmit 3 config radius auth support-coa enable 192.168.10.20
Step 3 – Configure SSID for 802.1X
GUI:
- WLANs → Create New → Go.
- Name:
Corp-Secure - SSID:
Corp-Secure - Security: WPA2-Enterprise
- Authentication: 802.1X → RADIUS Server: ISE
[Screenshot: WLC WLAN Security Tab]
Step 4 – Create ISE Policy Set
- Go to Policy → Policy Sets → Add.
- Name:
Wireless_8021X_Policy - Conditions:
Device Type = WirelessANDSSID = Corp-Secure. - Authentication Policy: Allow EAP-TLS/PEAP against AD.
- Authorization Policy: Map roles to VLANs or ACLs.
[Screenshot: ISE Policy Set Screen]
Step 5 – Validate Authentication
On WLC CLI:
debug client <MAC-address> debug aaa all enable show client detail <MAC-address>
On ISE GUI:
- Operations → RADIUS Live Logs → Look for
Authentication Passed.
[Screenshot: ISE Live Logs Success Entry]
Step 6 – Validate Authorization
On WLC CLI:
show wlan <wlan-id> show client detail <MAC-address> | include VLAN
Check if VLAN/ACL matches ISE authorization result.
FAQs
1. Do I need a separate SSID for ISE integration?
Answer: No. You can integrate any existing SSID with ISE by changing its authentication method to WPA2/WPA3-Enterprise (802.1X) and pointing it to the ISE RADIUS server. However, many engineers prefer creating a dedicated SSID (e.g., Corp-Secure) for easier testing before migrating production users.
2. Which authentication protocols are supported?
Answer: Commonly used protocols are PEAP-MSCHAPv2 (username/password) and EAP-TLS (certificate-based). PEAP is easier to deploy but less secure. EAP-TLS provides the highest security but requires PKI infrastructure for certificate management.
3. Can WLC send device MAC addresses to ISE for profiling?
Answer: Yes. WLC includes Calling-Station-ID (client MAC) in RADIUS requests. ISE can use this for profiling to differentiate device types (laptop, phone, IoT) and apply different authorization rules.
4. How do I verify that RADIUS communication is working?
Answer:
- On WLC CLI:
test aaa radius 192.168.x.x username password ascii - On ISE GUI: Check Operations → RADIUS Live Logs for authentication attempts.
5. What is CoA and why is it important in wireless NAC?
Answer: Change of Authorization (CoA) allows ISE to change a user’s session dynamically without disconnecting them — for example, after posture validation. Without CoA, the user must reconnect to get updated policies.
6. Can I assign VLANs dynamically based on AD group membership?
Answer: Yes. Create Authorization Profiles in ISE mapping AD groups to VLAN IDs, then return the Tunnel-Private-Group-ID RADIUS attribute to WLC during authentication.
7. What happens if ISE is unreachable during wireless authentication?
Answer:
- If Fallback Policy on WLC is set to Open, users may connect without authentication (security risk).
- If set to Closed, authentication will fail and users cannot connect.
Design HA by deploying at least two ISE Policy Service Nodes.
8. How do I capture wireless authentication logs for troubleshooting?
Answer:
- On WLC CLI:
debug client <mac-address> debug aaa all enable - On ISE GUI: Check Live Logs with filters for MAC or username.
9. Is there a difference in config between AireOS WLC and IOS-XE WLC (9800 series)?
Answer: Yes — the GUI paths differ, and IOS-XE uses a policy profile structure. But the AAA concepts, RADIUS server settings, and ISE integration principles remain identical.
10. Can I integrate multiple WLCs with a single ISE cluster?
Answer: Absolutely. Each WLC is added as a separate network device in ISE with its own management IP and shared secret. They can all point to the same ISE PSN(s) for authentication.
YouTube Link
For more in-depth Cisco ISE Mastery Training, subscribe to my YouTube channel Network Journey and join my instructor-led classes for hands-on, real-world ISE experience
Closing Notes
Today’s lab bridged the gap between wireless infrastructure and centralized NAC policy enforcement.
With ISE and WLC integrated, your SSIDs are no longer just “Wi-Fi access points” — they’re policy enforcement points for identity-based, dynamic access control.
Fast-Track to Cisco ISE Mastery Pro
Master Cisco ISE & Security End-to-End — Join the 4-Month CCIE Security Instructor-Led training
In this live program, you’ll:
- Build full-scale labs in EVE-NG/VMware.
- Configure wired, wireless, VPN, and advanced NAC scenarios.
- Learn real-world troubleshooting with GUI & CLI mastery.
- Prepare for enterprise deployments & CCIE Security Lab.
- Seats Limited — Reserve yours now: https://course.networkjourney.com/ccie-security/
- Be job-ready and deploy Cisco ISE like a pro in under 120 days.
Enroll Now & Future‑Proof Your Career
Email: info@networkjourney.com
WhatsApp / Call: +91 97395 21088
![[Day 42] Cisco ISE Mastery Training: Integrating Cisco WLC for Wireless Access Control](https://networkjourney.com/wp-content/uploads/2025/08/Day-42-Cisco-ISE-Mastery-Training-Integrating-Cisco-WLC-for-Wireless-Access-Control.png)
![Performance Routing (PfR) Basics: Optimize Traffic Like a Pro [CCNP ENTERPRISE] networkjourney](https://networkjourney.com/wp-content/uploads/2025/06/nj-blog-post-PFR.jpg)

