[Day 51] Cisco ISE Mastery Training: Wireless DACL Assignments
Table of Contents
Introduction
Downloadable ACLs (dACLs) let Cisco ISE push per-session, per-user ACLs to the WLAN edge at the moment of authorization—so wireless clients get only the access they need (internet-only, app-only, or micro-segmented). Instead of pre-staging many ACLs on the controller, ISE becomes the source of truth, returning the right ACL dynamically based on identity, device profile, posture, or time of day.
Problem Statement
Common wireless access problems:
- One-size-fits-all VLANs/ACLs (too open or too restrictive).
- Operational sprawl maintaining many per-SSID/per-site ACLs on WLCs.
- No per-user context (role, device, posture) at authorization time.
- Slow change management—every policy tweak needs controller changes.
You need centralized, identity-driven enforcement that can be changed in ISE and applied instantly to clients via CoA.
Solution Overview (What you’ll build)
- Create dACL objects in ISE and return them in Authorization Profiles.
- Policy Set matches wireless sessions and assigns the right dACL per role.
- Configure WLC (9800-CL or AireOS) for AAA override and RADIUS accounting.
- Validate application of ACL on the client session via ISE Live Logs and WLC CLI.
- If your WLC/image doesn’t support true dACL for WLAN, use Airespace (named) ACLs on the WLC and have ISE return the ACL name.
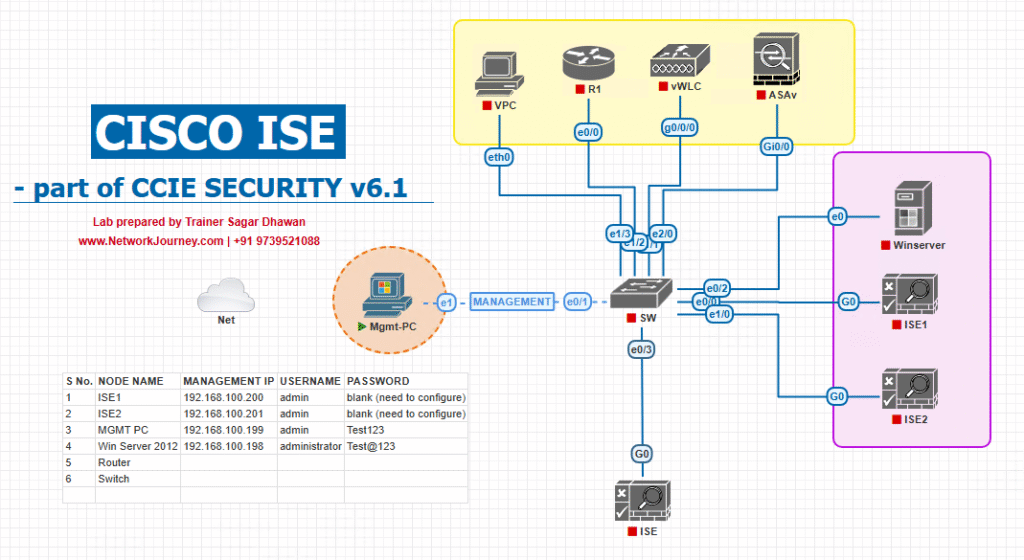
Sample Lab Topology
Platform (VMware/EVE-NG)
- Cisco ISE 3.x (PAN/PSN in one VM for lab)
- Cisco WLC 9800-CL (or AireOS 8.10+)
- Catalyst L2 switch (virtual fine)
- DHCP/DNS (switch or Windows server)
- Endpoints: Win 11 laptop, iPhone/Android, test IoT
Topology Layout:
Step-by-Step GUI Configuration Guide (with validation)
PREREQS
- Time/DNS aligned.
- WLC added in ISE: Administration > Network Resources > Network Devices (RADIUS secret).
- WLAN has RADIUS accounting & AAA override enabled.
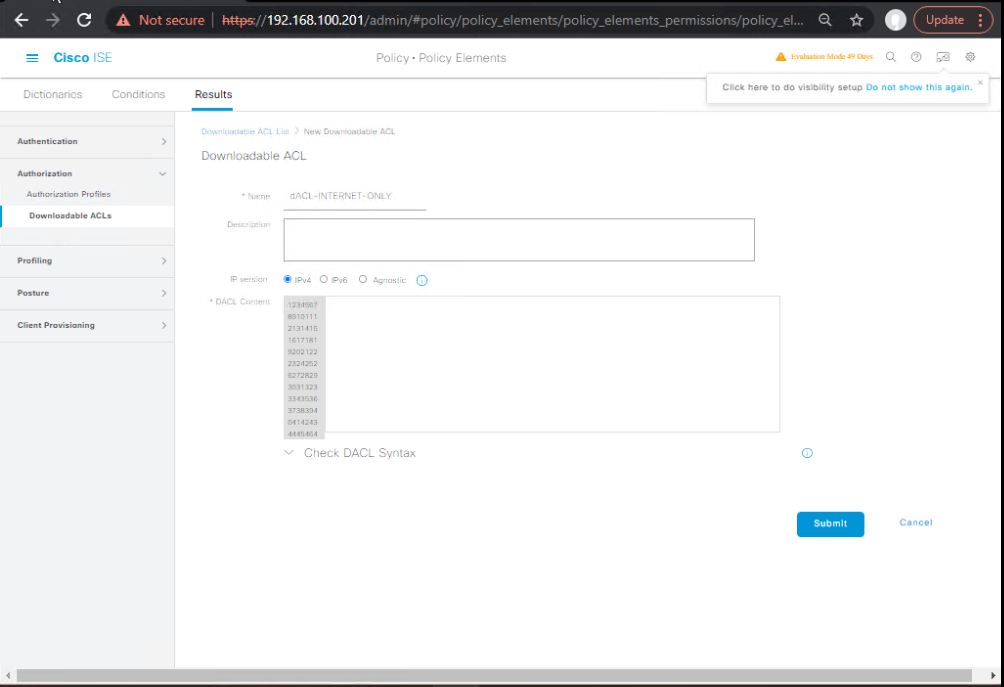
A) ISE — Build Downloadable ACLs (dACLs)
- Create dACL Objects
- Policy > Policy Elements > Results > Authorization > Downloadable ACLs > Add
- Name:
dACL-INTERNET-ONLY - ACL Content (example)
permit udp any any eq domain permit udp any any eq bootpc permit udp any any eq bootps permit icmp any any permit tcp any any eq 443 deny ip any 10.0.0.0 0.255.255.255 deny ip any 172.16.0.0 0.15.255.255 deny ip any 192.168.0.0 0.0.255.255 permit ip any any - Save.
- Name:
- Repeat for
dACL-BYOD-CORP-APPS,dACL-IOT-CAMERA-OUTBOUND, etc. - [Screenshot: ISE Downloadable ACL Editor]
- Policy > Policy Elements > Results > Authorization > Downloadable ACLs > Add
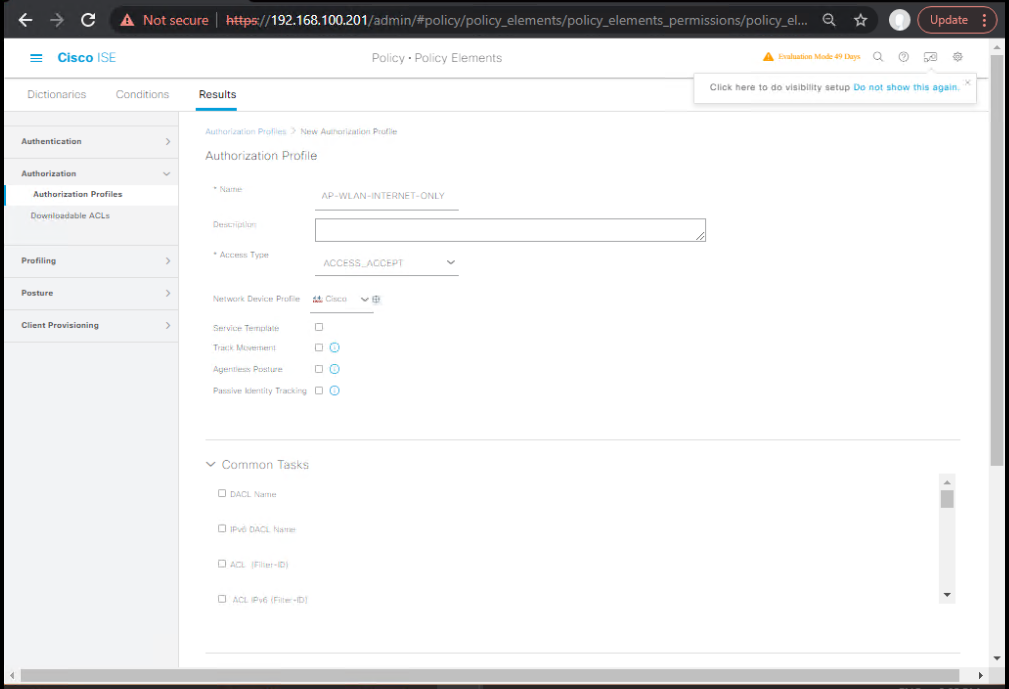
- Create Authorization Profiles
- Policy > Policy Elements > Results > Authorization > Authorization Profiles > Add
- Name:
AP-WLAN-INTERNET-ONLY - Common Tasks:
- DACL: select
dACL-INTERNET-ONLY(if your WLC supports wireless dACL) - (Fallback) Airespace ACL Name:
ACL-INTERNET-ONLY(if using WLC-local ACL)
- DACL: select
- RADIUS Accounting: ensure enabled on WLAN (WLC side).
- Name:
- Repeat profiles for other roles (
AP-WLAN-BYOD,AP-WLAN-IOT, etc.). - [Screenshot: Authorization Profile – dACL Selected]
- Policy > Policy Elements > Results > Authorization > Authorization Profiles > Add
Note: Some WLC images apply dACL natively; others require Airespace (named) ACL. We’ll configure both so you can test which your platform supports.
B) ISE — Authorization Policy (Wireless Policy Set)
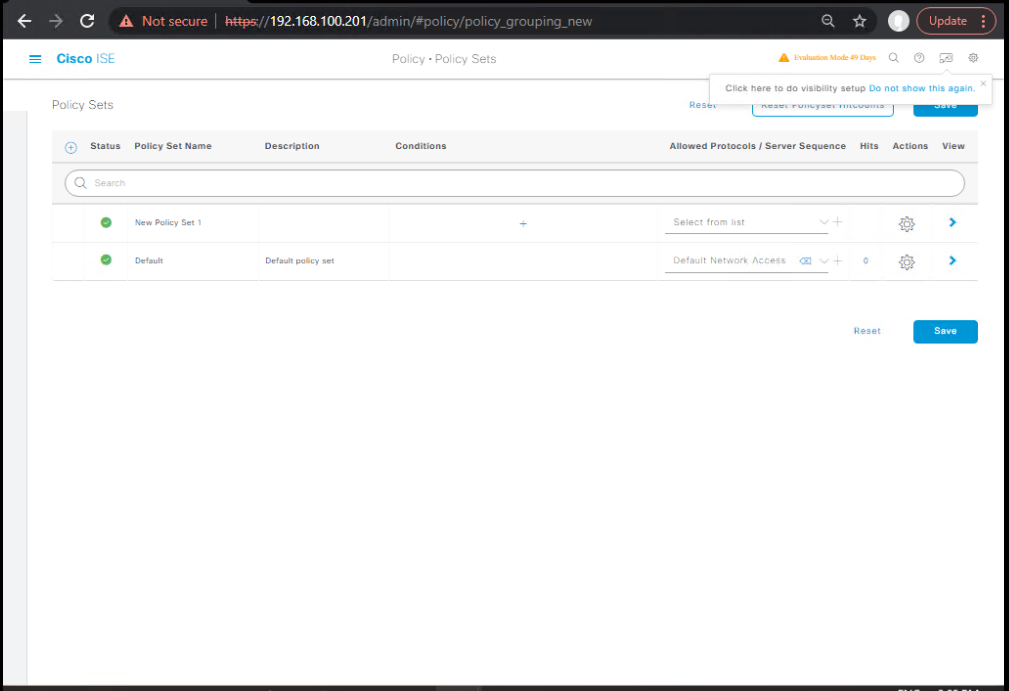
- Policy Set
- Policy > Policy Sets > Add → Name:
Wireless-DACL - Conditions:
NetworkDeviceType = Wireless(or NDG:WLC) - [Screenshot: Policy Set Condition]
- Policy > Policy Sets > Add → Name:
- Authentication Policy
- Keep your existing 802.1X/PEAP/EAP-TLS entries; ensure MAB if you use CWA flows.
- Authorization Policy (top-down)
- Rule 1: Employees + EAP-TLS → Result:
AP-WLAN-BYOD(dACL or Airespace)- Condition:
EapAuthentication = EAP-TLSANDExternalGroups = AD-Employees
- Condition:
- Rule 2: Guests/Unknown → Result:
AP-WLAN-INTERNET-ONLY - Rule 3: IoT Camera profile → Result:
AP-WLAN-IOT - Default: Deny/Quarantine
- [Screenshot: ISE Authorization Rules with Result column]
- Rule 1: Employees + EAP-TLS → Result:
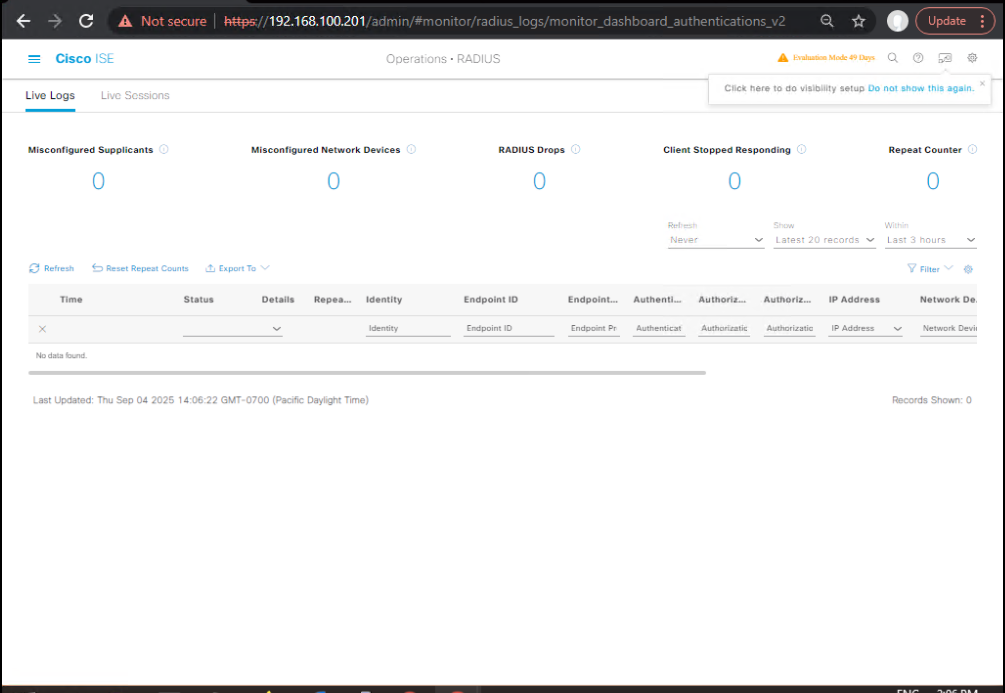
Validation – ISE GUI
- Operations > RADIUS > Live Logs → Click the session
- Authorization Result: your
AP-WLAN-...profile - Details > Attributes: shows dACL name or Airespace-ACL-Name returned
- [Screenshot: Live Logs – Returned Attributes]
- Authorization Result: your
C) WLC 9800-CL — AAA, ACLs, WLANs
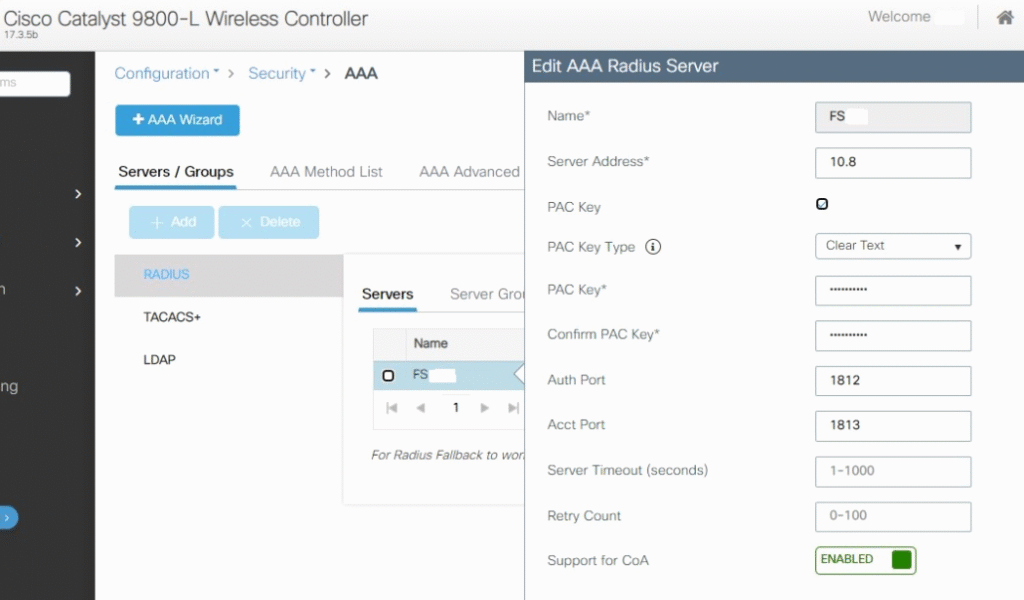
- AAA/RADIUS
- Configuration > Security > AAA > Servers > RADIUS → ISE auth & acct
- Accounting enabled on WLAN.
- [Screenshot: WLC RADIUS Servers]
- Enable AAA Override on WLAN
- Configuration > Tags & Profiles > Policy Profiles >
- AAA Override: Enable
- [Screenshot: Policy Profile – AAA Override]
- Configuration > Tags & Profiles > Policy Profiles >
- (Fallback Path) Create Airespace (Named) ACLs on WLC
- Configuration > Security > ACL > Add (IPv4) → Name:
ACL-INTERNET-ONLY - Add entries that mirror your ISE dACL logic (DNS/DHCP/ICMP/443 permit, RFC1918 deny, etc.).
- [Screenshot: WLC ACL Editor]
- Configuration > Security > ACL > Add (IPv4) → Name:
- WLAN
- Configuration > Tags & Profiles > WLANs → your
CORP-WLAN - Security > AAA: ISE for AuthN/AuthZ/Acct, Accounting Interim Updates on
- [Screenshot: WLAN AAA]
- Configuration > Tags & Profiles > WLANs → your
Validation – WLC CLI (9800)
show wireless client mac <client-mac> detail ! Look for: Policy Profile, IPv4 ACL (or DACL name), AAA Override: Enabled show access-lists summary show access-list ACL-INTERNET-ONLY show aaa servers show logging | inc AAA|RADIUS|CoA|ACL debug wireless mac <client-mac> events debug aaa all undebug all
AireOS CLI (if applicable)
show client detail <mac> show acl summary show acl <ACL-NAME> debug client <mac> debug aaa events enable
D) Change Control & CoA Validation
- Modify the dACL in ISE (e.g., add
permit tcp any <test-app> eq 8443). - Save → Re-auth the client (or ISE > Live Sessions > Reauthenticate).
- Observe on WLC: logs showing CoA applied; client keeps session and ACL updates in place.
Quick Test from Client
- Reach allowed resources (e.g., 443 to internet).
- Fail to reach denied RFC1918 ranges.
- If behavior doesn’t match, verify which ACL (dACL vs Airespace) is actually applied.
E) Role Mapping Examples
- Employees (EAP-TLS) →
dACL-BYOD-CORP-APPS(allow corp apps, block lateral) - Guests (self-reg) →
dACL-INTERNET-ONLY - Contractors →
dACL-CONTRACTOR-LIMITED(SaaS + ticketing) - IoT Cameras →
dACL-IOT-CAMERA-OUTBOUND(DNS/NTP + RTSP to NVR only)
FAQs
1) Why is my dACL not being applied to the wireless client?
This is usually because the WLC platform or software version doesn’t support true ISE downloadable ACLs for WLAN sessions. In such cases, you must configure an Airespace (named) ACL locally on the WLC and have ISE return its name instead. Also verify:
- AAA Override is enabled on the WLAN’s Policy Profile.
- RADIUS Accounting is turned on.
- The Authorization Profile in ISE references the correct dACL or Airespace ACL name.
2) Where exactly do I configure the dACL in ISE?
Under Policy > Policy Elements > Results > Authorization > Downloadable ACLs you create the ACL object. Then, in an Authorization Profile, under Common Tasks, select the dACL from the dropdown. If you’re using Airespace ACL fallback, type the exact ACL name in the Airespace ACL Name field.
3) Can I apply both a VLAN and a dACL from ISE at the same time?
Yes. In the same Authorization Profile, you can set VLAN ID, dACL, and even SGT simultaneously. The WLC will apply them in combination—VLAN for L2 segmentation, dACL for L3/L4 restrictions.
4) How can I verify which ACL was actually applied to a wireless client?
- In ISE: Go to Operations > RADIUS > Live Logs, open the session details, and check Returned RADIUS Attributes. Look for Cisco-AVPair=ip:inacl#… (dACL) or Airespace-ACL-Name.
- In WLC CLI: Use
show wireless client mac <MAC> detailand look for IPv4 ACL Name or dACL entry.
5) Do dACLs support IPv6 traffic filtering?
Only if your ISE and WLC support IPv6 enforcement in ACLs. Otherwise, IPv6 traffic may bypass IPv4-only ACLs, so you’ll need separate IPv6 ACLs or SGT-based policy.
6) How do I update a dACL without disconnecting the user?
You can edit the dACL in ISE, then send a CoA (Change of Authorization) or Reauthenticate command from Live Sessions. This will refresh the ACL on the session without a full WLAN rejoin.
7) My ACL changes are not taking effect after CoA—why?
Some client devices or WLC modes cache ACL rules until the wireless session fully resets. If a CoA doesn’t push the change, try a full disconnection and reconnection. Also confirm that the new ACL is indeed the one ISE is returning in Live Logs.
8) What’s the main difference between a dACL and an Airespace ACL?
- dACL: Created in ISE, downloaded dynamically to the WLC per session, fully centralized.
- Airespace ACL: Preconfigured locally on the WLC; ISE only tells the WLC which one to apply by name.
Use dACL when supported; use Airespace ACL for older hardware or unsupported software versions.
9) Do I need RADIUS Accounting enabled for dACLs to work?
Yes. Without accounting, CoA and dynamic policy changes may not be applied mid-session. Enable accounting in the WLAN settings and on the AAA server list.
10) Can I test a dACL safely without affecting production SSIDs?
Yes—create a lab/test SSID on the WLC mapped to the same ISE policy set. Apply your dACLs there first. Once confirmed via ping/traceroute/browser tests and WLC CLI validation, you can roll out to production with confidence.
YouTube Link
For more in-depth Cisco ISE Mastery Training, subscribe to my YouTube channel Network Journey and join my instructor-led classes for hands-on, real-world ISE experience
Closing Notes
You now enforce identity-based, per-session ACLs on wireless with ISE at the center. Use dACLs where supported for single-pane policy, and fall back to Airespace ACL names where needed. Always validate with ISE Live Logs + WLC client detail and keep AAA Override and Accounting on.
Upgrade Your Skills – Start Today
Ship a production-grade wireless NAC with confidence—guided by an expert.
Join 4-Month, Instructor-Led CCIE Security & Cisco ISE Mastery:
- Live builds of WLC 9800 + ISE: dACLs, SGT, pxGrid, BYOD, Guest
- EVE-NG topologies, graded lab workbooks, and solution walk-throughs
- Real-world templates: dACL libraries, AuthZ rulebooks, CoA runbooks
- Career mentorship, recordings, and mock interviews
Wireless Enforcement Pack (ready-to-use dACLs, WLC ACL mirrors, validation scripts).
Check the full syllabus & reserve your seat: https://course.networkjourney.com/ccie-security/
Enroll Now & Future‑Proof Your Career
Email: info@networkjourney.com
WhatsApp / Call: +91 97395 21088

![[Day 40] Cisco ISE Mastery Training: End-to-End Wired Authentication Lab Validation](https://networkjourney.com/wp-content/uploads/2025/08/Day-40-Cisco-ISE-Mastery-Training-End-to-End-Wired-Authentication-Lab-Validation.png)
![Mastering EtherChannel Load Balancing Methods: A Complete Guide with CLI & EVE-NG Lab [CCNP ENTERPRISE]](https://networkjourney.com/wp-content/uploads/2025/06/Mastering-EtherChannel-Load-Balancing-Methods_A-Complete-Guide_networkjourney.png)
