[Day 52] Cisco ISE Mastery Training: Wireless VLAN Assignment
Table of Contents
Introduction
Dynamic VLAN assignment lets Cisco ISE place each wireless client in the right L2 segment at the moment of authorization—employees to corp VLAN, guests to internet-only, IoT to isolated networks—on the same SSID. You’ll build per-role VLAN results in ISE, enable AAA Override on the WLC, and verify the RADIUS attributes & client session state.
Problem Statement
Typical pain points:
- Multiple SSIDs, SSID sprawl, inconsistent policy.
- Hard-coded WLAN-to-VLAN maps that ignore user/device identity.
- Risky lateral movement (guest/IoT mixing with corp users).
- Change windows on WLCs for every segmentation tweak.
You need identity-driven VLANs centrally controlled in ISE and applied instantly via CoA.
Solution Overview (What you will build)
- ISE Authorization Profiles returning VLAN using RADIUS IETF tunnel attributes (and Airespace-Interface-Name for AireOS).
- WLC AAA Override to accept VLAN results per session.
- Central switching (controller-switched) and FlexConnect local switching options.
- Live validation in ISE (Live Logs) and WLC/AireOS CLI.
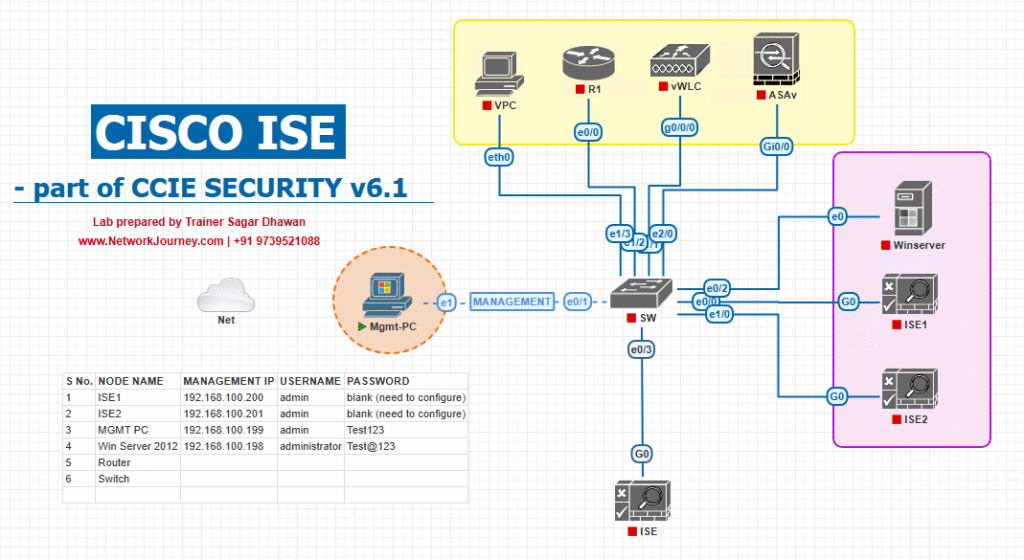
Sample Lab Topology
Platform (VMware/EVE-NG)
- Cisco ISE 3.x (PAN/PSN in one VM for lab)
- Cisco WLC 9800-CL (or AireOS 8.10+)
- Catalyst switch upstream (SVIs/DHCP helper)
- DHCP/DNS (on switch or Windows server)
- Endpoints: Win 11, iPhone/Android, IoT device
Topology Layout:
Step-by-Step GUI Configuration Guide (with validation)
PREREQS
- Time/DNS aligned on ISE/WLC/switch.
- WLC added as a network device in ISE (Administration > Network Resources > Network Devices).
- Trunk from WLC to switch allows target VLANs; SVIs & DHCP configured.
A) Catalyst Switch – Trunk, SVIs, DHCP Helper (Reference)
! Trunk to WLC interface Gig1/0/10 description To-WLC-9800 switchport trunk encapsulation dot1q switchport mode trunk switchport trunk allowed vlan 20,30,40 spanning-tree portfast trunk ! SVIs (gateway + DHCP helper) interface Vlan20 ip address 10.20.0.1 255.255.255.0 ip helper-address 10.10.10.10 ! DHCP server interface Vlan30 ip address 10.30.0.1 255.255.255.0 ip helper-address 10.10.10.10 interface Vlan40 ip address 10.40.0.1 255.255.255.0 ip helper-address 10.10.10.10
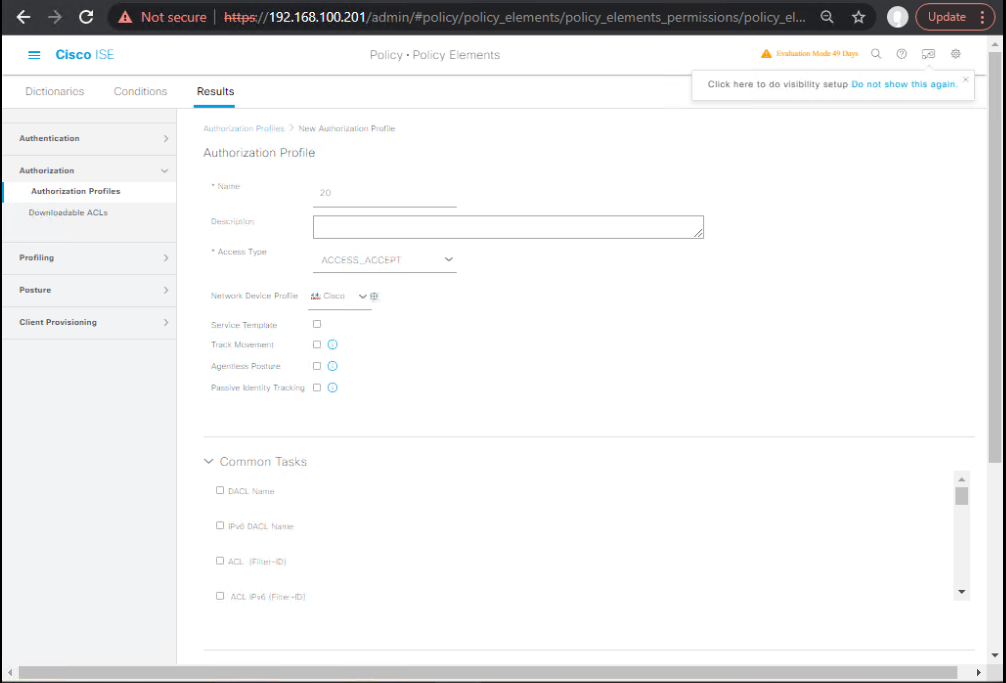
B) ISE — Create VLAN Authorization Profiles
Path: Policy > Policy Elements > Results > Authorization > Authorization Profiles > Add
Create three profiles:
- AP-VLAN-EMPLOYEES
- Common Tasks → VLAN:
- VLAN ID/Name:
20(orVLAN20)
- VLAN ID/Name:
- (ISE will send IETF RADIUS attributes: Tunnel-Type=VLAN, Tunnel-Medium-Type=802, Tunnel-Private-Group-ID=20)
- [Screenshot: ISE Authorization Profile VLAN Employees]
- Common Tasks → VLAN:
- AP-VLAN-GUEST
- VLAN ID:
30 - Optional dACL for internet-only if you also want L3 control.
- [Screenshot: ISE Authorization Profile VLAN Guest]
- VLAN ID:
- AP-VLAN-IOT
- VLAN ID:
40 - [Screenshot: ISE Authorization Profile VLAN IoT]
- VLAN ID:
AireOS option: instead of VLAN ID, you can set Airespace-Interface-Name (in the profile) to the interface name configured on AireOS (e.g.,
GUEST-INTF).
[Screenshot: ISE Authorization Profile – Airespace Interface Name]
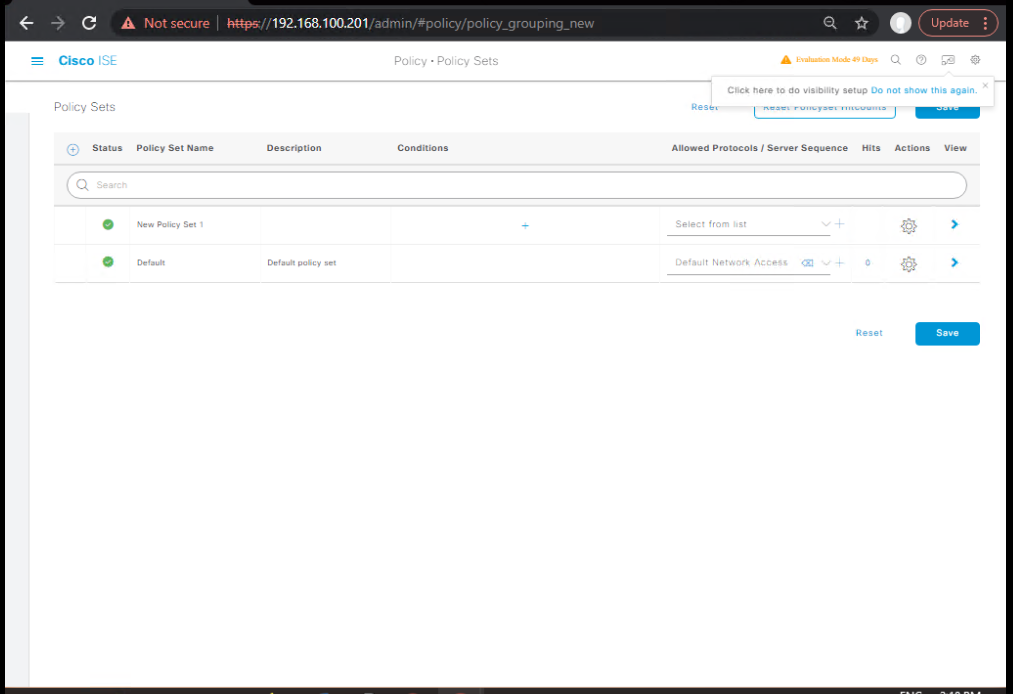
C) ISE — Build Wireless Policy Set & Rules
Path: Policy > Policy Sets > Add
- Policy Set Condition:
Device Type = Wireless(or NDG:WLC) - Authentication Policy: your existing 802.1X/PEAP/EAP-TLS; include MAB if needed.
- Authorization Policy (top-down):
- Employees (
EapAuthentication=EAP-TLSANDExternalGroups=AD-Employees) → AP-VLAN-EMPLOYEES - Guests (
IdentityGroup=GuestEndpoints OR GuestFlow) → AP-VLAN-GUEST - IoT (
EndpointProfile=Camera-Device OR Printer) → AP-VLAN-IOT - Default → Quarantine/Denial as preferred
- [Screenshot: ISE Policy Set Screen with VLAN Results]
- Employees (
Validation (ISE GUI)
- Operations > RADIUS > Live Logs → Click a session → confirm Authorization Result = your VLAN profile and RADIUS Attributes show Tunnel-Private-Group-ID.
- [Screenshot: ISE Live Logs – Returned Tunnel Attributes]
D) WLC 9800-CL — WLAN, Policy Profile, AAA Override
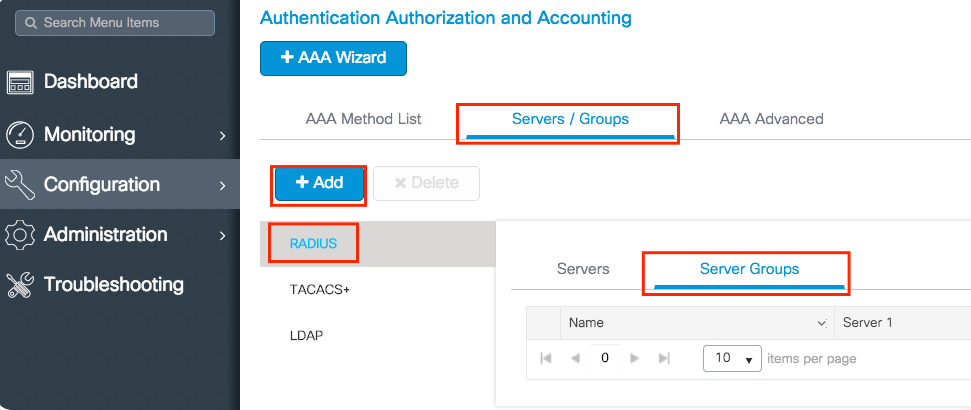
- RADIUS servers
- Configuration > Security > AAA > Servers > RADIUS → Add ISE for Auth and Accounting.
- [Screenshot: WLC RADIUS Server Config]
- WLAN (e.g., ID 10, SSID
CORP-SSO)- Configuration > Tags & Profiles > WLANs > CORP-SSO
- Security > AAA: set ISE for Auth/Acct, enable Accounting Interim Updates.
- [Screenshot: WLAN AAA]
- Policy Profile (bound to WLAN)
- Configuration > Tags & Profiles > Policy Profiles >
- AAA Override: Enabled
- VLAN/VXLAN: set a default VLAN (e.g., 30), used when ISE does not override.
- Central Switching: ON (for controller-switched)
- [Screenshot: Policy Profile – AAA Override & VLAN]
- Tags
- Ensure the WLAN is mapped to the Policy Profile and pushed via Policy Tag to APs.
- [Screenshot: Policy Tag Mapping]
Validation – 9800 CLI
show wlan summary show wireless client mac <client-mac> detail ! Look for: VLAN = 20/30/40 (overridden), Policy Profile, AAA Override: Enabled show policy-profile name <YourProfile> show wireless tag policy show logging | inc AAA|RADIUS|CoA|Tunnel-Private|VLAN
E) AireOS WLC — Interface & AAA Override (if you use AireOS)
- Create dynamic interfaces (e.g.,
corp20,guest30,iot40) with correct VLANs. - WLAN → Advanced: AAA Override: Enabled.
- In ISE Authorization Profile, set Airespace-Interface-Name = corp20/guest30/iot40.
Validation – AireOS CLI
show client detail <mac> ! Look for: Interface Name = corp20/guest30/iot40 show interface detailed <name> show wlan <wlan-id> debug client <mac> debug aaa events enable
F) FlexConnect – Local Switching Dynamic VLAN
- Site Tag / Flex Profile on 9800
- Configuration > Tags & Profiles > Flex Profiles → enable Local Switching for the WLAN.
- AP VLAN Mapping
- Map VLAN 20/30/40 on the AP’s local trunk at the branch.
- AAA Override still Enabled in Policy Profile.
- Ensure branch switch ports carry the right VLANs & DHCP helper local to site.
Validation – 9800 CLI
show ap name <AP-NAME> config general show ap name <AP-NAME> wlan <wlan-id> flex vlan show wireless client mac <mac> detail
Client should obtain an IP from the branch VLAN scope.
G) End-to-End Validation (What to check)
On the Client
- IP address from correct subnet:
ipconfig/ifconfig. - Default gateway & DHCP options match the expected VLAN.
- Access tests (ping gateway, reach corp app or only internet as designed).
On ISE
- Live Logs line-up for each connect: Auth success → VLAN Authorization Profile applied.
- Details show
Tunnel-Type=VLAN (13),Tunnel-Medium-Type=IEEE-802 (6),Tunnel-Private-Group-ID=20/30/40.
On WLC
- Client detail shows overridden VLAN.
- Logs show receipt of RADIUS attributes and CoA on rule change.
FAQs (Wireless VLAN Assignment)
1) What RADIUS attributes does ISE send to assign a VLAN?
ISE sends IETF Tunnel attributes:
Tunnel-Type = VLAN (13)Tunnel-Medium-Type = IEEE-802 (6)Tunnel-Private-Group-ID = <VLAN ID>
On AireOS, you can also sendAirespace-Interface-Name = <WLC interface name>instead of VLAN ID.
Tip: Check in ISE Live Logs → Details → RADIUS Attributes.
2) Why is my VLAN override not working even though ISE Live Logs show the VLAN ID?
Most common causes:
- AAA Override not enabled in the WLAN’s Policy Profile (9800) or WLAN Advanced tab (AireOS).
- Returned VLAN doesn’t exist on the WLC or isn’t allowed on the trunk uplink.
- FlexConnect AP doesn’t have VLAN mapped in its local switchport.
- ISE profile applied to wrong policy set.
3) Is AAA Override mandatory for Wireless VLAN Assignment?
Yes. Without AAA Override, the WLC ignores VLAN instructions from ISE and keeps clients on the WLAN’s default VLAN.
4) How can I verify VLAN assignment from the WLC side?
- 9800-CL CLI:
show wireless client mac <mac> detailLook for VLAN = and Policy Profile. - AireOS CLI:
show client detail <mac>Look for Interface Name or VLAN.
5) Can I assign VLANs dynamically for both 802.1X and MAB clients?
Yes. The same Authorization Profiles work for both. Just ensure your policy set covers both EAP and MAB flows.
6) What’s the difference between returning VLAN ID vs Airespace-Interface-Name?
- VLAN ID (Tunnel-Private-Group-ID) is standards-based and works on 9800 & AireOS.
- Airespace-Interface-Name is proprietary to AireOS and directly maps to a named WLC interface.
9800 does not support Airespace-Interface-Name.
7) Does dynamic VLAN assignment work with FlexConnect local switching?
Yes, but VLAN must exist at the AP’s local switch and be mapped in the Flex Profile. The WLC only tells the AP which VLAN ID to use.
8) How do I handle DHCP renewals after VLAN change?
After VLAN change via CoA or reauth:
- Some clients renew automatically.
- Others need a CoA Disconnect to trigger DHCP DISCOVER.
- Always ensure ip helper-address exists for that VLAN in the gateway.
9) Can I combine VLAN assignment with dACL or SGT?
Yes. An Authorization Profile can return VLAN + dACL + SGT in the same RADIUS response for layered policy enforcement.
10) Can VLAN changes be done live without disconnecting users?
Partially. A CoA Reauth can move a client to a new VLAN mid-session, but there is usually a 1–3 second drop while DHCP rebinds.
For critical users, schedule changes during low usage windows.
YouTube Link
For more in-depth Cisco ISE Mastery Training, subscribe to my YouTube channel Network Journey and join my instructor-led classes for hands-on, real-world ISE experience
Closing Notes
You’ve built identity-driven VLANs on a single SSID: ISE returns the VLAN, WLC enforces per session, and you verified it at the client, ISE, and WLC layers. Combine with dACL/SGT for layered enforcement, and use CoA for safe, live policy changes.
Upgrade Your Skills – Start Today
Turn today’s VLAN lab into a production-ready, audit-proof NAC rollout—guided by an expert.
Join 4-Months Instructor-Led CCIE Security & Cisco ISE Mastery:
- Live builds: VLAN & dACL enforcement, BYOD, Guest, Profiling, SGT/pxGrid
- EVE-NG topologies, graded workbooks, solution keys
- Real-world 9800 & FlexConnect designs, CoA runbooks, change-control templates
- Lifetime recordings, career mentorship, and mock interviews
Enrollment Bonus (Lead Magnet): Wireless Segmentation Pack
- Ready-to-use ISE Authorization Profiles (VLAN/dACL/SGT)
- WLC & switch config snippets, validation checklists, RCA flowcharts
See syllabus & reserve your seat: https://course.networkjourney.com/ccie-security/
Enroll Now & Future‑Proof Your Career
Email: info@networkjourney.com
WhatsApp / Call: +91 97395 21088

![[Day 41] Cisco ISE Mastery Training: Wireless 802.1X Authentication Overview](https://networkjourney.com/wp-content/uploads/2025/08/Day-41-Cisco-ISE-Mastery-Training-Wireless-802.1X-Authentication-Overview.png)

