[Day 70] Cisco ISE Mastery Training: Wireless NAC End-to-End Lab Validation
Table of Contents
Introduction
Wireless NAC (Network Access Control) is one of the most critical security use-cases in enterprise networks. While wired NAC ensures endpoints connected via switches are authenticated and authorized, wireless NAC validation ensures every mobile, IoT, and BYOD device connecting through Wi-Fi is properly authenticated against Cisco ISE.
End-to-end validation is essential:
- To confirm the AAA (Authentication, Authorization, Accounting) flow works as expected.
- To ensure wireless devices are assigned correct VLANs, ACLs, and policies.
- To detect failures quickly – whether the issue lies with WLC, ISE, certificate trust, or endpoint supplicant.
This lab is your capstone validation exercise for wireless NAC with ISE.
Problem Statement
Enterprises struggle with:
- Ensuring wireless endpoints comply with corporate policy (802.1X, posture, guest/BYOD).
- Validating that end-to-end policy enforcement works (endpoint → AP → WLC → ISE → AD/PKI).
- Troubleshooting where the NAC chain breaks when users fail authentication.
Without proper validation workflows, IT teams may deploy ISE but miss gaps in enforcement, leading to rogue devices bypassing policy or users falling back to open SSIDs.
Solution Overview
Cisco ISE enables end-to-end wireless NAC validation by:
- Acting as the central AAA server for WLC and endpoints.
- Enforcing authentication policies (PEAP, EAP-TLS, etc.).
- Delivering dynamic VLAN assignment, ACLs, or dACLs.
- Providing visibility reports in GUI and syslog.
- Allowing live CLI troubleshooting on WLC and ISE.
Sample Lab Topology
Topology Components:
- VMware/EVE-NG: Hosting Cisco ISE 3.x, AD/CA server, and WLC (9800/5508).
- Switches: Catalyst (access + distribution).
- WLC: Configured for SSID
Corp-WiFiwith WPA2-Enterprise (802.1X). - AP: Lightweight AP registered to WLC.
- Endpoints: Windows 10 laptop, iPhone, and BYOD Android device.
Diagram Description:
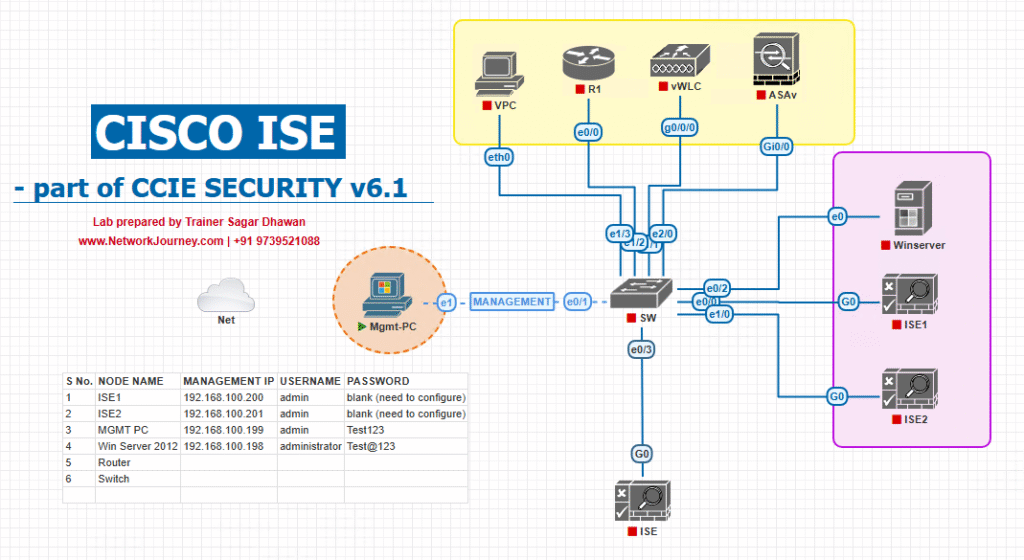
- Endpoints connect via AP → WLC.
- WLC forwards authentication to ISE (RADIUS).
- ISE queries AD/CA for identity/certificate.
- ISE responds with authorization profile (VLAN/ACL).
- WLC enforces VLAN/ACL.
Step-by-Step GUI Configuration Guide
Step 1: Configure WLAN on WLC for 802.1X
- Navigate to WLC GUI > WLANs > Create New > Corp-WiFi.
- Security > Layer 2: Choose WPA2-Enterprise with 802.1X.
- AAA Servers: Add Cisco ISE IP.
- [Screenshot: WLC WLAN Security Settings]
CLI validation:
show wlan summary show aaa servers
Step 2: Configure WLC as Network Device in ISE
- ISE GUI: Administration > Network Resources > Network Devices > Add.
- Name: WLC-9800, IP: .
- Check RADIUS Authentication Settings → Add shared secret.
- [Screenshot: ISE Add Network Device]
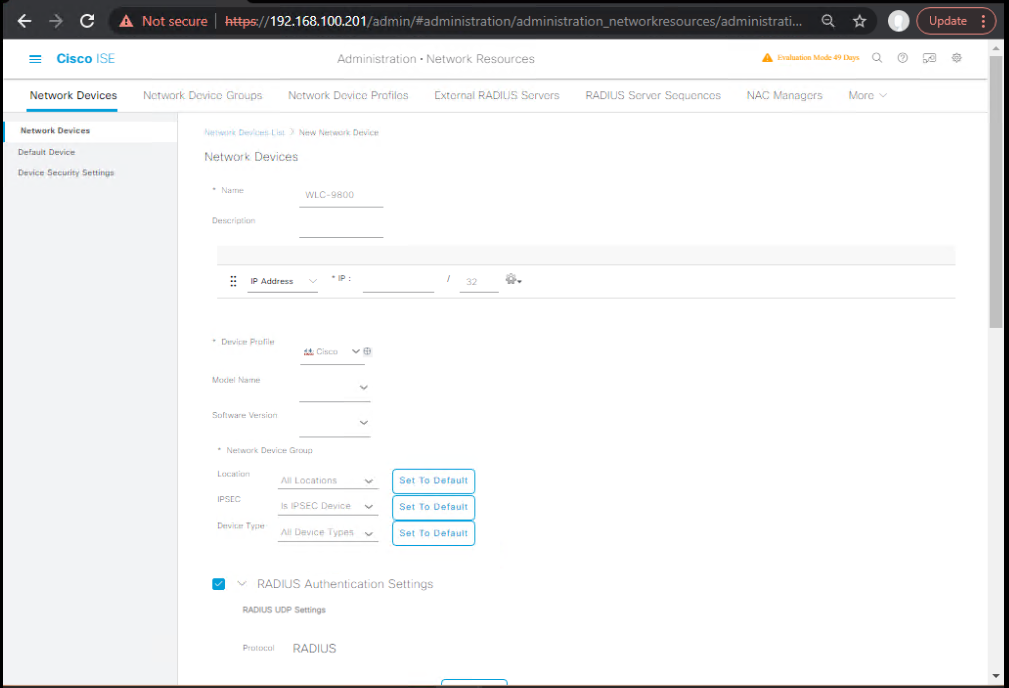
CLI validation on ISE:
show running-config | include network-device
Step 3: Configure Authentication Policy in ISE
- ISE GUI: Policy > Policy Sets > Create Policy Set: Wireless NAC.
- Authentication Rule:
If Wireless_MAB→ use MAB. - Authentication Rule:
If Wireless_802.1X→ use AD. - [Screenshot: ISE Authentication Policy Screen]
Step 4: Configure Authorization Policy in ISE
- Example Rules:
- Corporate Laptops → Assign VLAN 20 + ACL.
- Guests → Redirect to Guest Portal.
- BYOD → Onboard Policy.
- [Screenshot: ISE Authorization Policy Screen]
CLI validation on ISE:
show logging application ise-psc.log tail
Step 5: Endpoint Connection Test
- Connect a laptop to
Corp-WiFi. - Enter AD credentials (if PEAP).
- Verify: Authentication request hits ISE.
WLC CLI validation:
show client summary show client detail <mac-address> debug client <mac-address>
ISE Live Logs validation:
- GUI: Operations > RADIUS > Live Logs.
- [Screenshot: ISE Live Logs Authentication]
Step 6: Verify Policy Enforcement
- Confirm device is placed in correct VLAN.
- Test ACL access (e.g., reach internal server).
- ISE Context Visibility shows endpoint attributes.
- [Screenshot: ISE Context Visibility Endpoint]
Step 7: Troubleshooting Common Issues
- Certificate error → Verify CA trust on endpoint.
- User rejected → Check AD join status.
- VLAN mismatch → Verify authorization rule mapping.
FAQs – Wireless NAC End-to-End Lab Validation
Q1. How do I confirm if my wireless client is authenticated successfully in ISE?
- Go to ISE GUI > Operations > RADIUS > Live Logs.
- Look for the endpoint MAC or username.
- Status should show Authentication Succeeded.
- CLI check:
show logging application ise-psc.log tail
Q2. Why does my wireless client connect to the SSID but doesn’t get an IP address?
- Common causes:
- Authorization rule didn’t assign the correct VLAN.
- DHCP server unreachable in that VLAN.
- Validate:
- ISE Authorization Policy (VLAN ID returned).
- On WLC CLI:
show client detail <mac-address>
Q3. How do I validate that the WLC is actually forwarding RADIUS requests to ISE?
- On WLC CLI:
show aaa servers debug aaa all enable - In ISE: confirm logs are received under Live Logs. If not, RADIUS config or shared secret may be wrong.
Q4. Can I assign different VLANs dynamically for different user groups?
- Yes. In Authorization Policy, map AD/Identity Groups to specific VLANs via Authorization Profile.
- Example:
- IT Users → VLAN 30
- HR Users → VLAN 40
Q5. My client shows “Unable to join network” when using PEAP/EAP-TLS. What should I check first?
- PEAP: Ensure user credentials are valid in AD.
- EAP-TLS: Check that client has a valid certificate issued by a trusted CA.
- Verify trust chain: ISE Certificate Store + Endpoint Supplicant Trusted Root CA.
Q6. How do I test CoA (Change of Authorization) in this wireless NAC lab?
- On ISE, change the Authorization Profile for a connected endpoint.
- Then, in Live Sessions, click Reauthenticate.
- WLC should disconnect client and reapply the new VLAN/ACL.
- CLI on WLC:
show client detail <mac>
Q7. What’s the best way to debug wireless client issues on WLC during NAC validation?
- WLC CLI:
debug client <mac-address> show client detail <mac-address> show wlan summary - This shows real-time authentication messages and applied policies.
Q8. How do I confirm posture validation is applied during wireless NAC?
- In ISE Policy Set, configure posture requirements.
- On endpoint: Cisco AnyConnect with ISE posture module.
- Check ISE → Context Visibility > Endpoint Details for posture state.
Q9. Can guest/BYOD onboarding be tested in this same end-to-end lab?
- Yes. Create separate Authorization Rules:
- Guests → Web Redirect Portal.
- BYOD → Onboarding Policy.
- Connect a smartphone to SSID → ISE should redirect to provisioning portal.
Q10. How can I generate a summary report of wireless NAC validation for documentation?
- In ISE:
- Navigate to Operations > Reports > Endpoints and Users > Authentication Summary.
- Export as CSV/PDF.
- This report includes success/failure counts, endpoint types, and applied authorization rules.
YouTube Link
For more in-depth Cisco ISE Mastery Training, subscribe to my YouTube channel Network Journey and join my instructor-led classes for hands-on, real-world ISE experience
Closing Notes
Wireless NAC validation is the final exam for ISE deployment. By walking through WLC configuration, ISE policies, endpoint onboarding, and validation logs, you prove end-to-end enforcement works. This prevents misconfigurations, strengthens security posture, and ensures smooth operations in production.
Upgrade Your Skills – Start Today
For more in-depth Cisco ISE Mastery Training, subscribe to my YouTube channel Network Journey and join my instructor-led classes.
Fast-Track to Cisco ISE Mastery Pro:
I run a focused 4-month instructor-led CCIE Security program where you get:
- Deep-dive ISE, ASA, Firepower, VPNs.
- Hands-on labs in VMware/EVE-NG.
- End-to-end enterprise security design.
Enroll here: CCIE Security Course Outline
Enroll Now & Future‑Proof Your Career
Email: info@networkjourney.com
WhatsApp / Call: +91 97395 21088
![[Day 70] Cisco ISE Mastery Training: Wireless NAC End-to-End Lab Validation](https://networkjourney.com/wp-content/uploads/2025/08/Day-70-Cisco-ISE-Mastery-Training-Wireless-NAC-End-to-End-Lab-Validation.png)
![Wireless QoS Settings – Prioritizing Your Wireless Traffic Like a Pro[CCNP Enterprise]_networkjourney](https://networkjourney.com/wp-content/uploads/2025/07/Wireless-QoS-Settings-–-Prioritizing-Your-Wireless-Traffic-Like-a-Pro-CCNP-Enterprise.png)

![AAA Authentication with TACACS+ and RADIUS – Step-by-Step Cisco Guide [CCNP ENTERPRISE]](https://networkjourney.com/wp-content/uploads/2025/07/nj-blog-post-AAA-TACACS-RADIUS.jpg)