[Day 83] – Cisco ISE Mastery Training: pxGrid Overview & Use Cases
Table of Contents
Introduction
What you’ll master today: Building, securing, and validating pxGrid 2.0 so Cisco ISE can publish identity, posture, SGT, profiling, endpoint status, and ANC to your security ecosystem (FMC/FTD, SecureX, Stealthwatch/Secure Network Analytics, AMP/Secure Endpoint, Splunk/SIEM, DNAC, custom apps). You’ll configure end-to-end, prove data flows, and simulate actions (e.g., quarantine) while watching subscribers react in real time.
Outcome: A production-style pxGrid fabric with strict certificates, approved clients, topic subscriptions, policy-driven reactions, and repeatable GUI & CLI validation.
Problem Statement
- Controls (FW, EDR, SIEM, NDR) often don’t know the user/device context behind an IP.
- Manual response (block lists, ACL edits) is slow and inconsistent.
- Telemetry silos (FW logs, EDR alerts, NAC sessions) make triage and enforcement hard.
- Need a secure message bus to share who/what/where/risk across vendors, with near-real-time policy reaction.
Solution Overview
Cisco pxGrid 2.0 (REST + WebSocket, mutual-TLS) is ISE’s context exchange & action bus:
- Publish: ISE sends session, user, endpoint, posture, profiling, SGT, ANC events.
- Subscribe: Consumers (FMC, AMP, SNA, SIEM, SOAR, DNAC, custom apps) subscribe to topics.
- Act: Consumers invoke ISE ANC (Quarantine/Unquarantine) or re-evaluate authorization; ISE triggers CoA to network devices.
- Security: Mutual certificates, explicit client approval, topic-level authorization.
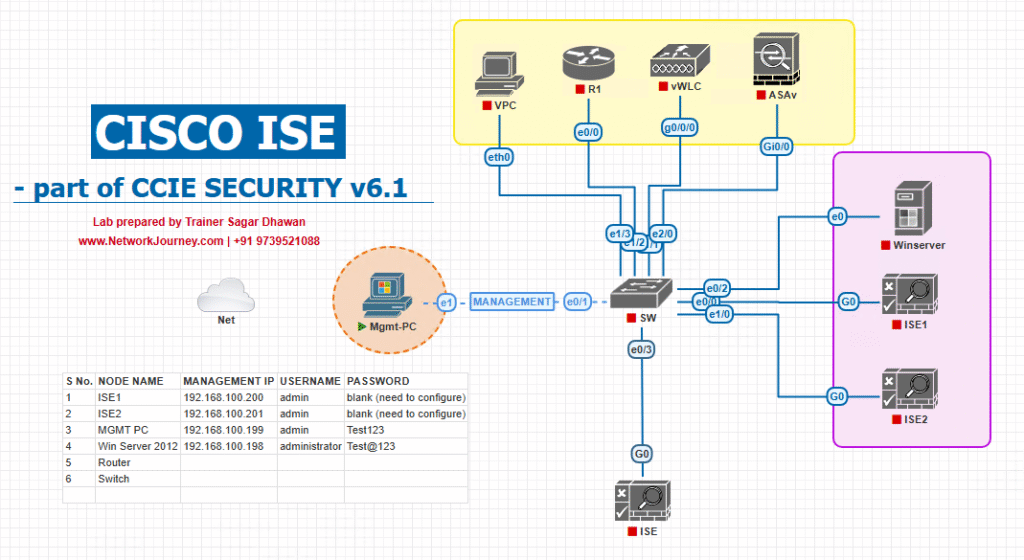
Sample Lab Topology (VMware/EVE-NG)
Compute: VMware ESXi/Workstation or EVE-NG
Nodes:
- ISE 3.2/3.3 (PAN/PSN/MnT; pxGrid enabled on PAN or dedicated PSN)
- Cisco FMC 7.x (example pxGrid subscriber)
- Secure Endpoint (AMP) Cloud (optional)
- Stealthwatch/Secure Network Analytics (SNA) (optional)
- Catalyst 9300 (17.x) access switch (802.1X/MAB, CoA/dACL/CTS)
- WLC 9800-CL (CoA/Airespace ACL/VLAN)
- AD DS
- Endpoints: Win10/11, Linux, iPhone/Android (optional)
Text diagram:
Pre-Reqs checklist:
- DNS forward/reverse for ISE & subscribers (FQDN everywhere)
- NTP sync (ISE, FMC, switch, WLC, AD)
- ISE Internal CA or enterprise PKI ready
- RADIUS authz/CoA working on access devices (for ANC tests)
- Admin creds for ISE + subscribers
Step-by-Step GUI Configuration Guide (with CLI & validation)
A) ISE – Enable pxGrid & Certificates
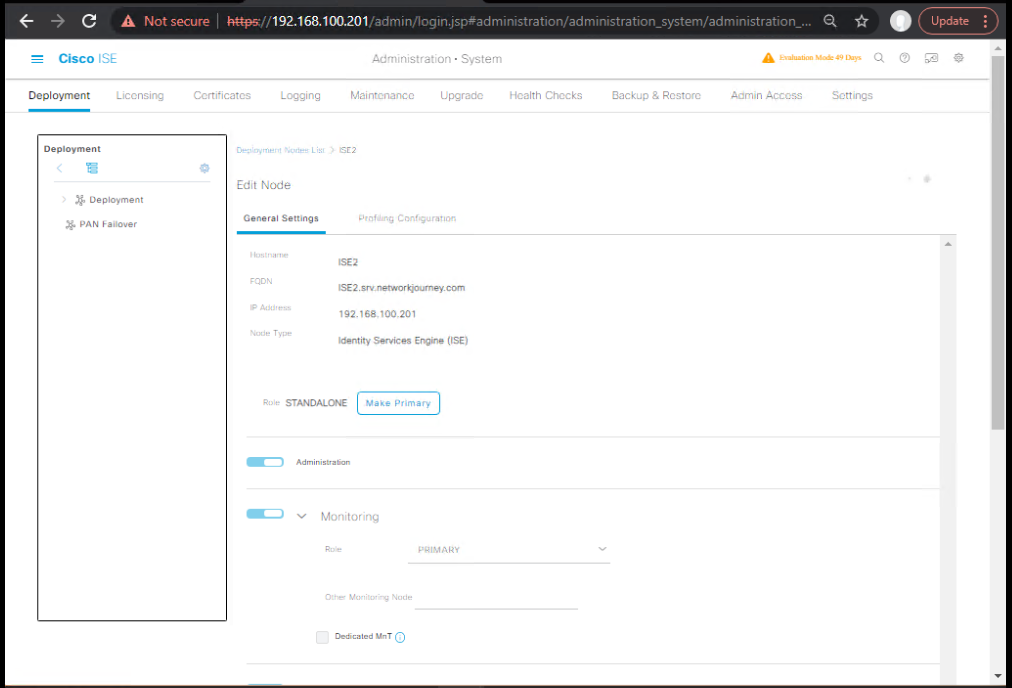
- ISE GUI:Administration → System → Deployment → select node → Edit
- Enable pxGrid (and pxGrid Controller if this is your controller) → Save
[Screenshot: ISE Deployment – Enable pxGrid]
- Enable pxGrid (and pxGrid Controller if this is your controller) → Save
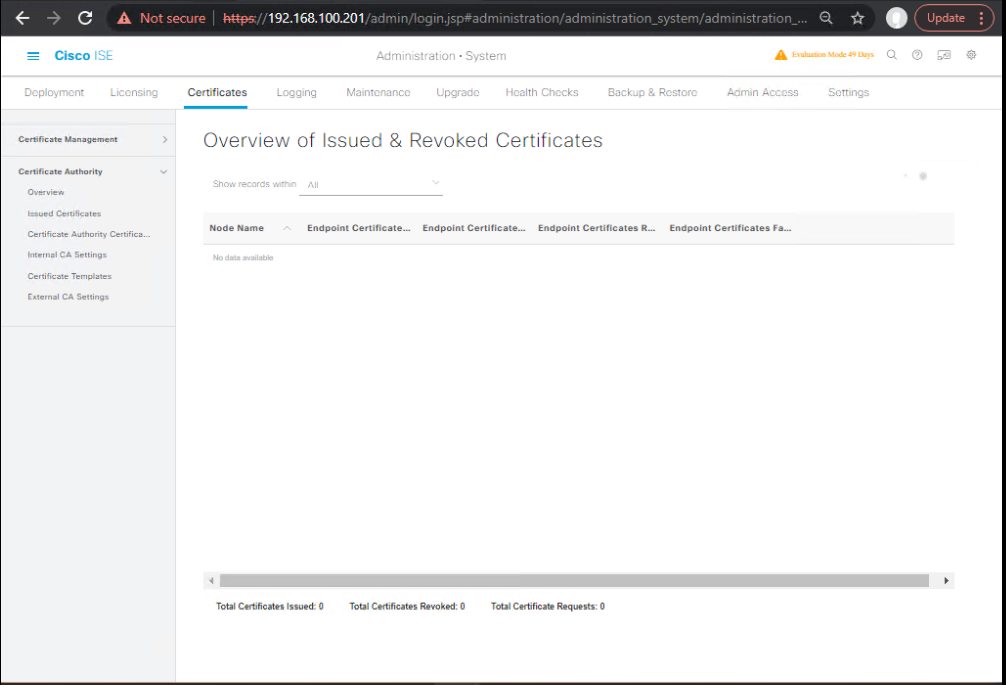
- ISE GUI:Administration → System → Certificates → Certificate Authority
- If using ISE Internal CA, ensure it’s enabled. Export the CA Chain (Base64).
[Screenshot: ISE Internal CA Chain Export]
- If using ISE Internal CA, ensure it’s enabled. Export the CA Chain (Base64).
- ISE GUI:Administration → pxGrid Services → Certificates
- Generate pxGrid Client Cert for each subscriber FQDN (e.g.,
fmc.lab.local). Include SAN (FQDN + IP). - Export client cert/key (PFX/P12) and CA chain.
[Screenshot: ISE pxGrid – Generate Client Certificate]
- Generate pxGrid Client Cert for each subscriber FQDN (e.g.,
CLI Validation (ISE):
ise/admin# show application status ise | include pxGrid ise/admin# show logging application pxgrid.log | include 'started|listening|error'
Expected: pxGrid processes running, no TLS/CA errors.
B) Subscriber (example FMC) – Add ISE/pxGrid
- FMC GUI:System → Integration → Identity Sources → Identity Services Engine
- Add ISE FQDN, upload ISE CA chain, upload pxGrid client cert (PFX/P12). Test & Save.
[Screenshot: FMC – ISE Integration Wizard]
- Add ISE FQDN, upload ISE CA chain, upload pxGrid client cert (PFX/P12). Test & Save.
- ISE GUI:Administration → pxGrid Services → Clients
- Find FMC client → Approve → verify Connected.
[Screenshot: ISE pxGrid Clients – Approve FMC]
- Find FMC client → Approve → verify Connected.
Validation (GUI):
- ISE pxGrid Clients = Approved / Online
- FMC ISE status = Connected
CLI Validation (ISE):
ise/admin# tail -n 100 /var/log/ise/pxgrid/pxgrid.log | grep -i <FMC_FQDN>
Look for “client approved”, TLS handshake success.
C) ISE – Publish What Subscribers Need
Enable Session Directory + TrustSec + ANC topics:
- ISE GUI:Administration → pxGrid Services → Settings
- Enable Session Directory publishing
- Enable TrustSec (SGT/SGACL) publishing (if you use SGT-based enforcement)
- Enable ANC topic access
[Screenshot: ISE pxGrid – Topic Settings]
- ISE GUI:Work Centers → TrustSec → Components
- Confirm SGTs exist (e.g., Quarantine, Finance, IoT).
[Screenshot: ISE TrustSec – SGTs]
- Confirm SGTs exist (e.g., Quarantine, Finance, IoT).
- ISE GUI:Policy → Policy Elements → Results → Authorization → Authorization Profiles
- Create QUAR-VLAN/QUAR-dACL/QUAR-SGT profiles for enforcement tests.
[Screenshot: ISE AuthZ Profiles – Quarantine options]
- Create QUAR-VLAN/QUAR-dACL/QUAR-SGT profiles for enforcement tests.
CLI Validation (ISE):
ise/admin# show logging application pxgrid.log | egrep -i "session|trustsec|anc"
Expected: Topics registered/publishing.
D) ISE – Authorization Policy for Quarantine (so ANC has effect)
- ISE GUI:Policy → Policy Sets → (Your Set) → Authorization
- Add rule at high priority: Condition =
Network Access:UseCase EQUALS ANC-Quarantine - Result = choose QUAR-VLAN or QUAR-dACL or QUAR-SGT
[Screenshot: ISE Authorization – Quarantine Rule]
- Add rule at high priority: Condition =
Validation (no subscriber needed yet):
- Use manual ANC (next step) and watch CoA + new policy hit.
E) ISE – Manual ANC Test (baseline)
- ISE GUI:Operations → Adaptive Network Control → Assign ANC
- Create policy QUARANTINE (Action: Quarantine or SGT assign).
- Assign ANC to a test endpoint (MAC/IP).
[Screenshot: ISE – Assign ANC]
- ISE GUI:Operations → RADIUS → Live Logs
- Find the session → verify CoA Issued = Yes, Result = QUAR-xxx
[Screenshot: ISE Live Logs – CoA + Result]
- Find the session → verify CoA Issued = Yes, Result = QUAR-xxx
CLI Validation (Access Switch):
show authentication sessions interface Gi1/0/10 details show access-session interface Gi1/0/10 show ip access-lists | i <dACL> show cts role-based sessions interface Gi1/0/10 (if TrustSec)
Expected: VLAN changed or dACL/SGT enforced.
CLI Validation (WLC 9800):
show wireless client mac <mac> detail show access-control list name <ACL-name> (if using Airespace ACL)
Expected: Client policy/VLAN/ACL reflects quarantine.
F) Subscriber – Subscribe & React (examples)
FMC example (others similar: SNA/SIEM/SOAR/DNAC)
- FMC GUI:Policies → Access Control → Identity
- Confirm Identity Source = ISE pxGrid
- Build rule: If SGT = Quarantine → Block (or If ANC tag present → dynamic rule)
[Screenshot: FMC Access Control – Identity/SGT Rule]
- Trigger ANC again (ISE) on same endpoint.
- FMC GUI:Analysis → Connections/Users
- See endpoint identity & SGT/quarantine reflected.
[Screenshot: FMC – Identity / Connection Events]
- See endpoint identity & SGT/quarantine reflected.
FTD CLI (optional):
> show users > show access-control-config > show conn address <endpoint_ip>
G) Developer/Automation Bonus (optional)
Goal: Prove a non-Cisco client can subscribe to pxGrid and print session events.
- pxGrid client cert: generate in ISE for
pxgrid-client.lab.local. - Use a pxGrid sample client (Python/Java). Configure:
- pxGrid node = ISE FQDN
- mTLS using client PFX and CA chain
- Subscribe to
com.cisco.ise.session
- Run subscriber and plug/unplug the endpoint; watch JSON session updates.
[Placeholder: code repo link in your class notes]
[Screenshot: Terminal – session JSON events from pxGrid]
H) End-to-End Validation Matrix (tick as you go)
| Plane | What to check | Where |
|---|---|---|
| Control (pxGrid) | Client approved, connected | ISE: pxGrid Clients, pxgrid.log |
| Data (topics) | Session/TrustSec/ANC publish | ISE: pxGrid Settings + logs |
| Action | CoA triggered, new AuthZ result | ISE Live Logs |
| Enforcement | VLAN/dACL/SGT applied | Switch/WLC CLI |
| Subscriber | Identity/SGT seen, rule hit | FMC/SIEM UI, device CLI |
| Time | No skew | NTP everywhere |
I) pxGrid Ops – Troubleshooting Snippets
TLS/certs:
ise/admin# show logging application pxgrid.log | egrep -i "tls|handshake|cert|trust|error"
Topic flow:
ise/admin# tail -f /var/log/ise/pxgrid/pxgrid.log | egrep -i "session|trustsec|anc|publish|subscribe"
Traffic capture (ISE):
ise/admin# tcpdump -i eth0 port 8910 -vvv -s0 -w /mnt/disc/pxgrid_tls.pcap
pxGrid Troubleshooting:
1. pxGrid Node Registration Failure
Symptom:
- pxGrid client cannot connect.
- ISE Live Logs show:
Failed to register client on pxGrid: Authorization Error - Client app certificate not trusted.
Root Cause:
- pxGrid node certificate not issued by trusted CA or client certificate missing.
Fix:
- Verify pxGrid certificate in ISE:
- GUI: Administration > System > Certificates > System Certificates
- Ensure pxGrid role is enabled on the cert.
- Export the CA chain and install it on client.
- On ISE CLI:
show application status ise show logging system ade/ADE.log | include pxgrid - Regenerate and rebind pxGrid certificate if invalid.
2. pxGrid Services Not Starting
Symptom:
show application status iseshows pxGrid innot runningstate.
Root Cause:
- pxGrid service not enabled or node not part of pxGrid persona.
Fix:
- GUI: Administration > Deployment > Select Node > Enable pxGrid persona.
- Restart application service:
application stop ise application start ise - Validate:
show application status ise
3. Client Cannot Subscribe to Topics
Symptom:
- pxGrid client app connects but cannot see session or SGT topics.
Log Example:
Subscription denied for topic com.cisco.ise.session
Root Cause:
- Client account not authorized in ISE pxGrid clients list.
Fix:
- GUI: Administration > pxGrid Services > Clients
- Approve pending client and grant access to topics.
- Test again using pxGrid client (e.g., FMC, Stealthwatch).
4. FMC–ISE pxGrid Integration Fails
Symptom:
- FMC dashboard shows “ISE not reachable”.
Root Cause:
- pxGrid port blocked (default 8910).
Fix:
- On ISE CLI, confirm pxGrid listening:
netstat -an | grep 8910 - On firewall, allow TCP 8910 between FMC ↔ ISE.
- Re-initiate connection in FMC.
5. SXP-to-pxGrid SGT Sync Issues
Symptom:
- SGTs not visible in pxGrid subscribers.
Root Cause:
- SXP or TrustSec misconfigured.
Fix:
- Check SXP status:
show cts sxp connections - Verify in ISE: Work Centers > TrustSec > SXP Devices.
- Resync manually:
pxGrid resync all
6. High CPU Usage on pxGrid Node
Symptom:
- pxGrid node CPU spikes > 90%.
Root Cause:
- Too many simultaneous subscriptions (e.g., FMC, Stealthwatch, AMP).
Fix:
- Move pxGrid persona to a dedicated ISE node.
- Distribute clients across multiple pxGrid nodes.
- Monitor with:
show cpu usage
7. pxGrid Certificates Expired
Symptom:
- pxGrid client disconnects suddenly.
Root Cause:
- pxGrid certificate expired.
Fix:
- Renew certificate in ISE:
- GUI: Administration > Certificates > pxGrid Certificate
- Generate new CSR or import new cert.
- Re-distribute certificate to clients.
- Restart pxGrid services:
application stop ise application start ise
8. pxGrid Client “Pending” State Forever
Symptom:
- Client shows as
Pendingin ISE GUI.
Root Cause:
- Auto-approval not enabled, manual approval pending.
Fix:
- GUI: Administration > pxGrid Services > Clients > Approve manually.
- If auto-approve desired: Enable “Auto Approve” in pxGrid settings.
9. Context Visibility Dashboard Not Populating Data
Symptom:
- pxGrid connected but FMC/Stealthwatch shows empty dashboard.
Root Cause:
- ISE not publishing session directory updates.
Fix:
- Enable Session Directory in pxGrid services.
- Test with CLI:
show logging application pxgrid.log - Confirm clients subscribed to session topics.
10. General Debug Commands for pxGrid
ISE CLI Debugs:
show logging application pxgrid.log tail show logging system ade/ADE.log tail debug pxgrid all
Packet Capture (to confirm connectivity):
capture-traffic interface eth0 match tcp port 8910
Reset pxGrid Service:
application stop ise application start ise
Validation Checklist for pxGrid
show application status ise→ pxGrid running- GUI → pxGrid Services → Clients → all approved
- Client can subscribe to topics (sessions, SGTs, ANC events)
- FMC/Stealthwatch dashboards receiving updates
- Certificates valid and trusted
FAQs – Cisco ISE pxGrid Overview & Use Cases
FAQ 1. What exactly is pxGrid in Cisco ISE, and how is it different from RADIUS?
Answer:
- RADIUS is a request–response protocol used for authentication/authorization during session setup.
- pxGrid (Platform Exchange Grid) is a publish–subscribe data-sharing framework.
- With pxGrid, ISE continuously streams contextual information (user, endpoint, posture, SGT, ANC events) to integrated systems like FMC, Stealthwatch, Firepower, AMP, Splunk, or SIEMs.
- RADIUS answers one query at a time, while pxGrid enables bi-directional, real-time sharing of identity + threat context across security ecosystems.
FAQ 2. What certificates are required for pxGrid, and how do I validate them?
Answer:
- pxGrid always requires mutual TLS authentication between ISE and clients.
- Each pxGrid node must have a certificate with pxGrid role enabled.
- Steps to validate:
- GUI → Administration > System > Certificates > System Certificates → check pxGrid role.
- CLI →
show logging application pxgrid.log tail openssl s_client -connect <ISE_IP>:8910
- Always install the Root CA of ISE on pxGrid clients.
FAQ 3. Which ISE node roles support pxGrid persona?
Answer:
- Only Policy Service Nodes (PSNs) can host the pxGrid persona.
- Best practice: Deploy dedicated PSNs for pxGrid, especially if large integrations (FMC, Stealthwatch, AMP) are expected.
- Admin nodes do not run pxGrid persona.
FAQ 4. How does pxGrid handle scaling when multiple clients (FMC, Stealthwatch, Umbrella, etc.) connect?
Answer:
- pxGrid supports multi-node redundancy: clients can connect to any available pxGrid node.
- Load is balanced automatically.
- Scaling tips:
- Enable pxGrid persona on at least 2 PSNs.
- Use DNS FQDN for pxGrid node registration.
- Monitor CPU/memory via:
show cpu usage show memory statistics
FAQ 5. Can pxGrid share ANC (Adaptive Network Control) policies with FMC or other systems?
Answer:
- Yes. pxGrid shares ANC events and quarantines.
- Example: If AMP detects malware, it signals ISE via pxGrid → ISE applies ANC → endpoint quarantined.
- In GUI:
- Work Centers > Policy > ANC Policies.
- Verify in logs:
show logging application pxgrid.log tail
FAQ 6. What ports does pxGrid use, and how do I troubleshoot connectivity?
Answer:
- Default Ports:
- TCP 8910 → pxGrid client connection
- TCP 443 → pxGrid REST/ERS APIs (optional)
- Troubleshoot:
- CLI:
netstat -an | grep 8910 capture-traffic interface eth0 match tcp port 8910 - Ensure firewall between pxGrid node ↔ clients allows TCP 8910.
- CLI:
FAQ 7. How do I check if pxGrid is working properly?
Answer:
- Validation checklist:
- CLI:
show application status ise→ pxGrid must be “running” - GUI: pxGrid Services → Clients → client must be Approved
- Test subscription using pxGrid client tools (Cisco pxGrid SDK or FMC integration test).
- Logs:
show logging application pxgrid.log tail
- CLI:
FAQ 8. What happens if pxGrid certificate expires?
Answer:
- All pxGrid clients immediately lose connectivity.
- Fix:
- Renew certificate in GUI (Administration > Certificates).
- Redistribute new cert to clients.
- Restart pxGrid services:
application stop ise application start ise
FAQ 9. Can pxGrid be used for SIEM integration (Splunk/QRadar)?
Answer:
- Yes. pxGrid can stream session directory, posture, and threat events to SIEM tools.
- Use-case: Splunk receives live identity + endpoint mapping via pxGrid → correlates security events with users.
- Many SIEM vendors provide native pxGrid plugins.
FAQ 10. How does pxGrid fit into TrustSec deployments?
Answer:
- In Cisco TrustSec, pxGrid is the channel that shares SGT mappings + policy context across security domains.
- Example:
- ISE assigns an SGT to endpoint.
- pxGrid sends SGT mapping to FMC.
- FMC enforces security rules based on SGT instead of IP.
- Validation:
show cts sxp connections show logging application pxgrid.log tail
YouTube Link
For more in-depth Cisco ISE Mastery Training, subscribe to my YouTube channel Network Journey and join my instructor-led classes for hands-on, real-world ISE experience
Closing Notes
- Treat pxGrid as your security fabric bus: authenticate securely, approve strictly, publish only what you need, and validate every plane (publish, subscribe, act, enforce).
- Always keep certs, DNS, and NTP tight.
- Bake in testable quarantine (ANC + AuthZ rule) to prove reaction on Day-1 and during audits.
Upgrade Your Skills – Start Today
For more in-depth Cisco ISE Mastery Training, subscribe to my YouTube channel Network Journey and join my instructor-led classes.
Fast-Track to Cisco ISE Mastery Pro — (4-month live).
- Enterprise labs: pxGrid 2.0, Threat-Centric NAC, TrustSec/SGT, Wired/Wireless, Posture, FMC/AMP/SNA/SIEM integrations
- Runbooks, diagrams, packet captures, troubleshooting bibles, mentoring & office hours
Course outline & enrollment: https://course.networkjourney.com/ccie-security/
Enroll Now & Future‑Proof Your Career
Email: info@networkjourney.com
WhatsApp / Call: +91 97395 21088