Don’t Let Your Router Crash! Master Control Plane Policing (CoPP) with Labs & CLI [CCNP ENTERPRISE]
Ever had one of those moments where your device just locks up, and you can’t even SSH or ping it anymore—even though the CPU is not maxed out? I’ve been there. As someone who’s spent years deep in the trenches of data centers and campus networks, I can tell you that most of the time, it’s not the data plane that gives up—it’s the control plane that’s overwhelmed
That’s why today, we’re diving into one of the most critical but often neglected topics in network hardening: Control Plane Policing (CoPP). If you’re building or managing enterprise-grade infrastructure—be it for service providers or high-availability enterprise cores—CoPP isn’t optional; it’s essential. In this blog, we’ll unpack what CoPP is, why it matters, how it works, and how to implement and troubleshoot it using both CLI and EVE-NG labs.
Table of Contents
Theory in Brief
What is the Control Plane?
The Control Plane is like the brain of a network device—it manages routing tables, processes management protocols (like SSH, SNMP), handles CDP/LLDP, and more. It doesn’t forward actual traffic—that’s the job of the Data Plane—but it tells the data plane how to forward traffic.
The Problem: Control Plane Overload
Unlike the data plane, which is often hardware accelerated, the control plane is CPU-driven and vulnerable to high packet rates. Malicious actors or even legitimate traffic surges (like OSPF storms) can bring your router’s brain to a halt, making it unresponsive.
The Solution: Control Plane Policing (CoPP)
CoPP is a feature that allows you to define and enforce QoS policies for traffic destined to the control plane. It helps prevent DoS attacks and keeps critical protocols functional by rate-limiting or dropping unnecessary traffic before it reaches the CPU.
How it Works
Cisco platforms implement CoPP using Modular QoS CLI (MQC). You define traffic classes, create policies, and apply them to the control-plane using a special command. You can match protocols, IPs, ACLs, or even DSCP values.
Summary
| Feature | Description |
|---|---|
| Purpose | Protect router/switch control plane from overload |
| Applies To | Traffic destined to the device itself |
| Implementation Platform | IOS, IOS-XE, NX-OS (syntax may vary) |
| Common Matches | SSH, Telnet, BGP, OSPF, SNMP, ICMP, etc. |
| Enforcement | Policy Maps with policing or rate-limiting |
| Deployment Best Practice | Permit essential, rate-limit important, drop unknown |
| Troubleshooting Tool | show policy-map control-plane, show class-map, debug control-plane |
CLI Commands
| Task | Command Example | Notes |
|---|---|---|
| Create ACL for BGP | ip access-list standard BGP-ACLpermit host 10.1.1.1 | Match trusted BGP neighbor IPs |
| Define class-map | class-map match-any BGP-CLASSmatch access-group name BGP-ACL | |
| Create policy-map | policy-map CONTROL-PLANEclass BGP-CLASSpolice 8000 1000 conform-action transmit exceed-action drop | Polices traffic to 8kbps |
| Apply to control-plane | control-planeservice-policy input CONTROL-PLANE | Applies policy to traffic going to CPU |
| Verify policy | show policy-map control-plane | Check if matches and actions are applied |
| Debug traffic | debug ip icmpdebug control-plane input | Use carefully—impacts CPU |
Real-World Use Case
| Scenario | Problem | How CoPP Helps |
|---|---|---|
| Large campus core switch | Broadcast storms or rogue SNMP floods | Rate-limit non-essential control traffic |
| BGP Edge Router under DDoS | BGP, SSH traffic floods hitting CPU | Drop untrusted source IPs, police essential protocols |
| Remote access router | ICMP flood via WAN link | Rate-limit ICMP to prevent CPU starvation |
| IoT Network | Excessive CDP/LLDP packets from unmanaged devices | Drop or rate-limit discovery protocols |
EVE-NG Mini LAB: Control Plane Policing
LAB TOPOLOGY
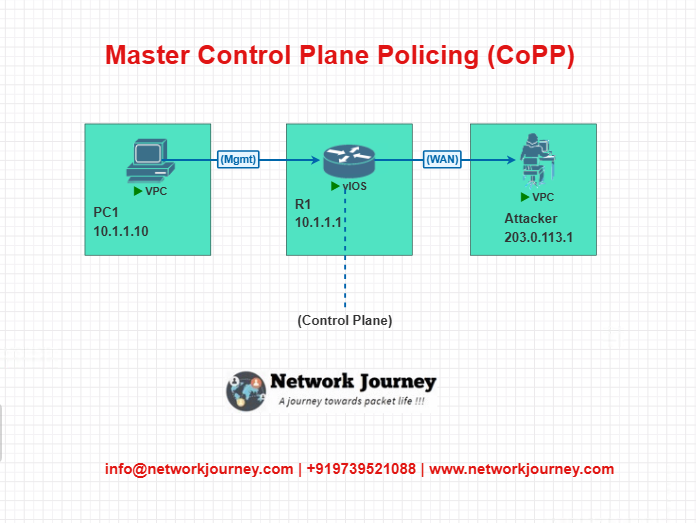
DEVICE CONFIGURATION
Step 1: Create ACL to Match BGP Peer
R1(config)# ip access-list standard BGP-ACL
R1(config-std-nacl)# permit 10.1.1.2
Step 2: Define Class-map
R1(config)# class-map match-any BGP-CLASS
R1(config-cmap)# match access-group name BGP-ACL
Step 3: Create Policy-map
R1(config)# policy-map CONTROL-PLANE
R1(config-pmap)# class BGP-CLASS
R1(config-pmap-c)# police 8000 1000
R1(config-pmap-c)# conform-action transmit
R1(config-pmap-c)# exceed-action drop
Step 4: Apply to Control Plane
R1(config)# control-plane
R1(config-cp)# service-policy input CONTROL-PLANE
VERIFICATION
R1# show policy-map control-plane
Look for “packets matched” and “drop” counts.
Troubleshooting Tips
| Symptom | Possible Cause | Solution |
|---|---|---|
| Device unreachable | CoPP drops critical management protocols | Ensure correct match in class-map and ACLs |
| Policy not matching | Wrong ACL or class-map syntax | Verify ACL entries, use show class-map |
| Legitimate packets dropped | Over-aggressive policing | Adjust policing rate and burst sizes |
| High CPU despite CoPP | CoPP not applied correctly | Re-check with show policy-map control-plane |
| ICMP reply dropped | ICMP not permitted in any class | Add class-map for ICMP with controlled rate |
Most Common FAQs on CoPP
1. What exactly is Control Plane Policing (CoPP) and why is it important?
Answer:
Control Plane Policing (CoPP) is a security and QoS feature that allows network engineers to filter and rate-limit traffic destined to the control plane (CPU) of a router or switch.
Its importance lies in:
- Preventing Denial-of-Service (DoS) attacks on the CPU.
- Ensuring that vital protocols like BGP, OSPF, SSH, SNMP, and ICMP are protected and receive sufficient CPU time.
- Allowing fine-grained control over which protocols can reach the control plane and at what rate.
Without CoPP, even a simple ICMP flood or malformed routing packet could render your core device unreachable.
2. How does CoPP differ from traditional QoS or ACL filtering?
Answer:
CoPP is control-plane specific, whereas traditional QoS or ACLs are often applied on transit traffic going through the data plane.
Key differences:
| Feature | Traditional QoS/ACLs | CoPP |
|---|---|---|
| Applies to | Transit traffic (data plane) | Control plane (to device CPU) |
| Objective | Prioritize/delay/drop traffic | Protect router CPU from overload |
| Applied On | Interfaces | Control plane (via control-plane command) |
CoPP protects the device itself, not the traffic going through it.
3. Can CoPP cause legitimate traffic like BGP or SSH to drop?
Answer:
Yes, if misconfigured, CoPP can unintentionally rate-limit or block essential control plane traffic.
Common causes include:
- Incorrect or missing IPs in the ACL.
- Overly strict policing values.
- Not accounting for burst traffic from protocols like OSPF or BGP.
Tip: Always test CoPP policies in a lab first and monitor live counters (show policy-map control-plane) during initial deployment.
4. What is the syntax to apply a CoPP policy in Cisco IOS/IOS-XE?
Answer:
The syntax uses MQC (Modular QoS CLI) style:
- Define an ACL: nginxCopyEdit
ip access-list standard SSH-ACL permit host 10.1.1.1 - Define a class-map: pgsqlCopyEdit
class-map match-any SSH-CLASS match access-group name SSH-ACL - Define a policy-map: pgsqlCopyEdit
policy-map CONTROL-PLANE class SSH-CLASS police 8000 1000 conform-action transmit exceed-action drop - Apply to control-plane: pgsqlCopyEdit
control-plane service-policy input CONTROL-PLANE
This limits SSH traffic from 10.1.1.1 to 8 Kbps with 1 Kbps burst.
5. What are the best practices when designing a CoPP policy?
Answer:
Follow these structured best practices:
- Categorize traffic:
- Critical: SSH, BGP, OSPF → Permit or rate-limit gently.
- Important: SNMP, ICMP → Police moderately.
- Unknown/Unwanted: Drop or tightly police.
- Use specific ACLs to match trusted sources only.
- Monitor initial traffic rates before deciding on police values.
- Test in EVE-NG or lab before applying to production.
- Document policy intent for future audits or team members.
6. What’s the difference between CoPP and CPPr?
Answer:
While both protect the control plane, there are key differences:
| Feature | CoPP | CPPr (Control Plane Protection) |
|---|---|---|
| Scope | Whole control-plane | Sub-interfaces of control-plane (routing, mgmt) |
| Configuration | MQC style with ACL, class-map, etc. | Platform-dependent (available in ISR/ASR) |
| Granularity | Basic | More granular |
| Availability | IOS/IOS-XE | Not available on all platforms |
Use Case Tip: If CPPr is available on your platform, it gives more refined control over types of control traffic.
7. How to verify if CoPP is working correctly on a live router?
Answer:
Use the following command to verify CoPP behavior:
show policy-map control-plane
Look for:
- Class Match Count – How many packets are hitting each class.
- Dropped Packets – Ensure legitimate protocols aren’t being dropped.
- Police Rate Match – Confirms if policing is applied as intended.
Additionally, check:
show access-lists
show class-map
show policy-map
Use debug ip packet or debug control-plane carefully (on low CPU usage).
8. What happens if I don’t implement CoPP on my edge routers?
Answer:
Not having CoPP can lead to:
- Complete CPU starvation during attacks like ICMP floods or BGP route spamming.
- Unreachable routers—even management protocols like SSH or SNMP may stop responding.
- Control plane instability affecting OSPF/BGP adjacencies.
- Increased security risk from unauthorized or malformed packets.
For any internet-facing device, CoPP is a must-have, not a luxury.
9. How can I test CoPP in a lab setup like EVE-NG?
Answer:
Here’s how to simulate and test CoPP:
- Create 3 nodes:
- R1 (router with CoPP policy)
- PC1 (management station)
- PC2 or Kali Linux (attacker)
- Use attacker node to flood R1 with ICMP, SNMP, or TCP traffic.
- Check CoPP stats using: pgsqlCopyEdit
show policy-map control-plane - Adjust police values and observe whether packets are dropped or allowed.
You can also run ping -t, nmap, or use hping3 to simulate various protocols.
10. Can I log dropped or policed packets in CoPP for auditing?
Answer:
Yes, but with limitations.
Options include:
- ACL logging: pgsqlCopyEdit
ip access-list extended DROP-ACL deny ip any any log - Syslog configuration to send logs to a central server.
- Use SNMP traps (for larger environments) tied to control-plane thresholds.
- Manual counter checks: pgsqlCopyEdit
show policy-map control-plane
Logging every packet can be CPU-intensive, so log initially during testing, then disable for performance.
YouTube Video: CoPP Explained with Demo
Watch the Complete CCNP Enterprise: Master Control Plane Policing (CoPP) with Labs & CLI Demo & Explanation on our channel:
Final Note
Understanding how to differentiate and implement Don’t Let Your Router Crash! Master Control Plane Policing (CoPP) with Labs & CLI is critical for anyone pursuing CCNP Enterprise (ENCOR) certification or working in enterprise network roles. Use this guide in your practice labs, real-world projects, and interviews to show a solid grasp of architectural planning and CLI-level configuration skills.
If you found this article helpful and want to take your skills to the next level, I invite you to join my Instructor-Led Weekend Batch for:
CCNP Enterprise to CCIE Enterprise – Covering ENCOR, ENARSI, SD-WAN, and more!
Get hands-on labs, real-world projects, and industry-grade training that strengthens your Routing & Switching foundations while preparing you for advanced certifications and job roles.
Email: info@networkjourney.com
WhatsApp / Call: +91 97395 21088
Upskill now and future-proof your networking career!
![Don’t Let Your Router Crash! Master Control Plane Policing (CoPP) with Labs & CLI [CCNP ENTERPRISE]](https://networkjourney.com/wp-content/uploads/2025/07/nj-blog-post-CoPP.jpg)
![EIGRP Metric Calculation – Understand the Brain Behind Route Selection. [CCNP ENTERPRISE]](https://networkjourney.com/wp-content/uploads/2025/06/EIGRP-Metric-Calculation-–-Understand-the-Brain-Behind-Route-Selection_networkjourney.png)

