Loop Prevention Techniques – Keeping Your Network Stable and Efficient [CCNP ENTERPRISE]
We’re going to unravel one of the most critical topics in networking — Loop Prevention Techniques. If you’ve ever spent hours troubleshooting unstable networks, flapping routes, or broadcast storms, chances are, you’ve come face-to-face with some sort of looping issue.
In the classroom or during real-world deployments, this is something I see engineers struggle with quite a bit. But don’t worry — by the end of this article, you’ll not only understand why loops happen, but also how to prevent them like a pro using industry-standard techniques and tools.
Let’s break it down in a way that’s simple, actionable, and lab-tested .
Table of Contents
Theory in Brief – What Causes Loops?
In networking, a loop is a scenario where packets continuously circulate between devices without reaching their destination. This can:
- Consume bandwidth
- Overwhelm routers/switches
- Cause instability and outages
Loops typically occur in Layer 2 (switching) or Layer 3 (routing) domains, and the prevention techniques vary depending on the layer.
Layer 2 Loops
At Layer 2, Ethernet doesn’t have a native TTL mechanism — so frames can circulate forever. This is why Spanning Tree Protocol (STP) and its variants exist: they prevent switching loops by creating a loop-free topology.
Layer 3 Loops
At Layer 3, routing loops occur when incorrect or outdated routing information causes packets to bounce between routers. These are often a result of:
- Slow convergence
- Misconfiguration
- Route redistribution without filters
To combat this, routing protocols have built-in loop prevention mechanisms like hop count limits, split horizon, and route poisoning.
Comparison – Loop Prevention Techniques
| Technique | Layer | Used In | Pros | Cons |
|---|---|---|---|---|
| Spanning Tree Protocol | 2 | Ethernet Switching | Automatically blocks loops | Slow convergence (in classic STP) |
| Rapid STP / MST | 2 | Modern Switching | Faster convergence | Still can block backup paths |
| Split Horizon | 3 | RIP, EIGRP | Prevents routing info bouncing | Doesn’t work in all topologies |
| Route Poisoning | 3 | RIP | Marks bad routes to flush them | Limited to distance-vector protocols |
| Hold-Down Timers | 3 | RIP | Suppresses route flapping | May delay convergence unnecessarily |
| TTL / Hop Count Limit | 3 | All IP packets | Ensures packets don’t loop forever | Doesn’t prevent loop formation |
| Loop Guard / BPDU Guard | 2 | Cisco Switching | Prevents unidirectional loops | Needs manual config and monitoring |
| Route Filtering with Tags | 3 | Redistribution | Prevents routing loop via tags | Requires route-map knowledge |
Essential CLI Commands
| Command | Description |
|---|---|
show spanning-tree | View STP status and root bridge info |
spanning-tree bpduguard enable | Enable BPDU guard on interface |
show ip protocols | View routing protocol timers & AD |
debug ip rip / debug eigrp packets | Trace routing updates for loop detection |
show ip route | Examine route origin and potential loops |
show ip ospf database | Verify LSAs and routing loops in OSPF |
| `show run | include route-map` |
Real-World Use Case: Multi-WAN with Conditional Routing & Redistribution
| Scenario | Description |
|---|---|
| Environment | Enterprise with dual WAN links (ISP1 and ISP2) |
| Problem | Loops occurred due to improper redistribution between OSPF and EIGRP |
| Solution | Used route-maps with tagging + distribute-list filtering |
| Result | Routes are now cleanly exchanged without looping back into original domain |
| CLI Used | set tag, match tag, route-map, redistribute, distribute-list |
EVE-NG LAB: Simulating a Routing Loop and Preventing It
Lab Topology
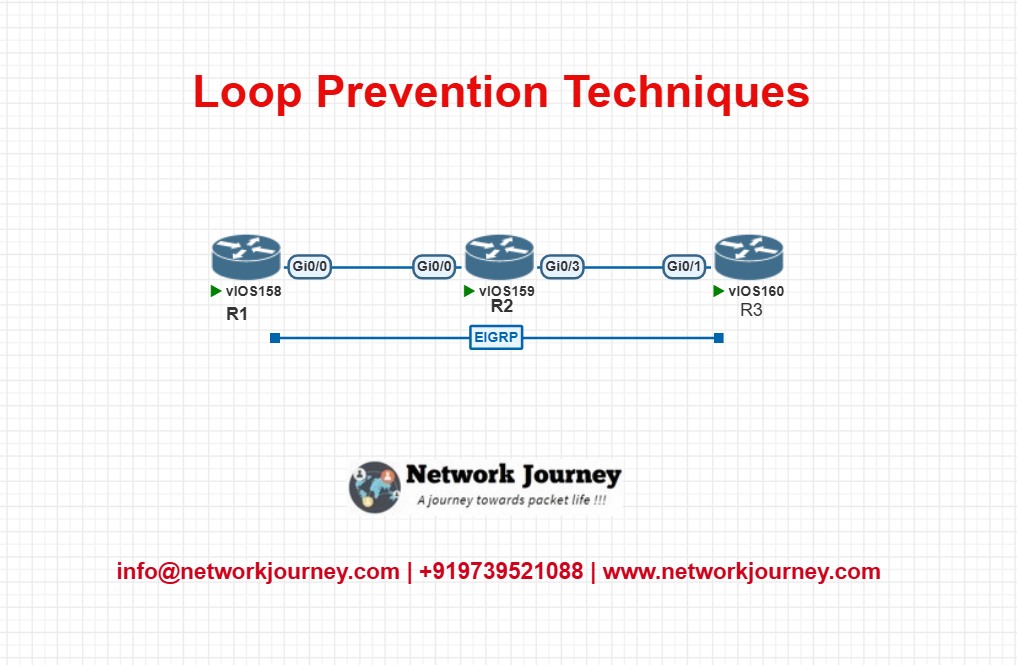
Goal:
- R1 runs OSPF
- R3 runs EIGRP
- R2 redistributes between both
Without proper filtering, R1 → R2 → R3 → R2 → R1 will create a loop!
Key Configuration Snippet
On R2: Tag incoming EIGRP routes
route-map TAG-EIGRP permit 10
set tag 100
router ospf 1
redistribute eigrp 100 subnets route-map TAG-EIGRP
! Prevent re-injection
route-map BLOCK-TAG permit 10
match tag 100
!
route-map BLOCK-TAG deny 20
router eigrp 100
redistribute ospf 1 route-map BLOCK-TAG
Verification
show ip route
debug ip routing
show ip protocols
You’ll now see that OSPF routes tagged with 100 do not return to EIGRP — loop prevented!
Troubleshooting Tips
| Symptom | Possible Cause | Fix |
|---|---|---|
| STP topology flaps frequently | Misbehaving switches or unidirectional link | Enable BPDU Guard and Loop Guard |
| EIGRP routes bounce back into OSPF | No filtering or tagging applied | Use route-maps with tags |
| RIP loops in hub-and-spoke topology | Split horizon disabled on hub | Enable split horizon or use filtering |
| Traffic keeps spinning between routers | No TTL decrement or convergence delay | Check TTL, use debug ip packet |
| Convergence too slow after loop fix | STP/RIP timers too high | Optimize hello/dead/hold-down timers |
FAQs – Loop Prevention Techniques
1. What is a routing loop, and why is it dangerous for a network?
Answer:
A routing loop occurs when packets circulate endlessly between routers due to incorrect or outdated routing information. It happens mostly in dynamic routing environments where convergence is slow or broken. This situation consumes bandwidth, CPU, and memory resources and can bring down your entire network segment. That’s why loop prevention is not just good practice—it’s essential.
2. How do distance vector protocols prevent routing loops?
Answer:
Distance vector protocols like RIP and EIGRP use several loop prevention mechanisms:
- Split Horizon: Prevents a route learned on an interface from being advertised back out the same interface.
- Route Poisoning: Marks a failed route with an unreachable metric (e.g., 16 in RIP).
- Hold-down Timers: Suppresses changes for a certain period to allow stable convergence.
- Triggered Updates: Sends immediate updates on route changes.
These techniques help avoid loops before they form or reduce the impact of a temporary loop.
3. What loop prevention techniques are used in OSPF?
Answer:
OSPF is a link-state protocol and doesn’t rely on techniques like split horizon or route poisoning. Instead, it uses:
- Dijkstra’s SPF algorithm: Calculates the shortest path tree with a complete network topology.
- LSA aging and sequence numbers: Ensure routers always have the most recent information.
- Hierarchical design with areas: Limits the scope of route updates, making the protocol more loop-resilient.
Since OSPF maintains a full map of the network, it inherently avoids routing loops during normal operation.
4. How does BGP prevent routing loops, especially on the internet?
Answer:
BGP (Border Gateway Protocol) uses AS_PATH attribute to prevent loops. Every time a BGP route passes through an autonomous system (AS), the AS number is prepended to the AS_PATH.
If a router receives a route containing its own AS number in the AS_PATH, it knows that the route has already passed through it and rejects it, preventing a loop.
This is a very scalable and effective technique in large-scale networks like the internet.
5. What is the role of TTL in loop prevention?
Answer:
TTL (Time to Live) is a Layer 3 mechanism in IP packets that acts as a last-resort loop prevention technique. Every time a packet passes through a router, the TTL is decremented by 1.
If TTL reaches 0, the packet is discarded, and an ICMP “Time Exceeded” message is sent back. This prevents packets from looping infinitely, though it doesn’t stop the loop itself—just its symptoms.
6. What is Split Horizon, and how does it work?
Answer:
Split Horizon is a simple yet effective rule used in distance vector protocols like RIP and EIGRP. It states:
“Never advertise a route back out of the interface from which it was learned.”
This avoids the possibility of another router considering you as a valid next-hop for a route that it originally advertised to you. It’s a key defense mechanism against loops in small-to-medium networks.
7. What is route poisoning and how is it different from hold-down timers?
Answer:
Route Poisoning means advertising an unreachable route with the maximum possible metric (e.g., 16 in RIP, which means “infinity”). This tells all neighboring routers that the route is no longer valid.
On the other hand, Hold-down Timers temporarily suppress changes to routes for a fixed period, allowing time for the network to converge. They prevent the “bouncing” of routes due to flapping links.
Both work together to stabilize and protect the network during topology changes.
8. How does EIGRP prevent loops differently from RIP?
Answer:
EIGRP uses a more advanced method called the Diffusing Update Algorithm (DUAL). It ensures that:
- Routes are only installed if a feasible successor exists.
- Feasibility Condition ensures loop-free routes by comparing advertised distances.
Unlike RIP, which waits on timers, EIGRP makes intelligent decisions based on real-time topology changes. This makes loop prevention faster and more reliable.
9. Can using static routes create routing loops? How do we prevent them?
Answer:
Yes, static routes can unintentionally cause loops, especially in redundant topologies where administrators forget to account for failover paths or don’t monitor interface states.
To prevent loops with static routes:
- Always use next-hop verification.
- Combine with IP SLA and object tracking.
- Implement floating static routes with higher AD as backups.
Manual configuration needs careful planning—static doesn’t mean safe by default.
10. What best practices should a network engineer follow to avoid routing loops?
Answer:
Here are some practical recommendations:
- Understand your routing protocol’s loop prevention tools (split horizon, DUAL, SPF, AS_PATH).
- Use route summarization to limit routing updates and convergence scope.
- Design a hierarchical network (especially with OSPF areas or BGP confederations).
- Avoid unnecessary redistribution between protocols.
- Monitor routes proactively using syslogs, SNMP traps, or NetFlow.
Loop prevention is about anticipating mistakes, not just reacting to them. Think like a troubleshooter before issues arise.
YouTube Link
Watch the Complete CCNP Enterprise: Loop Prevention Techniques – Keeping Your Network Stable and Efficient Lab Demo & Explanation on our channel:
Final Note
Understanding how to differentiate and implement Loop Prevention Techniques – Keeping Your Network Stable and Efficient is critical for anyone pursuing CCNP Enterprise (ENCOR) certification or working in enterprise network roles. Use this guide in your practice labs, real-world projects, and interviews to show a solid grasp of architectural planning and CLI-level configuration skills.
If you found this article helpful and want to take your skills to the next level, I invite you to join my Instructor-Led Weekend Batch for:
CCNP Enterprise to CCIE Enterprise – Covering ENCOR, ENARSI, SD-WAN, and more!
Get hands-on labs, real-world projects, and industry-grade training that strengthens your Routing & Switching foundations while preparing you for advanced certifications and job roles.
Email: info@networkjourney.com
WhatsApp / Call: +91 97395 21088
Upskill now and future-proof your networking career!
![Loop Prevention Techniques – Keeping Your Network Stable and Efficient [CCNP ENTERPRISE]_networkjourney](https://networkjourney.com/wp-content/uploads/2025/07/Loop-Prevention-Techniques-–-Keeping-Your-Network-Stable-and-Efficient-CCNP-ENTERPRISE.png)
![Ticket#8 - VOIP Choppy Audio – DSCP Marking Mismatch Fixed [QoS Real World] [CCNP ENTERPRISE]](https://networkjourney.com/wp-content/uploads/2025/07/nj-blog-post-Ticket-8.jpg)
![Ansible Playbook for VLAN Configuration – Automate Smarter, Not Harder! [CCNP ENTERPRISE]_networkjourney](https://networkjourney.com/wp-content/uploads/2025/07/Ansible-Playbook-for-VLAN-Configuration-–-Automate-Smarter-Not-Harder-1.png)
